Choose risk-first compliance that’s always on, built for you.
Go back to blogs
7 reasons why proactive third-party risk management is necessary
Last updated on
September 27, 2023
7
min. read

Your relationship with your vendor is an important one. Like all relationships, the one you share with your vendor has its share of both the good and the bad.
The good: They provide a wide range of products and services–from IT systems and software to logistical support and supply chain management.
The bad: They have the potential to expose your company to security threats that compromise its data and ruin its reputation.
Like a well-meaning friend who knows your most embarrassing childhood stories, vendors have to be managed carefully, to avoid exposing your organization's sensitive information.
This makes vendor risk management a dire need that has to be addressed constantly and proactively.
In this blog, we explore why proactive third party risk management is an absolute necessity and learn some best practices that make it effective.
What is third-party risk management?
Third party risk management involves the assessment and monitoring of risks associated with vendors, suppliers, contractors, and other external entities that have access to an organization's data, systems, or operations.
In the past, organizations usually opted for a reactive approach to risk management, addressing issues only after they occurred. However, no company can survive with such a strategy (or the lack of it) in today's security landscape.
With the dawn of digitalization, data has become decentralized, requiring the involvement of an increasing number of third parties in most organizations' critical operations. Due to this, a large amount of organizational risk lies outside a company's immediate control, making proactive third party vendor risk management an absolute need.
Why is proactive third party risk management necessary?
As an organization increases its use of vendors, it increases its vulnerability to external threats. A proactive third-party risk management program should be on top of the list of priorities when it comes to vendor management.
Good vendor risk management begins even before onboarding a vendor, with thorough background checks and due diligence, and continues throughout their lifecycle, with constant monitoring and evaluations. Thorough vendor risk assessments should be carried out regularly to make sure that vendors are on top of their game when it comes to security.
A proactive third party risk management program will implement both risk management and risk mitigation strategies and leave little room for vendor-related security incidents.
Here are some key reasons why proactive third-party risk management is non-negotiable when it comes to an organization's security and compliance.
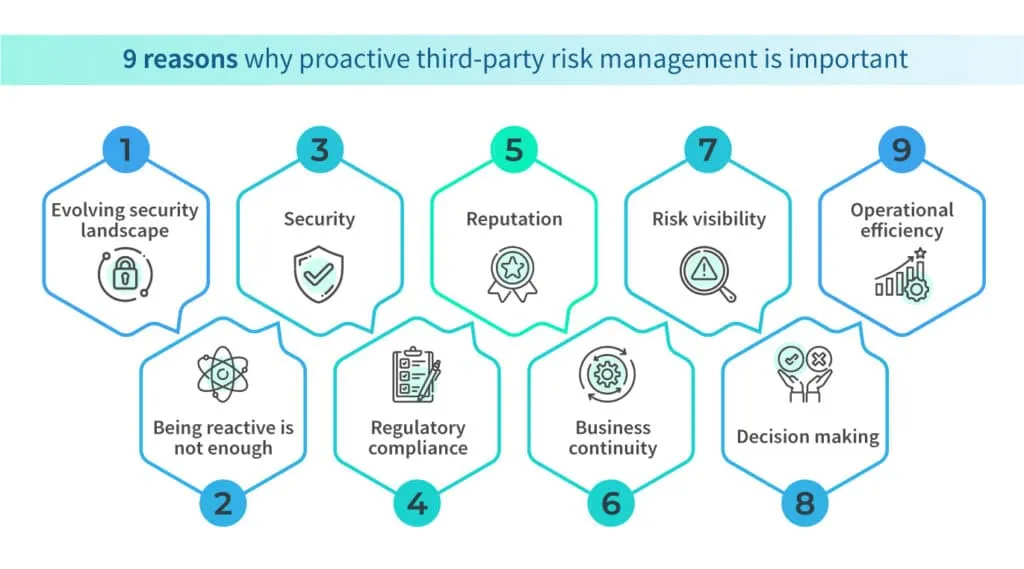
1. Evolving security landscape
The modern security landscape is a landmine of security threats. Cybercriminals dedicate their time to targeting any vulnerability that they may find in an organization's security posture. This vulnerability includes gaps in its vendors' security program.
2. Being reactive is not enough
A reactive approach to vendor risk management focuses on reducing the negative impact of security incidents after they occur. It does not address their root cause or predict the occurrence of new security risks. This reactive approach leaves too much leeway for security threats.
A proactive approach, on the other hand, anticipates and prevents potential risks in advance. It addresses them before they have the chance to cause any damage.
3. Meeting regulatory compliance
Compliance requirements are increasing by the day across industries. Proactive risk management enables organizations to identify and address potential compliance gaps in their third-party relationships. This ensures consistent adherence to legal and regulatory obligations.
4. Reputation
If your vendor suffers a data breach, it not only puts your data at risk, but it also negatively impacts your organization's reputation. Being proactive prevents such incidents and safeguards your company's brand value and customer trust.
5. Business continuity
Any service interruption from your vendors' end can disrupt your organization's business operations. For instance, if your vendor experiences frequent power outages, it delays the delivery of their goods or service. Proactive risk management identifies potential weaknesses and establishes contingency plans to minimize the impact of any disruptions.
6. Risk visibility
Proactive risk management allows your organization to gain a comprehensive view of potential risks within its third-party ecosystem.
It establishes a robust risk assessment framework and regularly evaluates third-party relationships. It implements measures such as regularly reviewing vendor SOC 2 reports to weed out or address any vendor who poses a substantial risk to your company.
7. Informed decision-making
Proactive risk management enables your organization to make informed decisions regarding its third-party engagements. Conducting thorough due diligence helps organizations identify high-risk vendors and suppliers and make strategic choices that align with their risk appetite and business objectives.
8. Operational efficiency
A proactive approach to risk management reduces the chances or impact of security incidents. This means your organization will not have to spend time and effort reacting to security incidents. This saves your company a lot of time and money that can be used for other productive activities.
What are the best practices for proactive third-party risk management?
Now that we've established why proactive third-party risk management is a necessity, let's take a look at some best practices that make it effective.
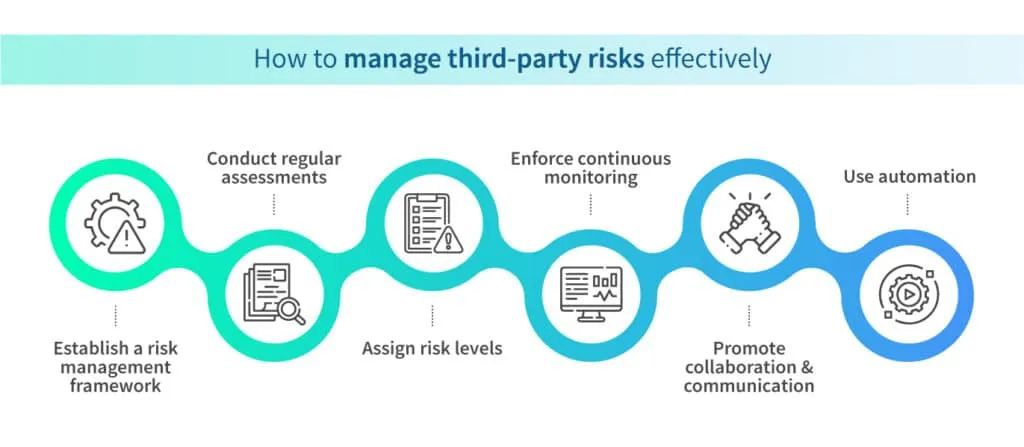
1. Establish a risk management framework
To get the best results, your organization should create a structured and comprehensive risk management framework that includes regular risk identification, assessment, monitoring, and mitigation strategies tailored to its third-party relationships.
2. Conduct regular assessments
Regularity is key when it comes to proactive vendor risk management. Financial stability, security practices, and regulatory adherence should be evaluated periodically. This will help address any vulnerabilities or regulatory lapses.
3. Assign risk levels

Third-party risk management becomes a lot more streamlined when risk levels are assigned to all vendors. For instance,
- Level 1 could be assigned to vendors who pose the lowest risk. These could be vendors who do not handle sensitive data such as vendors who provide video editing software.
- Level 2 can cover vendors who handle information such as employee data and proprietary business information. These assessments could be done once every three years.
- Level 3 can consist of vendors who work with consumer data including personally identifiable information (PII) or credit report data. Since the nature of this data is highly sensitive, annual audits are recommended for vendors who deal with such information.
4. Enforce continuous monitoring
Continuous monitoring should be carried out to track changes in the security landscape and ensure ongoing compliance with established security requirements. Real-time monitoring is ideal for detecting potential risks before they strike and implementing proactive measures.
5. Promote collaboration and communication
Effective collaboration and communication between internal stakeholders should be encouraged. All employees in the procurement, legal, and information security teams should do their part in vendor risk management to enhance the organization's security.
6. Use automation
Proactive vendor risk management calls for the use of third party risk management software that can automate assessments and incident response. This not only improves the efficiency of the risk management program but also saves cost and time by reducing manual effort.
Wrapping up
Any third party that an organization associates with should be regarded as a potential carrier of security risks. As paranoid as this sounds, it's better to be safe than sorry—and being safe requires a proactive approach to vendor risk management.
From regular vendor assessments to continuous monitoring of security risks, proactive third-party risk management is always on its toes to improve security.
One of the best ways to proactively manage vendor risks is investing in a tool like Scrut to take care of continuous risk monitoring, vendor evaluation, and risk mitigation. Schedule a demo today to learn more.
FAQs
1. What is third party risk management? Third party risk management involves the assessment and monitoring of risks associated with vendors, suppliers, contractors, and other external entities that have access to an organization's data, systems, or operations.
2. Why is proactive third-party risk management necessary? Proactive third-party risk management is necessary because it tackles vendor risks swiftly through effective risk monitoring and mitigation practices.It anticipates and prevents potential risks in advance and addresses them before they have the chance to cause any damage.
3. What are the best practices for proactive third party risk management? Some of the best practices for proactive third party risk management include:
- Establishing a risk management framework
- Conducting regular assessments
- Assigning risk levels
- Enforcing continuous monitoring
- Promoting collaboration and communication
- Using automation
Table of contents