SOC 2 Compliance Timeline: How Long Does It Take to Achieve Compliance?

SOC 2 compliance is, no doubt, vital for safeguarding information and building customer loyalty, but it can be burdensome. The process demands meticulous planning, rigorous assessments, and ongoing efforts to align internal controls with the stringent trust services criteria. If your organization handles sensitive data, achieving SOC 2 compliance is vital to safeguarding information and building customer trust.
In this blog, we'll delve into the factors that influence the duration of SOC 2 compliance, provide a typical timeline for the process, and share valuable strategies to expedite your journey.
But first, let's take a look at what SOC 2 compliance is.
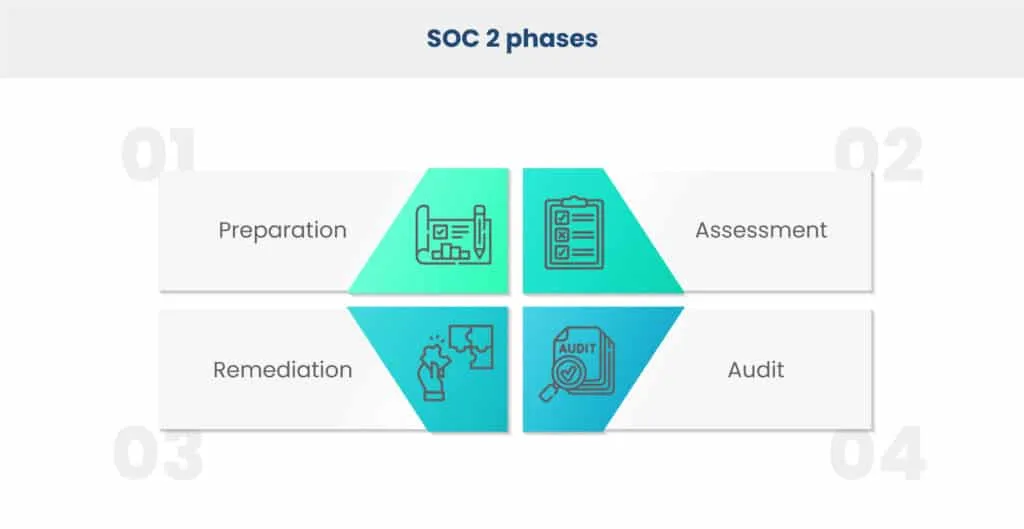
Overview of Typical SOC 2 Phases
The compliance process involves several key phases, such as preparation, assessment, remediation, and the final audit.While timelines for each stage can vary, the entire process usually takes between six and twelve months to complete.
SOC 2 Compliance Timeline
Let's take a look at the steps involved in a SOC 2 compliance process and the time each step takes in a little more detail. The timelines provided are approximate and may vary based on your organization's size, complexity, and readiness level.
Step 1: Assess Your Organization's Needs and Scope (Timeline: 1-2 weeks)
Identify the scope of the SOC 2 compliance assessment, including the systems, processes, and data to be evaluated.
Determine which of the five core principles (security, availability, processing integrity, confidentiality, and privacy) are relevant to your organization. This initial phase sets the foundation for the entire compliance process and involves several crucial activities.
Let's take a look at some of them:
- Define Compliance Objectives: Clearly articulate the objectives you aim to achieve through SOC 2 compliance. Understand the specific reasons behind seeking compliance and how it aligns with your organization's overall goals and values.
- Identify Systems and Data: Take stock of the systems, applications, and data that are subject to the SOC 2 assessment. This includes both internal and external-facing systems that handle customer data or support critical operations.
- Select Relevant SOC 2 Principles: Determine which of the five core SOC 2 principles (security, availability, processing integrity, confidentiality, and privacy) are applicable to your organization's business operations and customer data.
- Assess Compliance Readiness: Evaluate your organization's current state of compliance readiness. Identify existing controls and practices that align with SOC 2 principles and pinpoint potential gaps that require attention.
- Establish Compliance Scope: Define the scope of the SOC 2 assessment to focus efforts and resources effectively. This involves deciding which business units, departments, or processes fall under the compliance evaluation.
- Engage Key Stakeholders: Collaboration among key stakeholders is vital during this step. Engage leaders from IT, legal, security, and relevant departments to gain a comprehensive understanding of compliance requirements and potential challenges.
- Review Legal and Regulatory Requirements: Familiarize yourself with the legal and regulatory obligations your organization must meet in addition to SOC 2. This ensures that compliance efforts address all relevant standards.
- Plan the Compliance Journey: Based on the assessment results, create a detailed SOC 2 project plan outlining the timeline, resource allocation, and responsibilities for each phase of the compliance process.
By conducting a thorough assessment, you gain a clear understanding of your organization's compliance needs and set realistic expectations for the entire SOC 2 compliance journey.
This foundational step provides crucial insights that guide subsequent actions. This helps ensure that your organization is well-prepared to embark on a successful SOC 2 compliance endeavor.
Step 2: Conduct a Risk Assessment (Timeline: 2-4 weeks)
After defining the scope and objectives in Step 1, the next crucial phase in the SOC 2 compliance journey is conducting a thorough risk assessment.
The risk assessment process helps identify potential vulnerabilities, threats, and risks that could impact your organization's ability to achieve SOC 2 compliance.
Here's a detailed look at the activities involved:
- Identify Data and Asset Inventory: Begin by cataloging all critical data assets, systems, applications, and IT infrastructure that play a role in processing or storing customer data. This inventory serves as a foundation for risk identification.
- Analyze Threat Sources: Assess potential threat sources, such as cyberattacks, data breaches, internal security incidents, natural disasters, and operational disruptions. Understanding these threat vectors helps prioritize risk management efforts.
- Evaluate Vulnerabilities: Identify weaknesses and vulnerabilities within your organization's IT infrastructure, processes, and controls. These vulnerabilities can expose sensitive data to potential threats and call for prompt mitigation.
- Assess Impact and Likelihood: Evaluate the potential impact and likelihood of risks occurring. Determine the potential consequences of a risk event, such as financial losses, reputational damage, or legal repercussions.
- Assign Risk Levels: Assign risk levels to each identified risk based on its impact and likelihood. Categorize risks as high, medium, or low to prioritize subsequent risk mitigation efforts.
- Develop Risk Mitigation Strategies: Develop risk mitigation strategies tailored to address each identified risk. These strategies may include implementing additional security controls, enhancing data encryption, or implementing redundancies in critical systems.
- Prioritize Risk Remediation: Based on the risk levels and potential impact, prioritize risk remediation efforts. Focus on addressing high-risk areas first to minimize the organization's exposure to significant threats.
- Monitor and Review: Implement continuous monitoring and periodic reviews of the risk landscape to ensure that emerging threats are promptly addressed and that risk mitigation strategies remain effective.
By understanding vulnerabilities and assessing risks, you can develop targeted strategies to mitigate those risks, strengthen internal controls, and ensure a robust foundation for SOC 2 compliance.
This proactive approach reduces the likelihood of security incidents and enhances your organization's overall risk management posture, bolstering your credibility and trust with clients and stakeholders.
Step 3: Establish Internal Controls (Timeline: 4-6 weeks)
Establishing robust internal controls is a critical step in achieving SOC 2 compliance.
Internal controls are the policies, procedures, and practices put in place to safeguard sensitive data, maintain operational integrity, and ensure compliance with SOC 2 principles.
Ensure that you implement suitable controls and develop and document policies and procedures for each control. Update your policies, as it simplifies and streamlines the auditor's work.
- Identify Key Controls: Begin by identifying the key controls relevant to the selected SOC 2 principles. These controls will serve as the foundation for your organization's data security and risk management efforts.
- Develop Policies and Procedures: Once you have identified the key controls, develop clear and comprehensive policies and procedures outlining how these controls will be implemented and maintained. These documents will serve as a guide for employees and stakeholders, ensuring consistency and adherence to SOC 2 requirements.
- Train Employees: Proper training is essential to ensure that all employees understand their roles and responsibilities in adhering to the established internal controls. Training sessions should cover data security best practices, incident response protocols, and the importance of maintaining compliance.
- Implement Access Controls: Access controls limit access to sensitive data only to authorized personnel. Implementing access controls ensures that information is accessible to the right people while safeguarding it from unauthorized users.
- Data Encryption: Encrypting data both in transit and at rest adds an extra layer of security to protect sensitive information from unauthorized access. Implement encryption measures based on industry best practices and compliance requirements.
- Incident Response Planning: Develop a comprehensive incident response plan to address potential security incidents effectively. The plan should include steps for identifying, containing, and mitigating security breaches to minimize their impact on the organization.
- Regular Monitoring and Auditing: Regularly monitor and audit internal controls to ensure they remain effective and compliant. Audits help identify any deviations from established controls, allowing for prompt corrective action.
- Continuous Improvement: Internal controls should be subject to continuous improvement based on emerging threats, technological advancements, and changes in business processes. Regularly review and update controls to address new risks and challenges.
By establishing robust internal controls, your organization can proactively protect sensitive data, demonstrate compliance with SOC 2 principles, and foster a culture of security and accountability.
These controls form the backbone of your SOC 2 compliance journey, setting the stage for a successful SOC audit and providing assurance of data protection to clients and stakeholders.
If controls are insufficient or not present to demonstrate compliance with a selected Trust Service Criteria (TSC), you will have to take remedial actions to demonstrate compliance.
Step 4: Conduct Readiness Assessments (Timeline: 2-4 weeks)
Conducting readiness assessments is a pivotal step in preparing your organization for the official SOC 2 audit.
These assessments involve conducting mock SOC audits or evaluations of your internal controls, processes, and documentation. The goal is to identify any gaps or deficiencies that you need to address before the official audit.
Here's a more detailed explanation of this critical step:
- Engage Internal and External Auditors: Collaborate with internal audit teams or engage external auditors to conduct readiness assessments. These auditors will play a crucial role in objectively evaluating your organization's compliance readiness.
- Evaluate Internal Controls: Assess the effectiveness of your organization's internal controls in meeting the selected SOC 2 principles. The evaluation should cover areas such as data security, access controls, change management, incident response, and data privacy.
- Identify Compliance Gaps: Through the assessment process, identify any gaps or weaknesses in your current controls and practices that could hinder SOC 2 compliance. Pinpoint areas that require improvement or additional measures.
- Review Policies and Procedures: Evaluate the adequacy and comprehensiveness of your organization's policies and procedures related to data security and compliance. Ensure that they align with SOC 2 requirements and industry best practices.
- Conduct Interviews and Testing: Conduct interviews with key personnel and perform testing of selected controls to validate their effectiveness. This process helps uncover potential compliance issues and provides valuable insights for improvement.
This step builds confidence in your organization's commitment to data security and compliance. This sets the stage for a successful SOC 2 audit and reinforces trust with clients and stakeholders.
Step 5: Remediate and Improve (Timeline: Ongoing)
Use the results of the readiness assessments to drive continuous improvement in your organization's compliance efforts. Regularly review and update internal controls, policies, and procedures to align with emerging risks and industry standards.
Based on the assessment findings, develop remediation plans to address identified gaps and deficiencies. Each plan should outline specific action items, responsibilities, and target completion dates.
Step 6: Engage a Third-Party Auditor (Timeline: 4-6 weeks)
Select a qualified and independent third-party auditor to conduct the SOC 2 audit. Discuss the audit objectives, scope, and timeline with the auditor.
Selecting an auditor is the most challenging and important step. While selecting an auditor, keep the following checklist in mind:
- Auditing firm reputation
- Experience
- Communication style
- Knowledge of tech stack
- Price
The auditor should provide you with all the tools, such as the audit checklist and work schedule.
Scrut can help you identify the 'best-fit' auditor for your requirements within a couple of days. We have a vast network of auditors with in-depth experience conducting SOC 2 audits across geographies and industries.
Step 7: Conduct the SOC 2 Audit (Timeline: 6-12 weeks)
When the above checklist is done, the auditor starts the audit. The auditor will begin gathering and examining audit evidence for the SOC 2 report.
For the uninitiated, evidence is everything that you hand over to the auditor for evaluation to prove system controls are in place to protect the data. It includes documents like spreadsheets, emails, and screenshots of access control metrics. Collecting evidence for various artifact controls across TSCs can be overwhelming.
This is the most time-consuming step in the SOC 2 compliance audit process and usually takes 6-8 weeks. However, with Scrut, you can automate 85% of evidence collection and complete the process in 2-3 weeks.
Once you've handed in the evidence, the third-party auditor evaluates your organization's compliance with the selected principles. The SOC audit includes testing controls, reviewing documentation, and conducting interviews with key personnel.
The audit process involves a substantial amount of work, often stretching over several months. However, there's a more efficient option. With Scrut, you can complete the entire audit process in just 6-8 weeks. This means you can achieve compliance without the extended timeline that traditional methods often require.
Step 8: Receive SOC 2 Report (Timeline: 2- 4 weeks)
The auditor provides a SOC 2 report, detailing the assessment's results and your organization's compliance status. Depending on the type of report (Type I or Type II), the report may cover specific dates or a period of time.
Here's a brief overview of this step:
- Auditor's Evaluation: The independent auditor evaluates your organization's internal controls, processes, and practices based on the selected SOC 2 principles.
- SOC 2 Report Types: Depending on the engagement, the auditor issues either a SOC 2 Type I or Type II report. The Type I report covers the design and implementation of controls as of a specific date, while the Type II report includes the operational effectiveness of controls over a defined period.
- Compliance Assessment: The SOC 2 report outlines the auditor's assessment of your organization's compliance status, including any identified deficiencies or areas for improvement.
- Audit Findings: The report highlights any non-compliance issues or control deficiencies discovered during the SOC audit. These findings are essential for your organization's awareness and future remediation efforts.
- Management Response: Your organization may provide a management response to address the audit findings, acknowledging corrective actions taken or explaining plans for remediation.
- Distribution of the Report: Once the SOC 2 report is finalized, the auditor will distribute copies to your organization and other relevant parties, such as customers and business partners, as requested.
- Utilization of the Report: The SOC 2 report serves as a valuable tool for your organization to demonstrate compliance with SOC 2 principles to clients and stakeholders. It enhances trust and confidence in your data security practices.
- Continuous Improvement: Use the SOC 2 report findings as a roadmap for continuous improvement. Address any identified deficiencies promptly and proactively enhance your internal controls to strengthen data security and compliance.
Receiving the SOC 2 report is a significant milestone in the compliance journey. It provides valuable insights into your organization's compliance status and helps drive ongoing efforts to maintain data security, improve controls, and meet the expectations of your clients and business partners.
Step 9: Address any Findings (Timeline: Ongoing)
Upon receiving the SOC 2 report and audit findings, the crucial next step is to address any identified deficiencies or non-compliance issues.
This ongoing process involves promptly responding to the SOC audit findings and taking corrective actions to rectify any shortcomings.
As part of the remediation efforts, your organization should:
- Prioritize Remediation: Prioritize addressing high-priority findings first to mitigate significant risks and enhance data security and compliance posture.
- Develop Corrective Action Plans: Develop comprehensive corrective action plans for each finding, outlining specific steps, responsibilities, and timelines for implementation.
- Collaborate with Stakeholders: Engage relevant stakeholders, including IT, legal, and compliance teams, to ensure a collaborative and coordinated approach to remediation.
- Monitor Progress: Regularly monitor the progress of corrective actions to track their implementation and ensure timely completion.
- Document Remediation Efforts: Thoroughly document all remediation efforts, including the steps taken and evidence of their effectiveness.
- Validate Effectiveness: Verify the effectiveness of remediation efforts through testing and validation processes.
This ongoing process of addressing SOC audit findings reinforces compliance excellence, fosters a culture of accountability, and instills confidence in clients and stakeholders that their data is being protected and managed in accordance with SOC 2 principles.
Step 10: Renewal and Ongoing Compliance (Timeline: Annually)
SOC 2 compliance is a dynamic process that requires continuous attention to ensure data security and privacy are well maintained. Plan for regular SOC 2 audits and renew your compliance annually.
Also, make sure you continuously monitor and update internal controls to adapt to changing risks and requirements. Constant monitoring will help you assess any loopholes you may have in your security controls.
SOC 2 Type 2 Process
SOC 2 Type 2 takes longer than SOC 2 Type 1. You will need to complete all the above steps mentioned in SOC 2 Type 1.
A few auditors will let you start the process from scratch, while Scrut helps you continue the process from SOC 2 Type 1 to achieve SOC 2 Type 2. This way, the process becomes much easier and less expensive.
SOC 2 Compliance Challenges and How to Overcome Them?
Navigating SOC 2 compliance can be challenging. Common hurdles include resource constraints, complex IT infrastructure, and adapting to evolving regulations.
- Resource constraints: To overcome resource constraints, collaborate closely with leadership to prioritize compliance efforts and secure adequate resources. This ensures that the necessary support and commitment are available to achieve compliance objectives effectively.
- Complex infrastructure: Streamlining processes, centralizing controls, and ensuring uniformity across all locations are crucial steps to navigate the complexities of diverse IT setups and multiple operational sites.
- Evolving Regulations: Remaining proactive in monitoring regulatory updates and promptly implementing necessary changes is essential to staying compliant with evolving requirements.
You may also learn from successful SOC 2 compliance stories where organizations achieved timely compliance through effective planning, collaboration, and a proactive approach. By examining real-life examples, you can gain valuable insights into best practices and potential pitfalls to avoid.
Factors Influencing SOC 2 Compliance Duration
- Organization Size, Complexity, and Readiness
Larger and more complex organizations may require additional time to implement controls and gather evidence. Your organization's readiness level at the start of the process also influences the timeline.
- Internal Resources and Budget
Adequate resources and budget allocation is essential for a smooth compliance journey. A committed team and funding help speed up the process.
- Third-Party Vendors' Willingness To Cooperate
If your organization relies on third-party vendors, their compliance status and willingness to collaborate impacts the overall duration.
How Long Does It Take To Get A SOC 2 Certification?
In a nutshell, a SOC 2 Type 1 audit will take 3 to 4 months, and a SOC 2 Type 2 audit will take 7-8 months.
SOC 2 Type 2 controls are described and evaluated for a minimum of 6 months to check if the controls are functioning as defined by management. And that's why SOC 2 Type 2 reports consume more time than SOC 2 Type 1 reports.
With Scrut, you can get SOC 2 certification quickly and cost-effectively.
Wrapping Up
Planning carefully, working together, and being aware of the timeframe are all necessary for navigating SOC 2 compliance.
By taking into account the factors that influence the timeline and implementing efficient strategies, your organization can successfully achieve SOC 2 compliance and build a strong foundation for data security and customer trust.
Frequently Asked Questions
1. What Is The Typical Duration For Achieving SOC 2 Compliance? The typical duration for achieving SOC 2 compliance varies depending on the organization's size, complexity, and readiness level. Generally, the process takes between 6 and 12 months. Smaller and less complex organizations may complete the compliance journey closer to the 6-month mark, while larger organizations might require the full 12 months or even longer.
2. What Factors Influence The SOC 2 Compliance Timeline? Several factors influence the SOC 2 compliance timeline. Organization size plays a role, as larger organizations may have more systems and processes to assess, leading to a longer timeline. The organization's readiness level also impacts the duration; those with well-established security practices might complete the process more quickly. Additionally, association with third-party vendors can affect the timeline, as their compliance status and cooperation can either expedite or slow down the overall process.
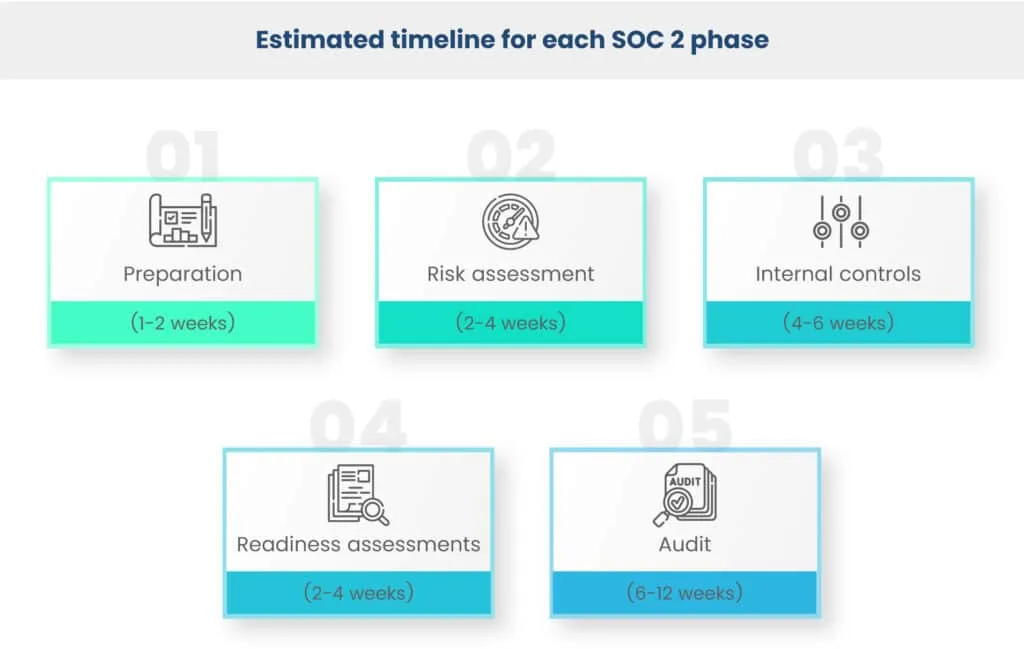
3. What Is The Estimated Timeline For Each SOC 2 Phase? The estimated timeline for each SOC 2 phase can vary based on the organization's preparedness and resource allocation.
- The soc 2 audit preparation phase, which includes identifying the scope and objectives, typically takes around 1 to 2 weeks.
- Conducting a comprehensive risk assessment may require 2 to 4 weeks, while establishing internal controls can take 4 to 6 weeks.
- Readiness assessments, which involve mock audits to identify gaps, generally last 2 to 4 weeks.
- The SOC 2 audit itself is the most time-consuming phase, often spanning 6 to 12 weeks, depending on the scope and complexity of the assessment.
4. What Strategies May Be Used To Expedite The SOC 2 Compliance Process? Organizations can use a number of strategies to speed up the SOC 2 compliance process. Establishing a structured plan early on and defining clear objectives ensures focused efforts. Hiring a capable audit team with knowledge of SOC 2 requirements and compliance can speed things up and prevent delays. Organizations can spot compliance gaps and address problems proactively by conducting readiness assessments or mock audits early on.
5. What Are The Common Challenges Encountered During Soc 2 Compliance? Common challenges encountered during SOC 2 compliance include resource constraints, complex IT infrastructure, and adapting to evolving regulatory requirements. Organizations can overcome these challenges through careful planning and collaboration with leadership. Securing adequate resources and budget allocation is crucial to supporting the compliance journey effectively.


















