Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Comprehensive Guide to FMEA Analysis Techniques
Last updated on
April 17, 2025
17
min. read

Risk calculation involves assessing, analyzing, and quantifying potential risks to an organization's objectives, assets, or operations. It typically involves evaluating the likelihood of specific risks occurring and estimating the magnitude of their potential impact. By combining these assessments, organizations can calculate the overall risk level associated with particular scenarios or activities.
There are various methods of risk calculation that you can implement in your organization. Some of these risk calculation methods are Failure Mode and Effects Analysis (FMEA), SWOT analysis, and TPRM.
Failure Mode and Effects Analysis (FMEA) involves identifying possible failure modes, determining their likelihood and severity, and prioritizing them based on risk to take proactive measures for mitigation. FMEA helps organizations improve reliability, safety, and performance by addressing potential issues before they occur, thus enhancing overall quality and efficiency.
In this article, we will learn about the process of implementing FMEA in your organization.
II. Understanding FMEA
What is FMEA?
FMEA stands for Failure Mode and Effects Analysis. It's a systematic methodology used to identify and assess potential failure modes within a system, process, or product, along with evaluating their potential effects on operations or outcomes.
The primary goal of FMEA is to proactively identify and prioritize potential failures, determine their causes and effects, and develop strategies to mitigate or eliminate these failures before they occur. FMEA is widely utilized across various industries, including automotive, aerospace, healthcare, and manufacturing, to enhance product reliability, improve safety, and reduce the risk of failures.
The core principles of FMEA
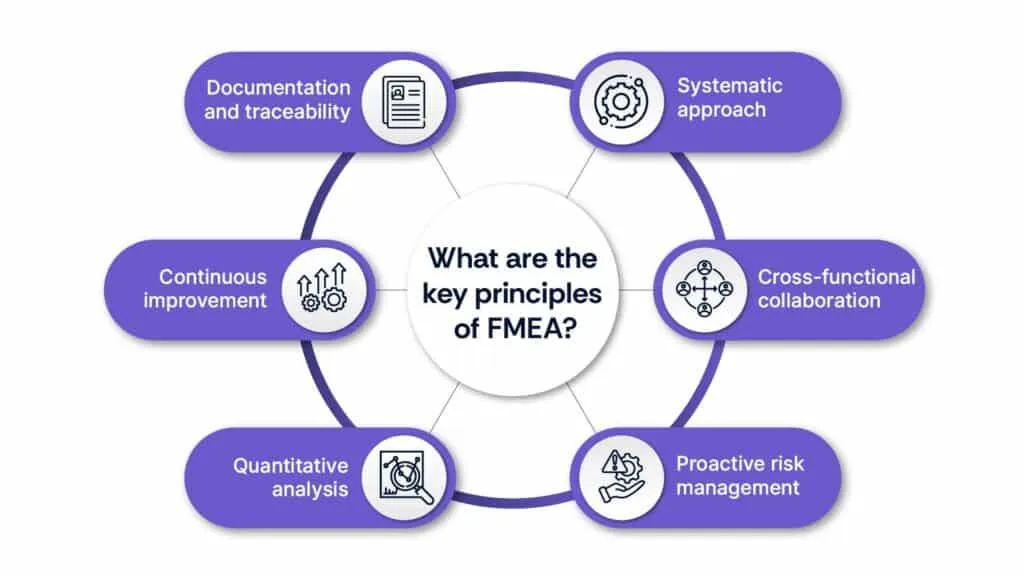
The core principles of FMEA encompass several key concepts essential to its effectiveness:
1. Systematic approach
FMEA follows a structured and systematic methodology for identifying potential failure modes, analyzing their causes and effects, and developing appropriate preventive or corrective actions. This ensures thorough coverage and consistency in the assessment process.
2. Cross-functional collaboration
FMEA involves collaboration among multidisciplinary teams with diverse expertise and perspectives. This ensures comprehensive analysis and consideration of various factors contributing to failure modes, including design, manufacturing, operations, and maintenance.
3. Proactive risk management
FMEA is a proactive risk management tool aimed at identifying and addressing potential failures before they occur. By anticipating and mitigating risks early in the development or operational phases, organizations can prevent costly failures, improve reliability, and enhance overall performance.
4. Quantitative analysis
FMEA incorporates quantitative analysis to assess the severity, occurrence probability, and detection capability of potential failure modes. Assigning numerical values to these parameters facilitates prioritization and decision-making regarding risk mitigation strategies.
5. Continuous improvement
FMEA is not a one-time activity but rather a continuous improvement process. Organizations regularly review and update FMEA analyses to reflect changes in processes, technologies, or operating conditions, ensuring ongoing effectiveness in managing risks and enhancing performance.
6. Documentation and traceability
Proper documentation of FMEA activities, including identified failure modes, causes, effects, and mitigation measures, is essential for accountability, traceability, and knowledge transfer within the organization. Documented FMEA results serve as valuable reference materials for future projects and decision-making.
Types of FMEA
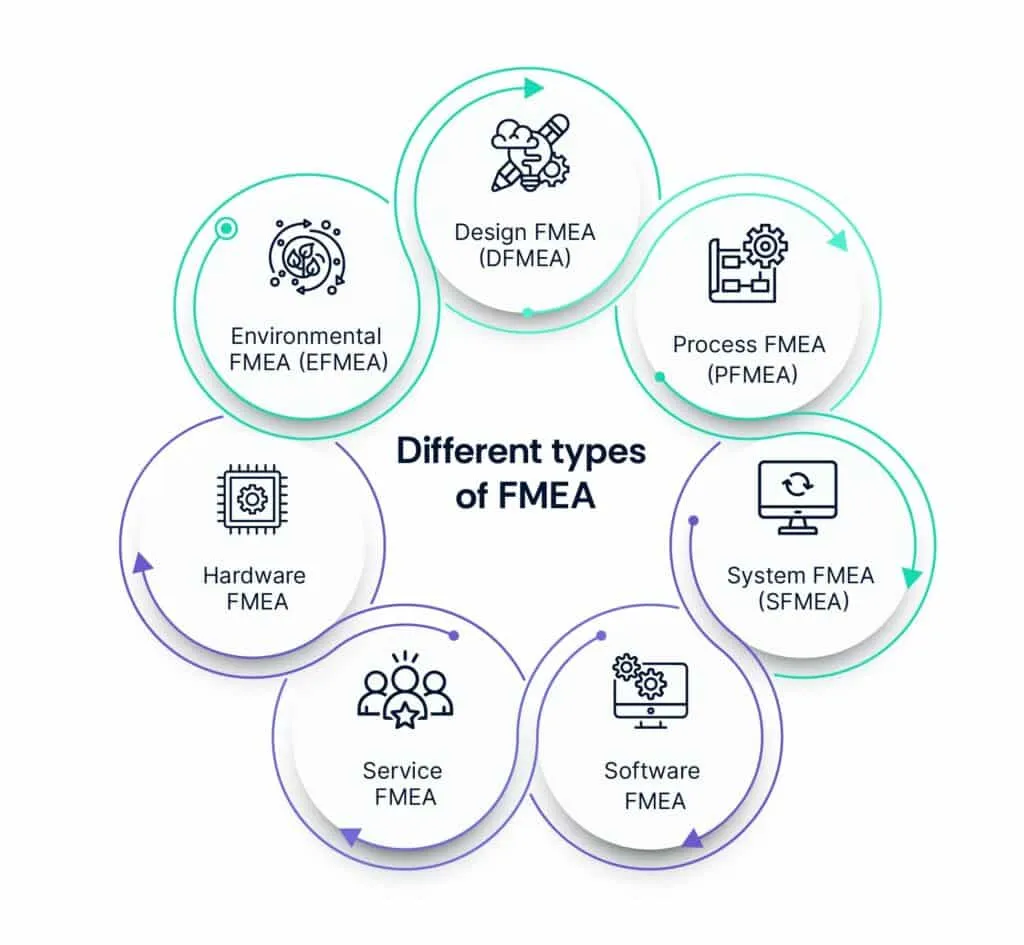
There are several types of FMEA, each tailored to specific contexts and objectives:
1. Design FMEA (DFMEA)
This type of FMEA focuses on identifying potential failure modes and their effects during the design phase of a product, system, or process. It aims to prevent or mitigate design-related failures before they occur, thereby improving product reliability and reducing development costs.
2. Process FMEA (PFMEA)
Process FMEA evaluates potential failure modes and their effects on manufacturing or operational processes. It helps organizations identify process weaknesses, error-prone areas, and opportunities for improvement to enhance quality, efficiency, and consistency in production.
3. System FMEA (SFMEA)
System FMEA assesses potential failure modes and their impacts at the system level, considering interactions among various subsystems or components. It helps organizations understand how failures within individual components or subsystems may affect the overall system performance or reliability.
4. Software FMEA
Software FMEA specifically addresses potential failure modes and their effects on software systems, applications, or algorithms. It focuses on identifying software-related defects, errors, or vulnerabilities that may compromise system functionality, data integrity, or security.
5. Service FMEA
Service FMEA examines potential failure modes and their consequences within service-oriented processes or operations. It helps organizations identify risks associated with service delivery, customer interactions, and support activities, enabling them to improve service quality and customer satisfaction.
6. Hardware FMEA
Hardware FMEA concentrates on potential failure modes and their effects on physical components, equipment, or machinery. It aims to identify hardware-related failures, malfunctions, or defects that could impact product performance, safety, or reliability.
7. Environmental FMEA (EFMEA)
EFMEA evaluates potential failure modes and their effects related to environmental factors such as temperature, humidity, vibration, or chemical exposure. It helps organizations assess risks associated with environmental conditions and design products or processes to withstand or mitigate these risks.
FMEA automation
FMEA software streamlines Failure Mode and Effects Analysis by providing a structured framework for identifying failure modes, assessing their effects, and developing mitigation strategies. It supports collaboration among teams, manages data, prioritizes risks, and facilitates documentation and reporting. Integrating with other systems, it offers customization options to adapt to organizational needs, improving risk management efficiency and effectiveness. You can implement FMEA software to automatically perform FMEA analysis in your organization.
10-step guide to an FMEA analysis
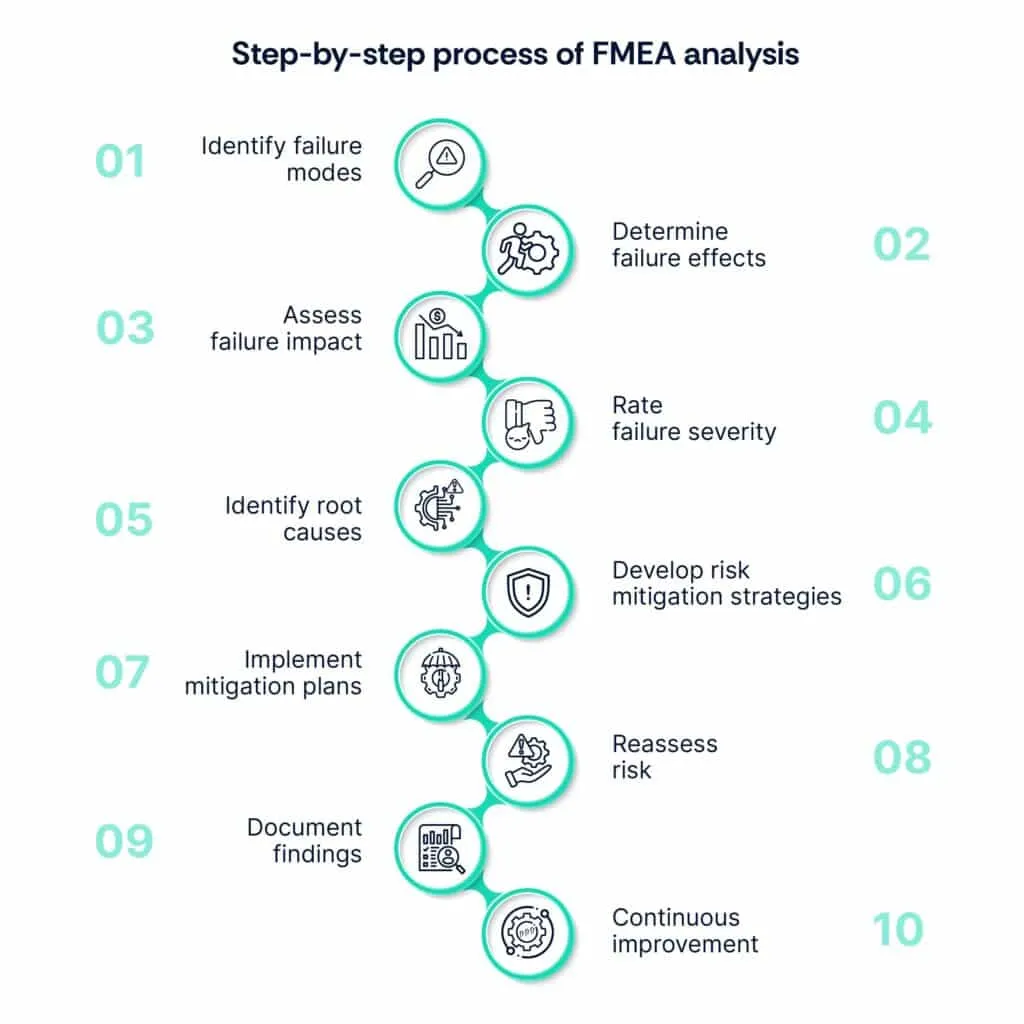
Here are ten steps you can take to implement FMEA analysis in your organization:
Step 1: Identify failure modes
Failure modes refer to potential ways in which a system, process, or product can fail to meet its intended functionality or performance requirements. These modes represent specific scenarios or conditions that could lead to a loss of function, quality, or safety within the analyzed system.
Techniques for identifying failure modes
- Brainstorming: Engage multidisciplinary teams to generate ideas and scenarios that could lead to failures within the system or process.
- Historical data analysis: Review past incidents, breaches, or failures to identify recurring patterns or vulnerabilities.
- Fault tree analysis (FTA): Analyze the system's structure and identify potential combinations of events or conditions that could lead to failures.
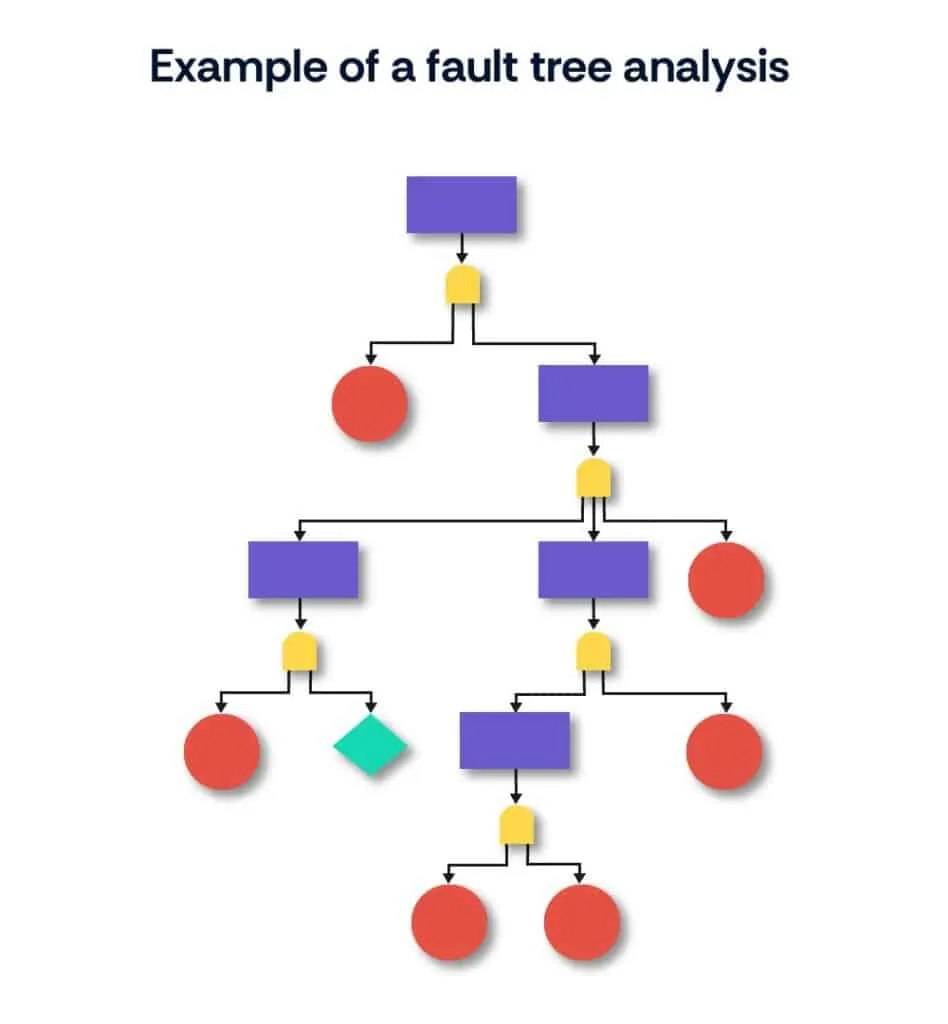
- Threat modeling: Systematically identify potential threats and attack vectors that could exploit weaknesses in cybersecurity defenses.
- Scenario analysis: Develop hypothetical scenarios or use cases to explore different failure modes and their potential impacts.

Step 2: Determine failure effects
Failure effects refer to the consequences or impacts resulting from the occurrence of a failure mode within a system, process, or product. These effects can range from minor disruptions to critical failures, potentially leading to financial losses, reputational damage, or safety hazards.
Techniques for determining failure effects
- Cause and effect analysis: Identify how each failure mode could propagate through the system and affect its various components or stakeholders.
- Scenario analysis: Explore hypothetical scenarios or use cases to understand the potential outcomes of each failure mode.
- Risk matrix: Assess the severity of failure effects by categorizing them based on their impact on business operations, compliance, safety, or customer satisfaction.
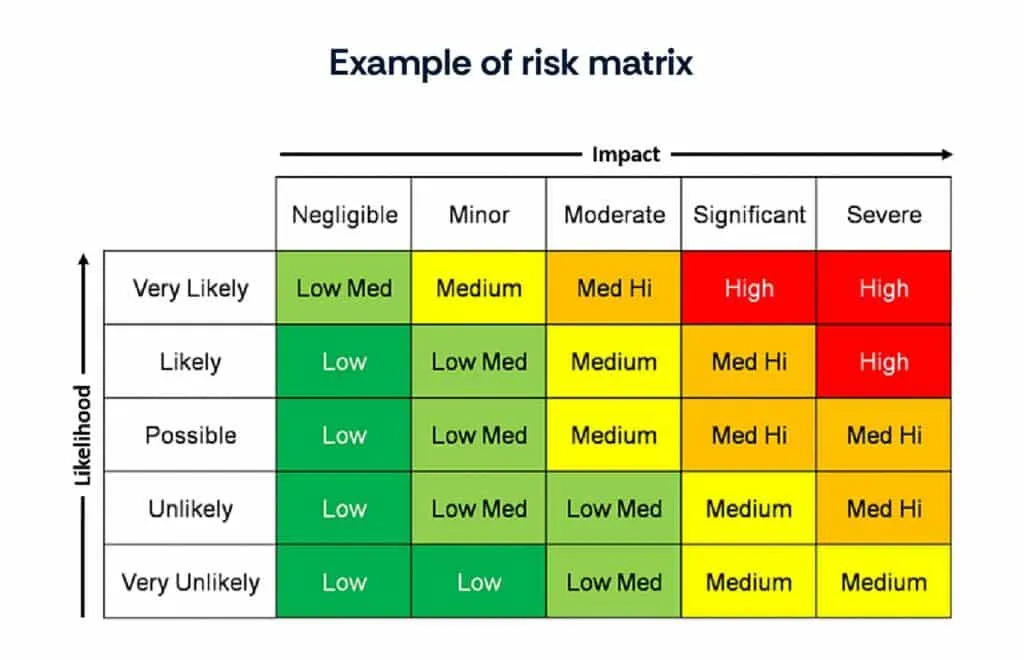
- Expert judgment: Consult subject matter experts or stakeholders to determine the potential consequences of failure modes based on their knowledge and experience.
- Historical data review: Analyze past incidents or failures to understand the real-world impacts of similar failure modes.
Step 3: Assess failure impact
Failure impact refers to the extent or magnitude of the consequences resulting from the occurrence of a failure mode within a system, process, or product. It quantifies the severity of the effects on various aspects such as safety, quality, compliance, financial, or operational performance.
Techniques for assessing failure impact
- Severity rating scales: Use predefined severity rating scales to assess the severity of failure impacts on a numerical scale (e.g., 1 to 10), considering factors such as financial loss, safety hazards, regulatory compliance, or customer satisfaction.
- Cost-benefit analysis: Evaluate the potential costs associated with failure impacts against the benefits of implementing preventive or corrective measures to mitigate risks.
- Expert judgment: Seek input from subject matter experts or stakeholders to assess the potential consequences of failure impacts based on their knowledge and experience.
- Historical data analysis: Analyze past incidents or failures to understand the real-world impacts of similar failure modes and estimate the potential consequences.
- Scenario analysis: Explore hypothetical scenarios or use cases to assess the potential outcomes of failure impacts under different conditions or circumstances.

Step 4: Rate failure severity
Failure severity refers to the degree of impact or harm that could result from the occurrence of a failure mode within a system, process, or product. It quantifies the seriousness or severity of the consequences, ranging from minor inconveniences to critical failures with significant implications.
Rating scales for severity assessment
Severity rating scales typically use numerical or qualitative descriptors to assess the severity of failure consequences. Common scales include:
- Numerical scale: Assign severity ratings on a numerical scale (e.g., 1 to 10), with higher numbers indicating greater severity.
- Qualitative scale: Use descriptive labels (e.g., Low, Medium, High) to categorize severity levels based on the potential impact of failure consequences.

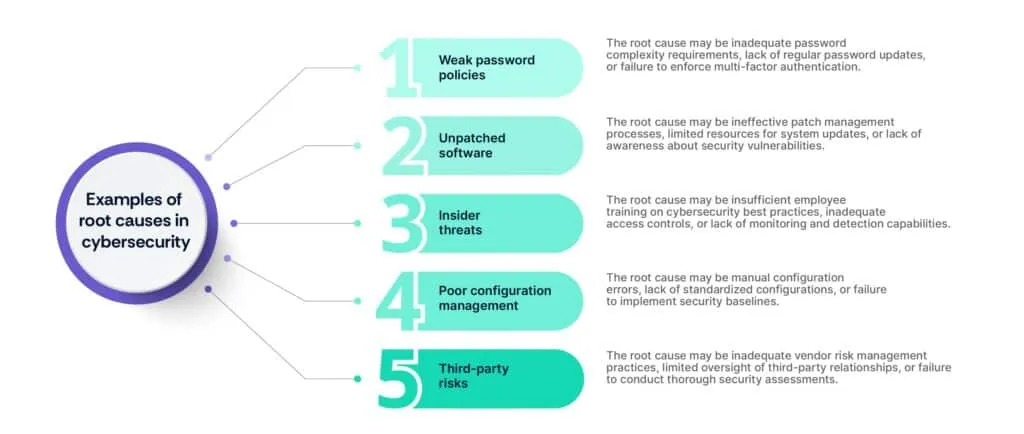
Step 5: Identify root causes
Root causes are the underlying factors or fundamental reasons that contribute to the occurrence of failure modes within a system, process, or product. Identifying root causes is essential for understanding why failures occur and developing effective corrective actions to prevent recurrence.
Techniques for identifying root causes
- “5 Whys" analysis: Ask “why" repeatedly to drill down to the underlying causes of a failure mode, typically reaching a root cause after asking “why" five times.
- Fishbone diagram (Ishikawa diagram): Use a structured approach to identify potential causes of a failure mode across categories such as people, process, equipment, materials, environment, and management.
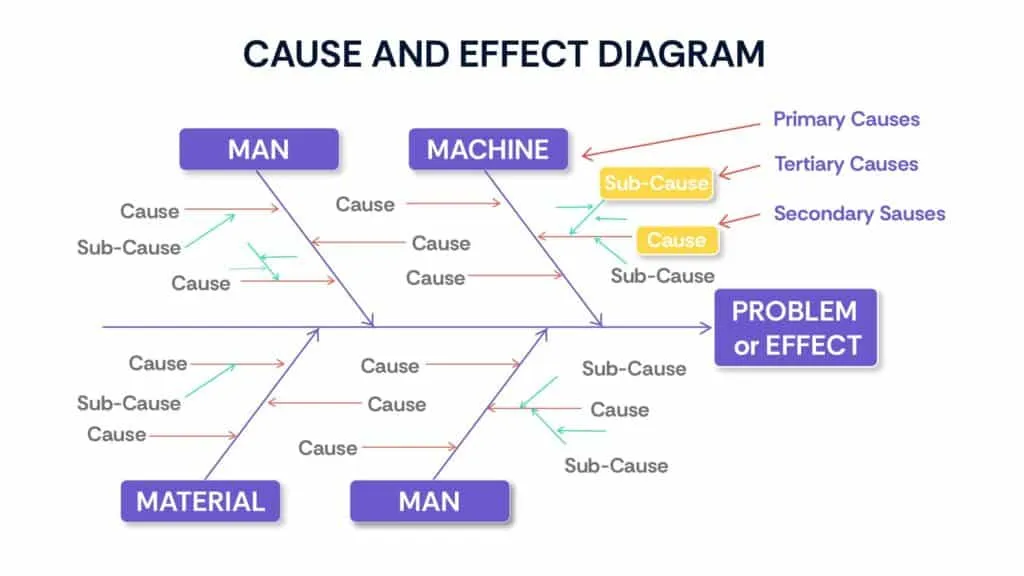
- Failure analysis techniques: Utilize specialized techniques such as Failure Mode, Effects, and Criticality Analysis (FMECA), Fault Tree Analysis (FTA), or Root Cause Analysis (RCA) to investigate complex failures and determine root causes.
- Brainstorming and expert judgment: Engage multidisciplinary teams and subject matter experts to brainstorm potential root causes based on their knowledge, experience, and insights.
- Data analysis: Analyze historical data, incident reports, logs, and metrics to identify patterns, trends, or systemic issues that may contribute to failure modes.
Step 6: Develop risk mitigation strategies
Risk mitigation involves the development and implementation of actions or measures aimed at reducing the likelihood or impact of identified risks within a system, process, or product. These strategies seek to minimize the occurrence of failure modes or mitigate their consequences to enhance overall resilience and performance.
Strategies for mitigating risks identified through FMEA

- Preventive controls: Implement measures to prevent failure modes from occurring, such as strengthening access controls, implementing security patches promptly, or enhancing employee training on cybersecurity best practices.
- Detective controls: Deploy monitoring and detection mechanisms to identify and respond to potential failure modes in real-time, such as intrusion detection systems, security event monitoring, or anomaly detection algorithms.
- Corrective actions: Develop procedures and protocols to address failure modes promptly and effectively when they occur, such as incident response plans, disaster recovery processes, or backup and recovery strategies.
- Risk transfer: Transfer or share the risk with third-party service providers, insurance coverage, or contractual agreements to mitigate the financial or operational impacts of failure modes.
- Continuous improvement: Establish a culture of continuous improvement by regularly reviewing and updating risk mitigation strategies based on emerging threats, changing business requirements, or lessons learned from past incidents.
Step 7: Implement mitigation plans
A. Developing action plans
- Translate risk mitigation strategies into actionable steps and tasks to address identified failure modes.
- Define specific objectives, milestones, and timelines for implementing mitigation plans effectively.
- Establish clear priorities and sequencing of actions based on the severity and likelihood of failure modes.
B. Assigning responsibilities
- Identify individuals or teams responsible for executing each action or task within the mitigation plans.
- Clearly communicate roles, responsibilities, and expectations to ensure accountability and alignment.
- Assign appropriate resources, authority, and support to enable successful implementation of mitigation plans.
C. Monitoring progress
- Establish monitoring mechanisms to track the progress and status of implementation efforts.
- Regularly review and update mitigation plans to address any deviations, obstacles, or emerging risks.
- Communicate progress updates and status reports to relevant stakeholders to maintain transparency and accountability.
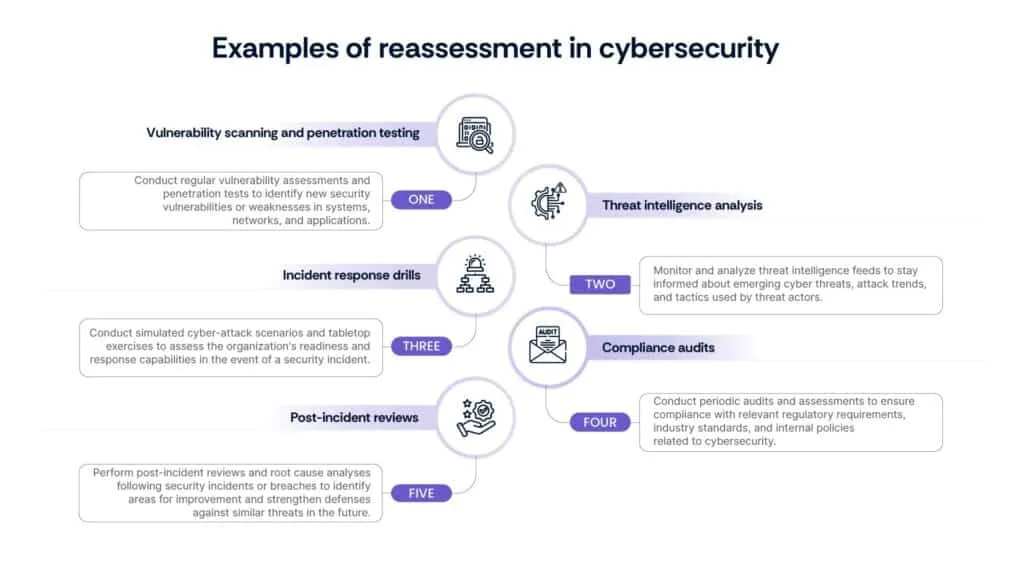
Step 8: Reassess risk
A. Periodic review and reassessment
- Schedule regular intervals for reviewing and reassessing cybersecurity risks to ensure the ongoing effectiveness of mitigation efforts.
- Incorporate reassessment activities into existing governance processes, compliance audits, or risk management frameworks.
- Consider external factors such as emerging threats, regulatory changes, technological advancements, and organizational changes that may impact risk levels.
B. Adapting mitigation strategies as needed
- Evaluate the effectiveness of existing mitigation strategies in addressing identified risks and meeting organizational objectives.
- Identify areas for improvement or gaps in mitigation efforts and adapt strategies accordingly.
- Incorporate lessons learned from past incidents, near misses, or changes in the threat landscape to enhance resilience and responsiveness.
Step 9: Document findings
Importance of documentation
- Accountability: Documentation provides a record of FMEA activities, findings, and decisions, ensuring accountability and transparency within the organization.
- Knowledge transfer: Documented FMEA analyses serve as valuable reference materials for future projects, enabling knowledge transfer and continuity across teams and personnel.
- Compliance: Documentation helps demonstrate compliance with regulatory requirements, industry standards, and internal policies related to risk management and cybersecurity.
- Continuous improvement: Documented findings enable organizations to track progress, identify trends, and make informed decisions for continuous improvement of cybersecurity practices.
Templates and formats for documentation
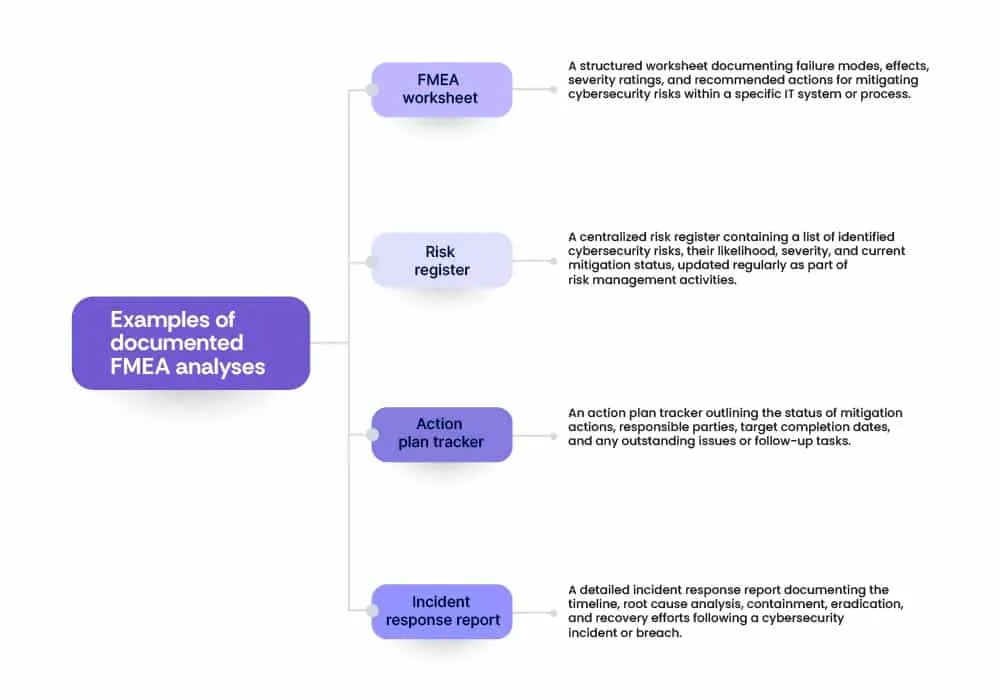
- FMEA worksheet: Use structured templates or worksheets to document FMEA activities, including failure modes, effects, severity ratings, mitigation strategies, and action plans.
- Risk register: Maintain a centralized risk register or database to record identified risks, their associated attributes (e.g., severity, likelihood), and mitigation status.
- Action plan tracker: Create action plan trackers to monitor the implementation progress of mitigation plans and track assigned responsibilities, deadlines, and status updates.
- Incident response reports: Document post-incident reports detailing the root causes, impacts, response actions, and lessons learned from cybersecurity incidents or breaches.
Step 10: Continuous improvement
A. Establishing a culture of continuous improvement
- Leadership support: Foster leadership buy-in and support for continuous improvement initiatives by emphasizing the importance of agility, innovation, and adaptability in cybersecurity.
- Employee engagement: Encourage active participation and feedback from employees at all levels to identify areas for improvement, share best practices, and contribute to a culture of continuous learning.
- Recognition and rewards: Recognize and reward individuals or teams that contribute to continuous improvement efforts, promoting a positive and collaborative work environment.
- Training and development: Provide training and professional development opportunities to enhance employees' skills, knowledge, and capabilities in cybersecurity risk management and FMEA methodologies.
- Process evaluation: Regularly review and evaluate existing processes, procedures, and methodologies to identify inefficiencies, bottlenecks, or areas for enhancement.
B. Learning from past experiences
- Post-incident reviews: Conduct thorough post-incident reviews and root cause analyses following cybersecurity incidents or breaches to identify lessons learned and opportunities for improvement.
- After-action reports: Document findings, recommendations, and corrective actions resulting from post-incident reviews to facilitate knowledge sharing and continuous improvement.
- Trend analysis: Analyze historical data, trends, and patterns to identify recurring issues, common vulnerabilities, or emerging threats that require attention and proactive mitigation.
- Benchmarking: Compare cybersecurity practices, performance metrics, and outcomes against industry standards, best practices, and peer organizations to identify areas for improvement and establish benchmarks for success.
C. Integrating FMEA into Cybersecurity Processes
- Embed FMEA methodologies: Incorporate FMEA methodologies and principles into existing cybersecurity risk management processes, such as risk assessments, vulnerability management, and incident response.
- Cross-functional collaboration: Foster collaboration and communication among multidisciplinary teams involved in cybersecurity, risk management, compliance, and business operations to leverage FMEA insights effectively.
- Iterative approach: Adopt an iterative approach to FMEA analysis, continuously updating and refining risk assessments, mitigation strategies, and action plans based on changing threats, technologies, and business requirements.
- Automation and tools: Utilize automation tools, software platforms, and technology solutions to streamline FMEA activities, capture data, and facilitate real-time collaboration and decision-making.
Final thoughts
FMEA is instrumental in fortifying cybersecurity posture by systematically identifying, assessing, and mitigating potential failure modes and their impacts. By prioritizing risks and developing targeted mitigation strategies, organizations can enhance resilience against cyber threats, ensuring the integrity and availability of their critical assets and operations. We discussed a step-by-step process in which you can apply FMEA in your organization.
Embrace FMEA as a proactive approach to cybersecurity risk management. Commit to its ongoing utilization to optimize resource allocation, stay ahead of emerging threats, and ensure the long-term security and sustainability of your digital assets and operations.
Elevate your risk management strategy with Scrut's comprehensive platform, enabling efficient identification, evaluation, and mitigation of IT and cyber risks. Utilize Scrut's continuous monitoring, intuitive tools, and robust communication features to stay ahead of evolving threats, empower your team, and engage stakeholders effectively.
FAQs
1. What is Failure Mode and Effects Analysis (FMEA)?
Failure Mode and Effects Analysis (FMEA) is a systematic methodology used to identify potential failure modes within a system, process, or product, along with evaluating their potential effects on operations or outcomes. It aims to proactively identify and prioritize potential failures, determine their causes and effects, and develop strategies to mitigate or eliminate these failures before they occur.
2. Why is FMEA important for organizations?
FMEA is important for organizations because it helps them understand and prioritize risks, enabling informed decision-making, resource allocation, and risk management strategies. By systematically analyzing failure modes and their potential impacts, organizations can develop targeted mitigation strategies, enhance resilience against threats, and improve overall performance.
3. What are the core principles of FMEA?
The core principles of FMEA include a systematic approach to risk assessment, cross-functional collaboration among multidisciplinary teams, proactive risk management aimed at identifying and addressing potential failures before they occur, quantitative analysis to assess the severity, occurrence probability, and detection capability of potential failure modes, continuous improvement through regular review and updating of FMEA analyses, and proper documentation and traceability of FMEA activities.
Table of contents