Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Open-source CSPM: What is It and What You Need to Know
Last updated on
January 20, 2025
10
min. read

Cloud security posture management (CSPM) accumulates information from your cloud resources and monitors this environment for vulnerabilities and compliance violations. The adoption of clouds to run software, infrastructures, applications, databases, and operations is growing rapidly. The cloud computing industry is expected to grow at a CAGR of 19.9% to reach $ 2,432 billion by 2030.
Simultaneously, attacks on cloud environments also become more frequent. The year 2022 saw a 48% rise in cyberattacks on cloud infrastructures. These instances show the critical need for cloud security tools like CSPM.
However, an organization is faced with two choices when picking a CSPM solution: Proprietary CSPM tools or open-source CSPM tools?
In this article, we will focus on how an open-source CSOM tool works and how it compares to a proprietary CSPM tool.
What is open-source CSPM?
Open-source CSPM is a cloud security software where the source code is publicly available. These open-source cloud security tools use a decentralized development model. The source code is available to the public for collaboration, modification, and enhancement.
An open CSPM is developed in layers. This can be done by different individuals or organizations who modify the source code. These modifications turn into variants of the open-source CSPM tool. They may also be additions in the form of applications and extensions created by the CSPM’s open-source community.
These open-source cloud security tools can perform all the basic functions required for a CSPM tool. This would include cloud monitoring and security posture management. However, CSPM open-source tools may greatly vary in available features. The development of these features largely depends on the open-source community.
The availability of different modifications, patches, features, and integrations for open CSPM tools depends on whether or not someone in the community has developed them. The developers of individual features, applications, or extensions may or may not make it available as part of the license for the open-source CSPM tool.
Difference between proprietary CSPM and open-source CSPM
The primary difference between a proprietary CSPM (also known as commercial CSPM or closed-source CSPM) and an open-source CSPM lies in the way this software is licensed and developed. All the other differences between these two formats stem from this. Let’s understand how an open CSPM differs from a closed CSPM:
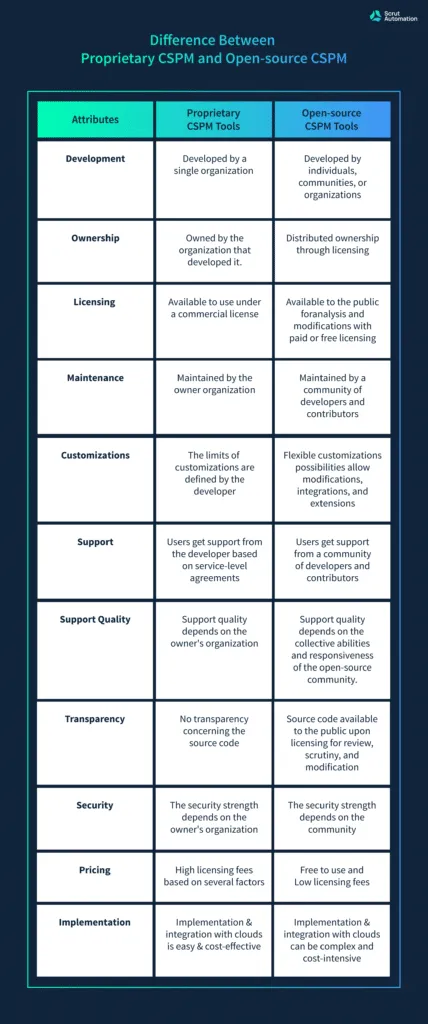
This gives you a general overview of the differences between closed-source and open-source cloud security tools. There may be more or fewer differences depending on the tools you choose to compare.
Even different open-source CSPM tools have unique features and characteristics. These may be defined by the initial developer of the source code. Or they may be a result of the community that contributes to the open CSPM or modifies it.
What does open CSPM do?
In terms of functionality, an open-source CSPM can perform similar actions to a proprietary cloud security posture management software. However, the scope of functionality heavily depends on the features and modifications developed by its community.
Here are a few functionalities that you would need in open-source CSPM tools:
1. Integration
You need to check whether the open-source CSPM tools integrate with your existing public and private clouds. If you plan to use multiple clouds, you also need to check whether the open-source security platform offers multi-cloud security posture management functionality.
2. Data collection
CSPM tools can gather data on configurations of the cloud environment. This functionality may vary in open-source cloud security tools. You need to examine the extent of configuration analysis conducted by your chosen CSPM tools in an open-source model. You need to assess the types of cloud resources encompassed by the CSPM tool for configuration checks.
Additionally, you also need to check the frequency of cloud environment analysis. Some open-source CSPM tools may offer one-time manual configuration checks. While others offer automated recurring configuration checks.
3. Visibility
The majority of CSPM tools offer single dashboard visibility of the cloud environment. They can identify the resources and configurations. This data is converted into visualizations on the user interface dashboard. This dashboard gives you complete visibility over the cloud environment. It also helps you identify vulnerabilities and compliance issues.
You should assess the user interface features of the CSPM open-source tool to check the extent of visibility it offers. You should be able to see the entire inventory of your cloud environment and its configurations.
4. Policy checks
A CSPM tool assesses the cloud architecture based on security compliance criteria. These criteria can be based on cloud compliance frameworks such as HIPAA, GDPR, CCPA, and so on. An organization can also customize the policy checks based on their specific requirements.
You need to assess the compliance management capabilities of your chosen open-source CSPM tool. You also need to check the level of customization the open CSPM offers for defining cloud security compliance criteria.
5. Security alerts
Once the open-source cloud security tool runs a policy check, it should notify you about the current security posture of your cloud architecture. Based on the defined security criteria, the open-source CSPM tool should notify you about potential risks, vulnerabilities, and compliance violations.
You need to examine how the open-source cloud security posture management tool conducts this communication. You also need to check whether the CSPM’s open-source interface integrates with your DevOps tools to convey alerts and notifications regarding potential threats.
Furthermore, you also need to examine the remediations suggested by the open CSPM tools for patching the vulnerabilities. This will help reduce the burden on your DevOps team and help them easily fix the vulnerabilities and compliance breaches.
These features cover the basic functionality you need for cloud security posture management. Some open-source CSPM tools may also offer additional features. You may also get extensions and purpose-specific tools developed by the open-source community. However, you first need to assess the tool’s capabilities to fulfill the fundamental requirements.
Who can use open CSPM?
A cloud security posture management tool is commonly used in the following scenarios:
- To gain visibility over the cloud environment, its components, and their configurations.
- To run security checks for assessing threats, vulnerabilities, and compliance violations.
- To manage cloud security posture in-line with industry standards, government regulations, and cloud security best practices.
- To identify security and compliance threats in the cloud infrastructure and develop patches for remediation.
You can consider both proprietary and open CSPM tools to fulfill these requirements. While proprietary CSPM software offers assurance and reliability of a brand. An open-source CSPM tool offers flexibility and community support.
The capabilities of the open CSPM are also highly dependent on the community. The CSPM tools in the open-source licensing model are cheaper compared to proprietary CSPM tools. Some CSPM open-source tools even license the software free of cost.
But, they are more difficult to deploy, integrate, and manage compared to proprietary CSPM tools. open-source tools may require significant customizations to manage cloud security and compliance. However, if you need very specific customizations or define niche compliance policies, these open-source security platforms can facilitate the required flexibility.
You can consider such open-source cloud security platforms if you work under budget constraints. At the same time, you will need significant resources to deploy and maintain these tools. Consider the benefits and limitations of open-source products listed below before making a decision.
What are the advantages and disadvantages of open-source CSPM?
The benefits and limitations of an open CSPM tool stem from the open-source model. These are highly dependent on the community that develops, upgrades, and maintains the open-source security platform. We will cover the common advantages and disadvantages of using an open-source CSPM to manage the security posture of your organization.
Advantages of open-source CSPM tools
An open-source CSPM tool offers the following benefits for your organization:
- Inexpensive: CSPM tools in the open-source model are quite cheap to license. Many of the open-source security platforms are also free to use.
- Transparency: open-source CSPM tools provide access to the underlying code of the software so that you can assess its capabilities and security measures.
- Flexibility: You can modify the source code of an open CSPM and mold it for your specific security requirements. You can customize the functionality, add new features, and integrate it with other systems.
- Community Support: You can also benefit from the modifications, functionalities, and features developed by the community and integrate them with your open-source cloud security tools. The community can also help you with regular upgrades, bug fixes, patches, and the latest compliance changes to keep your CSPM up to date.
- Integrations & Extensions: Open CSPM tools allow you to use integrations and extensions to include different cloud platforms, security frameworks, and third-party tools within your cloud environment.
These benefits depend on the type of community you get with the open-source CSPM software. If the community is active, it can collaborate for rapid development and innovation. However, if the community is ineffective, you might have to carry much of the development burden by yourself.
Disadvantages of open-source CSPM tools
Let’s understand the limitations of a CSPM tool in the open-source model:
- Inconsistent Functionalities: As open CSPM tools are dependent on the community for development and maintenance, it may lead to inconsistent functionalities compared to proprietary and commercial CSPM tools.
- Security Risks: As the source code of open CSPMs is available to the public, such tools are more vulnerable to cyber-attacks. The open-source Security and Risk Analysis 2023 Report found open-source vulnerabilities in 84% of code bases. Cybercriminals can use the underlying flaws in the source code to bypass the configurations of open-source security platforms.
- Community Dependence: You have to depend on the open-source community for the maintenance and upkeep of the open-source cloud security tools. This includes patches, updates, bug fixes, functionalities, integrations, expertise, threat identification, features, and support.
- Resource Intensive Deployment: You need a certain level of expertise to modify and integrate open CSPM tools with your clouds and third-party tools. You may face compatibility issues when integrating open-source cloud security tools in a multi-cloud environment.
As the capabilities of the software depend on the community, the advantages and drawbacks of different open-source security products depend on the communities that maintain them.
Use Scrut for Consistent Cloud Security Management
Open-source CSPM tools offer a cost-effective and flexible solution for cloud security. They are also resource intensive to deploy and make an organization dependent on the development community for maintenance and functionalities of the software.
If you want a hassle-free cloud security posture management solution, consider Scrut’s Cloud Security Solution. This CSPM software integrates with various clouds and offers thorough visibility of the cloud environment.
You can use the pre-defined compliance frameworks or define your own security policies for cloud monitoring, threat assessment, vulnerability identification, and compliance management. You can also integrate the Scrut CSPM software with DevOps communication and task management tools to remediate misconfigurations and compliance issues.
Table of contents