Staying on the Offence: Strengthening Cloud Security with Continuous VAPT

Cloud computing has become an integral part of modern businesses, enabling agility, scalability, and cost-efficiency. However, the rise of cloud adoption has also brought about new security challenges.
To tackle these challenges, organizations are fast turning towards offensive security methods. Offensive security involves actively testing and probing an organization’s systems and networks to uncover vulnerabilities before malicious actors can exploit them.
One such crucial security measure which falls under the realm of offensive security is continuous Vulnerability Assessment and Penetration Testing (VAPT).
In this blog, we will explore what VAPT entails, why it is essential to continuously perform VAPT, and how it strengthens cloud security.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) is a systematic approach to evaluating the security of an organization’s IT infrastructure, including its cloud-based systems and applications.
There are two primary components of VAPT; vulnerability assessment and penetration testing. Let’s take a look at each one in detail.
Vulnerability Assessment
This process involves identifying and quantifying vulnerabilities in a system or network. It aims to detect weaknesses that could potentially be exploited by attackers, such as misconfigurations, outdated software, weak access controls, or unpatched vulnerabilities. Vulnerability assessment tools and techniques, such as automated scans and manual inspections, help identify these weaknesses.
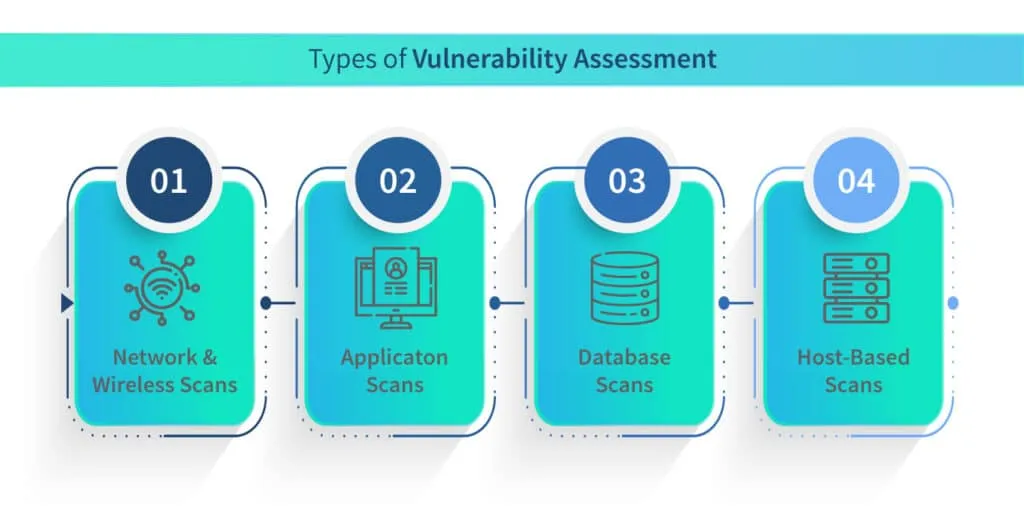
Penetration Testing
Also known as ethical hacking, penetration testing simulates real-world attacks on a system to identify vulnerabilities and assess the effectiveness of security controls. Penetration testers employ various techniques to exploit weaknesses, gain unauthorized access, and provide insights into the system’s resilience against potential threats.
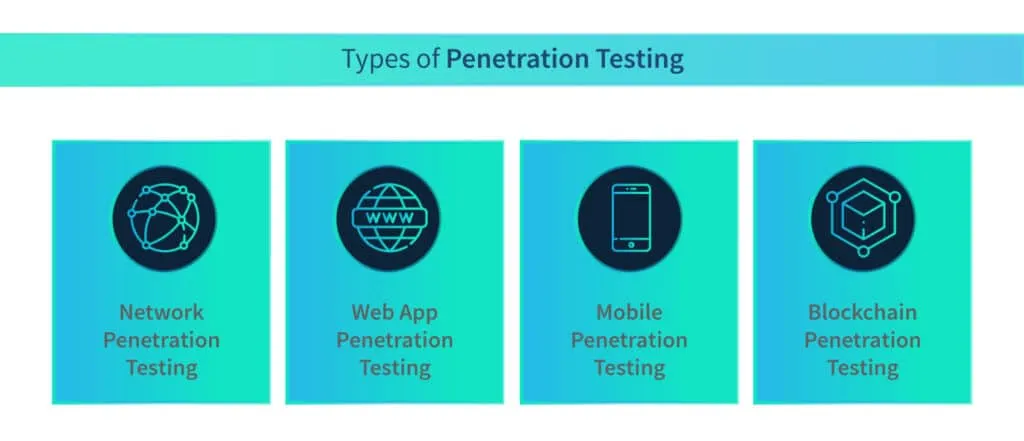
Why is Continuous VAPT necessary to strengthen cloud security?
1. Evolving Threat Landscape
Cyber threats are constantly evolving, with new attack vectors and sophisticated techniques emerging regularly. Relying on a one-time security assessment is no longer sufficient to safeguard cloud environments. Continuous VAPT ensures ongoing visibility into security vulnerabilities and provides proactive measures to mitigate risks in a rapidly changing threat landscape.
2. Timely Detection and Response:
Cloud environments are dynamic, with frequent changes in configurations, software updates, and new application deployments. These changes can introduce new vulnerabilities or inadvertently weaken existing security measures. Regular VAPT enables organizations to detect vulnerabilities in real-time, allowing for prompt remediation before attackers can exploit them.
3. Compliance Requirements
Many industries and regulatory frameworks mandate regular security assessments and penetration testing to ensure compliance. Continuous VAPT helps organizations meet these requirements and provides evidence of their commitment to maintaining a robust security posture. Failure to comply with such regulations may result in severe financial penalties and reputational damage.
4. Third-Party Risks
Cloud-native organizations often rely on various third-party components, such as APIs, frameworks, and libraries. These dependencies can introduce vulnerabilities that are beyond an organization’s direct control. Continuous VAPT helps identify potential risks arising from third-party integrations and allows organizations to work collaboratively with vendors to address them.
How to effectively use Vulnerability Assessment and Pentesting to strengthen cloud security?
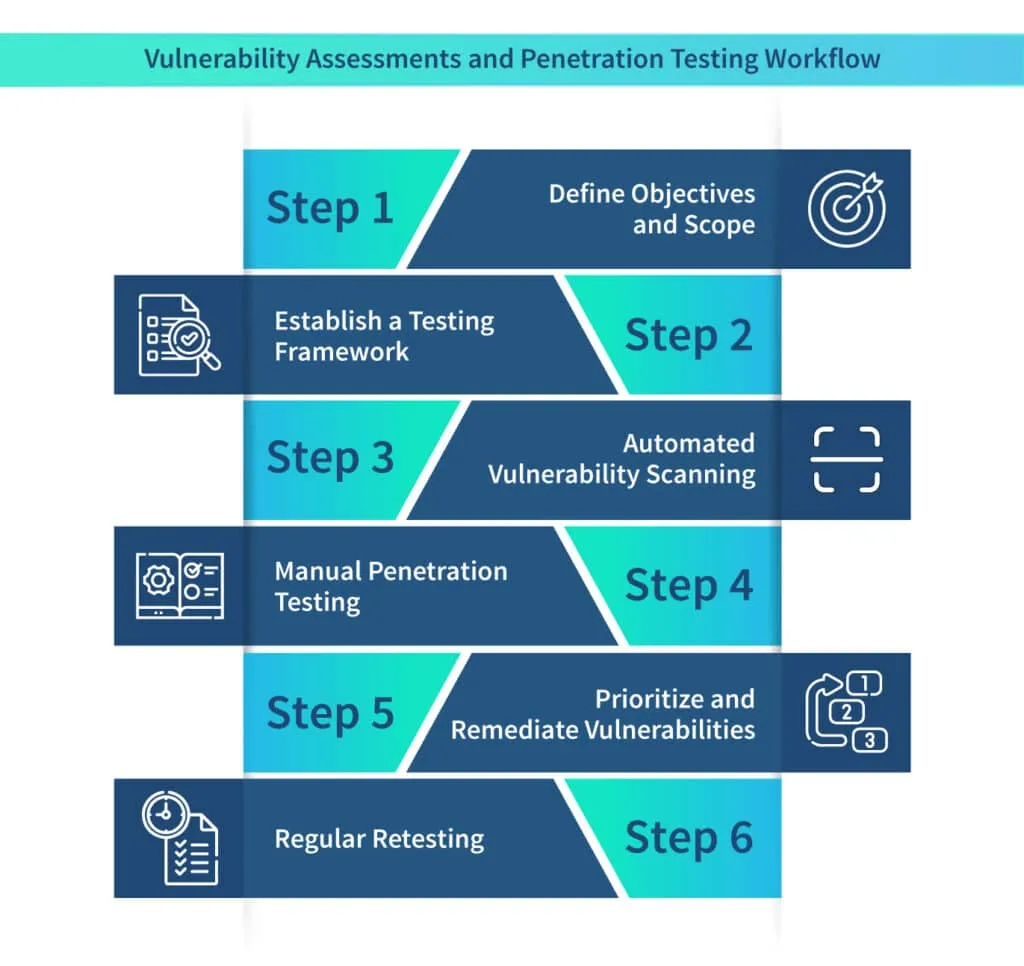
Step 1: Define Objectives and Scope: Before initiating VAPT, organizations should clearly define their objectives, including the systems and applications to be tested. A well-defined scope ensures that all critical components are thoroughly evaluated, minimizing any blind spots.
Step 2: Establish a Testing Framework: Developing a comprehensive testing framework helps ensure consistency and repeatability in VAPT activities. This framework should include guidelines for vulnerability scanning and penetration testing
Step 3: Automated Vulnerability Scanning: Automated vulnerability scanning tools play a vital role in continuously monitoring cloud environments. These tools can identify known vulnerabilities, misconfigurations, and weaknesses in software versions, providing organizations with an initial assessment of their security posture.
Step 4: Manual Penetration Testing: While automated tools provide valuable insights, manual penetration testing is crucial to simulate real-world attacks and identify complex vulnerabilities that may go undetected by automated scans. Skilled penetration testers employ their expertise to explore different attack vectors and test the effectiveness of security controls.
Step 5: Prioritize and Remediate Vulnerabilities: After performing VAPT, organizations must prioritize vulnerabilities based on their severity and potential impact. This allows for the efficient allocation of resources for remediation efforts. Promptly addressing vulnerabilities and tracking the remediation progress is vital to maintaining a strong security posture.
Step 6: Regular Retesting: As cloud environments evolve, it is essential to conduct regular retesting to validate the effectiveness of remediation efforts and identify new vulnerabilities that may arise due to system changes. This iterative process helps organizations stay ahead of potential threats and maintain continuous improvements in their security posture.
Final thoughts
In an era where cyber threats are constantly evolving, continuous Vulnerability Assessment and Penetration Testing (VAPT) is no longer an option but a necessity to strengthen cloud security.
By following a structured approach and leveraging both automated vulnerability scanning and manual penetration testing, organizations can confidently navigate the cloud landscape and safeguard their critical assets.
Scrut is enabling organizations to perform continuous VAPT scans without adding any additional burden to their plate. As experts in application security and compliance automation services, we’re placing organizations at the forefront of defining cloud security.
To know more about our services and how it can help you strengthen your security posture, talk to us today.



















