Why are Internal Controls Critical for Your Organization?

Bleeping Computer reported a recent ransomware attack on multiple medical groups in the Heritage Provider Network in California, USA. Data from over 3 million patients were exposed due to this attack. The attackers stole sensitive data, including social security numbers, medical reports, health plan member numbers, and contact details.
Such breaches raise the threat level for millions of users and related organizations.
One of the ways to improve an organization’s security posture is to have tighter internal controls. But to implement internal controls correctly, it is imperative to understand them in depth. Let’s take an in-depth look into what internal controls are and why they are critical in the present day.
What are internal controls?
Security controls include but are not limited to, the actions taken to avoid, detect, counteract, and prevent/minimize the damage to an organization’s physical and digital assets. There are two types of security controls – external and internal.
- External security controls are the controls that are put into place by any third party to ensure that the organization protects its physical and digital assets. These controls include compliance regulations, like GDPR, CPRA, and PCI/DSS, and frameworks, such as SOC2, ISO 27001, and NIST frameworks.
- Internal controls are the series of policies, procedures, and technical safeguards put in place by the organization to secure its physical and intellectual assets. These controls include firewalls, data backups, secure logins, employee training, and internal audits.
What are the types of internal controls?
Internal controls are divided into three primary categories depending on the type of function they perform. They are as follows;
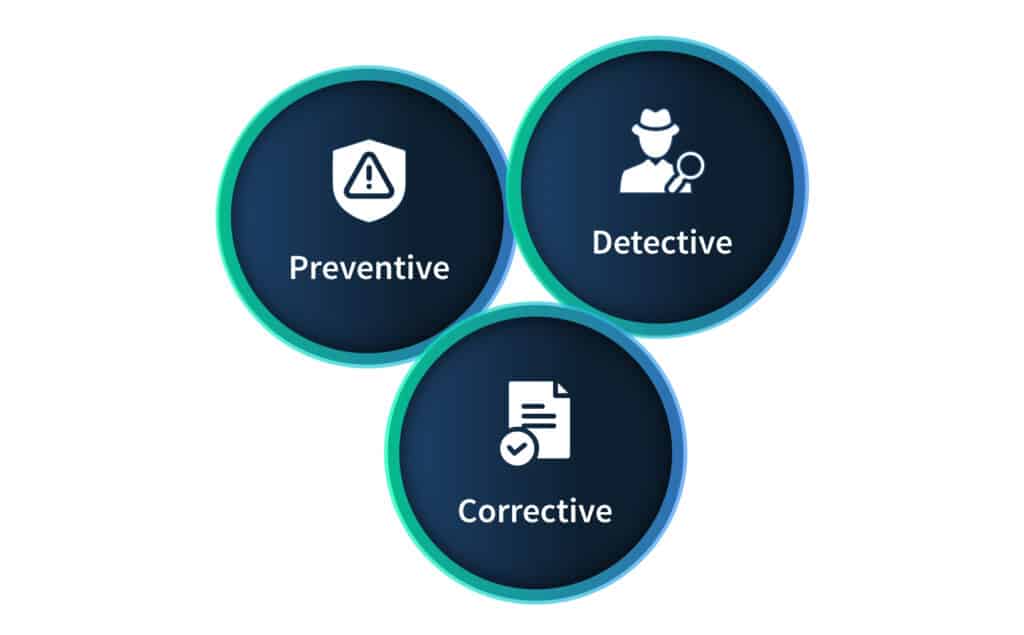
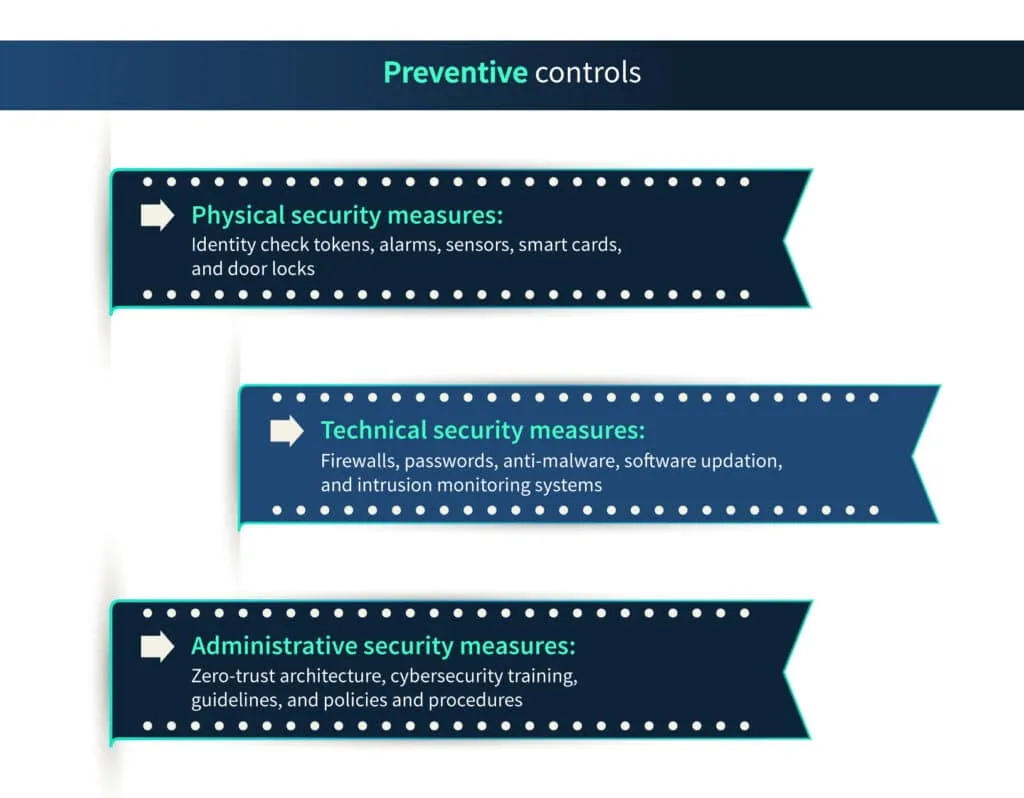
Preventive controls
Preventive security controls are the actions taken by an organization to prevent unfavorable events from happening. It is designed to keep out incorrect information, undesirable code, or unauthorized person from the organization’s systems.
Some examples of preventive cybersecurity controls are:
Detective controls
Detective controls are the internal controls designed to detect the threat event while it is happening. These controls can assist the organization during the event and while conducting the event review. Detective controls alert the management in case of a breach and help them track the security breach after the event.
Some examples of detective controls are:

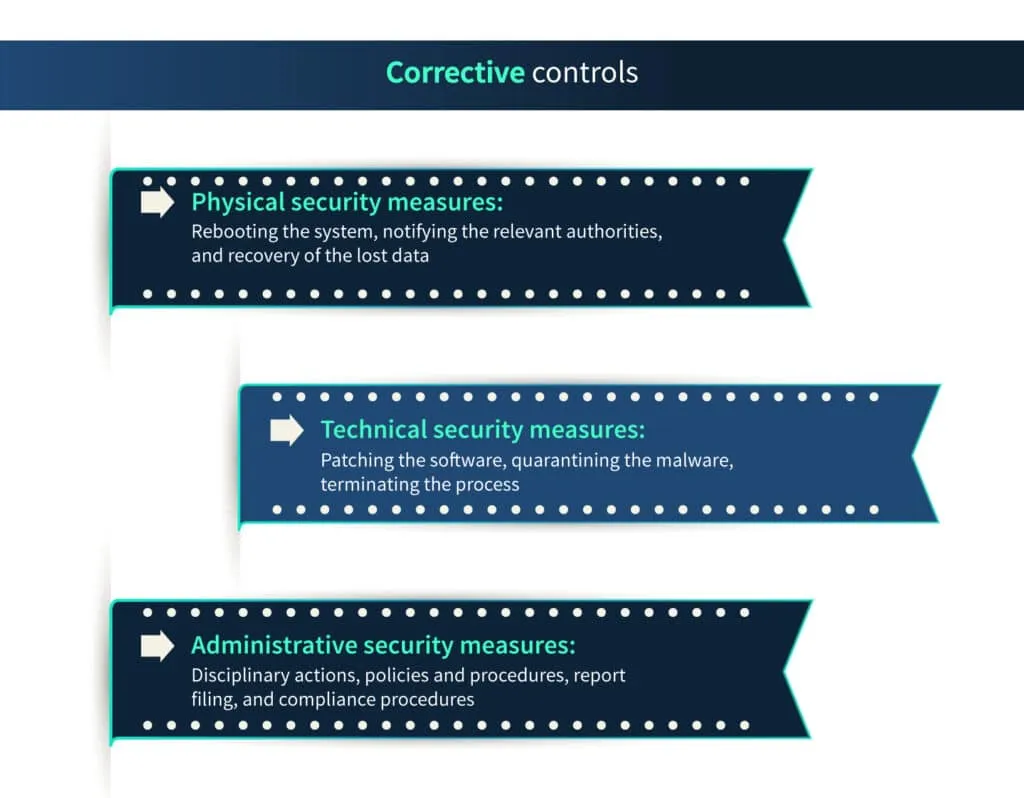
Corrective controls
Despite sufficient preventive measures, your organization might fall victim to a cybersecurity incident. The internal controls for taking corrective actions are designed to measure and minimize the effects of the security incident and minimize business downtime after the incident. The corrective measures are taken after the detective measure discovers the issues. After the incident, the preventive and detective measures are reconsidered, and changes are made as required to prevent another attack.
The following are some examples of corrective internal controls:
What are the different components of internal controls?
The Committee of Sponsoring Organizations (COSO) of the Treadway Commission has recommended five components of internal controls to assist organizations in developing their own distinctive and effective internal controls.
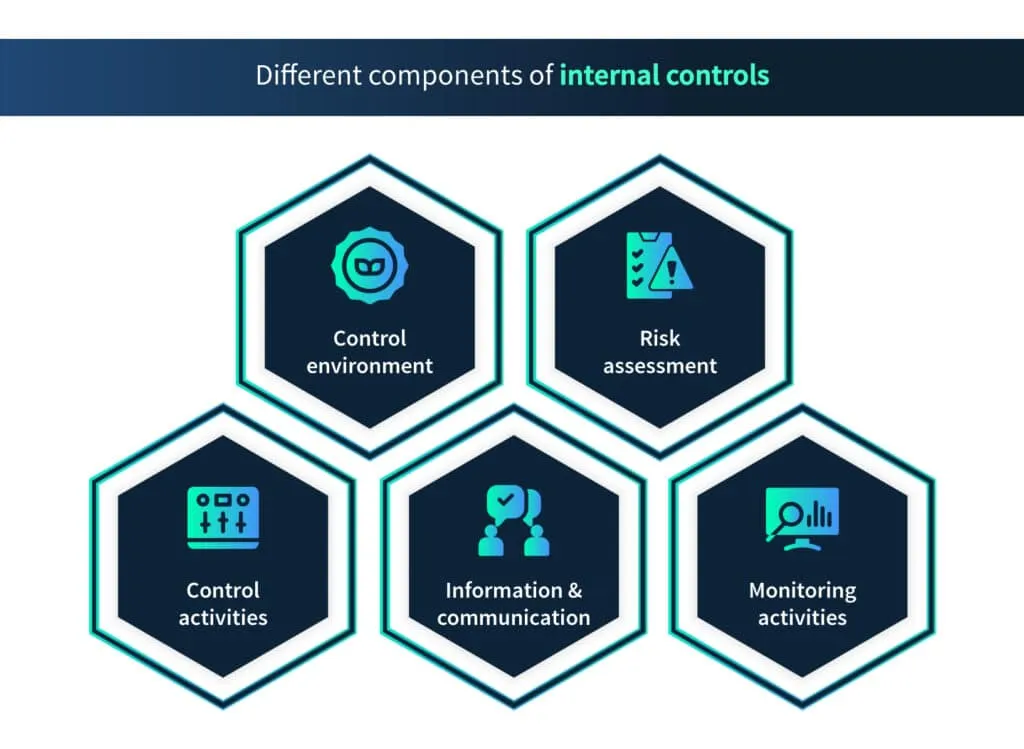
Control environment
Control environment defines the authority and responsibility structure of an organization. An organization should follow the following rules to develop a reliable control environment:
- The control environment should be such that it demonstrates a commitment to integrity and ethical values
- The superior officer exercises the responsibility of overseeing their ward
- The control environment should establish a clear structure of authority and responsibility
- It should be committed to competence
- It should enforce accountability
Risk assessment
The second component of internal control is risk assessment. An organization should consider its operation, reporting, and compliance objectives by keeping cybersecurity in mind. They should ask themselves how secure their operation is. Are they taking adequate measures for compliance? And are they reporting the true and fair state of affairs? The following points should be taken into account while assessing the cyber risk in internal controls:
- The plan should specify suitable objectives
- The control measures should be able to identify and analyze risks
- Fraud risk must be taken into account while formulating the internal controls
- If there are any significant changes in the organization, the internal controls should be able to identify and analyze them
Control activities
Control activities – technological and general – can help an organization to reduce cyber risk. An organization should form policies and procedures addressing control activities to improve its cyber resilience.
- Internal controls should select and develop control activities
- The general controls must be selected and developed over technology
- The control activities should be deployed through policies and procedures
Information and communication
Communication and information play a critical role in the organization’s business. The organization should define internal and external communication channels and protocols for secure communication.
For example, an organization can set email as the official communication channel for external communications and Slack for internal communications. The cybersecurity posture of these channels must be verified beforehand.
- The internal controls must use good quality, relevant information
- It should address internal and external communications
Monitoring activities
If you just set policies and procedures and don’t take pains to verify whether they are being implemented adequately, your system is bound to fail. Internal controls should be verified by conducting monitoring activities, such as internal audits, regularly.
- You can conduct periodic internal audits or have a system of ongoing audits;
- Any deficiencies in the internal controls must be communicated to the management, and appropriate steps to nullify the effects of the deficiencies must be taken.
Why are internal controls critical for your organization?
Internal controls are not limited to the IT department but extend throughout the organization. Every department, including finance, marketing, and administration, should adhere to the policies and procedures to mitigate cybersecurity risks. Internal controls ensure that the organization takes adequate measures to prevent cybersecurity incidents.
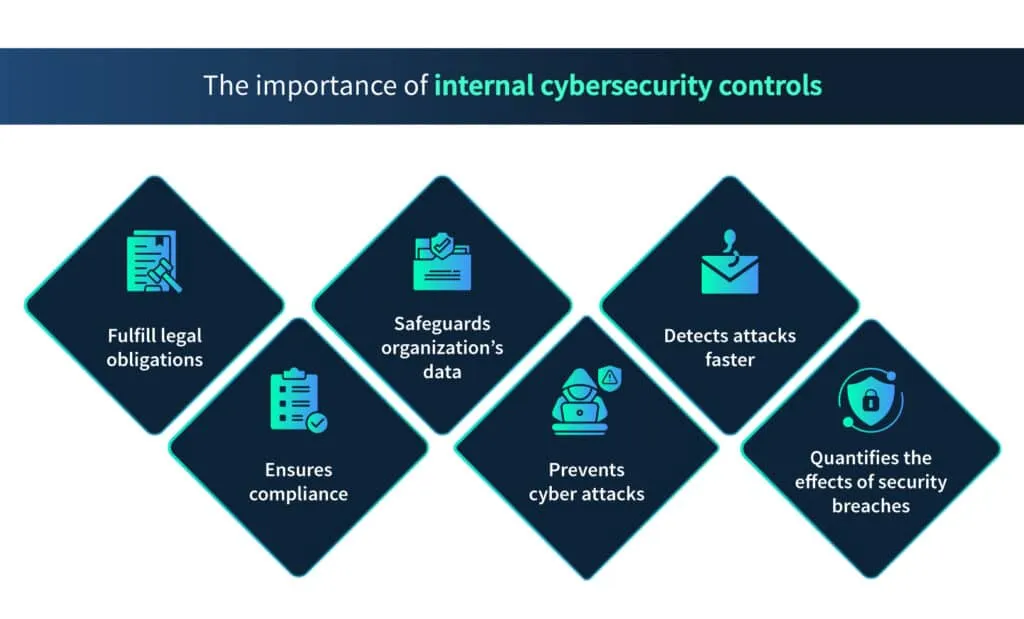
The importance of internal cybersecurity controls is shown below:
Fulfill legal obligations
Many financial compliances require organizations to declare security measures in their financial reports.
Additionally, the Sarbanes-Oxley Act of 2002 (SOX) also requires certain proof of internal controls. The SOX was created to deal with fraudulent financial practices and accounting errors in the wake of the frauds committed by public companies such as Enron, WorldCom, and Tyco International. The Act mostly applies to public companies; however, some provisions apply to private companies and non-profit organizations as well.
Section 404 of the SOX deals with “Management Assessment and Internal Controls.” This section requires the company to publish the details about its internal controls. Additionally, it requires the company executives to sign the reports and make them personally liable in case of violations.
The SOX requires the company to report annually about the steps taken to prevent fraud and that they have addressed any uncertainties in the reports. It further requires the accurate presentation of the financial data.
Ensures compliance
Compliance standards like GDPR, CPRA, PCI/DSS, and SOC 2 require organizations to follow strict internal controls. Customers can trust you more with their information if they feel you are taking adequate measures to protect it. A compliance certificate can prove your due diligence to the customers.
Internal controls can assist you in compliance with the federal, state, and local laws and regulations affecting your organization’s operations.
Safeguards organization’s data
There is a saying, “small change, big difference.” Information or data security can only be assured by making small changes in the habits of every person working for the organization. Internal controls can guide the employees about cyber hygiene and physical security. They can also be used to check whether the employees are actually following the guidelines issued by the management.
For example, as a part of security standards, the management can set a password expiration time, after which the employees must change their passwords. This policy prevents an attacker from using a leaked password if a certain amount of time has elapsed, thereby decreasing the chances of a cyber attack.
In order to check whether the employee has changed their password, the organization can code the applications to block access with older passwords.
Prevents cyber attacks
Robust internal controls can dodge malicious attacks on the organization’s system. All the hardware, software, networks, and Internet of things (IoT) devices are verified periodically to detect and eliminate vulnerabilities. It reduces the chances of vulnerabilities being found by an actor and used for malicious purposes.
On the other hand, you can also control the types of websites the employees can access on their devices to prevent cyber attacks from malicious sites. You can whitelist the safe websites and blocklist the malicious websites. You can either set your system to allow only whitelisted websites or restrict access to blocklisted ones.
Detects attacks faster
Breaches can go undetected for long periods, causing more and more damage with time. If the attackers have more time inside the organization’s network, they can steal more information and can move laterally and horizontally in the network.
This freedom of movement might lead to a secondary breach of the supplier’s or customer’s network. Early detection can pull breaks on the breach. Strong internal controls are the best answer to early detection.
For example, if an employee makes the mistake of clicking on a phishing link and lets in an attacker, it might go undetected for a long time. However, with strong internal controls, you can detect and mitigate the breach faster.
Quantifies the effects of security breaches
After a security breach, an organization must take stock of what is lost. Questions like how much data is stolen, if the data includes sensitive information of the users, or if any other network is compromised need to be answered rapidly.
The law requires the breached organization to release a statement to the government, framework agencies, and the affected parties about the stolen information. Internal controls can help the organization quantify the data easily.
For example, there is a data breach in your organization, and the customer database containing information about the customers of a certain geographic location is stolen. In the absence of strong internal controls, it would be difficult to isolate the database to quantify the leak.
Conclusion
Internal controls are crucial for any organization as they serve as a system of checks and balances to safeguard against fraud, errors, and other financial mismanagement. These controls ensure that financial information is accurate, complete, and reliable, which in turn helps to build trust and confidence among stakeholders.
Effective internal controls also help organizations comply with regulatory requirements and reduce the risk of financial losses. By implementing internal controls, organizations can mitigate risks, increase operational efficiency, and improve overall performance.
In short, internal controls are a critical component of any successful organization, and their importance cannot be overstated. Schedule a demo with our experts today to learn more about how to streamline the process of setting up internal controls using Scrut smartGRC.

FAQs
What are internal controls?
Internal controls are the actions taken by an organization to prevent and detect cybersecurity threats and counteract them in case of a security breach.
What are the different components of internal controls?
The following are the different components of internal control:
- Control environment
- Risk assessment
- Control activities
- Information and communication
- Monitoring activities
How does an organization verify the implementation of internal controls?
Organizations can carry out internal audits to verify the effectiveness of internal controls. These internal audits can be carried out periodically, that is, quarterly, monthly, or yearly, or can be carried out continuously. Continuous monitoring involves carrying out verification of a section of internal controls daily.


















