Understanding inherent risk vs Residual risk: Key concepts in security and compliance

Picture this: a high-stakes game where the odds are constantly shifting and the consequences of losing are not just financial but could jeopardize an entire organization’s future. Welcome to the world of risk management in the realm of security and compliance, a dynamic arena where vigilance is your best ally.
In our digital age, where data is the new gold and regulations are ever-evolving, risk management isn’t just a good practice—it’s the lifeline of modern business. But here’s the twist: it’s not just about recognizing the risks; it’s about understanding the subtle dance between inherent risk and residual risk, a dance that can mean the difference between survival and catastrophe.
Join us on this thrilling journey as we unravel the mystery behind inherent and residual risks, helping you master the art of risk management in security and compliance. Get ready to safeguard your organization’s future like a pro!
Understanding inherent risk
A. What is inherent risk?

To truly grasp this concept, let’s break it down further.
It represents the natural or inherent susceptibility of a situation to potential adverse events or losses. Inherent risk is essentially the risk an organization would face if it took no steps to address or manage the risk factors involved.
To put it simply, inherent risk is the baseline risk level that exists without any protective measures in place. It provides a starting point for organizations to assess and manage risks, helping them understand the potential vulnerabilities and threats associated with their operations. Once inherent risks are identified, organizations can then implement risk mitigation strategies to reduce the level of risk to an acceptable or residual level.
B. What are the factors that contribute to inherent risk?
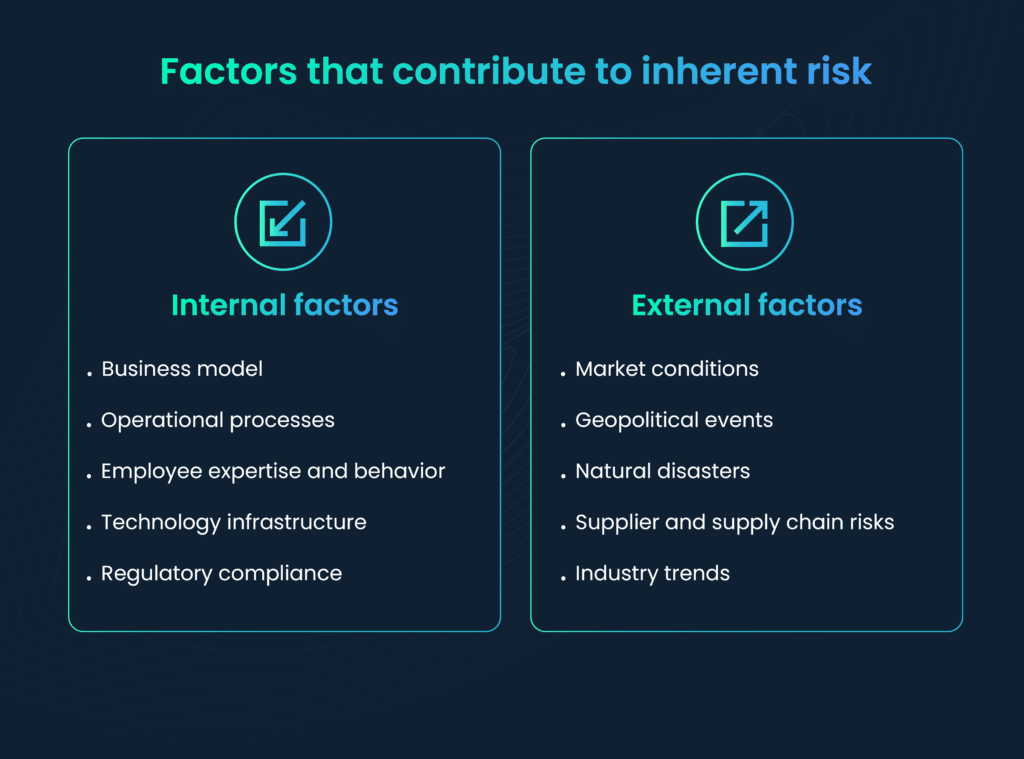
Factors contributing to inherent risk can vary widely depending on the specific context or industry, but they generally fall into two categories: internal factors and external factors. Here are some common factors within each category:
Internal factors that contribute to inherent risk
Internal factors are elements that originate within an organization itself, such as its business model and operational processes. Let’s look at the internal factors that affect inherent risk.
- Business model: The nature of the organization’s business and its core activities can significantly impact inherent risk. For example, a financial institution inherently faces risks related to lending and investments due to its business model.
- Operational processes: The efficiency, reliability, and complexity of an organization’s operational processes can influence inherent risk. Complex processes may inherently carry more risk than streamlined ones.
- Employee expertise and behavior: The knowledge, skills, and behavior of employees can affect inherent risk. For instance, a lack of cybersecurity awareness among employees can increase the inherent risk of data breaches.
- Technology infrastructure: The technology systems and infrastructure an organization uses can be a contributing factor. Outdated or poorly maintained systems may have inherent vulnerabilities.
- Regulatory compliance: The extent to which an organization complies with industry-specific regulations can impact inherent risk. Non-compliance inherently carries legal and regulatory risks.
External factors that contribute to inherent risk
External factors are elements outside the organization’s control, including market conditions and natural disasters.
- Market conditions: Economic conditions, market volatility, and shifts in consumer demand can introduce external factors that affect inherent risk. For example, a retail business inherently faces risks related to changes in consumer preferences.
- Geopolitical events: Organizations with international operations may inherently face risks associated with geopolitical events, such as trade disputes or political instability in foreign markets.
- Natural disasters: Depending on their location, organizations may inherently face risks from natural disasters like earthquakes, hurricanes, or floods.
- Supplier and supply chain risks: External factors related to suppliers, such as disruptions in the supply chain, can impact inherent risk. For instance, a manufacturing company may inherently face risks if a key supplier experiences production delays.
- Industry trends: External factors related to industry-specific trends and innovations can influence inherent risk. Organizations in rapidly evolving industries may inherently face risks related to technological obsolescence.
Understanding these internal and external factors that contribute to inherent risk is crucial for organizations when assessing and managing risks effectively. By identifying these factors, organizations can develop strategies and controls to mitigate inherent risks and improve their overall risk management practices.
C. Real-world examples of inherent risk:
- Financial services industry: Inherent risk is evident in the financial sector, where market volatility and economic fluctuations are external factors that contribute to the inherent risk of investment portfolios. Despite expert management, inherent risk remains a constant challenge for asset managers.
- Healthcare industry: Healthcare organizations inherently deal with patient data, making them susceptible to data breaches. Even with robust security measures in place, the inherent risk associated with data security remains high due to the value of medical information on the black market.
- Software development: In the tech world, software development inherently carries the risk of bugs and vulnerabilities. Developers can reduce this risk through rigorous testing, but they can never completely eliminate it. The inherent risk in software development is why software updates and patches are so common.
Understanding inherent risk is the first step in effective risk management. It sets the baseline against which organizations can measure the effectiveness of their risk mitigation efforts. By comprehending the internal and external factors contributing to inherent risk and learning from real-world examples across various industries, organizations can make informed decisions about how to tackle this fundamental level of risk.
Understanding residual risk
A. What is residual risk?

Residual risk exists because it is often challenging or impossible to completely eliminate all risks associated with a particular endeavor. Organizations use risk management strategies and controls to reduce inherent risk to an acceptable level, but there may still be residual risk that needs to be monitored and managed.
The goal is to ensure that the residual risk aligns with the organization’s risk tolerance and does not exceed acceptable thresholds. Effective risk management involves ongoing assessment, monitoring, and adjustment of controls to keep residual risk within acceptable bounds.
B. How do organizations assess and manage residual risk?
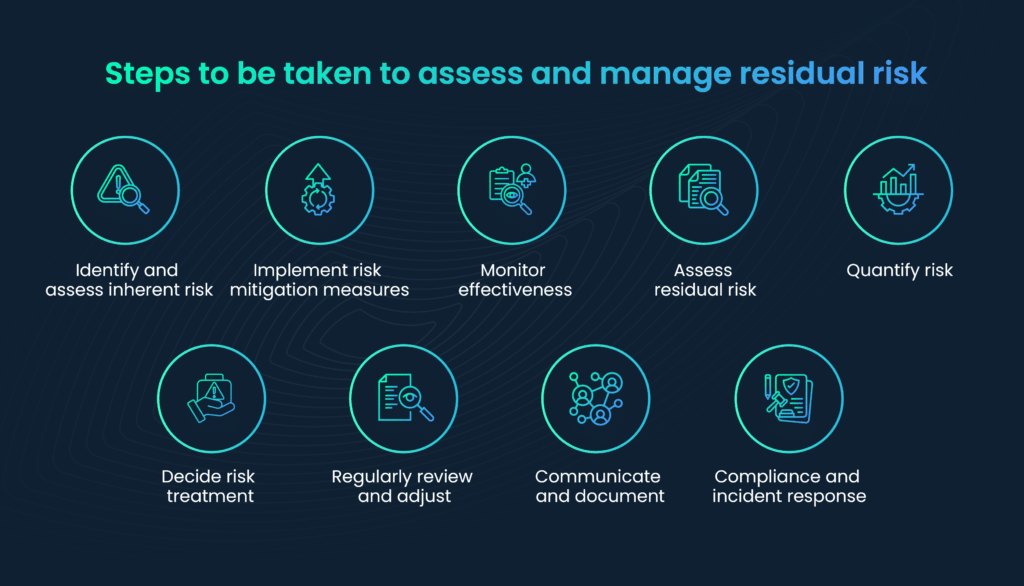
Organizations assess and manage residual risk through a systematic and ongoing process that involves several key steps and strategies. Here’s an overview of how organizations typically approach the assessment and management of residual risk:
- Identify and assess inherent risk: Identify and assess the initial risk associated with a specific activity, process, or project, considering internal and external factors.
- Implement risk mitigation measures: Apply measures and controls to reduce these risks to an acceptable level, like security protocols, compliance frameworks, and insurance policies.
- Monitor effectiveness: Continuously monitor and evaluate the effectiveness of these measures, ensuring they function as intended.
- Assess residual risk: Evaluate the remaining risk after implementing controls to determine if it aligns with acceptable limits.
- Quantify risk: Some organizations use quantification methods, assigning numerical values to risk factors for better assessment.
- Decide risk treatment: Decide whether to accept the residual risk within acceptable limits or apply further treatment strategies if it exceeds those limits.
- Regularly review and adjust: Periodically review and adjust risk mitigation measures to address changing circumstances and emerging threats.
- Communicate and document: Maintain clear communication channels for reporting and documentation, keeping stakeholders informed.
- Compliance and incident response: Ensure compliance with regulations, and have robust incident response plans for unforeseen events despite risk management efforts.
What are the key differences: inherent vs residual risk?
An inherent risk audit is a fundamental step in a broader risk management strategy, helping organizations understand their baseline risk profile. It serves as the foundation upon which residual risk management strategies can be developed and implemented to protect the organization’s interests and ensure compliance with applicable regulations.
This brings us to the comparison between inherent risk and residual risk. The following table represents the primary differences between inherent risks vs residual risks:
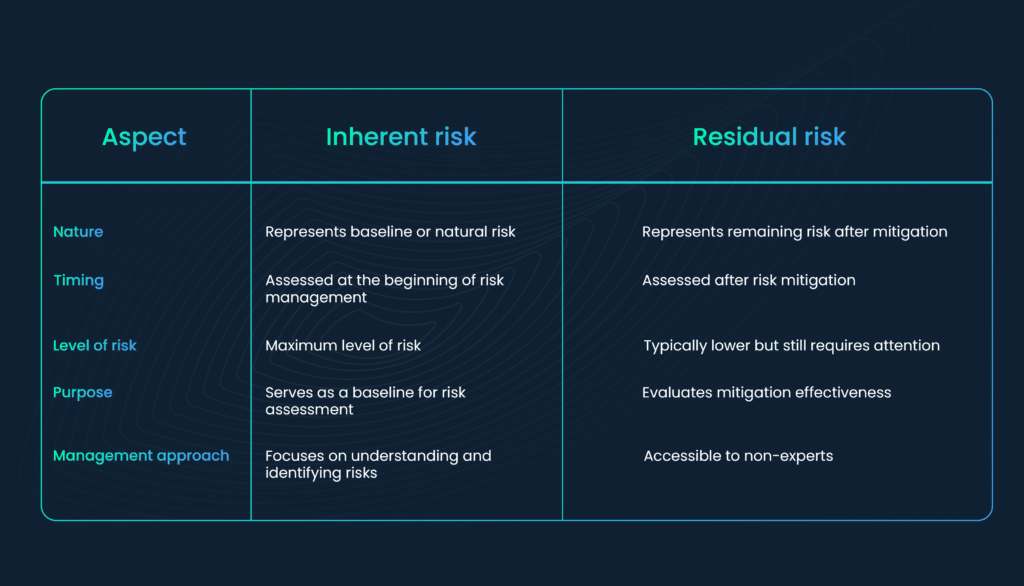
How do these differences impact decision-making and risk-management processes?
The differences between inherent risk and residual risk have significant implications for decision-making and the overall risk management processes within an organization. Here’s how these differences impact these processes:
A. Setting priorities
- Inherent risk: Understanding the inherent risk helps organizations prioritize which areas or activities require the most attention in terms of risk management. It directs efforts toward addressing the most significant threats.
- Residual risk: Residual risk assessment informs decisions about whether risk mitigation measures are effective and whether additional resources or strategies should be allocated to further reduce the remaining risk.
B. Resource allocation
- Inherent risk: Allocation of resources, such as budget and manpower, is influenced by the level of inherent risk. High inherent risk areas may receive more resources for risk mitigation.
- Residual risk: Resources are allocated based on the effectiveness of risk mitigation efforts. If residual risk remains high, additional resources may be allocated to further reduce it.
C. Risk treatment strategies
- Inherent risk: Organizations determine which risk treatment strategies are appropriate based on the magnitude of inherent risk. This may involve risk avoidance, risk reduction, risk transfer, or risk acceptance.
- Residual risk: Decisions regarding the adequacy of risk treatment strategies are made by assessing whether the remaining risk (residual risk) is within acceptable tolerance levels. If not, adjustments or additional measures are considered.
D. Performance evaluation
- Inherent risk: Performance in managing inherent risk is evaluated by comparing the effectiveness of risk mitigation measures to the initial level of inherent risk. It measures how well the organization identifies and addresses risks.
- Residual risk: The effectiveness of risk management efforts is evaluated by assessing the reduction in risk from the inherent to the residual level. It gauges how effectively the organization has controlled and minimized risks.
E. Compliance and reporting
- Inherent risk: Organizations consider inherent risk when determining their compliance obligations and reporting requirements. Regulatory frameworks often require organizations to assess and manage inherent risk to meet compliance standards.
- Residual risk: Residual risk assessment and reporting demonstrate to regulatory bodies and stakeholders that an organization is effectively managing and reducing risks to an acceptable level.
F. Continuous improvement
- Inherent risk: Inherent risk assessment serves as a starting point for continuous improvement efforts. It encourages organizations to regularly review and enhance their risk management practices.
- Residual risk: Residual risk assessment drives continuous improvement by identifying areas where risk mitigation measures may need adjustments or where new risks have emerged.
In summary, distinguishing between inherent risk and residual risk informs decision-making by helping organizations set priorities, allocate resources, choose appropriate risk treatment strategies, evaluate performance, meet compliance requirements, and drive continuous improvement in their risk management processes. It ensures that risk management efforts remain effective and adaptable in the face of evolving risks and challenges.
Regulatory and compliance implications for risk management
Regulatory bodies and compliance standards play a crucial role in addressing both inherent and residual risk within organizations. They provide guidelines and requirements that organizations must follow to ensure effective risk assessment and management. Here’s how regulatory bodies and compliance standards address these risks, along with examples and consequences of non-compliance:
A. Addressing inherent and residual risk
Regulatory bodies and compliance standards play a pivotal role in guiding organizations to address both inherent and residual risks within their operations. They provide essential guidelines for assessing and managing these risks effectively.
Inherent risk: Regulatory bodies often require organizations to assess and address inherent risks as part of their compliance obligations. They expect organizations to identify and understand the fundamental risks associated with their operations, especially those related to data security, financial stability, and public safety.
Residual risk: Regulatory standards emphasize the need for organizations to implement risk mitigation measures and controls to reduce residual risk to an acceptable level. Organizations are expected to evaluate the effectiveness of these measures and ensure that residual risks are within defined tolerance levels.
B. Compliance requirements
Various regulatory frameworks and compliance standards mandate specific requirements for organizations to ensure that risk assessment and management are conducted comprehensively. These requirements vary across industries and regions.
Example 1: General Data Protection Regulation (GDPR): The GDPR, applicable to organizations handling the personal data of European Union citizens, requires organizations to conduct risk assessments related to data privacy. This includes assessing inherent risks associated with data processing activities and implementing measures to reduce residual risks, such as data encryption and access controls.
Example 2: PCI DSS (Payment Card Industry Data Security Standard): PCI DSS mandates that organizations that handle credit card information must conduct regular risk assessments. They are expected to identify inherent risks related to cardholder data and implement controls to mitigate these risks. Failure to comply can result in significant financial penalties.
Example 3: ISO 27001 (Information Security Management System): ISO 27001 provides a framework for managing information security risks. Organizations are required to assess both inherent and residual risks related to their information assets and implement a comprehensive risk treatment plan to reduce residual risks to an acceptable level.
C. Consequences of non-compliance
Non-compliance with regulatory and compliance requirements regarding risk assessment and management can lead to a range of serious consequences, including financial penalties, legal liabilities, and reputational damage. Organizations must prioritize compliance efforts to mitigate these risks effectively.
- Financial penalties: Non-compliance with regulatory requirements can result in substantial fines and penalties. For example, GDPR violations can lead to fines of up to €20 million or 4% of the company’s global annual revenue, whichever is higher.
- Legal liability: Organizations may face legal actions and liabilities, including lawsuits from affected parties or regulatory bodies, for failing to manage inherent and residual risks effectively.
- Reputation damage: Non-compliance can lead to reputational damage, eroding trust among customers, partners, and stakeholders, which can have long-lasting negative impacts.
- Loss of business opportunities: Non-compliance can limit an organization’s ability to engage in certain business activities or collaborate with partners who require compliance as a condition of doing business.
- Operational disruptions: Regulatory penalties and remediation efforts to address non-compliance can disrupt business operations and lead to financial losses.
In conclusion, regulatory bodies and compliance standards mandate that organizations assess, manage, and mitigate both inherent and residual risks to meet legal requirements and industry best practices. Non-compliance can result in severe consequences, including financial penalties, legal liabilities, and damage to an organization’s reputation, underscoring the importance of effective risk management and compliance efforts.
What are risk mitigation strategies for inherent and residual risks?
Effective risk mitigation is crucial for reducing inherent risk to acceptable levels and maintaining low residual risk. Organizations employ various strategies to achieve this, emphasizing the importance of continuous monitoring and adjustment. Here’s an exploration of risk mitigation strategies, the role of ongoing monitoring, and best practices for minimizing residual risk:
A. Risk mitigation strategies for inherent risk
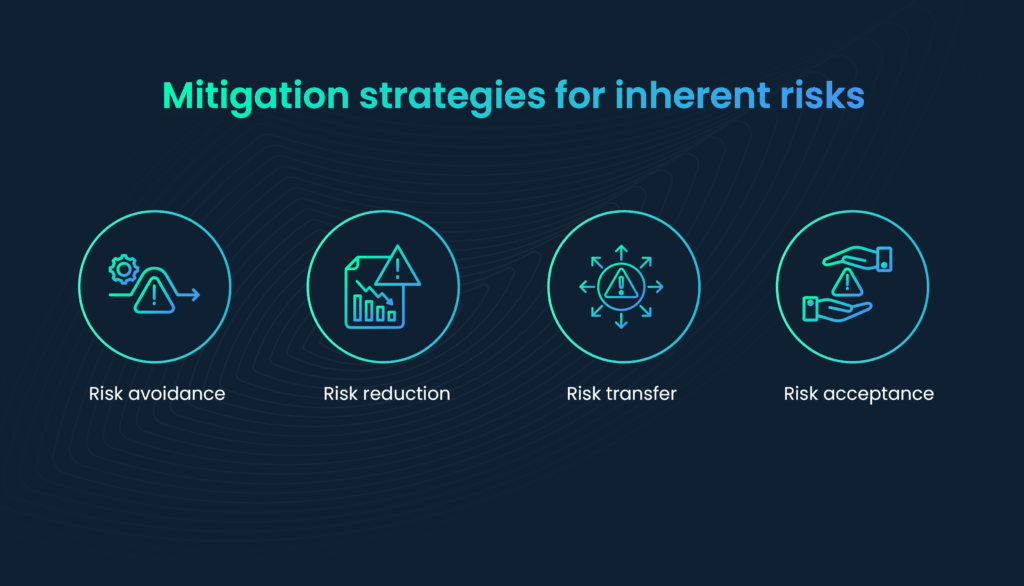
Organizations employ various strategies to reduce inherent risk, aiming to lower the baseline level of risk associated with their activities. These strategies include:
1. Risk avoidance
In some cases, organizations may choose to avoid certain activities or practices that inherently carry high risk. For example, a financial institution might avoid highly speculative investments to reduce inherent financial risks.
2. Risk reduction
Implementing measures to reduce inherent risk is common. This can include improving cybersecurity defenses, conducting thorough due diligence in business transactions, or enhancing safety protocols in high-risk industries.
3. Risk transfer
Organizations may transfer some inherent risk to third parties through insurance, contracts, or outsourcing arrangements. This is often seen in liability insurance or when outsourcing IT services to specialized providers.
4. Risk acceptance
Sometimes, organizations may accept inherent risk if it falls within their risk tolerance and cannot be feasibly reduced further. In such cases, they rely on monitoring and contingency plans to manage the risk’s impact.
B. Ongoing monitoring and adjustment
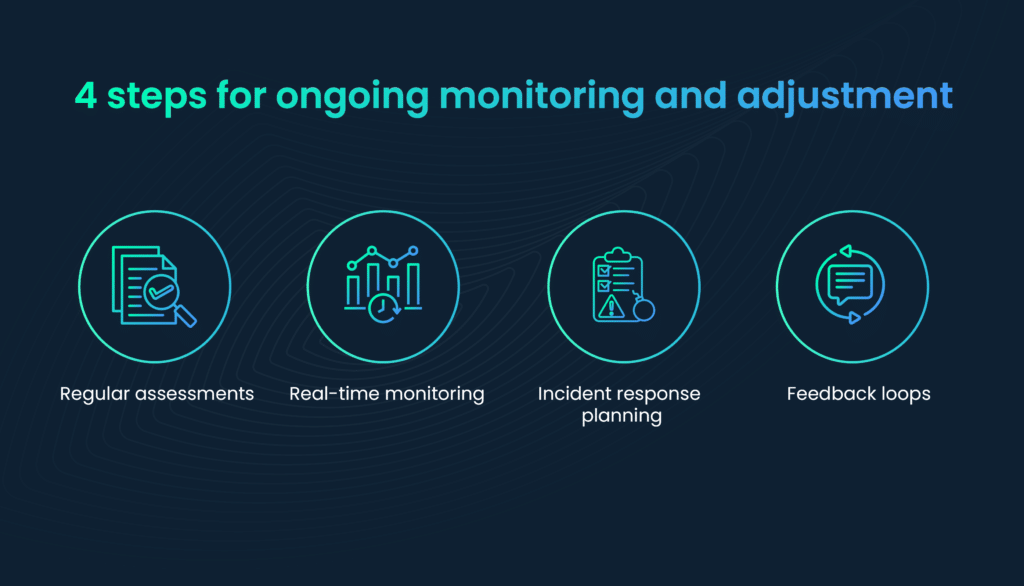
Continuous monitoring is essential to ensure that risk mitigation strategies remain effective. This involves
- Regular assessments: Periodically assess the effectiveness of mitigation measures to identify any emerging risks or vulnerabilities.
- Real-time monitoring: Implement systems and processes for real-time monitoring of critical areas, such as cybersecurity or financial transactions.
- Incident response planning: Develop and maintain robust incident response plans to address unforeseen events and minimize their impact on both inherent and residual risk.
- Feedback loops: Establish mechanisms for feedback and reporting from employees, stakeholders, or external sources to promptly identify issues and areas of concern.
C. Best practices for low residual risk
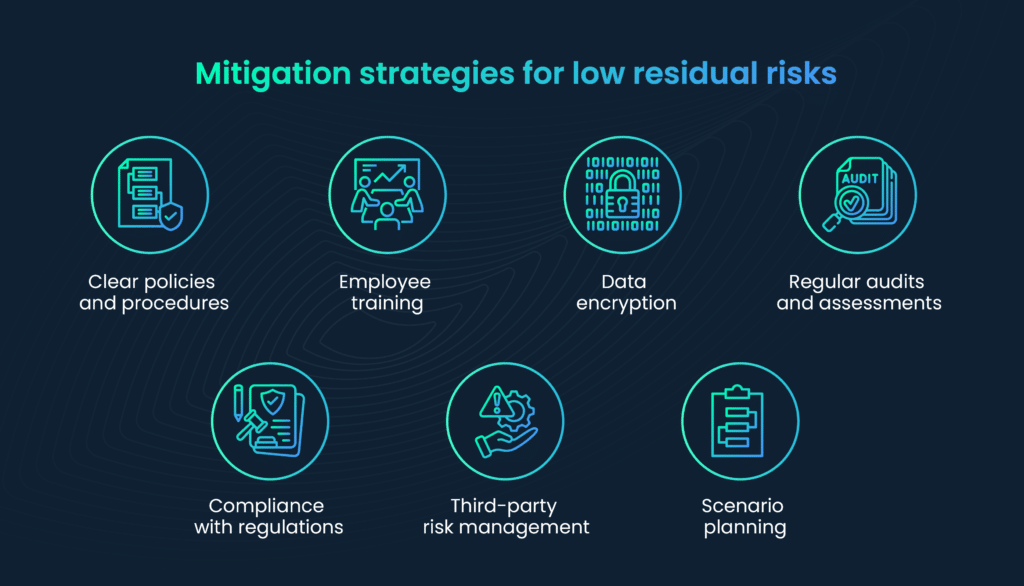
Maintaining low residual risk levels is a critical goal for organizations. Best practices include:
- Clear policies and procedures: Maintain clear and updated risk management policies and procedures that are well-communicated throughout the organization.
- Employee training: Invest in employee training and awareness programs to ensure that everyone understands their role in risk mitigation.
- Data encryption: Implement data encryption for sensitive information to reduce the risk of data breaches.
- Regular audits and assessments: Conduct regular audits and assessments to identify areas where residual risk may have increased and adjust mitigation strategies accordingly.
- Compliance with regulations: Ensure compliance with industry-specific regulations and standards to minimize legal and regulatory residual risk.
- Third-party risk management: Continuously evaluate and manage risks associated with third-party vendors and partners who may introduce new risks into your ecosystem.
- Scenario planning: Develop and regularly update scenario-based plans to prepare for potential risks, enabling a swift and coordinated response.
Effective risk mitigation involves a combination of these strategies, ongoing monitoring, and proactive adjustment of mitigation efforts. By following best practices and adapting to evolving risks, organizations can maintain low residual risk levels and enhance their overall risk management capabilities.
How can Scrut help you reduce inherent risks and residual risks?
Technology plays a pivotal role in modern risk management by enabling organizations to identify, assess, and manage both inherent and residual risk effectively. Advancements in risk management software and solutions have significantly enhanced these capabilities. Scrut is an excellent example of risk management software. Let’s discuss its role in risk management.
A. Improve visibility on your risk posture
Gain the essential visibility required to safeguard against threats and effectively communicate the consequences of risk to vital business operations. Scrut Risk Management offers a more intelligent approach to assist you in identifying, assessing, and mitigating IT and cyber risks.
B. Customize your risk register
With Scrut, you have the flexibility to create a customized risk register that suits your specific requirements. Utilize an automated risk-scoring approach to accurately quantify your risk profile. Leverage Scrut’s risk register to craft a comprehensive risk treatment plan and maintain ongoing risk monitoring seamlessly.
C. Identify risks across your landscape
Scrut employs automated scans to uncover risks across your code base, infrastructure, applications, vendors, employee activities, access controls, and beyond. Alternatively, you can leverage Scrut’s pre-existing risk library or create your custom risk profiles as needed.
D. Measure risk reliably
Determine your risk profile using expert-reviewed scoring methodologies embedded within the system. Evaluate the effectiveness of your risk mitigation strategies by examining both inherent and residual scores. With Scrut, gaining insights into your risk exposure, pinpointing critical risk areas, and taking steps to mitigate them becomes a straightforward process.
E. Monitor risk – 24X7
With Scrut, continuous risk monitoring becomes a practicality. Effortlessly configure alerts and notifications that seamlessly integrate with your preferred messaging and email applications, ensuring you stay informed and in control of your risk status.
F. Map risks to compliance frameworks
Concentrate your attention on the most relevant risks by aligning them with pre-mapped controls from widely recognized information security frameworks such as ISO 27001, SOC 2, and similar standards. Ensure compliance without the need to navigate through extensive lists of risk sources.
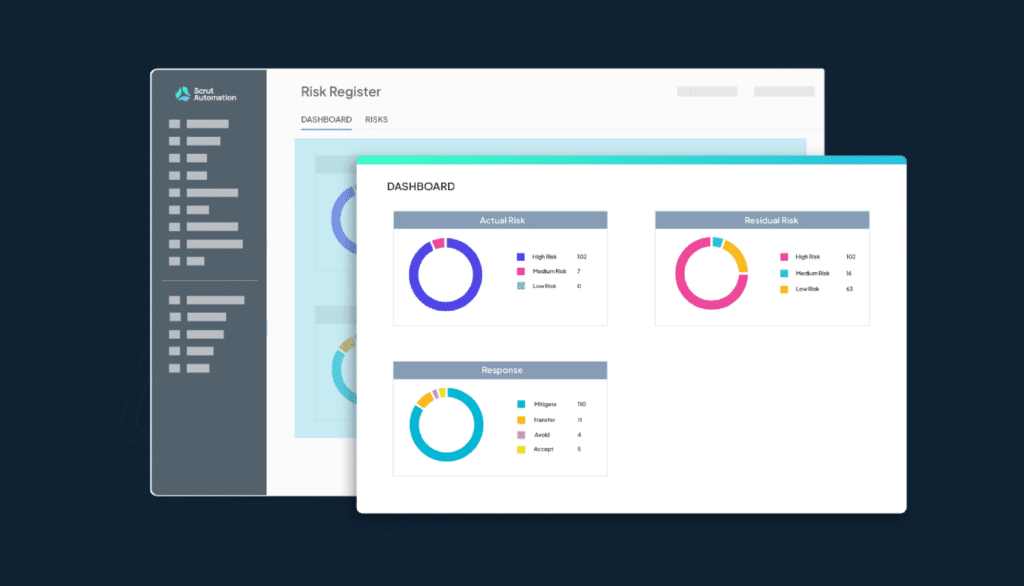
G. Use intuitive, actionable dashboards
Effectively visualize, quantify, and convey your risk position in alignment with your business priorities. This allows you to grasp the risk ramifications of strategic choices comprehensively.
Conclusion
In the fast-paced world of risk management in security and compliance, where the stakes are high and the consequences are far-reaching, we’ve delved into the intricate dance between inherent and residual risks. Our journey has taken us through the fundamentals of risk management, the differences between inherent and residual risks, and how they impact decision-making and compliance.
We’ve explored the critical role of regulatory bodies and compliance standards in shaping risk management practices, along with the potential consequences of non-compliance. It’s clear that risk management isn’t merely a good practice; it’s imperative for modern businesses to thrive and protect their future.
Moreover, we’ve seen how technology, exemplified by Scrut Risk Management software, is revolutionizing risk management. Scrut provides organizations with the tools they need to gain visibility into their risk posture, customize risk registers, identify risks across their landscape, and measure risk reliably. It enables 24/7 risk monitoring, aligns risks with compliance frameworks, and offers intuitive, actionable dashboards for informed decision-making.
Ready to elevate your risk management game? Explore the Scrut Risk Management tool today and safeguard your organization’s future like a pro. Get started now!
FAQs
1. What is the significance of risk management in security and compliance?
Risk management in security and compliance is vital because it helps organizations identify, assess, and mitigate risks that could impact their operations, data, reputation, and compliance with regulations. It ensures proactive measures are in place to protect against potential threats.
2. What is the difference between inherent risk and residual risk?
Inherent risk is the initial, natural level of risk associated with a specific activity or process before any mitigation measures are taken. Residual risk, on the other hand, is the remaining risk after mitigation efforts have been implemented. It represents the risk that persists despite mitigation.
3. How do organizations assess and manage inherent risk?
Organizations assess inherent risk by identifying potential vulnerabilities and threats associated with their operations. To manage it, they may employ risk avoidance, risk reduction, risk transfer, or risk acceptance strategies, depending on the magnitude of the risk.
4. What are some best practices for minimizing residual risk?
Best practices for minimizing residual risk include maintaining clear policies and procedures, investing in employee training, implementing data encryption, conducting regular audits and assessments, ensuring compliance with regulations, and continuously evaluating third-party risks.
5. Why is ongoing monitoring and adjustment essential in risk management?
Ongoing monitoring and adjustment are crucial to ensure that risk mitigation strategies remain effective. It helps organizations identify emerging risks, vulnerabilities, and areas of concern, allowing them to adapt and respond proactively.


















