The Unified Compliance Framework Vs. The Secure Controls Framework: What's Right For Your Organization?

The Unified Compliance Framework is a comprehensive framework that consolidates multiple regulatory requirements into a single set of controls. It provides a harmonized approach to compliance and simplifies the management of multiple compliance obligations. On the other hand, the Secure Controls Framework is a security-focused framework that provides a structured approach to implementing security controls. It offers a comprehensive set of controls organized into domains and guides security risk management.
So, which of these frameworks is suitable for your organization? Here's a basic overview of both frameworks.
What is Unified Compliance Framework?
A Unified Compliance Framework (UCF) is a large database of interconnected controls that enables compliance with multiple regulations and frameworks without duplicating control and test efforts. The UCF was created to streamline certification processes and reduce the time necessary for compliance rules. It is a fully automated process that handles end-to-end security, compliance, auditing, and risk management requirements management. A UCF is a complete way to manage a company's compliance requirements. It provides a framework for integrating different regulatory requirements into a single system, improving compliance management, and avoiding duplication of effort. Using a UCF, organizations may manage their compliance requirements more efficiently and effectively while ensuring they meet their legal and regulatory duties. The UCF covers various industries, including financial, healthcare, and technology, and encompasses GDPR, HIPAA, and PCI DSS regulations. The UCF implementation process entails mapping an organization's existing controls to the framework, detecting gaps, and adding additional controls as needed.
What is the Secure Controls Framework?
The Secure Controls Framework (SCF) is a collection of best practices controls encompassing various frameworks, rules, and standards, including the NIST CSF, ISO 27001, GDPR, and others. The SCF's purpose is to give a free solution to enterprises that addresses cybersecurity and privacy control recommendations to satisfy the operational demands of organizations of any size, industry, or country of origin. The SCF includes a risk-based approach to security, enabling organizations to prioritize and address their most critical security risks. It emphasizes identifying, assessing, and managing risks to protect sensitive data and ensure systems and information confidentiality, integrity, and availability. While the SCF focuses largely on security controls, it also considers relevant legal requirements, assisting organizations in mapping security controls to compliance obligations and ensuring that security measures are in accordance with applicable rules.
Choosing the Right Framework
Consider the following aspects when deciding which framework is best for your organization:
- Compliance requirements: The UCF encompasses many regulations, standards, and best practices, including international, federal, state, and industry-specific requirements. If your organization is required to comply with several rules or industry-specific criteria, the UCF's comprehensive coverage and control consolidation may be beneficial.
- Security focus: If strengthening your organization's security posture and managing security risks is your primary focus, the SCF's comprehensive security controls and risk management approach may be a better fit. It provides detailed guidelines for implementing security controls and managing security risks.
- Regulatory alignment: Both frameworks can assist your organization in aligning with relevant requirements, but the UCF is specifically built for compliance management and mapping controls across different frameworks.
- Customization needs: Determine whether you require a framework for greater flexibility in customizing controls based on your organization's specific needs and risk profile. The SCF is a free tool that organisations can use immediately to solve their cybersecurity and privacy control advice needs. This enables you to manage your demands immediately rather than waiting months to secure a budget. It provides a flexible framework for tailoring controls based on your security objectives and regulatory requirements.
The UCF can provide a comprehensive approach to compliance management, whereas the SCF can provide detailed security controls and risk management assistance. If your company is large and has other compliance responsibilities besides cybersecurity and data privacy, then the UCF is probably a better option. If your organization does not require extra compliance framework criteria, then the SCF provides everything you need to integrate governance, risk, and compliance in a consistent set of controls.
Implement SCF with Scrut
Scrut's platform allows organizations of all sizes to implement the SCF more efficiently with control mappings, automated evidence collection, third-party risk management workflows, etc.
Scrut smartGRC simplifies compliance by removing time-consuming manual procedures and keeping you updated on the development of your GRC program.
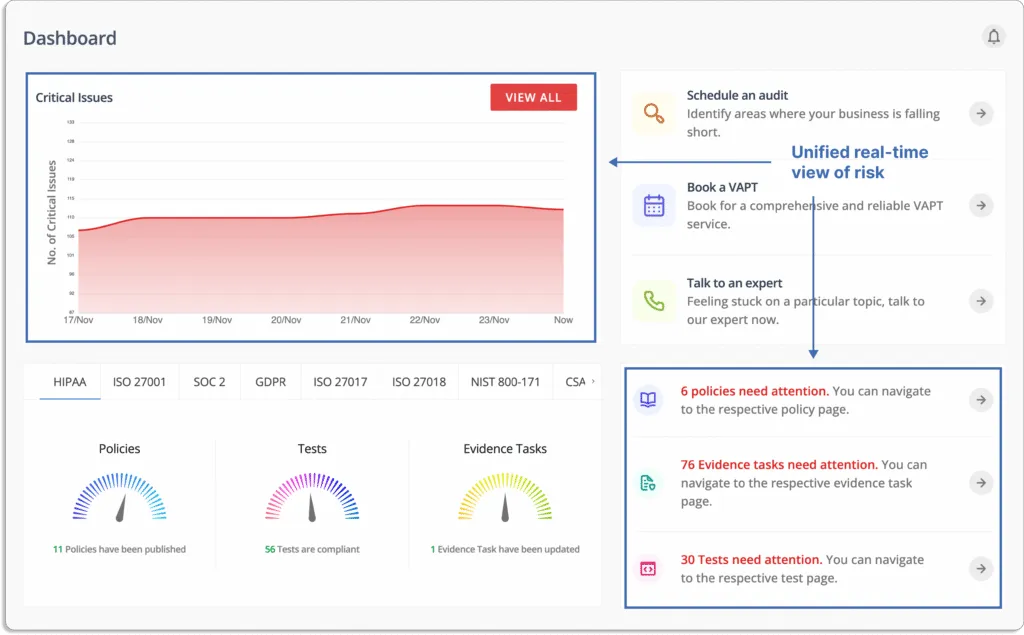
Scrut smartGRC platform assists users in compiling the documents required to pass the audit and gain certification by providing users with prebuilt policies and controls suited to various frameworks. With a library of 50+ policies designed and vetted by our in-house information security specialists, you can build your compliance program in minutes.
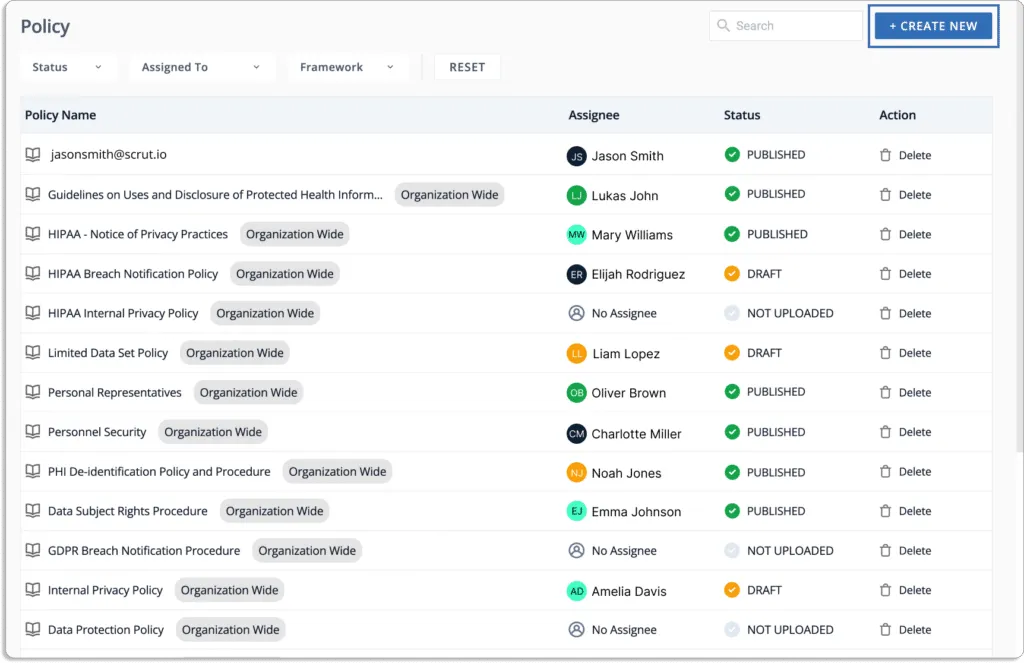
You can use an inline editor to customize and update these rules to meet your organization's needs.
The software provides continuous cloud security monitoring to help users stay compliant while proactively securing their data. It constantly monitors over 200 cloud controls. This allows users to address issues before malicious agents can exploit vulnerabilities.
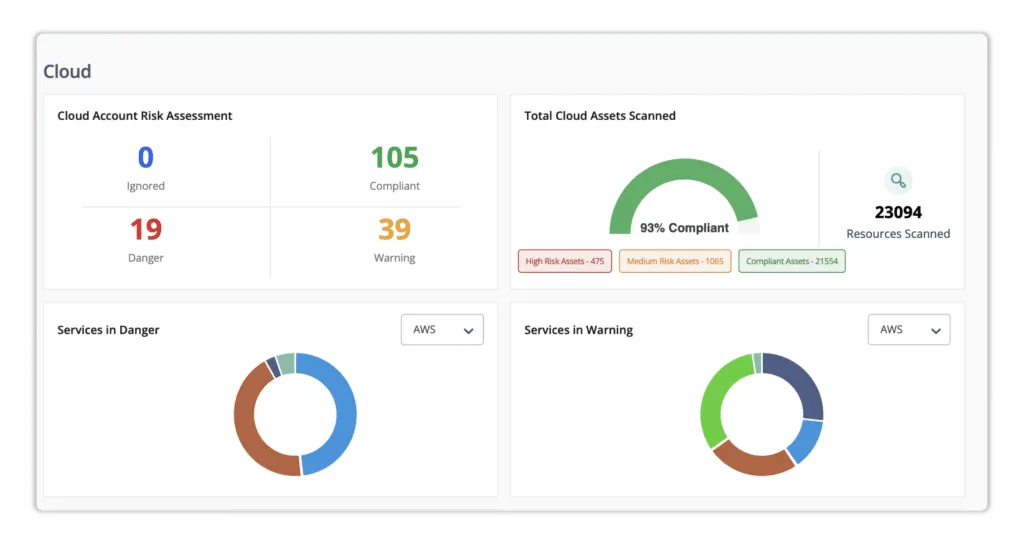
Scrut risk management allows users to identify company hazards by navigating through a pre-built library of controls. You may discover high-risk areas and better understand your risk posture by combining data with built-in, industry-standard scoring algorithms and expert-recommended ranks.
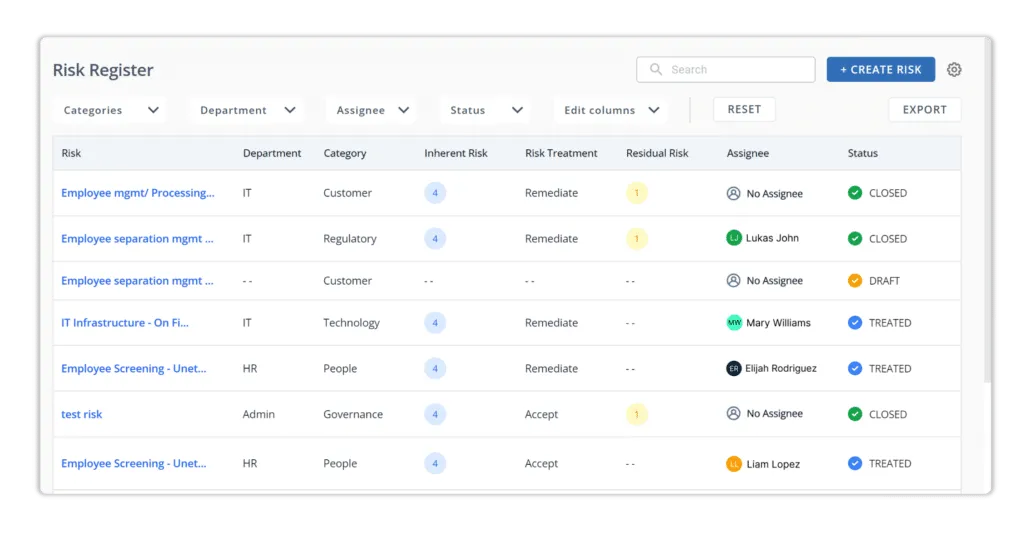
The solution interacts with your landscape to automate evidence collecting and lets users create, assign, and manage compliance assignments. The built-in mapping to all information security frameworks allows you to manage your compliance posture quickly. It delivers a single-window experience for checking compliance with numerous information security frameworks. The Scrut platform supports the following frameworks, among others: SOC 2, SOC 3, ISO 27001, ISO 27701, ISO 27017, ISO 27018, ISO 22301, ISO 20000-1, GDPR, HIPAA, FedRamp, CMMC, CCPA, PCI DSS, CSA Star, CMMI - DEV, GLB, and NIST 800 171.
Scrut uses pre-built modules to automate employee security awareness training. This equips staff with all they need to identify potential security dangers and avoid blunders like clicking on phishing emails. It keeps you informed of the general state of the training programs. As an administrator, you are always aware of the general characteristics of your employees' training programs. To check that they have read the policies, you can give quizzes.
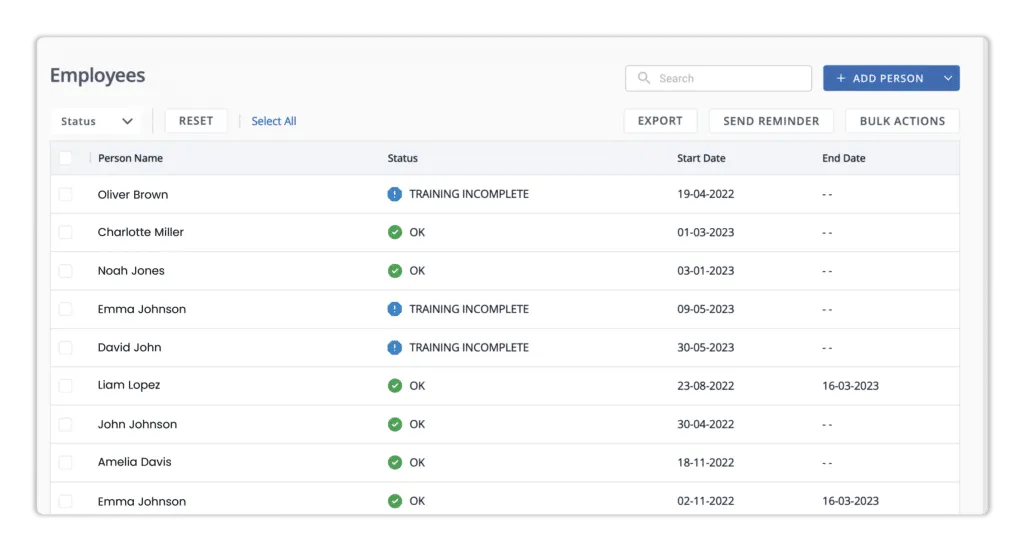
The platform assists users in identifying, monitoring, and managing risks associated with vendors. This allows users to determine whether a provider fits their compliance needs. It simplifies your vendor compliance check with security questions. You can create your custom questionnaire or use pre-built questions. You can also invite your vendors to the site to complete the security surveys.
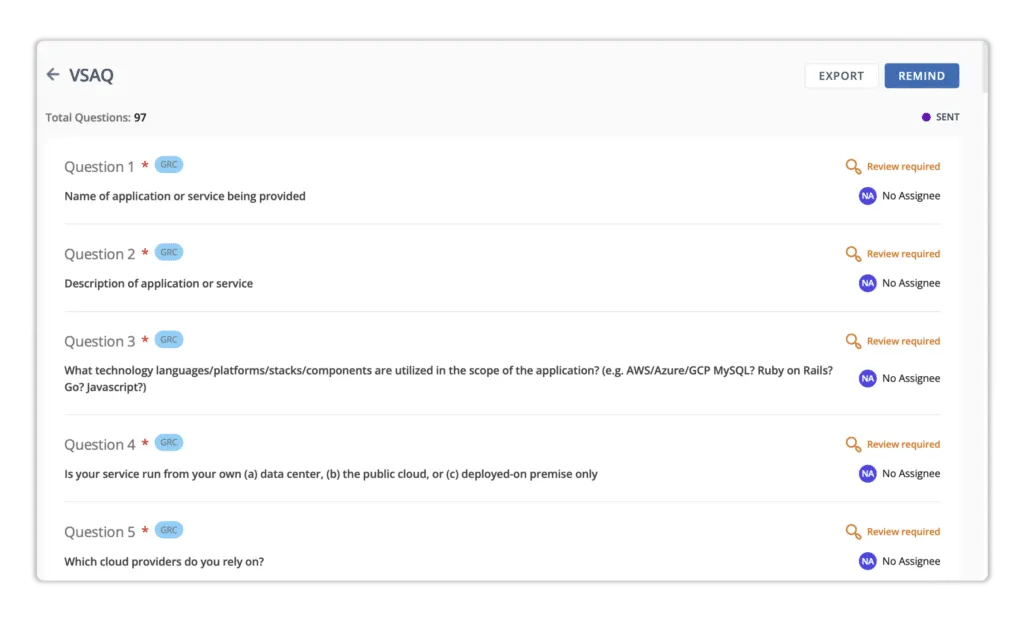
Scrut interacts with over 70 tools (AWS, GCP, Okta, Datadog, JAMF, Jira, and others). It enables you to automate more than 70% of evidence-collection tasks while decreasing manual tasks. The tool puts all evidence-related activities in one place, making it easy for the auditor to sift through them. This also lowers the need to manage many evidence sheets or documents.
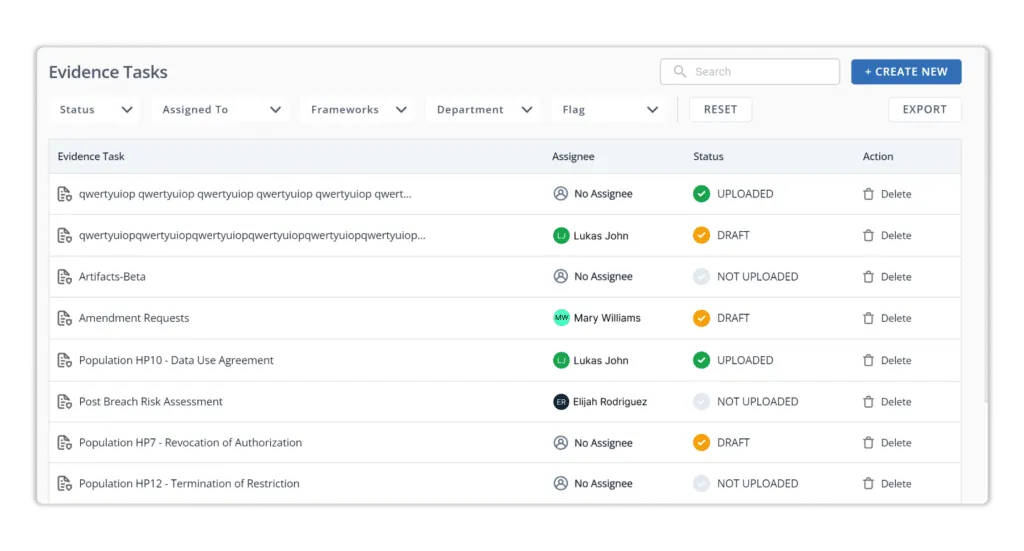
Scrut provides consumers with specific communication channels (such as Slack, Call, Whatsapp, and so on). The customer success team would collaborate with you to identify and resolve outstanding issues. Schedule a demo with Scrut to learn how our solution assists you in monitoring your controls for SOC 2, GDPR, CCPA, HIPAA, and other regulations in one location.


















