Top Cybersecurity Metrics to Pay Close Attention in 2023

With the growing number of cyber threats, organizations must implement effective security measures to protect their sensitive data and critical infrastructure. Managing your cyberassets effectively can be critical to the performance of your organization, and even its survival.
To measure the performance of these measures and their effectiveness, it is important to track and measure cybersecurity metrics regularly.
In this article, we will discuss the top eleven essential cybersecurity metrics that every organization should track to double-check their security posture and stay protected against cyber threats.
What is a cybersecurity metric?

A cybersecurity metric is a quantitative measure used to track and evaluate the effectiveness of an organization’s cybersecurity efforts. These metrics help organizations to identify vulnerabilities, measure associated risks, and provide data-driven insights into the overall IT security policy of an organization.
Using cybersecurity metrics, organizations can monitor and measure the effectiveness of their security controls, identify potential gaps in the cybersecurity infrastructure, and prioritize security initiatives based on the severity of each potential threat.
Why is tracking cybersecurity metrics important?
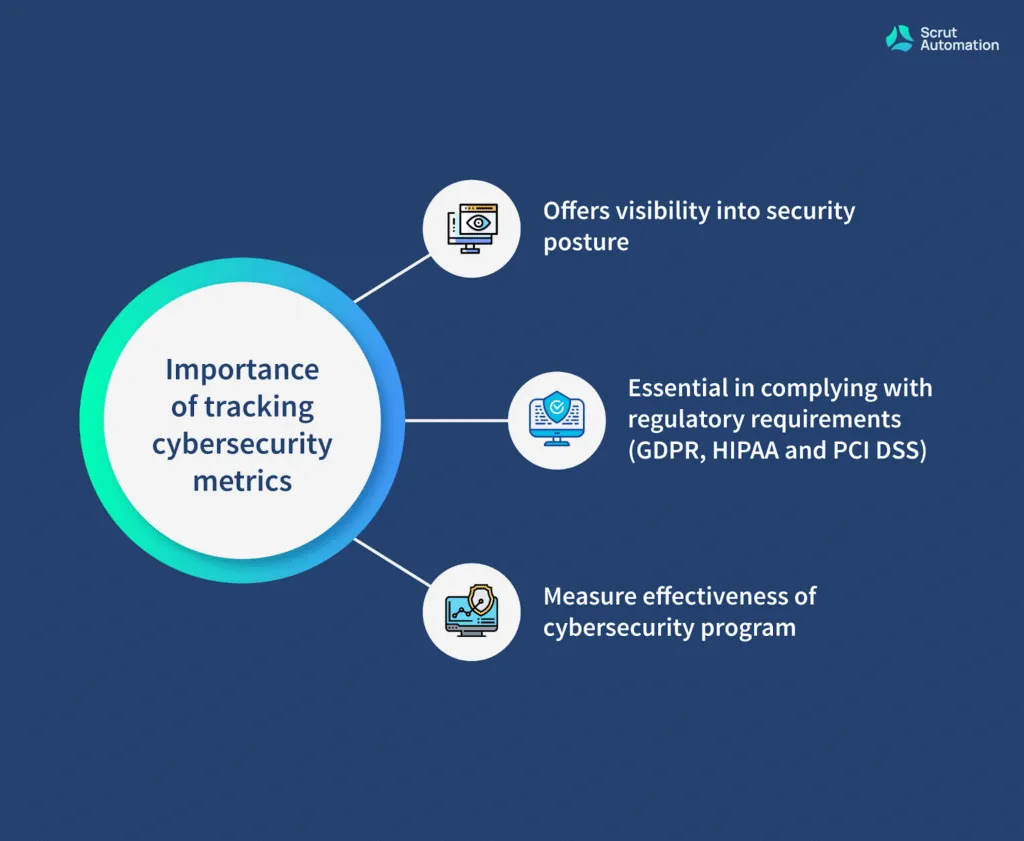
There are several reasons to track cybersecurity metrics for any organization.
For starters, it offers you visibility into the security posture of an organization’s IT infrastructure. This visibility, in turn, helps to make informed decisions about where to focus cybersecurity efforts and resources.
Secondly, tracking the important cybersecurity risk metrics allows organizations to measure the effectiveness of their cybersecurity program and make adjustments if and when necessary.
Most importantly, tracking cybersecurity metrics is essential in complying with regulatory requirements.
This can include:
- GDPR (General Data Protection Regulation)
- HIPAA (Health Insurance Portability and Accountability Act)
- PCI DSS (Payment Card Industry Data Security Standard)
11 Cybersecurity metrics to track in 2023
Now that you have learned what cybersecurity metrics are and their importance, let’s talk about the top cybersecurity metrics organizations need to track in 2023.
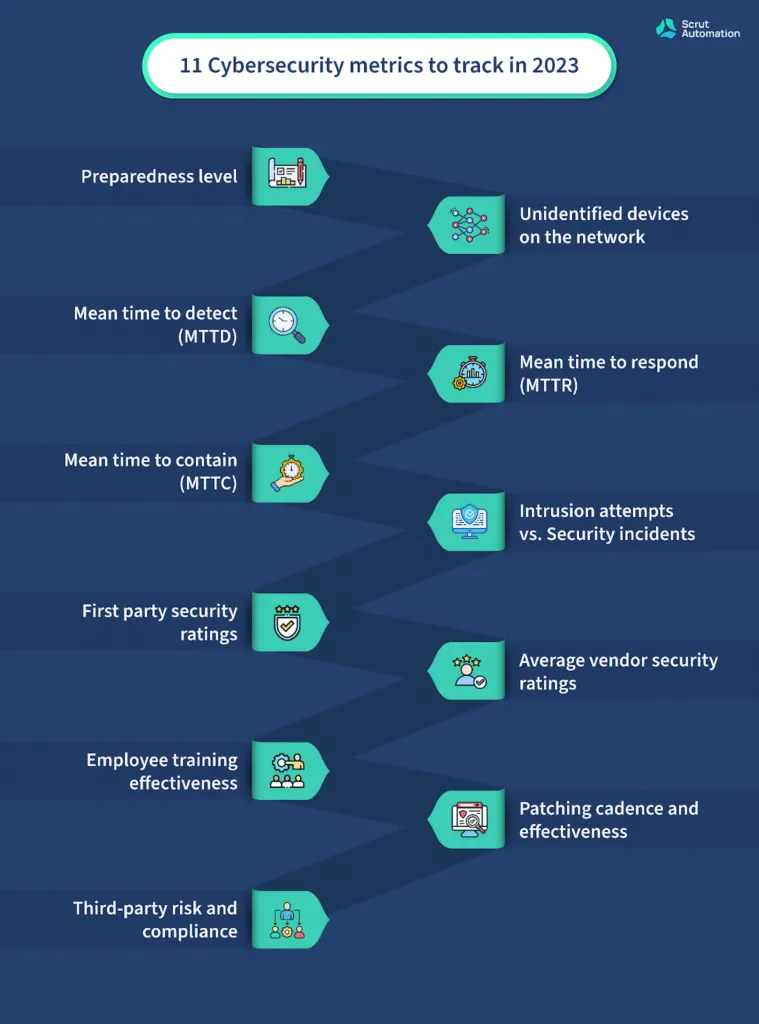
1. Preparedness level
The preparedness level metric measures how prepared an organization is to handle a cyber attack. This metric considers factors such as incident response planning, security awareness training, and effectiveness of security controls.
By tracking this metric, organizations can identify gaps in their security posture and take steps to improve their preparedness.
A higher preparedness level indicates that an organization is very well equipped to respond to a cyber attack and minimize the damage caused. A lower preparedness level indicates that the organization will be unable to effectively respond to or minimize the damage caused by a cyber attack.
Simply put, if an organization has a high preparedness level, it means they have an incident response plan in place that outlines the steps to be taken in case of a security incident. Additionally, an organization with a high preparedness level also provides regular training to employees and has implemented necessary security controls.
2. Unidentified devices on the network
Unidentified devices on the network can pose a significant risk to an organization’s cybersecurity.
For the uninitiated, an unidentified device on the network could be any smartphone, tablet, or laptop/computer that is not authorized to connect to the network.
These devices can provide attackers with a foothold into the network and can be used to exfiltrate data or launch attacks.
That’s why organizations must measure the number of unidentified devices on the network so that they can identify potential security risks and take appropriate measures to remediate them.
3. Mean time to detect (MTTD)
Mean time to detect (MTTD) metrics helps to measure the time an organization takes to detect a security incident.
The faster an organization can detect a security incident, the better chance it has of containing the damage and preventing further attacks.
This means, if an organization’s MTTD is low, it means they have effective monitoring tools in place that can detect security incidents quickly.
A low MTTD also indicates that the organization has implemented effective security controls, such as intrusion detection systems and firewalls.
4. Mean time to respond (MTTR)
The mean time to respond (MTTR) metric measures the time it takes an organization to respond to a security incident. The faster an organization can respond to a security incident, the better chance it has of containing the damage and preventing further attacks.
A lower MTTR indicates that an organization is capable of responding to security incidents and minimizing the damage caused more quickly, and vice versa.
To achieve this, organizations must consider investing in proactive cybersecurity solutions like CAASM (Cyber Asset Attack Surface Management) that automatically send alerts to cybersecurity personnel in case of any suspicious activity.
Other than this, organizations should also come up with and implement a mature incident response plan to respond quickly and efficiently to remediate any potential threats that may arise.
5. Mean time to contain (MTTC)
Mean time to contain (MTTC) measures the amount of time it takes for an organization to contain a security incident.
A lower MTTC indicates that an organization can contain security incidents more quickly and limit the damage caused, and vice versa.
There are several ways to achieve a lower MTTC. To begin with, every organization must implement effective security controls that help in containing security incidents and prevent them from spreading further and causing serious collateral damage.
Plus, it is essential to have a well-defined incident response plan in place that clearly outlines steps to be taken in case of a security incident.
6. Intrusion attempts vs security incidents
Measuring the ratio of intrusion attempts to security incidents is another crucial cybersecurity metric to monitor. It can help organizations understand how effective their security controls are in preventing successful attacks.
Intrusion attempts refer to unauthorized access attempts made by an external party to gain access to a company’s network or systems. Security incidents, on the other hand, are actual breaches or successful attempts at unauthorized access.
By tracking these two metrics, organizations can identify areas of vulnerability in their systems and take appropriate action to improve their security posture.
7. First party security ratings
First party security ratings provide an overall assessment of an organization’s security posture based on factors such as data protection, network security, and patching cadence (more on this later).
These ratings are usually calculated by third-party cybersecurity rating providers, who use various sources of data to assess an organization’s security posture.
Based on these ratings, an organization can identify and assess gaps in its security measures and prioritize cybersecurity efforts & investments to improve its overall cybersecurity program.
8. Average vendor security ratings
The current threat landscape is not confined to just an organization’s IT infrastructure, it extends way beyond that.
Today, every organization works with third-party vendors in some capacity to help run business operations smoothly. So, it is critical for organizations to implement robust vendor risk management to monitor and reduce third-party risks.
This is where average vendor security ratings come in.
Average vendor security ratings are assessments of the cybersecurity practices and measures of third-party vendors that an organization works with.
These ratings can be useful for identifying potential risks and vulnerabilities in an organization’s supply chain and taking necessary steps to mitigate those risks.
Simply put, it’s extremely critical for every organization to vet their vendors carefully and ensure that they have strong cybersecurity measures & practices in place.
9. Employee training effectiveness
The employee training effectiveness metric helps to measure the overall effectiveness of the employee cybersecurity training programs at an organization.
Through this metric, organizations can assess how well employees are able to apply the knowledge and skills acquired through cybersecurity training programs to real-world scenarios.
This, in turn, helps to evaluate the level of awareness, understanding, and practical application of cybersecurity concepts and best practices by employees.
In short, tracking employee training effectiveness is essential for organizations to identify gaps in their cybersecurity training programs and improve cybersecurity awareness among employees.
By doing so, organizations can ensure that their employees are equipped to protect against cyber threats and to minimize the risks of cyber attacks.
10. Patching cadence and effectiveness
One of the most important aspects of any cybersecurity program is ensuring that all software and systems are up to date with the latest security patches. This is because many cyber attacks exploit vulnerabilities in outdated software that have not been patched.
One metric that can be used to measure the effectiveness of your patching program is the patching cadence.
This metric measures how quickly patches are applied to systems after they are released. The faster patches are applied, the less time cybercriminals have to exploit vulnerabilities.
Another important metric to measure along with Patching Cadence is the effectiveness of your patching program.
This metric measures how many vulnerabilities are actually patched with each update. If patches are not effective, vulnerabilities will remain and cybercriminals will still be able to exploit them.
To ensure that your patching program is effective, you should have a process in place for testing patches before they are applied to production systems.
This will help to identify any issues or conflicts that may arise from applying the patch, and ensure that it does not cause any downtime or other issues.
11. Third-party risk and compliance
Third-party risk management is essential for ensuring the security of your organization’s data.
As more and more companies rely on third-party vendors to provide services and products, the risk of a data breach or cyber attack increases.
To effectively manage third-party risk, it’s important to establish clear policies and procedures for vendor management.
This includes conducting risk assessments of third-party vendors, monitoring their security practices, and ensuring compliance with industry regulations and standards.
One key metric for measuring third-party risk is the percentage of vendors that have completed a risk assessment. This metric can help you identify areas of vulnerability and prioritize vendor management efforts.
Additionally, you should also measure the percentage of vendors that that meet your organization’s security standards and compliance requirements.
To ensure compliance with industry regulations and standards, it’s important to establish clear policies and procedures for third-party compliance.
This includes conducting regular audits of third-party vendors, monitoring their compliance with industry regulations and standards, and providing ongoing training and support.
By effectively managing third-party risk and compliance, you can reduce the risk of a data breach or cyber attack and ensure the security of your organization’s data.
Level up your cybersecurity program!
Tracking these top cybersecurity metrics is essential to effectively manage your organization’s security posture.
By regularly monitoring and analyzing key performance indicators, you can identify areas of weakness and take proactive measures to mitigate risks.
Remember that not all metrics are created equal. While it’s important to track a variety of cybersecurity KPIs, it’s equally important to focus on those that are most relevant to your organization’s unique security needs and goals.
Overall, by tracking the right cybersecurity metrics and using them to inform your security strategy, you can help protect your organization from cyber threats and stay one step ahead of attackers.
FAQs
How can you measure cybersecurity?
Measuring cybersecurity requires assessing vulnerability, incident response, compliance with regulations & industry standards, user awareness, and security controls. Regular evaluation of these factors can help improve the overall security posture of an organization.
What are KPI and KRI in cybersecurity?
KPI (Key Performance Indicators) and KRI (Key Risk Indicators) are metrics used in cybersecurity to measure the effectiveness of security measures and identify potential risks.
KPIs indicate how well an organization is performing in terms of security. KRIs, on the other hand, indicate the level of risk to the organization.
Why is it important to measure cybersecurity?
Measuring cybersecurity is important because it helps to identify risks, evaluate the effectiveness of security measures, meet regulatory requirements, and protect against financial losses.
How can you set metrics in cybersecurity?
To set metrics in cybersecurity, you need to identify goals, determine metrics, establish a baseline, set targets, monitor regularly, take action, and continuously improve your strategy.


















