Unburdening security questionnaires: A guide to streamlining third-party assessments

Security questionnaires have become an indispensable tool for organizations seeking to fortify their defenses against potential cyber threats. They also play a pivotal role in demonstrating an organization’s commitment to safeguarding sensitive information.
These questionnaires, often utilized by customers and partners, serve as a crucial tool for assessing an organization’s security protocols, certifications, and compliance measures.
However, with the growing importance of these questionnaires comes a set of challenges. Organizations often grapple with the sheer volume and complexity of these assessments, consuming valuable time and resources. The intricate nature of questionnaire responses, coupled with varying industry standards, can pose hurdles in achieving consistent and efficient compliance.
In this blog, we delve into the intricacies of security questionnaires, exploring their significance in establishing trust, the inherent challenges they present, and the pressing need for a more streamlined alternative.
What are security questionnaires?
A security questionnaire is a set of written questions designed to assess and evaluate the security practices, policies, and measures implemented by an individual, organization, or third-party service provider.
These questionnaires are commonly used in various contexts, including information security assessments, vendor risk management, compliance audits, and cybersecurity evaluations. The goal is to gather information about the entity’s security posture and identify potential vulnerabilities, risks, and areas for improvement.
What topics do security questionnaires cover?
The questions in a security questionnaire typically cover a wide range of topics related to information security, such as:
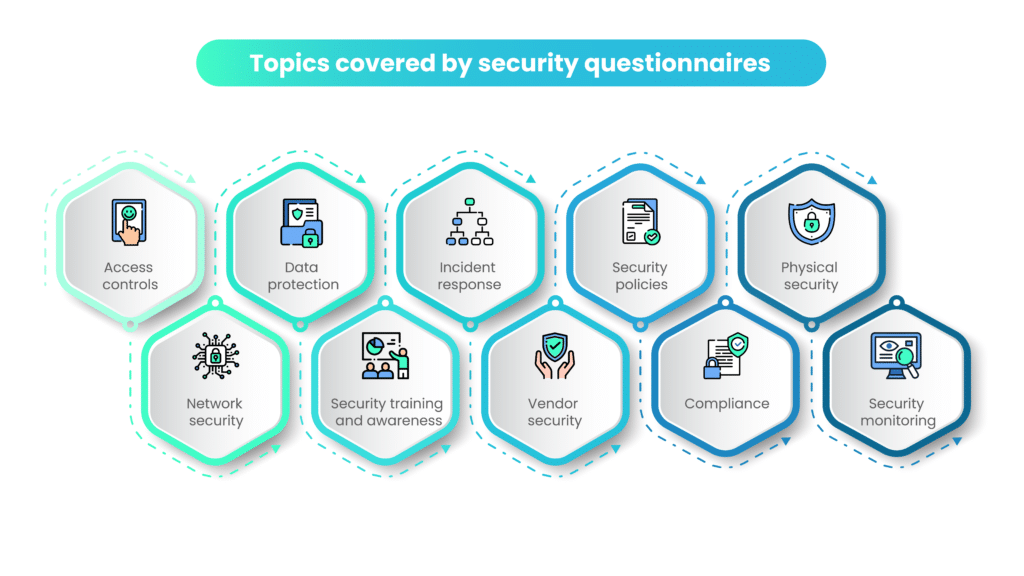
A. Access controls
Security questionnaires inquire about the measures an organization has in place to control access to its systems and sensitive information.
This involves understanding the authentication methods (e.g., passwords, biometrics) and authorization mechanisms used to manage user access.
It seeks to assess the effectiveness of these controls in preventing unauthorized access.
B. Data protection
In the realm of security questionnaires, data protection queries revolve around how sensitive information is handled.
This includes questions about data classification practices, encryption methods employed for data at rest and in transit, and mechanisms to ensure data integrity.
Security questionnaires aim to evaluate the organization’s commitment to safeguarding sensitive data throughout its lifecycle.
C. Incident response
Security questionnaires explore an organization’s incident response capabilities. This involves questions about the existence of an incident response plan, procedures for detecting and responding to security incidents, and recovery processes.
The goal is to assess the organization’s preparedness to manage and mitigate the impact of security breaches.
D. Security policies
Questions related to security policies in vendor security questionnaires seek to understand the documentation and communication of security guidelines within the organization.
They explore whether there are established policies and procedures, how these are communicated to employees, and the measures in place to ensure adherence to these policies.
E. Physical security
In the context of security questionnaires, physical security inquiries focus on how an organization controls physical access to its facilities and equipment.
This includes questions about access control measures, surveillance systems, and visitor management.
Security questionnaires aim to evaluate the effectiveness of physical security in preventing unauthorized access.
F. Network security
Security questionnaires delve into an organization’s network security practices. This involves questions about the measures in place to secure the network infrastructure, including firewalls, intrusion detection/prevention systems, and secure configurations.
Security questionnaires assess the organization’s ability to protect against unauthorized access and cyber threats.
G. Security training and awareness
Queries about security training and awareness in a questionnaire aim to assess the organization’s efforts to educate employees about security best practices.
This includes questions about training programs, awareness initiatives, and the integration of security education into onboarding processes.
H. Vendor security
Vendor security questionnaires focus on assessing the security measures implemented by third-party service providers.
This includes inquiries about the evaluation of vendor security, contractual agreements specifying security requirements, and adherence to industry standards.
Third-party security questionnaires aim to ensure that vendors align with the organization’s security standards.
I. Compliance
Security questionnaires explore an organization’s compliance with relevant regulatory requirements and industry standards.
This involves questions about the measures in place to comply with laws and regulations, as well as adherence to established security standards.
Security questionnaires aim to verify that the organization meets legal and industry-specific security obligations.
J. Security monitoring
Inquiries related to security monitoring in a questionnaire aim to understand how an organization continuously monitors for security events and potential threats.
This includes questions about monitoring tools, intrusion detection systems, and processes for identifying and responding to security incidents.
Security questionnaires assess the organization’s vigilance in safeguarding against evolving security threats.
The Crucial role of security Questionnaires
Security questionnaires serve as more than just a routine administrative task; they are a dynamic and essential aspect of modern cybersecurity practices. Let’s delve into the multifaceted role played by security questionnaires:
A. comprehensive evaluation by stakeholders
Customers and partners wield security questionnaires as a powerful tool for conducting a comprehensive evaluation of an organization’s cybersecurity infrastructure.
These questionnaires are meticulously crafted to probe various facets of security, ranging from data protection measures to incident response plans.
By seeking detailed information on security policies, data handling practices, and disaster recovery protocols, stakeholders aim to gauge the robustness of an organization’s defense mechanisms.
B. Validation of security protocols
Security questionnaires act as a validation mechanism for an organization’s declared security protocols. Customers and partners want assurance that the stated security measures align with industry best practices and regulatory standards.
As such, these assessments delve into the specifics of encryption methods, access controls, and authentication procedures, providing stakeholders with insights into the organization’s commitment to maintaining a secure environment.
C. Verification of certifications and compliance
For many industries, adherence to specific certifications and compliance standards is non-negotiable.
Security questionnaires become a means for stakeholders to verify the organization’s claims of certifications such as ISO 27001, SOC 2, PCI DSS, HIPAA, and others.
This verification process is crucial in establishing trust and confidence in the organization’s ability to meet industry-specific security requirements.
D. Assessment of data handling practices
Given the increasing concerns regarding data privacy, customers and partners use security questionnaires to assess an organization’s data handling practices.
These assessments delve into data storage procedures, data access controls, and the measures in place to mitigate the risk of unauthorized access or data breaches.
The goal is to ensure that sensitive information is handled with the utmost care and in compliance with privacy regulations.
E. Demonstration of transparency and accountability
Perhaps most importantly, security questionnaires serve as a tangible representation of an organization’s commitment to transparency and accountability.
By willingly providing detailed information about security practices, an organization signals its openness and dedication to maintaining a secure operational environment.
This transparency is fundamental in building trust, as it allows stakeholders to make informed decisions based on a thorough understanding of the organization’s cybersecurity posture.
F. Establishment of trustworthy partnerships
In the modern interconnected business landscape, partnerships are forged on the foundation of trust.
Security questionnaires become a crucial element in this trust-building process, enabling organizations to showcase their commitment to security and demonstrate their suitability as trustworthy partners.
A robust response to these assessments not only satisfies the immediate inquiries of customers and partners but sets the stage for enduring and reliable collaborations.
Challenges organizations face when filling out security questionnaires
Responding to security questionnaires can be a burdensome process. Organizations often encounter several challenges when filling out security questionnaires. These challenges can vary based on the nature of the questionnaire, the industry, and the specific security requirements. Here are some common challenges faced by organizations:
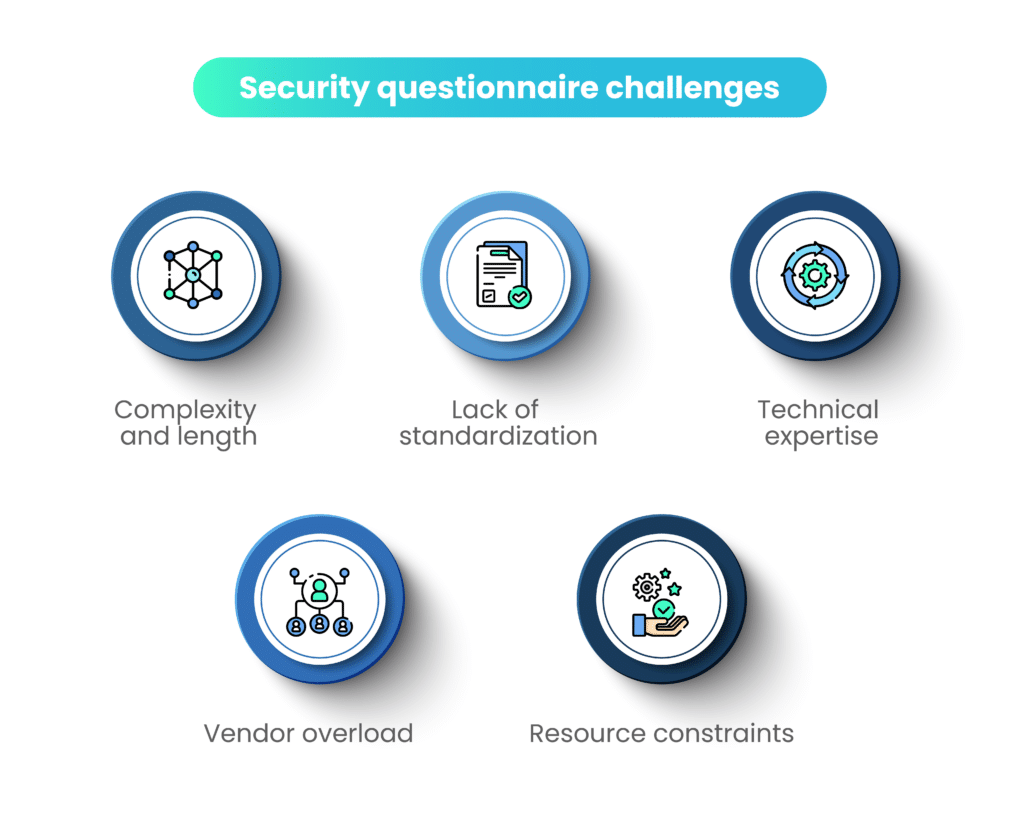
A. Complexity and length
Security questionnaires can be lengthy and complex, requiring a significant amount of time and resources to complete. Organizations may find it challenging to allocate the necessary resources while managing their day-to-day operations.
B. Lack of standardization
There is often a lack of standardization in security questionnaires. Different organizations or clients may use different formats and questions, making it difficult for companies to streamline the process and maintain consistency in their responses.
C. Technical expertise
Answering technical security questions may require specialized knowledge and expertise. Some organizations may struggle to find the right personnel who can accurately address the technical aspects of security assessments.
D. Resource constraints
Small and medium-sized enterprises (SMEs) may face resource constraints, both in terms of personnel and budget. As a result, they may find it challenging to meet the security requirements outlined in questionnaires.
E. Changing threat landscape
The cybersecurity landscape is dynamic, with new threats emerging regularly. Organizations may find it challenging to keep up with evolving security requirements and may need to continuously update their security practices.
F. Vendor overload
For companies dealing with multiple clients or partners, each with its security questionnaire, there may be a sense of overload. Managing and responding to numerous questionnaires can be time-consuming and may divert attention from other critical security tasks.
G. Interpretation of questions
The wording of security questions may be ambiguous or open to interpretation. Organizations may struggle to understand the specific intent behind certain questions, leading to challenges in providing accurate and relevant information.
H. Third-party dependencies
Organizations often rely on third-party vendors for various services. Coordinating responses to security questionnaires with these vendors can be challenging, especially if they are not well-prepared or have different security practices.
I. Regulatory compliance
Meeting regulatory compliance requirements can be a significant challenge. Organizations operating in multiple jurisdictions may need to navigate a complex web of regulations, each with its own set of security standards and requirements.
J. Documenting security controls
Some questionnaires require organizations to provide detailed documentation of their security controls and processes. Ensuring that all relevant information is documented and up to date can be time-consuming and demanding.
Best practices for answering security questionnaires effectively
To overcome the challenges associated with answering security questionnaires, organizations can implement several strategies and best practices. Here are some recommendations:
A. Establish a comprehensive cybersecurity program
Organizations can overcome the challenges of security questionnaires by developing and implementing a robust cybersecurity program. This program should encompass policies, procedures, and controls that align with industry best practices and regulatory requirements. By laying a strong foundation for security practices, organizations can address questionnaire inquiries more effectively.
B. Assign a dedicated security team
Assigning a dedicated team or individuals with specific responsibilities for handling security questionnaires is crucial. This team should possess the necessary expertise to understand and respond to technical security inquiries. Having a focused and knowledgeable team streamlines the response process and ensures accuracy.
C. Invest in employee training and awareness
Regular training sessions for employees play a pivotal role in enhancing awareness of security practices and compliance requirements. Well-informed personnel responsible for completing questionnaires are better equipped to provide accurate and relevant information, reducing the likelihood of errors.
D. Develop standardized responses
To streamline the questionnaire response process, organizations should develop standardized responses to common security questions. This approach ensures consistency across different assessments and facilitates a more efficient and organized approach to addressing security inquiries.
E. Centralize documentation of security controls
Maintaining centralized documentation of security controls, policies, and procedures is essential. This repository should be regularly updated and easily accessible. Having a centralized source of information expedites the response process and ensures that the documentation is current and accurate.
F. Leverage automation tools
Implementing automation tools and solutions can significantly streamline the questionnaire response process. Automation helps reduce the time and effort required to gather and present information, especially for routine or recurring questionnaires. This approach enhances efficiency and accuracy.
G. Collaborate with third-party vendors and legal teams
Close collaboration with third-party vendors and partners is essential for a coordinated response to security questionnaires. Additionally, involving legal and compliance teams ensures that responses align with contractual obligations, legal requirements, and industry standards.
H. Adopt a risk-based approach
Prioritizing responses based on risk is a strategic approach. Identifying critical security controls and focusing on providing detailed information where it matters most allows organizations to allocate resources effectively and address high-priority security concerns.
I. Implement continuous monitoring and improvement
Continuous monitoring practices help organizations stay informed about changes in the threat landscape and regulatory requirements. Regular updates to security processes and controls based on emerging threats and industry best practices contribute to a more resilient security posture.
J. Foster open communication
Establishing open lines of communication with clients, partners, or regulatory bodies issuing security questionnaires is crucial. Proactive communication regarding the organization’s commitment to security and willingness to address concerns fosters stronger relationships and builds trust.
K. Leverage established security frameworks
Adopting established security frameworks, such as ISO 27001 or the NIST Cybersecurity Framework, provides a structured foundation for security practices. These frameworks guide organizations in developing robust security controls and processes, facilitating more comprehensive and informed questionnaire responses.
Best practices for creating a security questionnaire
Creating an effective security questionnaire involves careful planning, thoughtful design, and a focus on gathering relevant and actionable information. Here are the key steps to create an effective security questionnaire:
A. Define objectives
Clearly define the objectives of the security questionnaire. Understand the purpose, scope, and specific information you aim to gather. Align the questionnaire with your organization’s security policies, compliance requirements, and risk management goals.
B. Identify stakeholders
Determine the stakeholders who will be involved in or affected by the security questionnaire. This includes internal teams, third-party vendors, or partners. Tailor questions to the audience and ensure that the questionnaire addresses their specific concerns and responsibilities.
C. Customize for context
Customize the questionnaire based on the context of the assessment. Consider the industry, regulatory requirements, and the specific security concerns relevant to your organization. Tailoring questions to the context ensures that the collected information is meaningful and applicable.
D. Use a structured format
Organize the questionnaire in a structured format, grouping related questions together. Use clear headings, subheadings, and numbering to enhance readability. A well-organized format helps respondents understand the flow and structure of the questionnaire.
E. Focus on clear and specific questions
Craft questions that are clear, specific, and unambiguous. Avoid vague or open-ended language that can lead to misinterpretation. Clearly articulate the information you are seeking, making it easier for respondents to provide accurate and relevant answers.
F. Prioritize questions based on risk
Prioritize questions based on the risk they address. Identify critical security controls and focus on obtaining detailed information in those areas. This risk-based approach ensures that the questionnaire is efficient and targets high-priority security concerns.
G. Include a mix of question types
Use a mix of question types, including multiple-choice, yes/no, and open-ended questions. This variety allows for flexibility in responses and provides a comprehensive view of security practices. Open-ended questions can capture nuanced details and insights.
H. Avoid redundancy
Review the questionnaire to eliminate redundant or duplicate questions. Redundancy can lead to survey fatigue and may result in inconsistent responses. Streamline the questionnaire to focus on essential information without unnecessary repetition.
I. Incorporate legal and compliance considerations
Include questions that address legal and compliance considerations relevant to your organization. Ensure that the questionnaire aligns with contractual obligations, industry standards, and applicable regulations to support a comprehensive assessment.
J. Pilot test the questionnaire
Before widespread distribution, conduct a pilot test of the questionnaire with a small group of respondents. This helps identify any ambiguities, misunderstandings, or areas where improvements are needed. Use feedback from the pilot to refine and finalize the questionnaire.
K. Provide clear instructions
Include clear instructions at the beginning of the questionnaire to guide respondents on how to complete it. Clarify any specific terms or definitions and provide contact information for inquiries. Clear instructions contribute to the accuracy and efficiency of responses.
L. Review and update regularly
Security landscapes evolve, so regularly review and update the questionnaire to ensure it remains relevant and aligned with current security practices, threats, and compliance requirements. Periodic revisions help maintain the effectiveness of the questionnaire over time.
Are there alternatives to security questionnaires?
The traditional reliance on security questionnaires is increasingly criticized for its time-consuming nature, repetitiveness, and the toll it takes on engineering teams’ valuable time that could otherwise be dedicated to product development.
The prolonged process of filling out repetitive security questionnaires not only hampers efficiency but also diverts essential engineering resources away from innovation and product advancement.
In contrast, tools like Scrut’s Trust Vault emerge as a transformative solution, providing a singular platform to expedite certification and report requests.
Trust Vault streamlines the demonstration of security protocols, offering real-time transparency into security and compliance postures.
By efficiently managing subprocessors and ensuring up-to-date communication with customers, Trust Vault becomes a dynamic alternative that not only saves time but also enhances the overall productivity of engineering teams, enabling them to focus on building and improving products without the cumbersome burden of traditional security questionnaire processes.
Conclusion
As organizations increasingly rely on interconnected systems and data sharing, the importance of comprehensive security assessments cannot be overstated.
By adopting a strategic approach to answering security questionnaires, businesses can not only streamline the process but also demonstrate their commitment to safeguarding sensitive information.
Efficiency in responding to security questionnaires involves understanding the unique requirements of each inquiry, leveraging existing security protocols, and maintaining a proactive stance toward continuous improvement. Through a well-defined and standardized approach, organizations can enhance their ability to convey their security posture accurately and efficiently.
Security questionnaires are not the only means to build trust with your customers and third parties. Discover the impactful capabilities of Scrut’s Trust Vault! Schedule a demo today!
FAQs
1. What is the purpose of security questionnaires?
Security questionnaires are designed to assess and evaluate the security practices, policies, and measures implemented by individuals, organizations, or third-party service providers. They are commonly used in various contexts such as information security assessments, vendor risk management, compliance audits, and cybersecurity evaluations to gather information about an entity’s security posture and identify potential vulnerabilities, risks, and areas for improvement.
2. What topics do security questionnaires typically cover?
Security questionnaires cover a broad range of topics related to information security, including access controls, data protection, incident response, security policies, physical security, network security, security training and awareness, vendor security, compliance, and security monitoring. These questions aim to assess the organization’s commitment to safeguarding sensitive information and its preparedness to manage and mitigate security risks.
3. How do security questionnaires contribute to building trust with stakeholders?
Security questionnaires play a crucial role in building trust by providing a comprehensive evaluation of an organization’s cybersecurity infrastructure. They validate an organization’s declared security protocols, verify certifications and compliance with industry standards, assess data handling practices, demonstrate transparency and accountability, and establish trustworthy partnerships through thorough and reliable collaborations.
4. What challenges do organizations face when filling out security questionnaires?
Organizations often encounter challenges such as the complexity and length of questionnaires, lack of standardization, technical expertise requirements, resource constraints, changes in the threat landscape, vendor overload, interpretation of questions, third-party dependencies, regulatory compliance, and the need for documenting security controls.
5. What are the best practices for answering security questionnaires?
Best practices for answering security questionnaires include establishing a comprehensive cybersecurity program, assigning a dedicated security team, investing in employee training and awareness, developing standardized responses, centralizing documentation of security controls, leveraging automation tools, collaborating with third-party vendors and legal teams, adopting a risk-based approach, implementing continuous monitoring and improvement, fostering open communication, and leveraging established security frameworks.


















