Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Demystifying IT Risk Management: A Comprehensive Guide
Last updated on
April 17, 2025
9
min. read

In today’s rapidly evolving technological landscape, information technology (IT) has become the backbone of almost every organization. With the growing dependence on digital infrastructure, businesses face numerous risks that can significantly impact their operations, reputation, and bottom line. To thrive in this digital age, organizations must effectively manage and mitigate these risks.
This is where IT risk management comes into play. In our last article, we learned how to create a risk register. In this one, we will go a step further to learn all about the art of risk management.
IT risk management is the process of identifying, assessing, and prioritizing risks associated with an organization’s IT systems, infrastructure, and operations. It involves developing strategies and implementing measures to minimize the negative impact of potential threats while capitalizing on opportunities that arise.
By proactively managing IT risks, organizations can enhance their ability to make informed decisions, protect sensitive data, ensure business continuity, and maintain a competitive advantage. This comprehensive guide will list the IT risks faced by an organization as well as the best practices an organization should adopt to build an effective IT risk management program.
Understanding IT risk management
IT risk management is an unavoidable process in today’s business environment. It involves the systematic approach of analyzing potential threats, vulnerabilities, and potential impacts to determine the likelihood and consequences of adverse cyber events that may occur.
The primary objective of IT risk management is to minimize the negative impact of IT-related risks on an organization’s operations, assets, reputation, and overall business objectives. By effectively managing IT risks, organizations can enhance their ability to make informed decisions, protect sensitive data, ensure business continuity, and maintain a competitive advantage in an increasingly digital environment.
Key components of IT risk management
IT risk management is an unceasing process that an organization must undertake to protect its IT and non-IT assets. An attack on the IT asset, i.e., a cyber attack, can take a toll on the business of the organization. It has been observed that data breaches cost businesses an average of $4.35 million in 2022 (AAG). The high cost of data breaches accentuates the need for IT risk management in every organization. Here are the four key components of IT risk management:
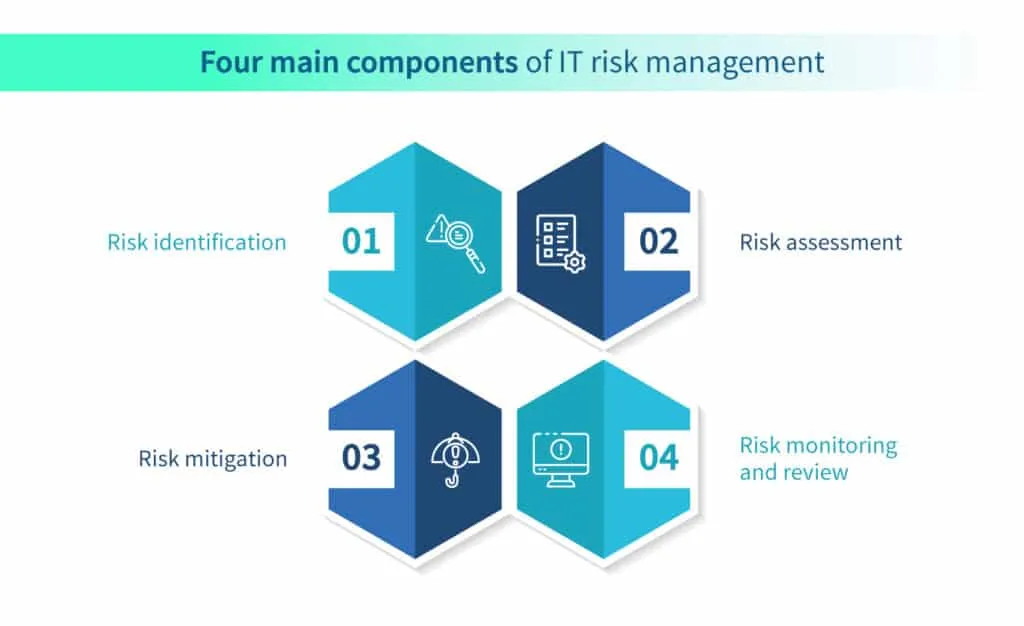
1. Risk identification
Risk identification involves systematically identifying and recognizing potential risks associated with IT systems, infrastructure, and operations. It requires a comprehensive understanding of the organization’s IT environment, including hardware, software, networks, data, and processes.
Risks can be identified through various methods such as conducting risk assessments, vulnerability scanning, threat intelligence analysis, and engaging with stakeholders to gather insights and perspectives.
There are different types of IT risks to be identified at this stage:
- Vulnerabilities – weaknesses or gaps in IT systems
- Threats – potential events that can exploit vulnerabilities
- Potential impact on confidentiality, integrity, and availability (CIA) of IT assets.
The identified risks should be well-documented and categorized to facilitate further analysis.
2. Risk assessment
Once risks are identified, a thorough risk assessment should be conducted to evaluate their likelihood of occurrence and potential impact. This step involves analyzing the probability of a risk event happening and assessing the magnitude of its consequences. Risk assessment can be performed using qualitative, quantitative, or semi-quantitative methods.
- Qualitative risk assessment focuses on descriptive measures such as likelihood ratings (low, medium, high) and impact scales (minor, moderate, severe) to prioritize risks.
- Quantitative risk assessment involves assigning numerical values to likelihood and impact factors and calculating risk scores or probabilities.
- Semi-quantitative methods combine elements of both approaches.
Risk assessment enables organizations to prioritize risks based on their significance and determine the appropriate level of attention and resources required for mitigation.
3. Risk mitigation
The third component of the IT risk management framework is risk mitigation. It involves developing and implementing strategies to reduce the likelihood and impact of identified risks. This component aims to proactively address risks and strengthen the organization’s IT security posture. Risk mitigation measures can vary depending on the nature of the risk and the organization’s specific circumstances.
Mitigation strategies may include implementing security controls such as firewalls, antivirus software, intrusion detection systems, and access controls to protect IT assets. Regular patching and updates, encryption, and secure coding practices can also be part of the risk mitigation plan. Establishing incident response plans, conducting security awareness training for employees, and performing regular backups and data recovery testing are essential elements of risk mitigation.
It’s crucial to consider a risk-based approach that prioritizes mitigation efforts based on the severity and likelihood of risks. This ensures that resources are allocated effectively to address the most critical risks first.
4. Risk monitoring and review
Ongoing monitoring and review are critical components of IT risk management. Risk monitoring involves continuously assessing the effectiveness of risk mitigation measures, detecting emerging risks, and evaluating changes in the IT environment that may impact the risk landscape.
Regular reviews and assessments should be conducted to validate the effectiveness of risk mitigation strategies, reassess risks, and identify any new risks that may have emerged. This can involve periodic risk assessments, security audits, vulnerability scans, penetration testing, and monitoring key risk indicators (KRIs).

Risk monitoring and review activities provide organizations with insights into the evolving risk landscape and enable them to make informed decisions and adjustments to their risk management approach. It ensures that the risk management strategy remains aligned with organizational objectives and adapts to changes in technology, regulations, and the threat landscape.
By diligently following these four components of IT risk management, organizations can strengthen their resilience to potential risks, protect their IT assets, and maintain the confidentiality, integrity, and availability of critical information systems.
Best practices for effective risk management
By proactively identifying, assessing, and mitigating risks, businesses can navigate uncertainties and seize opportunities. Effective risk management is the key to the security of the organization. Some of the best practices for effective risk management are mentioned below.
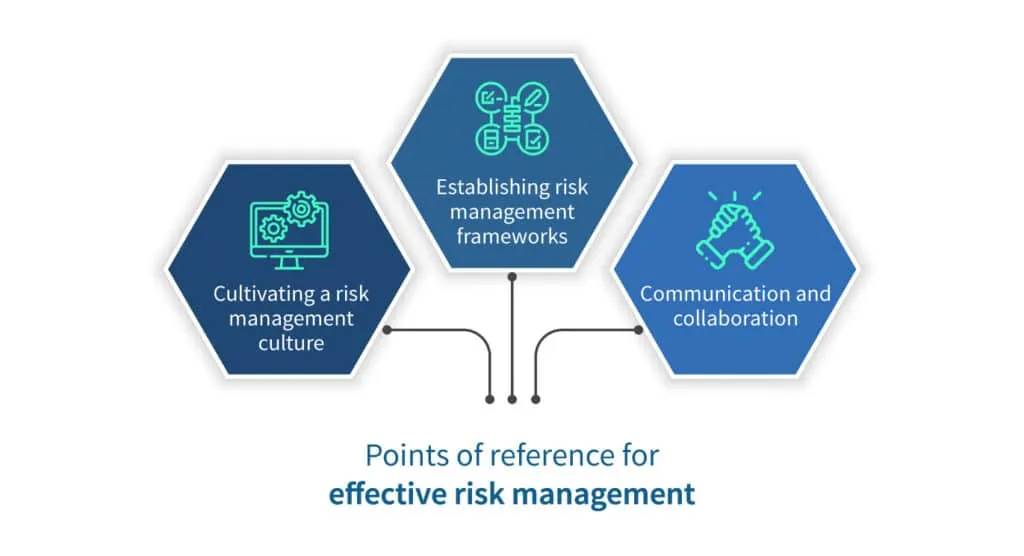
Cultivating a risk management culture
Creating a risk-aware culture is crucial for successful risk management. Encourage open communication, foster accountability, and promote risk awareness among all employees. When risk management becomes ingrained in the organization’s DNA, employees become active participants in identifying and mitigating risks.
Establishing risk management frameworks
Developing a robust risk management framework is essential for consistent and effective risk mitigation. Establish clear roles and responsibilities, define risk appetite and tolerance levels, and integrate risk management into organizational processes. By setting up a structured framework, organizations can ensure that risk management becomes an integral part of decision-making at all levels.
Communication and collaboration
Effective communication and collaboration are vital for successful risk management. Encourage open dialogue and knowledge sharing among different teams and departments. By fostering collaboration, organizations can leverage diverse perspectives and expertise, resulting in better risk identification and more robust mitigation strategies.
How to build an effective IT risk management program/framework?
Building an effective risk management program is critical to the success of an organization. Although we will discuss this topic in more detail in our upcoming article, the four steps for building a successful IT risk management plan have been listed here.
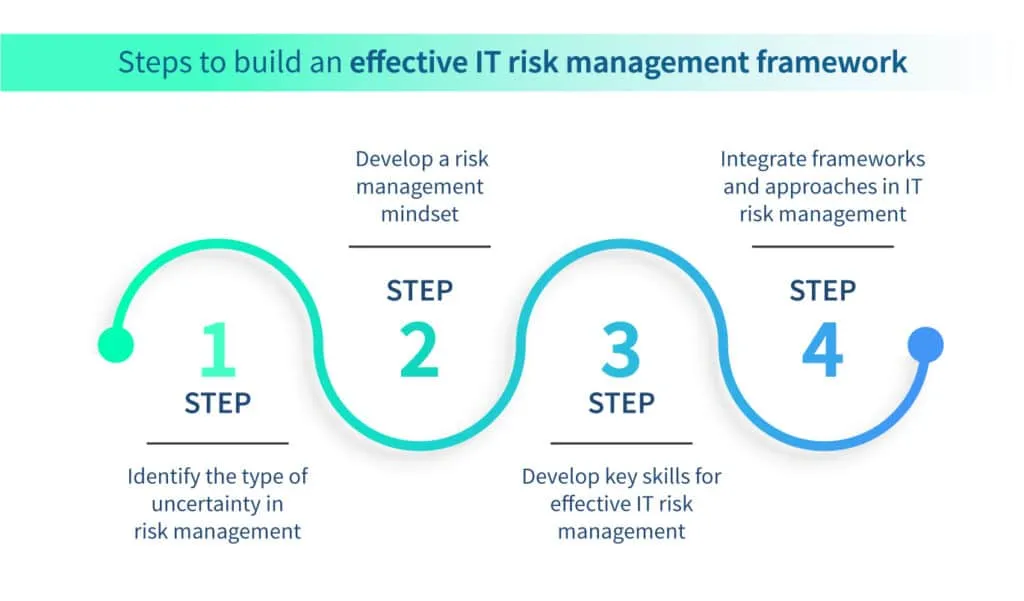
Step 1: Identify the type of uncertainty in risk management
Before developing an IT risk management program, it is crucial to identify the specific uncertainties and risks that the organization faces. This involves conducting a thorough assessment of the IT environment, including hardware, software, networks, data, and third-party dependencies. It also requires considering external factors such as regulatory compliance, emerging technologies, and cybersecurity threats. By understanding the specific uncertainties and risks, organizations can tailor their risk management program to address these unique challenges effectively.
Step 2: Develop a risk management mindset
Building a risk management mindset across the organization is essential for the successful implementation of an IT risk management program. This involves creating awareness about the importance of risk management, fostering a culture that encourages risk identification and reporting, and promoting accountability at all levels. It also requires instilling a mindset that views risk as an opportunity for improvement rather than solely focusing on negative consequences. By developing a risk management mindset, employees become active participants in identifying and managing IT risks.
Step 3: Develop key skills for effective IT risk management
Equipping employees with the necessary skills is crucial for the implementation of an effective IT risk management program. This includes developing skills such as critical thinking, data analysis, problem-solving, and communication. Employees should understand risk assessment methodologies, be knowledgeable about IT systems and security principles, and possess the ability to collaborate effectively. Ongoing training and professional development programs can help individuals develop and enhance these skills, ensuring the success of the risk management program.
Step 4: Integrate frameworks and approaches in IT risk management
To build an effective IT risk management program, organizations should integrate established frameworks and approaches. These frameworks provide a structured and systematic approach to risk management, ensuring consistency and comprehensiveness. Some commonly used frameworks include ISO 27001, NIST Cybersecurity Framework, and COBIT. Organizations should adapt these frameworks to their specific needs and align them with industry best practices. Additionally, leveraging risk management software and tools can streamline the process, automate risk assessments, and facilitate monitoring and reporting.
In a nutshell
In conclusion, navigating the unknown terrain of IT risk management requires a systematic and proactive approach. By developing a risk management mindset, cultivating key skills, and integrating frameworks and approaches, organizations can build an effective IT risk management program. This program involves identifying and assessing risks, implementing mitigation strategies, and continuously monitoring and reviewing the risk landscape.
By following best practices such as fostering a risk-aware culture, establishing clear frameworks, and promoting communication and collaboration, organizations can effectively mitigate risks and safeguard their IT assets. The ability to effectively manage IT risks is vital in today’s digital age, where organizations face evolving cybersecurity threats and increasing reliance on technology.
FAQs
What is IT risk management?
IT risk management is the process of identifying, assessing, and prioritizing risks associated with an organization’s IT systems, infrastructure, and operations. It involves developing strategies and implementing measures to minimize the negative impact of potential threats while capitalizing on opportunities that arise.
Why is IT risk management important?
IT risk management is essential because it allows organizations to protect their IT assets, make informed decisions, ensure business continuity, and maintain a competitive advantage in an increasingly digital environment. By effectively managing IT risks, businesses can mitigate potential financial losses, reputational damage, and regulatory non-compliance.
What are the key components of IT risk management?
The key components of IT risk management include:
1. Risk identification: Systematically identifying and recognizing potential risks associated with IT systems, infrastructure, and operations.
2. Risk assessment: Evaluating the likelihood and potential impact of identified risks through qualitative or quantitative methods.
3. Risk mitigation: Developing and implementing strategies to reduce the likelihood and impact of identified risks, such as implementing security controls, conducting employee training, and establishing incident response plans.
4. Risk monitoring and review: Ongoing assessment of risk mitigation measures, detection of emerging risks, and evaluation of changes in the IT environment that may impact the risk landscape.
Table of contents