Rebranding announcement: Strengthening our commitment towards simplifying infosec for organizations

Today is a big day for all of us at Scrut Automation. We have officially taken a new look, and a new identity, which we are all super excited about.
We started Scrut Automation with one goal in mind – simplifying information security for cloud-native organizations. What that meant for most of our customers was to help them streamline their information security processes, to help them establish strong and robust security postures in line with industry-leading frameworks like SOC 2, ISO 27001, GDPR, and so on.
And we did that well. We built products, features, and networks that help our customers get compliant faster, with minimal effort and pain. Below is a quick snapshot of what we built to enable 100+ high-growth organizations to get compliant with 21 standards like SOC 2, ISO 27001, GDPR, CMMC, NIST, and the like, and to support them across a cumulative of 400+ assessments:
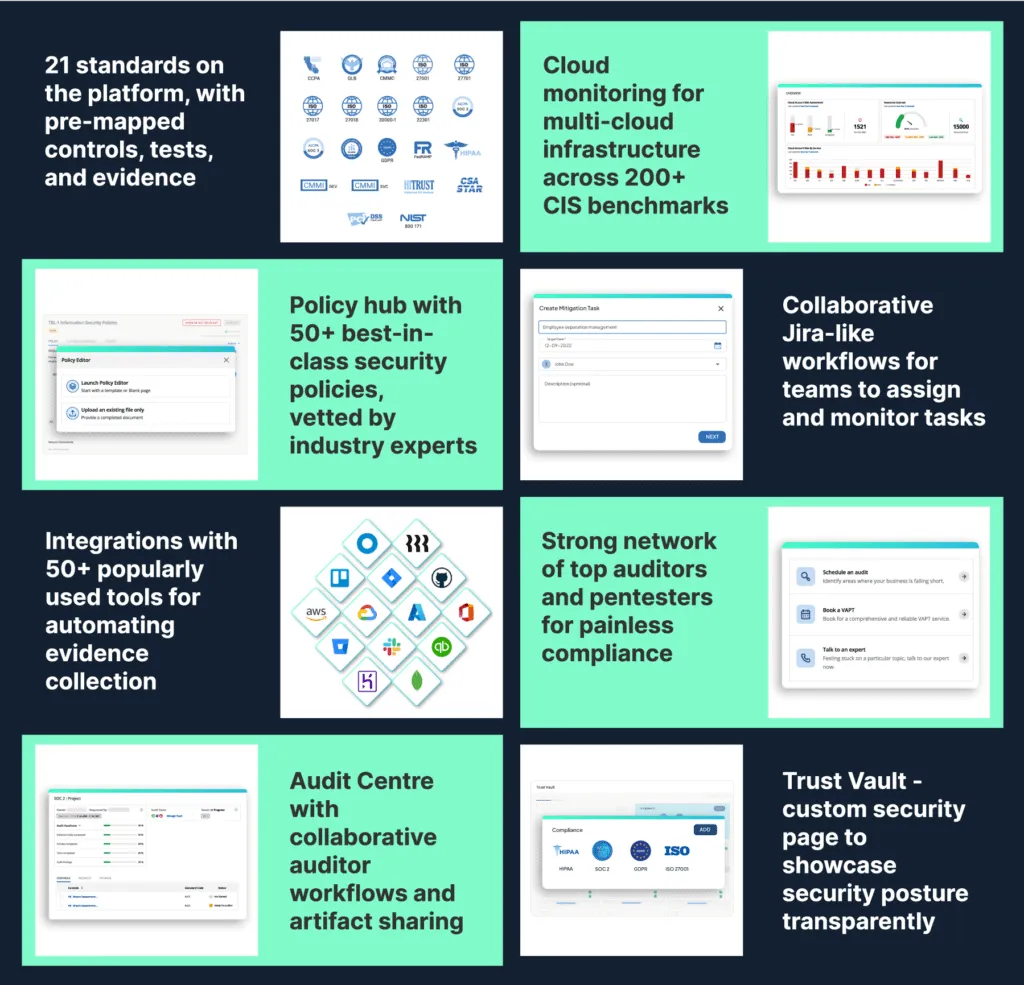
While this generated a lot of value for our customers (check out our G2 reviews) and gave us a lot of joy, we realized something was amiss.
Through the hundreds of hours spent speaking with founders, engineering teams, information security teams, CISOs, compliance officers, and auditors – there were a few fundamental learnings:
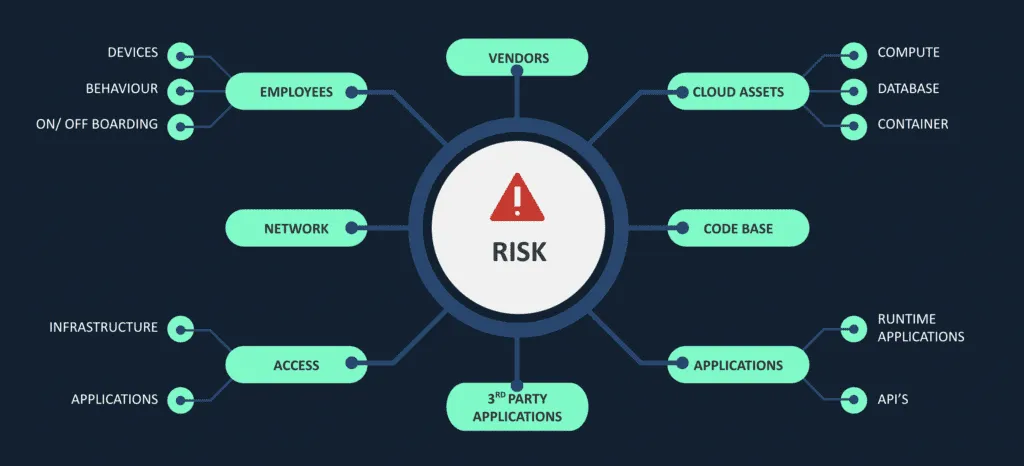
Risk visibility is limited
Most organizations do not have a realistic view of their potential risks and how to manage them. Be it cyber-assets, infrastructure and application landscape, their own employees, or their vendors – risk is distributed. And some are more critical than others.
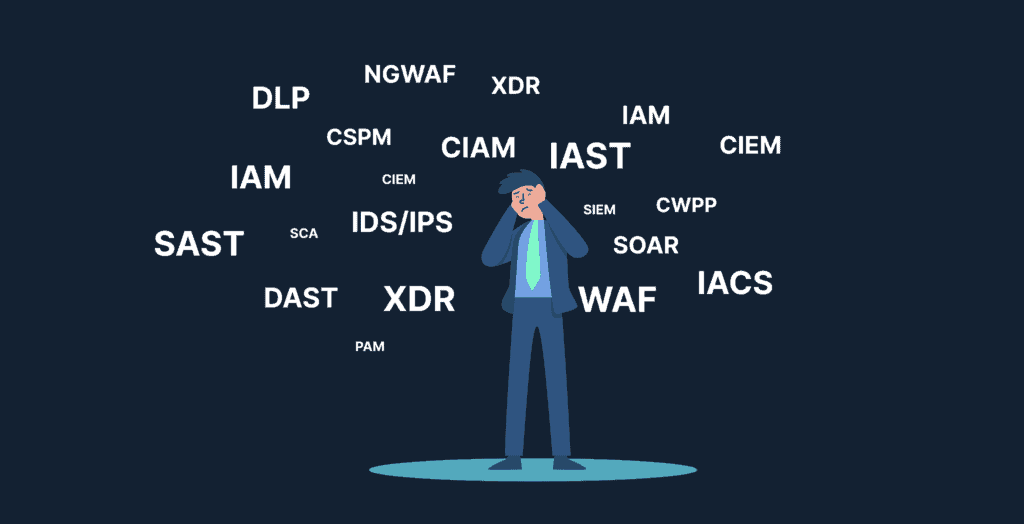
Tool fatigue and acronym fatigue are real
Organizations are dealing with multiple tools, and many of them are excellent ones at that. Don’t get us wrong – we adore some of these platforms. Snyk, Veracode, Okta, strongDM, Tenable, Blissfully, etc., are undoubtedly some of the leaders across these ‘acronym categories’, and organizations we personally draw a lot of inspiration from. However, this does not really solve the crux of the problem – gaining complete visibility of the risks an organization faces.
Controls do not talk to risks
This is inevitable. Without complete visibility of risks, organizations often only have one recourse – look at industry compliance frameworks for guidance. But the frameworks are just that. Your controls need to focus on where you see the most risk – the areas which are most critical for your business. At the same time, without complete risk visibility, you spend uncountable hours developing and enforcing controls on areas that are not as critical.
Audits for multiple standards come with repetitive overheads
Establishing independent controls established for an organization’s security posture and mapping them to individual frameworks’ or standards’ controls requires a significant amount of manual effort. What makes it more painful is that it is repetitive. For instance, >75% of the controls in ISO 27001 and SOC 2 overlap in some way, but for each of these audits, the compliance team needs to map out their controls to the standard’s controls and showcase proof of compliance, often resulting in hours and hours of extraneous non-value-adding manual effort.
It’s difficult to identify what needs fixing
Without complete visibility of risks, compliance, engineering, HR, admin, and other teams spend days, if not months on making changes that are incremental at best, overlooking often critical fixes. Prioritization of effort goes for a toss, which eventually results in loss of productive hours and/or potential vulnerabilities waiting to be exploited.
We realized that we would not be true to our mission without addressing all five. We are moving towards helping organizations across the globe build risk-first information security. By building a risk-first information security posture, organizations can be assured of a robust information security posture, and inevitably be compliant with all necessary and relevant standards, enabling them to accelerate those valuable deals.
Hence the need for a new identity. And the new brand.
In one short image, our new and updated approach to information security:
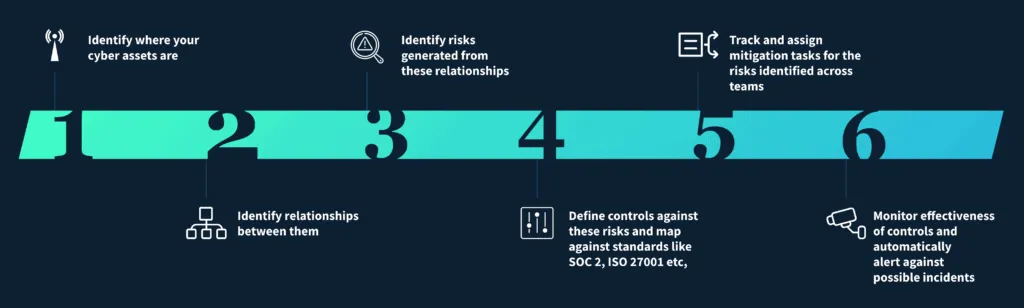
Over the last couple of quarters, our product and engineering teams have built some excellent products and features to help realize these goals. A quick snapshot:
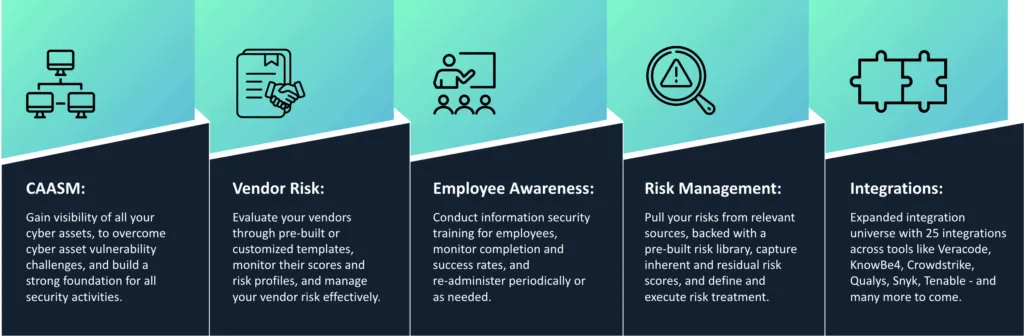
We are very thrilled to be on this new path – and hope to replicate the success we have seen in the past.


















