5 infosec compliance questions to ask potential SaaS vendors

Deloitte reported that organizations that excelled in performance were 59% more inclined to report favorable outcomes when they proactively engaged in cybersecurity initiatives within their partner ecosystems. Additionally, Deloitte's research revealed that a substantial 85% of highly cyber-mature organizations had established cybersecurity risk programs dedicated to overseeing and assessing the security status of their partners and suppliers.
One of the pivotal contributors to an organization's success is its software as a service (SaaS) vendors. This article will delve into the five critical information security compliance inquiries that large enterprises should pose to prospective SaaS vendors.
What is infosec compliance?
Infosec compliance can be defined as following industry-specific laws, regulations, and standards for protecting an organization's information. Infosec compliance is based on three principles – confidentiality, integrity, and availability, collectively known as the CIA triad. The CIA triad ensures that the information is readily available to authorized persons when they need it, and they can rely on the integrity of this information.
5 infosec compliance questions large enterprises must ask potential SaaS vendors
Fortune Business Insights predicted the compound annual growth rate (CAGR) of the SaaS market to be 19.7% during the forecast period of 2022 to 2029. The market is expected to grow from $251.17 billion in 2022 to $883.34 billion in 2029.
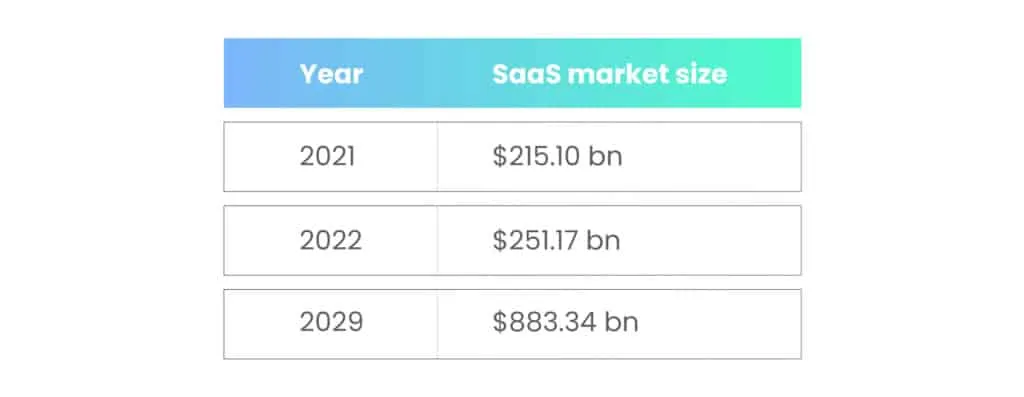
In the coming years, the dependency of organizations – large and small – on SaaS vendors will increase considerably. On average, a large organization (with revenue of $5 billion or more) spends $250 million or more on the cyber landscape (Deloitte). This amount includes the money spent on cybersecurity initiatives in partner ecosystems.
As an organization moves towards finalizing its partnership with a SaaS vendor, it must assess whether the vendor follows stringent infosec compliance policies by asking the following questions.
1. Which infosec regulations and standards do you comply with?
An organization is expected to follow multiple security regulations, like GDPR, HIPAA, and CRPA, as well as infosec standards, such as SOC 2, ISO 27001, and NIST series. The regulations are mandatory to follow if they apply to the company, while the standards are recommendatory. Regulations and standards can improve the cybersecurity posture of the organization.
You must ask your SaaS provider which regulations and standards they follow. Regulations and standards provide a framework for the organization to develop information security policies and procedures. If your SaaS vendor follows standards, they will have a report or a certificate indicating that they have cleared the required audits.
2. What does your infosec protocol look like?
The software and the behavioral rules defined by the organization to access, handle, use, and transfer data are called the infosec protocol. You must ask the organization you are interviewing whether they have an infosec protocol and, if yes, what the details are. If they don't have an infosec protocol, you must reconsider working with them, as they can put your data at risk.
A typical infosec protocol consists of rules to set passwords, use multi-factor authentication (MFA), control the flow of information, use virtual private networks (VPNs), secure data storage, and use SSL/TLS certificates to secure data in transit.
3. Do you assess your employees' infosec knowledge? And how?
For an organization's information security, having the perfect policies just framed is not adequate. The management must know if the policies are followed throughout the organization. In addition to a reliable infosec protocol, your SaaS vendor must also have implementation and assessment policies.
You must ensure that your SaaS vendor takes adequate steps to impart cybersecurity knowledge to their employees. Once the employees have been trained, the SaaS vendor must ensure that the implementation is done right.

The employees should be tested regularly on their cybersecurity knowledge in different ways, including simulation techniques, quizzes, or written tests. Repeating training after unsatisfactory assessments can enhance the cybersecurity knowledge of the employees.
4. What steps do you take to protect customer data?
One way to secure customer data is to separate it from the main network. So even if your vendor's main network is breached, your data remains safe. Check with your vendor about how they store your data. It is preferable if they use a single-tenant cloud for better security.
Ask your SaaS vendor if they restrict access to your data to the people who really need it for processing. Using MFA to verify the employee's identity before granting access can ensure the security of your data.
5. What are your incident response plans?
Incident response plans refer to an action plan in case of a security incident or a data breach. It includes the first response, actions taken to quarantine the affected area, steps taken to control the attack's spread, informing the relevant parties, and restarting the business.
A strong incident response plan can not only limit the spread of a cyber-attack but also helps in fulfilling compliance requirements. It can help the customers (in this case, you) know that your data has been breached. The SaaS vendor has an obligation to inform you of the breach and recommend a plan of action to move forward.
Conclusion
Information security compliance revolves around safeguarding an organization's data as well as the data of its customers. Non-compliance by your SaaS vendor with relevant regulations and standards can potentially jeopardize your data. It's essential to determine whether your SaaS vendor implements sufficient safeguards to secure their information network, thereby ensuring an extended layer of security for your data as well.
Scrut Automation is an innovative and radically simple governance, risk, and compliance automation platform for growing startups and mid-market enterprises. With Scrut, compliance teams can reduce ~70% of their manual effort in continuously maintaining compliance towards SOC 2, ISO 27001, GDPR, PCI DSS, HIPAA, and CCPA. Schedule your demo today to see how it works.
FAQs
1. What are the key compliance questions you should ask your vendors? The key compliance concerns to address with your vendor are the infosec regulations they follow, the things included in their infosec program, their employee's infosec awareness, the steps they take to protect customer data, and their incident response plan.
2. What is an incident response plan? An incident response plan refers to the documented procedure to be followed in case of a data breach or cybersecurity incident. It includes all the actions the organization must take to mitigate the effects of the breach, stop the lateral movement of the attacker, take corrective actions, and restart the business of the organization after the breach.
3. What are the consequences of not asking compliance questions to a potential SaaS vendor? Not asking questions about a SaaS vendor's compliance posture can increase the cybersecurity risk of an organization. Regulatory bodies can also find the organization to be in non-compliance with regulations, leading to fines and penalties.


















