6 reasons why businesses should prioritize IT and cyber risk assessment

Cyber threats are rising by leaps and bounds. Threat actors are using artificial intelligence and machine learning to their advantage to carry out more sophisticated attacks.
Despite rising cyber threats, many organizations overlook cybersecurity, driven by factors like limited awareness, resource constraints, and complacency from a lack of past incidents. The complexity of cyber threats further complicates prioritization amidst competing business needs.
Yet, prioritizing IT and cyber risk assessment is crucial for effective cybersecurity. Understanding threats, assessing impacts, and implementing countermeasures are fundamental steps in mitigating risks.
The following are the six reasons organizations should consider IT and cyber risk assessment as their top priority.
1. Compliance and Regulatory Requirements
Compliance is crucial for organizations as it ensures adherence to legal, regulatory, and ethical standards, safeguarding their reputation and mitigating risks of penalties or legal action.
By fostering a culture of ethical conduct and accountability, compliance also enhances trust among stakeholders, improves operational efficiency, and fosters a positive work environment.
There are many compliance standards and frameworks according to the business, location, and type of your organization. These standards include GDPR, HIPAA, FISMA, SOC 2, CCPA, and more.
IT and cyber risk assessments are instrumental in helping businesses meet compliance standards and regulatory requirements in several ways:
- Identification of Risks: Risk assessments allow businesses to identify potential cybersecurity risks and vulnerabilities within their IT systems and infrastructure. This proactive approach enables organizations to address these risks before they lead to compliance breaches.
- Adherence to Standards: By performing risk assessments, businesses can ensure they adhere to cybersecurity compliance standards and regulations. This includes assessing and documenting cybersecurity policies and procedures, which are often required for compliance.
- Implementation of Best Practices: Cyber security risk assessments help organizations adopt and implement cybersecurity best practices, which are often aligned with regulatory requirements. This ensures that businesses not only meet the minimum compliance standards but also enhance their overall cybersecurity posture.
- Continuous Monitoring and Improvement: Regular risk assessments allow businesses to continuously monitor their cybersecurity posture and identify areas for improvement. This iterative process ensures ongoing compliance with evolving regulatory requirements and industry standards.

2. Protection Against Cyber Threats
According to recent statistics, cyberattacks have been increasing in frequency and sophistication. In 2023, Kaspersky detected almost 125 million malicious files in total, a 3% increase from the previous year.
Additionally, ransomware attacks surged by 55.5%, highlighting the evolving nature of cyber threats. These statistics emphasize the urgent need for organizations to assess and address vulnerabilities in their digital environments to mitigate the risk of falling victim to cyberattacks.
Risk assessments play a critical role in identifying vulnerabilities and mitigating the risk of various cyber threats, including phishing schemes, ransomware attacks, and data breaches. Here's how they achieve this:
- Identification of Vulnerabilities: Risk assessments systematically analyze an organization's systems, networks, and processes to pinpoint weaknesses and vulnerabilities that could be exploited by cyber threats.
- Prioritization of Threats: By assessing the likelihood and potential impact of different cyber threats, risk assessments help prioritize mitigation efforts, focusing on the most significant risks first.
- Implementation of Controls: Based on the identified vulnerabilities and prioritized threats, organizations can implement appropriate security controls and measures to mitigate the risk of cyber threats, such as deploying email filtering systems to counter phishing attempts, installing anti-malware software to defend against ransomware attacks, and enforcing access controls to protect against unauthorized data breaches.
3. Prioritization of Critical Assets
The prioritization of critical assets involves identifying and ranking the most important components of an organization's infrastructure, data, and systems based on their significance to the business operations and potential impact if compromised.
This process allows organizations to allocate resources effectively, focus on protecting essential assets first, and mitigate risks more efficiently.
Prioritization of assets serves as a strategic approach to bolstering cybersecurity defenses and safeguarding against potential threats, thereby enabling organizations to operate securely and resiliently in an increasingly complex digital environment. It is crucial for several reasons:
- Risk Mitigation: By identifying and prioritizing critical assets, organizations can focus their resources on securing the most important components of their infrastructure. This targeted approach helps mitigate risks associated with potential cyber threats and vulnerabilities.
- Business Continuity: Protecting critical assets ensures the continuity of essential business functions. By prioritizing their security, organizations minimize the impact of potential cyberattacks or disruptions, maintaining operational resilience even in the face of security incidents.
- Resource Allocation: Effective allocation of resources is essential for optimizing cybersecurity efforts. By prioritizing critical assets, organizations can allocate resources more efficiently, focusing on areas that are most vulnerable or prone to cyber threats.

4. Enhanced Security Measures
Risk assessments serve as a foundation for implementing robust security measures by identifying vulnerabilities and threats within an organization's systems and processes. Through comprehensive evaluation, organizations can pinpoint areas susceptible to cyber threats, prompting the implementation of targeted security controls.
These measures may include encryption protocols to safeguard sensitive data, access controls to restrict unauthorized access, and employee training programs to enhance cybersecurity awareness and promote best practices.
By aligning security measures with identified risks, organizations can bolster their overall cybersecurity posture and mitigate potential security breaches and data compromises effectively.
5. Informed Decision-Making
Assessing IT and cyber risks offers crucial insights that drive informed decision-making in resource allocation and cybersecurity investments. By understanding the organization's risk landscape, decision-makers can prioritize areas of vulnerability and allocate resources effectively to mitigate potential threats.
This proactive approach enables organizations to make strategic investments in cybersecurity measures tailored to address identified risks, thereby enhancing resilience against cyber threats and minimizing the likelihood of costly security incidents.
6. Cyber Insurance
By leveraging IT and cyber risk assessments, insurers can offer tailored cyber insurance solutions that accurately reflect an organization's risk profile, ultimately enhancing cyber resilience and mitigating financial losses associated with cyber incidents.
- Risk Evaluation: IT and cyber risk assessments provide insurers with a comprehensive understanding of an organization's cybersecurity posture.
- Underwriting Process: Insurers use risk assessments to evaluate cyber risks accurately before issuing a policy.
- Premium Determination: The results of risk assessments influence premium rates, helping insurers tailor pricing to the level of risk exposure.
- Policy Coverage: Assessments aid in determining the scope of coverage needed, ensuring that policies adequately protect against potential cyber threats.
- Risk Mitigation: By identifying vulnerabilities and weaknesses, risk assessments enable organizations to implement measures that reduce the likelihood of cyber incidents, which may lead to fewer claims and lower premiums over time.
- Enhanced Defenses: Insurers may provide incentives or discounts for organizations that demonstrate robust cybersecurity measures through risk assessments, encouraging proactive cyber security and risk management.
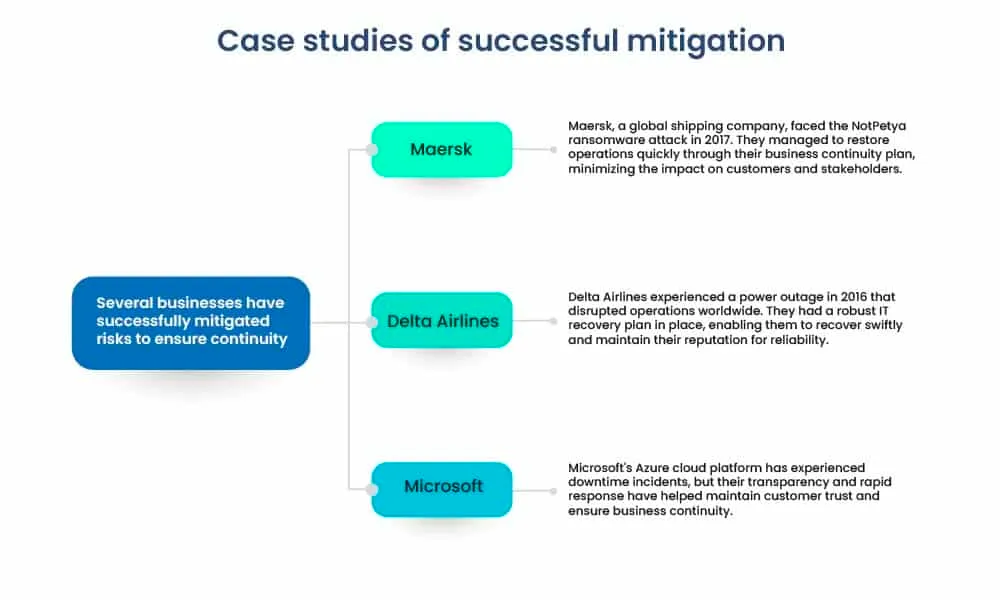
Target CorporationAfter suffering a massive data breach in 2013, Target invested heavily in cyber security and obtained cyber insurance. Their proactive risk management efforts helped them recover faster and mitigate financial losses.
Conclusion
By identifying vulnerabilities, prioritizing critical assets, and implementing robust security measures, businesses can mitigate the risk of cyber threats and enhance their resilience. Moreover, IT and cyber risk assessment not only help meet compliance requirements but also inform strategic decision-making and facilitate the procurement of tailored cyber insurance solutions.
Investing in IT and cyber security risk assessment is not just proactive—it's a strategic imperative for organizations to safeguard their operations, protect their assets, and maintain stakeholder trust in an evolving digital landscape.
Protect Your Digital Future Today! Schedule Your Cyber security Risk Management with Scrut and Safeguard Your Business.
FAQs
1. Why is IT and cyber risk assessment important for organizations? IT and cyber security risk assessment is crucial for identifying vulnerabilities in systems and processes, prioritizing critical assets, and implementing robust security measures. It helps organizations mitigate the risk of cyber threats and enhances overall resilience in the face of evolving cybersecurity challenges.
2. How can IT and cyber risk assessment protect organizations against cyber threats? IT and cyber risk assessment identify vulnerabilities and prioritize threats, allowing organizations to focus on mitigating the most significant risks. By implementing appropriate security controls and measures, such as encryption protocols and access controls, businesses can effectively defend against various cyber threats, including phishing schemes, ransomware attacks, and data breaches.
3. What role does cyber insurance play in mitigating cyber risks? Cyber insurance solutions tailored to an organization's risk profile can mitigate financial losses associated with cyber incidents. IT and cyber risk assessment aid in evaluating cyber risks accurately, determining premium rates, defining policy coverage, and incentivizing proactive risk management efforts, ultimately enhancing cyber resilience and reducing financial exposure.


















