How to select the right cyber risk quantification method
Cybersecurity and risk management are paramount for new-age businesses. Cyber risk quantification is a crucial step in understanding and mitigating cybersecurity risks like ransomware, malware, zero-day attacks, DDoS, etc.
But with various models and approaches available, selecting the best one for your organization can be challenging. In this blog, we’ll delve into the key considerations for choosing the right cyber risk quantification approach to safeguard your digital assets effectively.
Understanding cyber risk quantification
Cyber Risk Quantification (CRQ) is the process of calculating risk exposure and its potential financial impact on an organization in business-relevant terms. It involves attributing numerical values to the impact of cyber events on an organization’s operations, finances, and reputation. This has several benefits, such as:
- Financial clarity: It offers security leaders a clear understanding of the financial impacts of successful cybersecurity attacks, enabling organizations to assess potential losses.
- Resource allocation: CRQ helps organizations allocate resources more efficiently by focusing on addressing the most critical risks, preventing them from focusing on every risk and spreading resources thin.
- Targeted response: It strengthens an organization’s cyber maturity and resilience by providing insights into specific cyber threats. This allows for a more targeted and effective response to mitigate risks.
- Informed decision-making: Quantifying cyber risks empowers decision-makers with data-driven insights, enabling them to make informed decisions regarding cybersecurity investments, risk mitigation strategies, and cyber insurance coverage.
Exploring cyber risk quantification models
Quantitative methods of cyber risk quantification involve numerical data and measurable metrics, providing objective assessments of potential financial loss or impact from cyber threats. In contrast, qualitative methods rely on subjective judgments and descriptive evaluations to assess risk factors based on the analyst’s experience and expertise.
Cyber risk quantification methods are crucial tools for organizations to assess and measure their cyber risk. These models help express cyber risk in quantitative terms, allowing organizations to make informed decisions regarding cybersecurity investments, risk mitigation strategies, and cyber insurance coverage. Here are some notable cyber risk quantification methods:
1. FAIR model
The FAIR Model, which stands for Factor Analysis of Information Risk, is a framework used for analyzing, measuring, and understanding cybersecurity and operational risk in financial terms. It provides a structured approach to assess and quantify risk factors associated with information assets and processes.
FAIR provides a standard taxonomy for defining risk factors and attributes, which helps organizations consistently identify and assess risks. It assesses risk by considering the probability of an event occurring and its potential financial impact on an organization. Many cyber risk quantification solutions use the FAIR method to calculate risk.
How to calculate risk under the FAIR model
The FAIR method calculates cyber risk by considering two main components: Loss Event Frequency (LEF) and Loss Magnitude (LM). The formula for calculating risk in FAIR can be expressed as:
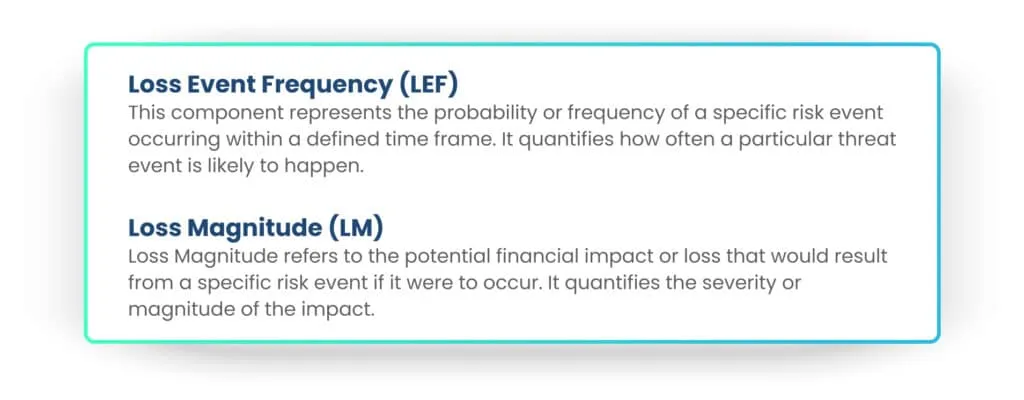
Risk = LEF x LM
By multiplying the LEF by the LM, FAIR provides a quantitative measure of the overall risk associated with a particular threat event. This approach allows organizations to assess and prioritize cybersecurity risks based on both their likelihood and potential impact in financial terms.
It’s important to note that the FAIR method employs a structured approach to gather data, assess risk factors, and assign values to LEF and LM. Monte Carlo simulations and other quantitative methods may also be used to refine the risk calculation.
Advantages of implementing the FAIR model:
- Quantitative analysis: FAIR focuses on quantitative analysis, allowing organizations to express risk in monetary terms. This helps in prioritizing risks and making informed decisions regarding risk mitigation strategies and resource allocation.
- Consistency: It provides a standardized taxonomy and methodology, ensuring consistency in risk assessments. This consistency aids in the effective communication of risk information within and across organizations.
- Objective assessment: FAIR offers an objective and systematic way to assess risk, reducing subjectivity in risk evaluations and leading to more accurate results.
- Risk prioritization: By quantifying risk, FAIR helps organizations prioritize risks based on their potential financial impact. This assists in directing resources to address the most critical risks.
Drawbacks of implementing the FAIR model:
- Complexity: FAIR can be complex to implement, requiring a deep understanding of risk factors, data sources, and probability distributions. This complexity may limit its adoption by smaller organizations or those with limited resources.
- Resource-intensive: Implementing FAIR often demands substantial time and resources, including access to relevant data, expertise in risk modeling, and specialized software tools.
- Data availability: The accuracy of FAIR assessments heavily depends on the availability of reliable data. In some cases, organizations may struggle to obtain accurate data for quantitative analysis.
- Subjectivity in inputs: While FAIR aims for objectivity, the quality of inputs and assumptions made during the modeling process can introduce subjectivity and bias into the results.
2. OCTAVE (Operationally critical threat, asset, and vulnerability evaluation)
OCTAVE, which stands for Operationally Critical Threat, Asset, and Vulnerability Evaluation, is a risk assessment methodology developed by the CERT Coordination Center at Carnegie Mellon University. It is designed to help organizations assess and manage their information security risks effectively.

Key benefits of using OCTAVE
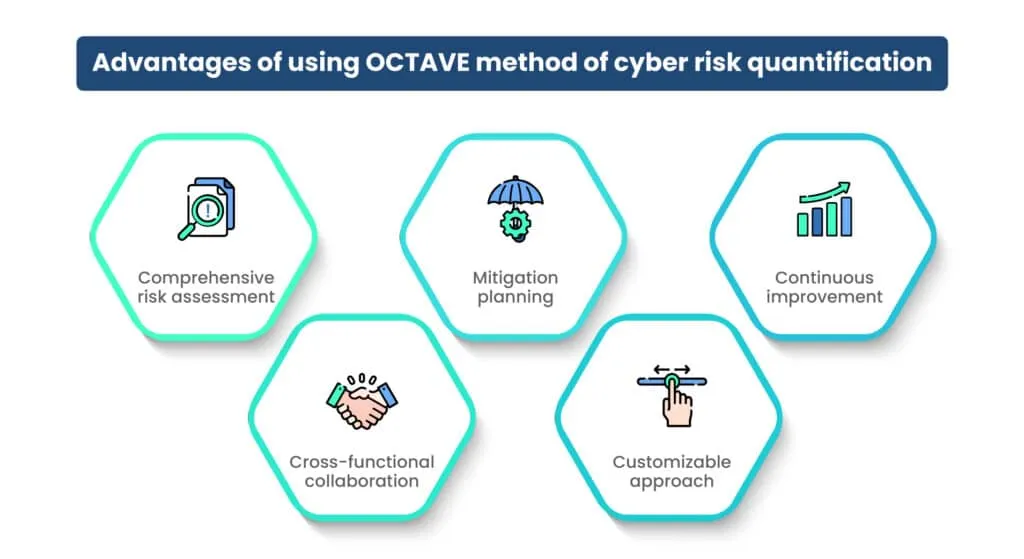
- Comprehensive risk assessment: Provides a structured framework for conducting a comprehensive assessment of information security risks within the organization.
- Cross-functional collaboration: Encourages collaboration among different departments and stakeholders, fostering a holistic approach to risk management.
- Mitigation planning: Facilitates the development of targeted risk mitigation strategies based on identified threats and vulnerabilities.
- Customizable approach: Allows organizations to adapt the methodology to their unique risk landscape and organizational structure.
- Continuous improvement: OCTAVE encourages a mindset of continuous improvement in managing information security risks, promoting ongoing assessments and updates to risk mitigation strategies.
Limitations of OCTAVE cyber risk quantification method
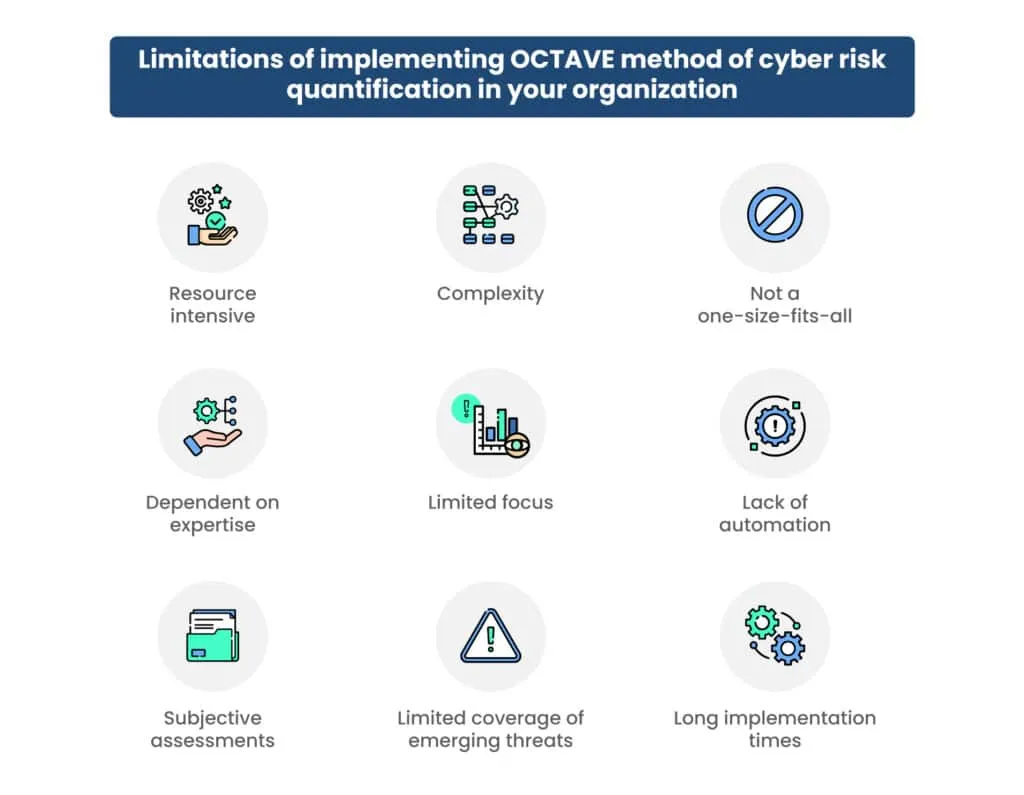
The OCTAVE method is a well-regarded approach for assessing and managing information security risks, but like any methodology, it has its limitations. Here are some of the key limitations associated with the OCTAVE method:
- Resource-intensive: OCTAVE can be resource-intensive, both in terms of time and personnel. It requires a significant commitment from the organization, which may be challenging for smaller organizations with limited resources.
- Complex: The OCTAVE method can be complex to implement, especially for organizations with little experience in risk assessment and management. It involves a structured process with multiple stages and can be overwhelming for those unfamiliar with the methodology.
- Not a one-size-fits-all: OCTAVE may not be suitable for all organizations or industries. It was initially developed with large, critical infrastructure organizations in mind, and adapting it to smaller organizations or different industries may require significant modifications.
- Dependent on expertise: Effective implementation of OCTAVE relies on having individuals with the necessary expertise in risk management and cybersecurity. Smaller organizations may struggle to find or afford such experts.
- Limited focus: OCTAVE primarily focuses on information security risks and may not fully address broader enterprise risk management concerns. Organizations looking for a more comprehensive risk assessment may need to supplement OCTAVE with other methodologies.
- Lack of automation: OCTAVE is a manual process that relies heavily on interviews, workshops, and documentation review. This lack of automation can make it time-consuming and potentially error-prone.
- Subjective assessments: Like many qualitative risk assessment methods, OCTAVE’s results can be influenced by subjectivity and biases introduced by the assessors. This subjectivity can lead to varying results when different teams or individuals conduct the assessment.
- Limited coverage of emerging threats: OCTAVE may not adequately address rapidly evolving cyber threats and emerging risks, as its focus is on existing assets and vulnerabilities. Organizations need to complement OCTAVE with ongoing threat intelligence and risk monitoring.
- Long implementation times: The OCTAVE method can take a significant amount of time to complete, which may not align with the need for quick decision-making in rapidly changing cybersecurity environments.
3. NIST 800-30
NIST Special Publication 800-30 is a comprehensive guide provided by the National Institute of Standards and Technology (NIST) for conducting risk assessments of information systems, particularly within federal agencies. It outlines a systematic approach to identifying, analyzing, and managing risk in the context of information security.
How to quantify cyber risk under NIST 800-30
Calculating risk under the NIST 800-30 model involves a structured process that considers the likelihood and impact of risks to information systems. These steps can be automated using cyber risk quantification tools.
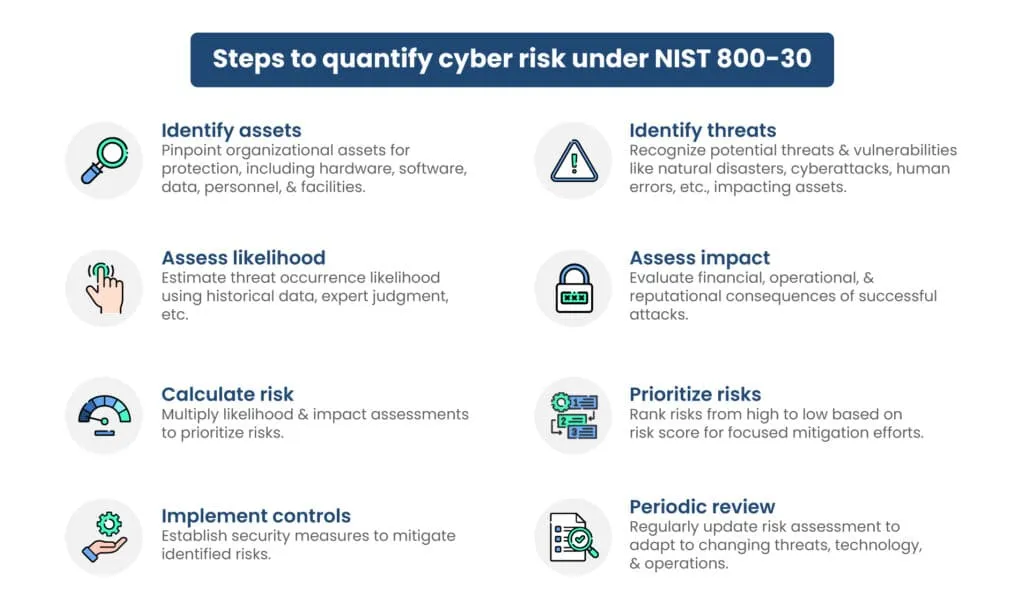
Advantages of implementing NIST 800-30:
- Structured framework: NIST SP 800-30 provides a structured and systematic approach to conducting technical risk assessments. It outlines a clear methodology for identifying, evaluating, and mitigating risks.
- Comprehensive guidance: It offers comprehensive guidance for assessing vulnerabilities and threats within defined system boundaries. This thoroughness ensures that potential risks are not overlooked.
- Mapping capability: NIST SP 800-30 allows for the mapping of vulnerabilities, threats, and risks, making it easier to understand the relationships between different elements of the risk assessment process.
- Risk communication: It assists in communicating technical risks effectively to stakeholders, enabling informed decision-making regarding risk mitigation strategies.
Drawbacks of implementing NIST 800-30:
- Complexity: The comprehensive nature of NIST SP 800-30 can make it complex and time-consuming to implement. Smaller organizations or those with limited resources may find it challenging to conduct assessments using this framework.
- Resource intensive: Conducting a technical risk assessment following NIST SP 800-30 may require significant resources, including expertise in cybersecurity, access to relevant data, and specialized tools.
- Focus on technical aspects: While it excels in addressing technical risks, NIST SP 800-30 may not provide a holistic view of an organization’s overall risk landscape. It primarily concentrates on technical vulnerabilities and threats.
- Updates and evolving threats: The document may not always reflect the most current cybersecurity threats and technologies. Organizations need to stay updated and adapt their assessments accordingly.
CyberInsight
CyberInsight is a cyber risk quantification method that involves measuring and analyzing the potential financial impact of a cyberattack on an organization. It focuses on evaluating cyber risks in a structured and data-driven manner, allowing organizations to make informed decisions regarding their cybersecurity strategies and investments.
How do we quantify cyber risk under the CyberInsight model?
The CyberInsight model is designed to help organizations quantify and manage their cyber risks effectively.
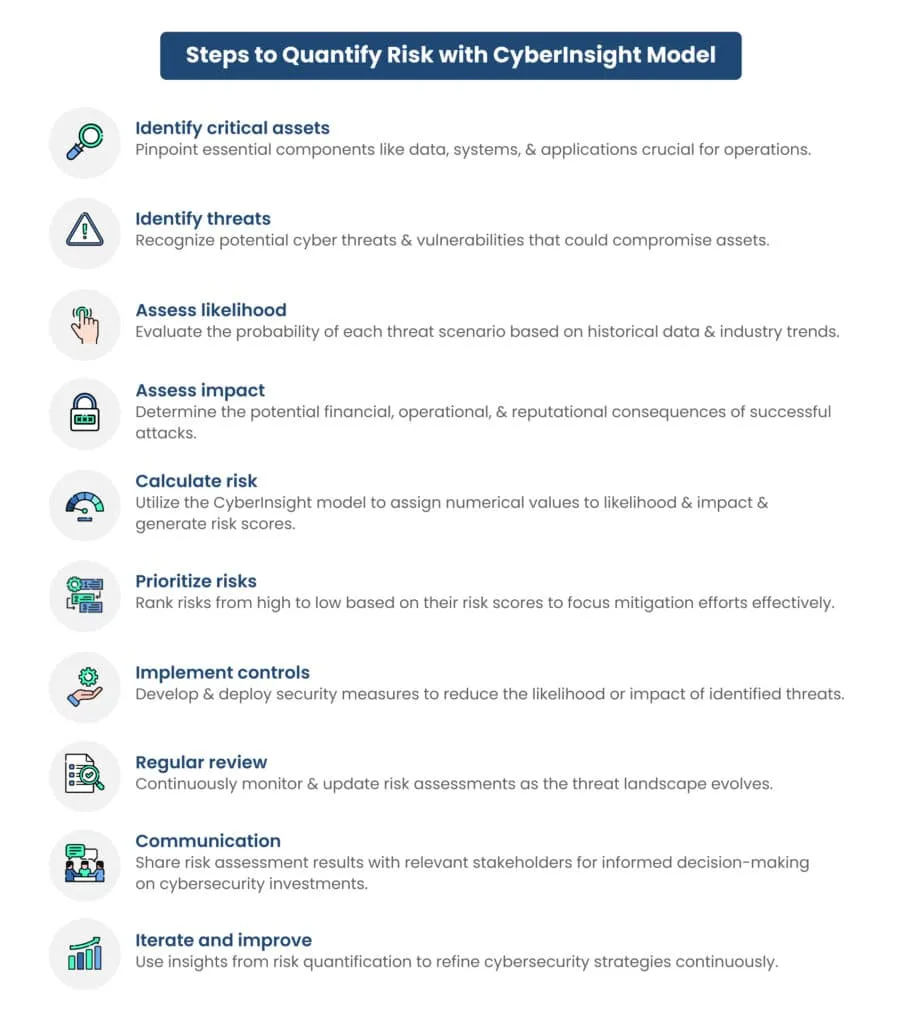
Advantages of Implementing CyberInsight:
- Objective assessment: CyberInsight provides an unbiased assessment of cyber risks, reducing the potential for subjective judgments.
- Continuous monitoring: Organizations can proactively manage cyber risks by continuously monitoring their risk posture.
- Data-driven decision-making: The method relies on data, enabling informed decisions on cybersecurity investments and strategies.
- Comparison to benchmarks: Users of CyberInsight can compare their cyber risk posture to industry benchmarks, such as the NIST Cybersecurity Framework (CSF). This benchmarking helps organizations understand how they stack up against recognized standards.
Drawbacks of Implementing CyberInsight:
- Complexity: Implementing CyberInsight may require expertise in data analysis and cybersecurity.
- Resource intensive: Gathering and analyzing data for real-time risk assessments can be resource-intensive.
- Dependence on data quality: Accurate results depend on the quality and completeness of data used for analysis.
Monte Carlo method
The Monte Carlo method is a mathematical cyber risk quantification method to assess and analyze the potential financial impact of cyber threats and vulnerabilities. It is named after the Monte Carlo Casino in Monaco because of the element of chance and randomness it involves.
How it works:
- Simulation: The Monte Carlo method constructs multiple possible outcomes (scenarios) based on various input parameters and probabilities. In the context of cyber risk, these scenarios represent different cyberattack events.
- Random sampling: It employs random sampling from probability distributions to create these scenarios. For example, it considers factors such as the likelihood of a cyberattack, the type of attack, and its potential impact.
- Analysis: Each scenario is then analyzed to calculate the associated financial loss. By running a large number of simulations (thousands or more), it provides a range of possible financial outcomes.
- Risk assessment: The method helps organizations understand the range of potential financial losses due to cyber incidents, allowing for better risk assessment and decision-making.
Advantages of implementing the Monte Carlo Method:
- Comprehensive: It considers a wide range of potential cyberattack scenarios and their financial implications, providing a holistic view of cyber risk.
- Flexibility: Can be adapted to different cyber risk assessment models and customized based on an organization’s specific needs.
- Quantitative results: Provides quantitative results, making it easier to prioritize cybersecurity investments and measure risk exposure.
Drawbacks of implementing the Monte Carlo Method:
- Data requirements: Requires accurate data on cyber threats, vulnerabilities, and their probabilities, which can be challenging to obtain.
- Complexity: Implementing Monte Carlo simulations can be complex and may require specialized expertise.
- Resource-intensive: Running a large number of simulations can be computationally intensive and time-consuming.
Custom Models in Cyber Risk Quantification (CRQ)
Custom models in cyber risk quantification are indispensable tools that organizations employ to assess and manage their cybersecurity risks effectively. These models are tailored to the specific needs, risk profiles, and circumstances of each organization, ensuring a customized approach to risk management.
Advantages of Custom CRQ Models
- Tailored solutions: Custom CRQ models address specific organizational needs, ensuring accurate risk assessment.
- Industry relevance: They consider industry-specific threats, aligning risk assessments with sector challenges.
- Regulatory compliance: Custom models integrate regulatory requirements, ensuring legal adherence.
- Asset focus: Prioritize assets effectively, optimizing resource allocation for protection.
- Risk prioritization: Enable focusing on critical risks based on organizational objectives.
- Flexibility: Adapt to evolving threats and business changes for continued relevance and effectiveness.
Limitations of Custom CRQ models
- Complexity and cost: Developing custom CRQ models can be time-consuming and expensive compared to off-the-shelf solutions.
- Expertise requirement: Custom models may require specialized expertise for development and maintenance, posing a challenge for organizations lacking in-house skills.
- Potential bias: Custom models may reflect the biases or assumptions of the developers, leading to less objective risk assessments.
- Limited scalability: Custom models may have limited scalability, making it difficult to adapt to organizational growth or changes in the risk landscape.
- Dependency on data quality: They rely heavily on accurate and comprehensive data, which can be challenging to obtain and maintain.
- Risk of overfitting: There’s a risk of overfitting the model to past data, which may not accurately represent future risks or scenarios.
Factors to consider while choosing the right cyber risk quantification method

When selecting a cyber risk quantification method, organizations should carefully consider several factors to ensure they align with their unique needs and context. Here are key factors to emphasize:
- Regulatory compliance: Compliance with cybersecurity regulations and standards is paramount. The selected approach should help the organization meet its legal and regulatory obligations, such as GDPR, HIPAA, or industry-specific guidelines.
- Data sensitivity: The nature of the organization’s data, including sensitive customer information, intellectual property, or financial data, impacts the level of risk. The chosen approach should assess and prioritize risks related to data sensitivity.
- Technology infrastructure: The organization’s existing technology stack and cybersecurity tools should integrate smoothly with the chosen quantification approach. Compatibility is crucial for efficient risk assessment and management.
- Risk complexity: The complexity of the organization’s risk landscape should be considered. Some organizations face multifaceted risks, such as supply chain vulnerabilities or advanced persistent threats, which require a more sophisticated quantification approach.
- Scalability: The chosen approach should be scalable to accommodate the organization’s growth and evolving cybersecurity needs. It should adapt as the organization expands or changes its technology landscape.
- Integration with existing processes: The chosen approach should seamlessly integrate with existing risk management and cybersecurity processes to avoid disruption and streamline risk mitigation efforts.
- Cost-benefit analysis: Finally, conduct a cost-benefit analysis to determine whether the chosen quantification approach delivers sufficient value relative to its cost.
Making the right decision
In making an informed decision for the best cyber risk quantification approach, it’s essential to tailor the choice to your organization’s unique needs, risk profile, and objectives. Ensure that the approach is customizable and aligns with industry-specific threats, regulatory demands, and organizational assets.
Additionally, you must emphasize the significance of ongoing evaluation and adaptation to stay resilient in the face of ever-evolving cyber threats. Cybersecurity is a dynamic field, and your quantification approach should reflect this by continuously monitoring, assessing, and adjusting to emerging risks. By staying agile and proactive, your organization can effectively manage cyber risks over the long term.
Take proactive steps to strengthen your risk management strategy today. Start by evaluating your current risk assessment processes and consider implementing a comprehensive cyber risk quantification approach tailored to your organization’s specific needs.
Engage with Scrut experts in the field, stay updated on evolving cyber threats, and regularly assess and adapt your risk management practices. By prioritizing risk management, you can safeguard your organization against potential cyber threats and enhance its overall resilience.
FAQs
1. What are the notable models for cyber risk quantification, and how do they work?
Notable CRQ models include FAIR, NIST 800-30, CyberInsight, Monte Carlo, and custom models. They each provide structured approaches to assess and measure cyber risk in financial terms, helping organizations make informed decisions.
2. What are the notable models for cyber risk quantification, and how do they work?
Notable CRQ models include FAIR, NIST 800-30, CyberInsight, Monte Carlo, and custom models. They each provide structured approaches to assess and measure cyber risk in financial terms, helping organizations make informed decisions.
3. How does the Monte Carlo method work in cyber risk quantification, and what are its strengths and weaknesses?
The Monte Carlo method uses simulations to assess the potential financial impacts of cyber threats. Strengths include comprehensiveness, flexibility, and quantitative results. Weaknesses include data requirements, complexity, and resource intensity.


















