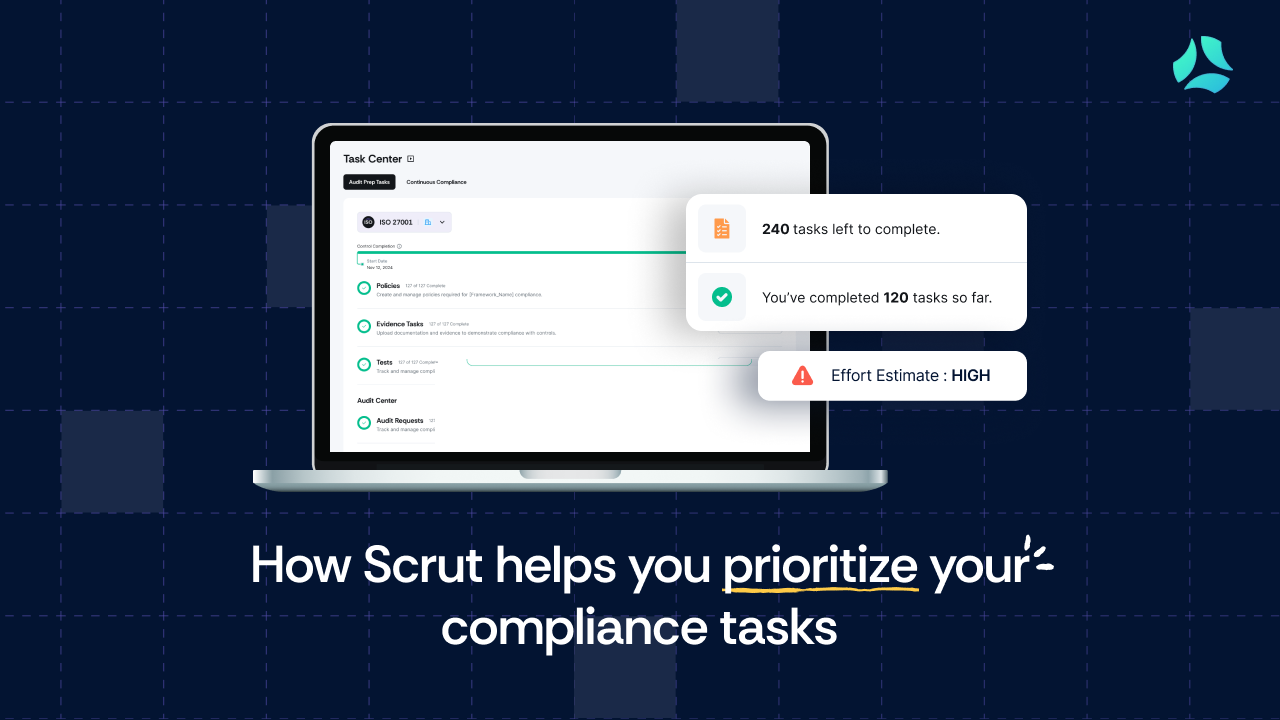
Choose risk-first compliance that’s always on, built for you.
Go back to blogs
SecuriTea Time Ep 2 | Cracking the Cyber Code with Evolving Perspectives of Cybersecurity
Last updated on
December 2, 2024
min. read

Welcome, readers, to another insightful episode of SecuriTea Time, a podcast curated for cybersecurity and tech folks.
Today, we have a distinguished guest joining us. Joshua Zweig, the co-founder of Zip Security, previously a Civil Liberties Engineer at Palantir Technologies, is here to share his expertise and insights into the ever-evolving world of cybersecurity.
Zip Security has made waves in the industry with its innovative approaches to safeguarding digital assets. We’ll delve deep into the fascinating world of cybersecurity and explore the secrets behind Zip Security’s success.
So, without further ado, let’s dive right into this riveting episode of SecuriTea Time!
You can listen to the complete podcast here.
Nicholas Muy: As a co-founder of a security startup, what are your thoughts on Black Hat, the event where security professionals, hackers, and researchers gather to discuss and showcase the latest trends, vulnerabilities, and research in the field of cybersecurity?
Joshua Zweig: I haven’t had the chance to attend Black Hat yet, but I find it fascinating. It’s a significant event in the security industry, and it can have an impact on various aspects like investor interest and potential customers. These conferences are essential for our small industry, offering valuable networking and business opportunities. This year, we didn’t go because our customers are often small security teams or companies without security professionals. However, I believe these events serve as a rallying point for the industry and provide opportunities for newcomers to break into the field. Despite the intimidating branding, there are resources available to help newcomers find their way, making these conferences valuable for anyone looking to enter the cybersecurity field.
Nicholas Muy: How do you see the cybersecurity industry evolving to address the challenges of making security solutions more accessible and manageable for a broader range of organizations and practitioners, considering the unique complexities it presents?
Joshua Zweig: Well, building a security company is a challenge. You really need to be disciplined in choosing your customer base. Security is unique; it’s not like building any other company. There’s this constant tension between raising money for a security company and managing expectations.
When you aim for billion or ten-billion-dollar outcomes, scale and scalability become critical. But here’s the thing, security is, in essence, a property of systems. Every company, every system has unique properties and security requirements, which makes it exceptionally hard.
Sometimes, companies try to make everyone in the organization a security expert, but that doesn’t work for everyone. It’s not a silver bullet. So, you need to be disciplined, especially in the early stages, about choosing your customers.
You have to decide how deep you want to go into the details and what lessons apply to your entire customer base. Balancing scalability and depth is tricky for any company, but security adds an extra layer of complexity because it’s deeply rooted in system properties.
Security products often require a high level of management. Almost everything in the security industry seems to have ‘managed’ before it – managed security service provider, managed bots, and so on. It’s because security products demand ongoing management, especially in areas like access controls where things are constantly changing.
The challenge is identifying repeatable problems and making them scalable. It’s tough because not many companies are addressing this. Customers often buy security tools but struggle to implement them effectively. We need to make this easier; it’s a big task for the next 5 to 10 years.
There’s also a job gap in cybersecurity. We need people to handle the management, but it’s not an easy role to fill because it’s not part of the core business processes. So, we’ve got a significant job gap, and it won’t be solved easily.
In summary, building a security company is complex, and simplification is essential. We need to make security work easier for practitioners and address the workforce development challenge in the cybersecurity field.
Nicholas Muy: You’ve mentioned the concept of making the cybersecurity problem significantly more accessible and manageable rather than just adding more professionals. Can you elaborate on how we might achieve this and what changes you think are necessary in the industry to make this approach effective? Additionally, how do you see the balance between security and a free society evolving in the context of cybersecurity?
Joshua Zweig: I remember our previous discussions about the “missing million” issue in cybersecurity. I hadn’t heard it framed that way before, but I find it to be a brilliant perspective. When we consider the challenges in cybersecurity, simply adding more people might not be the silver bullet. Instead, we should explore making the problem significantly more accessible and manageable, potentially by several orders of magnitude.
Even a million additional cybersecurity experts, as significant as it sounds, may not fully address the problem when you consider the scale of the workforce and the broader industry. To put it in perspective, in a country like the United States with a population of around 350 million, having a million cybersecurity practitioners would still represent only a small fraction. Comparing this to other industries like trucking, where millions are involved, makes you question the feasibility of relying solely on increasing the workforce.
Furthermore, we must strike a balance between security and maintaining the principles of a free society, similar to how physical security is approached. It’s essential to remember that cybersecurity primarily involves playing defense against adversaries who are constantly on the offensive. Understanding their tactics, budgets, and objectives is crucial for devising effective strategies in the cybersecurity landscape. This perspective offers valuable insights into how we should navigate the challenges and complexities of cybersecurity.
Nicholas Muy: A different approach to cybersecurity is needed, as the current model focuses on selling solutions that work well in perfect conditions, which are rarely encountered in real-world network environments. This underscores the need for a flexible and adaptable approach to cybersecurity. What are your thoughts?
Joshua Zweig: I believe it’s essential to question the concept of perfection, especially in the context of modeling real-world situations. Many aspects of our work involve modeling social interactions, which inherently decay over time. It’s crucial to shift our perspective from viewing this decay as a design constraint to considering it a design principle.
By embracing the complexity and unpredictability of these interactions, we can better serve our customers, as this complexity mirrors the real world. It’s a shift in mindset that aligns our approach with the inherent nature of the world we’re trying to understand and protect.
Nicholas Muy: The current trend of redundant integrations in security startups is costly and inefficient. We need innovative models to address challenges like data management more efficiently and reshape the industry. What do you think?
Joshua Zweig: I often think that while building a company like Slack may not directly seem like creating security features, you can essentially construct a security-focused company around elements like integrations and engineering. It’s a nuanced challenge to brand yourself as a security company or not, especially in the cybersecurity sector.
Regarding government involvement in cybersecurity, it’s been evolving significantly, especially in the past few years. In the early 2010s, cybersecurity was still a relatively new field, and the government was finding its footing. Recent initiatives like the DOJ’s rewards for information leading to the capture of cybercriminals are intriguing. I read about a case where the FBI actively pursued hackers during a ransomware incident, highlighting the shift from just defense to actively targeting cyber threats, even within government ranks where insider threats can also pose significant risks. It’s a complex landscape that continues to evolve.
Nicholas Muy: How do you envision the future of NIST 171 800 and similar frameworks in the context of evolving technology and potential shifts in the threat landscape?
Joshua Zweig: I often think about the future of NIST 171 800. It’s a valuable framework but challenging for smaller organizations due to its cost and complexity. I believe the industry will make compliance easier through technology in the next five to ten years. However, I’m concerned about its relevance as technology evolves. Changes in underlying technology could alter the threat landscape, making current frameworks less effective. Additionally, rigid adherence to rules might overshadow broader security goals.
Nicholas Muy: Help me debunk the misconception that security programs aim for complete risk elimination. In reality, achieving absolute security is neither possible nor practical for businesses. Instead, should we strive for a balanced approach that effectively manages the most pertinent risks?
Joshua Zweig: My approach to security is to focus on addressing the 80% of cases that can have the most significant impact. Most people, including non-security professionals, find it challenging to pinpoint their top cybersecurity risks. It’s a complex task because there are various threats to consider.
However, the goal isn’t to be constantly worried about these risks but rather to identify the key ones and take appropriate actions to mitigate them. This typically covers about 80% of the security concerns and provides a solid foundation for protection.
Nicholas Muy: Could it be that security challenges are not due to a lack of effort but rather to the overwhelming complexity and resource constraints we face?
Joshua Zweig: Well, it’d be intriguing to define the contrapositive scenario—the events we anticipate due to our prioritization efforts. I suspect this exercise isn’t common in many organizations. Our industry could do a lot better job of thinking about the ways in which we can make things in all different pockets of security more accessible, whether that’s in something like the stuff we’re talking about here, something low levels like malware, or reverse engineering. It’s something we ve been doing across the board, and I think this podcast has done a lot to help that out.
That concludes the highlights for this episode! Be sure to keep an eye out for the highlights of our next episode, where we’ll continue exploring the realms of cybersecurity and compliance.
Table of contents