SOC 2 and your security posture: A CISO's perspective

In the current macroeconomic environment, lower revenues, workforce reduction, and higher production costs are normalized. On one hand, an influx of cybercrime at unprecedented levels necessitates more vigilance, while on the other, the cybersecurity budget is shrinking. The regulators are increasing compliance requirements to standardize cybersecurity practices and gain customer confidence. It’s difficult for the CISOs to maintain the delicate balance between every aspect of modern-day cybersecurity and compliance.
One of the compliance frameworks is SOC 2, or System and Organization Controls 2. SOC 2 compliance helps CISOs address these challenges by providing a robust framework that ensures data security and privacy while streamlining compliance efforts. By aligning with SOC 2 standards, CISOs can enhance cyber resilience and reduce the risk of breaches, even with limited budgets and resources.
SOC 2 also builds customer trust and meets regulatory demands, enabling organizations to effectively balance security with operational efficiency in a cost-constrained environment.
In this article, we will talk about the practical aspects of how SOC 2 affects your security posture and what you can do as the CISO of your organization.
Understanding SOC 2 and its importance for CISOs
SOC 2 is critical for CISOs as it provides a structured framework to manage and safeguard sensitive customer data effectively. The key reasons it matters are:
- Demonstrates security commitment: SOC 2 compliance shows dedication to data security posture management, reassuring clients and stakeholders of robust security practices.
- Boosts trust and competitive advantage: Achieving SOC 2 certification enhances an organization’s reputation, building trust and potentially offering a competitive market advantage.
- Mitigates risk of data breaches: The SOC 2 framework focuses on security principles like availability, processing integrity, confidentiality, and privacy, helping CISOs reduce risks associated with data breaches and unauthorized access.
- Ensures compliance with standards: SOC 2 is crucial for companies handling sensitive data (e.g., customer, financial, or IP data) to comply with industry and regulatory requirements.
- Facilitates better security governance: By undergoing SOC 2 audits, CISOs can ensure security protocols are effectively integrated into organizational policies and that security practices are well-documented and continuously improved.
Read also: SOC 2 compliance: Top 10 challenges and strategies to solve them
Challenges faced by CISOs in 2024
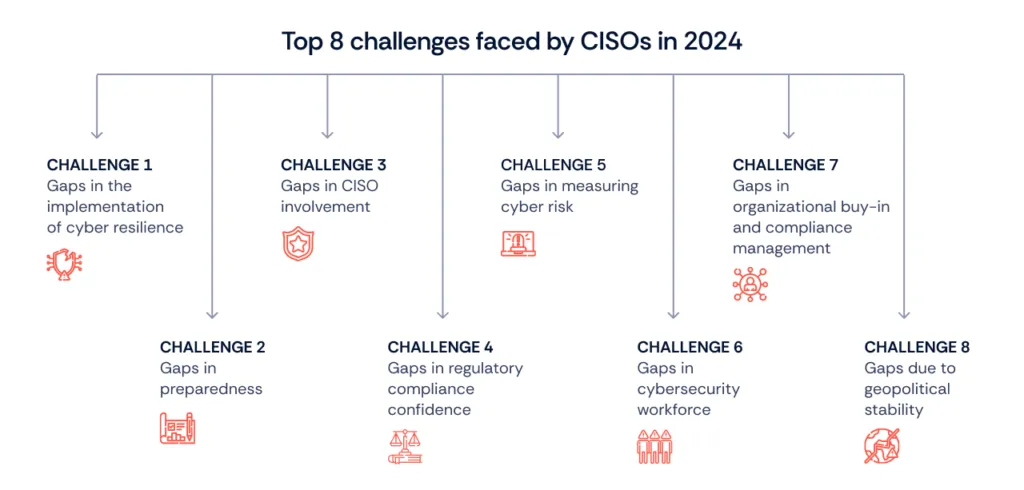
Some of the challenges faced by CISOs in 2024 and beyond are shown below. These challenges require unique solutions to maintain the organization’s cyber security and compliance. Therefore, we suggest some of the best practices you can adopt to align your security programs with SOC 2 requirements:
Challenge 1: Gaps in the implementation of cyber resilience:
In a 2025 Global Digital Trust Insights survey conducted by PwC, it was found that despite the elevated concerns about cyber risks, only 2% of the executives were confident about cyber resilience in their organizations.

Challenge 2: Gaps in preparedness
The top four cyber threats that the PwC survey respondents were most concerned about and, at the same time, unprepared for are cloud security posture management, hack-and-leak operations, third-party breaches, and attacks on connected products. This gap underscores the pressing need for improved investments and enhanced response capabilities.

Read also: Setting your SOC 2 audit up for success
Challenge 3: Gaps in CISO involvement
PwC also reported that less than 50% of executives report that their CISOs play a significant role in strategic planning, board reporting, and managing technology deployments. It’s not always the CISOs, but some organizations don’t involve their CISOs in key initiatives. This gap results in misaligned strategies and weaker security postures.
“Cyber professionals hate all the mandatory training we are forced to take, but somehow we expect others to love our mandatorfy awareness training classes.” – Ross Young, CISO-in-residence, Team8


Challenge 4: Gaps in regulatory compliance confidence
The other C-suites, including CEOs and CSOs, are generally found at different confidence levels than the CISO. PwC found the most significant gaps are in complying with AI, resilience, and critical infrastructure regulations. CISOs, who lead cybersecurity efforts, tend to be less confident than CEOs about their organization’s capability to adhere to these regulatory standards.

Challenge 5: Gaps in measuring cyber risk
Measuring cyber risk in terms of financial terms puts things in perspective for the CEO and other stakeholders. However, how many CISOs do it? Well, PwC found that only 15% of organizations are actually doing it to a significant extent. That’s painfully low, as when CEOs and board members look at how cyber risk will affect their balance sheet, they would be more willing to invest in cybersecurity.
“Where you spend your time and resources should be driven entirely by metrics,” said Nicole Ford, svp and CISO, Nordstrom.

Challenge 6: Gaps in cybersecurity workforce
57% of workers say shortages at their organization put them at moderate or
extreme risk of cybersecurity attacks (ISC2 Cybersecurity Workforce Study 2023). It says that there was a 12.6% year-on-year increase in the gap in the global cybersecurity workforce leading to a total of 3,999,964 people.
The high gap, coupled with frequent layoffs, hiring freezes, and budget cuts, results in skyrocketing costs of hiring and retaining efficient cybersecurity experts. 43% of the respondents of the above study stated that the world will face a cybersecurity workforce gap for the next couple of years. So, as a CISO, you will have to deal with it.
“Too many organizations approach SOC talent as entry-level,” said John McClure, CISO, Sinclair Broadcast Group. “Sometimes the ‘right’ talent might need to have more experience.”

Challenge 7: Gaps in organizational buy-in and compliance management
Ensuring organizational support for compliance initiatives is crucial. CISOs need buy-in from leadership and other departments, which can be challenging as they may not fully understand the value of SOC 2 compliance or the associated requirements. Silentbreach conducted a survey and 39% of cybersecurity professionals held a lack of organizational buy-in responsible for their sleepless nights.

Challenge 8: Gaps due to geopolitical stability
Global events and cyber threats stemming from geopolitical tensions pose significant risks to organizations. CISOs must ensure that security strategies are agile enough to adapt to new threats and regulatory requirements. The latest report by PwC indicates that there is an elevated risk of 49% in cyber risk (at the time this article was written) due to the recent geopolitical challenges the world is facing.
“AI helps us search through current Internet data and delivers customized responses when new threats or industry incidents arise. This serves as an alternative to manually navigating through discussion groups, technical news websites, and newsfeeds,” said Cassio Goldschmidt, CISO, ServiceTitan.

Read also: Becoming SOC 2 audit ready with SOC 2 readiness assessments
CISO strategies for a strong SOC 2 security posture
“Define your business objectives,” said Tomer Gershoni, former CISO, ZoomInfo. “This allows determination of SOC characteristics such as the most critical systems you need to monitor, minimum viable level of audit logs, and the number of analysts needed.”
Leveraging SOC 2 as a baseline to go beyond compliance, CISOs can adopt several proactive security measures to improve SOC efficiency and effectiveness:
1. Leveraging SOC 2 beyond compliance
SOC 2 serves as more than just a compliance standard; it’s a framework for enhancing overall security posture. CISOs can use it to assess and improve their organization’s risk management and data protection strategies.
How Scrut Helps: Scrut enables efficient SOC 2 audit completion with pre-built controls, making it easier to maintain compliance while focusing on broader security goals.
2. Implementing proactive security measures
Implementing SOC 2 security controls proactively helps organizations identify and mitigate potential risks before they impact operations. Monitoring, incident response, and continuous risk assessments are key strategies.
How Scrut Helps: Scrut’s automated tools offer continuous monitoring and real-time insights, ensuring that security risks are promptly identified and addressed.
3. Creating an actionable roadmap
A roadmap for continuous SOC 2 compliance is vital. It includes setting achievable milestones, regular audits, and iterative improvements to ensure ongoing adherence to SOC 2 principles.
How Scrut Helps: Scrut simplifies the process of maintaining an actionable roadmap with its platform, helping CISOs track progress and compliance requirements efficiently.
4. Establishing a culture of continuous security improvement
Continuous improvement is critical to addressing emerging threats. Regular training, awareness programs, and shared responsibility for security across the organization foster a strong security culture.
How Scrut Helps: Scrut streamlines compliance management, reducing manual efforts and allowing teams to focus on enhancing their security processes and cultivating a culture of compliance.
Read also: Demystifying SOC 2 audit exceptions: Challenges and solutions
Cost, timeline, and resource allocation in SOC 2 preparation
CISOs frequently face budget limitations, requiring them to maximize efficiency by automating key processes, minimizing reliance on costly consultants, and optimizing the audit process.
Dr. Andrew Aken, CIO and vCISO, DocDrew LLC, says: “Automation will dramatically increase the quality of work, and focus can turn to the most serious or unique incidents.”
1. Cost management and efficiency
CISOs must allocate financial resources efficiently, focusing on tools and strategies that maximize cost-effectiveness. Investments in automation and technology can reduce manual tasks, lowering the need for expensive consultants and minimizing the costs associated with audits and compliance efforts.
Investing in compliance platforms like Scrut can reduce the unnecessary burdens of manual processes and give you access to compliance experts at a much lower cost than hiring a consultant.
Read also: What is the cost of a SOC 2 audit?
2. Balancing the timeline and compliance priorities
Defining a clear SOC 2 timeline is key to avoiding delays. A step-by-step approach, including identifying the scope, choosing Trust Service Criteria, and preparing policies, helps keep the process aligned with business priorities while ensuring thorough compliance. Efficient planning reduces last-minute scrambling and supports timely audit readiness.
Scrut can significantly reduce the time to SOC 2 certification. It can guide you through all the intricacies of the SOC 2 audit so that you can get the certification with the least amount of effort.
3. Efficient engagement of personnel
Engaging the right personnel from various departments (IT, legal, compliance) at appropriate stages is crucial. A CISO needs to identify responsibilities early on and ensure all relevant stakeholders are involved to address all areas of compliance, avoiding gaps and redundancies.
The SOC 2 experts at Scrut carry out gap assessments to point out the shortcomings in your systems. They also give you the assistance you need to overcome these shortcomings so that you are ready for your SOC 2 audit. Only when the Scrut experts are satisfied that you are ready for the external audit, they will call in the external auditor to certify your organization.
“Don’t view the people in the SOC in isolation. They need to know who to reach out to, based on what they are seeing,” said Dennis Pickett, vp and CISO, Westat, who suggested that you “designate someone on the security team to be the lead for interactions with the network operations team.”
4. Cost-effective compliance
Addressing resource constraints and budget issues is critical. Highlighting the cost benefits of early compliance investment can mitigate risks and provide long-term savings by avoiding potential security breaches or compliance fines.
Scrut can not only help with SOC 2 but also with more than 50 other frameworks. Consolidating your compliance efforts can reduce the burden of evidence collection. The evidence you collect for one framework can also be used for other frameworks and standards, minimizing your efforts.
Read also: GRC Management Platforms: How to Evaluate ROI and Maximize Your Investment
Conclusion: Looking beyond compliance
In summary, SOC 2 compliance is a crucial benchmark for regulatory adherence and a framework for strengthening a company’s security posture. As cyber threats and economic pressures rise, CISOs must ensure robust cybersecurity despite limited resources. SOC 2 provides a structured approach to managing these challenges, securing sensitive data, building trust, and aligning security practices with business goals.
By leveraging SOC 2 principles, CISOs can proactively mitigate cyber risks and foster a culture of continuous improvement. Tools like Scrut streamline compliance efforts, enabling a security-first mindset. Viewing SOC 2 as more than a checklist allows CISOs to create lasting organizational value, enhancing resilience and laying a strong foundation for future growth.
Achieve SOC 2 compliance effortlessly with Scrut! Our compliance automation platform streamlines your SOC 2 tasks, ensuring a quick and hassle-free audit process. Start your journey to SOC 2 compliance today and strengthen your organization’s security posture!
FAQs
1. How do you describe a security posture?
According to NIST (National Institute of Standards and Technology), “security posture” refers to the security status of an organization’s information systems, based on the resources and policies designed to prevent, detect, and respond to cyber threats and vulnerabilities. It encompasses the overall state of security readiness, including technology, processes, and controls implemented to safeguard data, applications, and infrastructure against security breaches and attacks.
2. What are the SOC 2 security standards?
SOC 2 security standards are part of a compliance framework that specifies how organizations should handle and protect customer data. These standards ensure that third-party service providers store, process, and manage client data securely by establishing criteria for the secure handling of this data.
3. What are the 5 principles of SOC 2?
The five Trust Services Criteria (TSC) or principles of SOC 2 include:
‣ Security – The system is protected against unauthorized access.
‣ Availability – The system is available for operation and use as agreed.
‣ Processing Integrity – System processing is complete, valid, accurate, and authorized.
‣ Confidentiality – Information is protected as committed or agreed upon.
‣ Privacy – Personal information is collected, used, retained, and disclosed in line with the organization’s privacy notice and principles.
4. What is the CISO security strategy?
A CISO (Chief Information Security Officer) security strategy is a plan that helps manage and mitigate security risks within an organization. It typically focuses on reducing security gaps, improving visibility into threats, and ensuring compliance with various security standards. A solid security strategy aligns with the organization’s business goals and mitigates risks while adhering to regulatory requirements.
5. What are the 4 faces of the CISO?
While the search results do not provide a direct answer, the “4 faces of the CISO” generally refer to the different roles a CISO might take on:
‣ Strategist – Aligns security efforts with business objectives.
‣ Operator – Oversees the day-to-day implementation of security programs.
‣ Technologist – Focuses on the use of technologies to address cybersecurity risks.
‣ Guardian – Acts as a protector of the organization’s assets, ensuring adherence to compliance and policies.


















