Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Your 8-Minute Guide to Risk Control Matrix
Last updated on
April 21, 2025
8
min. read

Without proper risk management, an organization faces increased vulnerability to unexpected events and threats, leading to potential financial losses, reputation damage, regulatory non-compliance, and operational disruptions. This lack of preparedness can hinder the achievement of strategic objectives, erode stakeholder trust, and ultimately jeopardize the organization’s long-term sustainability and success.
By proactively addressing risks, organizations can make informed decisions, enhance operational resilience, protect assets, and maintain stakeholder trust, ultimately driving long-term success and sustainability.
Additionally, effective risk management fosters a culture of accountability, innovation, and continuous improvement within the organization, enabling it to adapt to changing environments and seize opportunities for growth.
A Risk Control Matrix (RCM) enables organizations to systematically evaluate potential risks, prioritize them based on severity and likelihood, and implement appropriate control measures. In this article, we will learn all about the risk control matrix.
What is the Risk Control Matrix? What is its purpose?
A Risk Control Matrix (RCM) is a structured tool used by organizations to systematically identify, assess, and manage risks and controls. It provides a comprehensive overview of an organization’s risk setting by mapping potential risks against established control measures.
Overall, RCMs play a critical role in enhancing risk management practices, fostering a proactive approach to identifying and addressing risks to achieve organizational objectives.
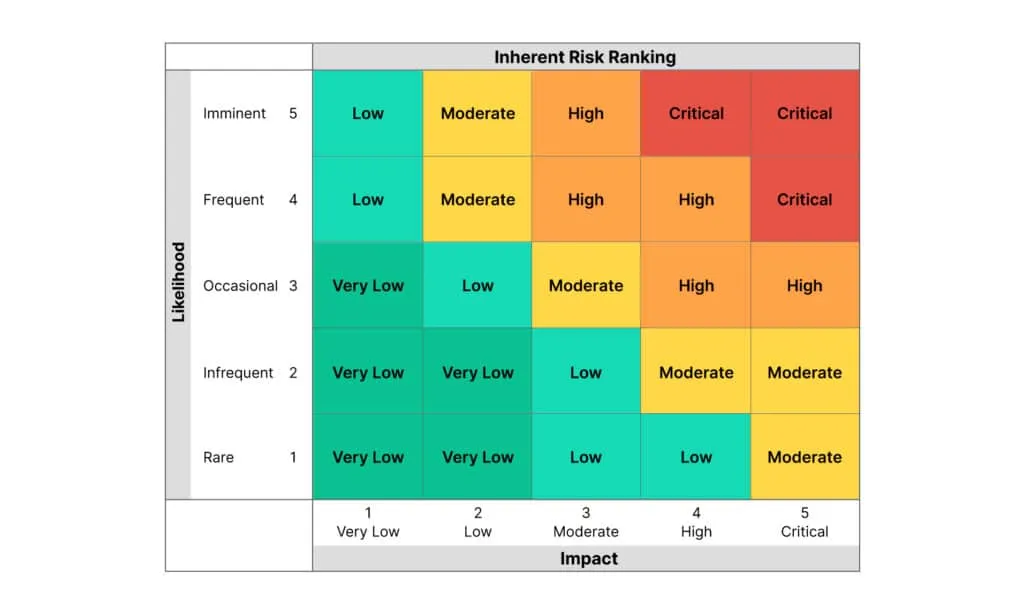
Example of a risk control matrix:
What is the importance of RCM in cybersecurity and compliance?
The Risk Control Matrix plays a crucial role in cybersecurity and compliance by providing a structured framework for organizations to identify, assess, and mitigate risks related to data security and regulatory requirements.
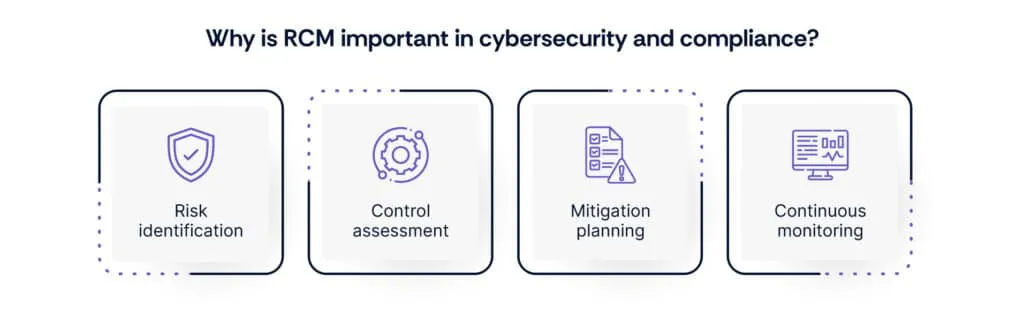
Here’s why RCM risk control matrix is important in these areas:
- Risk identification: RCM helps identify cybersecurity risks such as data breaches, unauthorized access, and system vulnerabilities, ensuring proactive measures are taken to address them.
- Control assessment: By aligning risks with existing controls, RCM enables organizations to evaluate the effectiveness of cybersecurity measures and compliance protocols, ensuring they meet industry standards and regulatory requirements.
- Mitigation planning: RCM assists in prioritizing cybersecurity risks and compliance gaps, allowing organizations to allocate resources efficiently for risk mitigation and regulatory compliance.
- Continuous monitoring: Through regular updates and reviews, RCM risk control matrix facilitates ongoing monitoring of cybersecurity controls and compliance measures, ensuring organizations remain resilient against evolving threats and regulatory changes.
How does the RCM contribute to an organization’s GRC efforts?
A Risk and Control Matrix is crucial for Governance, Risk, and Compliance (GRC) programs in several ways:
- Comprehensive risk assessment: RCM facilitates a structured approach to identifying and assessing risks. It links business objectives with associated risks and control processes, providing a holistic view of the organization’s risk landscape.
- Control effectiveness evaluation: RCM risk control matrix helps evaluate the effectiveness of existing controls in mitigating identified risks. By aligning risks with control measures, it enables organizations to gauge control adequacy and identify gaps.
- Risk prioritization and mitigation: It aids in prioritizing risks based on severity and likelihood. This prioritization assists in resource allocation and ensures that high-priority risks are effectively addressed to minimize potential negative impacts.
- Compliance assurance: RCM supports compliance efforts by aligning risks with regulatory requirements. It helps organizations implement control measures to meet compliance standards and mitigate compliance-related risks effectively.
How can you create an RCM tailored for your organization?
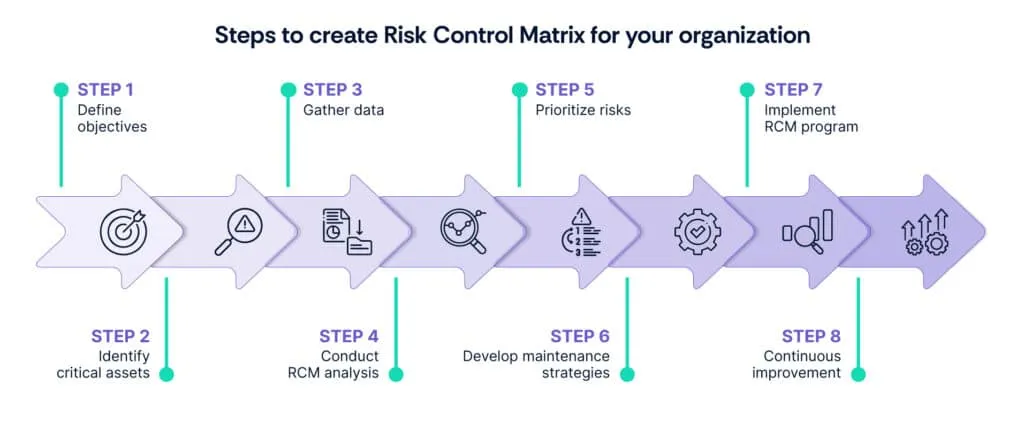
Step 1: Define objectives
Clearly outline the objectives and goals of implementing RCM within the organization. Determine what the organization aims to achieve through the RCM process, such as improving asset reliability, reducing maintenance costs, or enhancing safety.
Step 2: Identify critical assets
Identify the critical assets or equipment essential to the organization’s operations. Prioritize assets based on their significance and impact on production, safety, and overall performance.
Step 3: Gather data
Collect relevant data about the selected assets, including maintenance history, failure patterns, operational characteristics, and environmental conditions. Data gathering is essential for understanding asset behavior and performance.
Step 4: Conduct RCM analysis
Use structured analysis techniques like Failure Modes and Effects Analysis (FMEA) to identify potential failure modes, their causes, and the consequences of failure on asset performance. This step helps in understanding asset vulnerabilities and developing appropriate maintenance strategies.
Step 5: Prioritize risks
Prioritize identified failure modes based on their criticality and impact on organizational objectives. Consider factors such as safety, environmental impact, regulatory compliance, and financial implications to prioritize risks effectively.
Step 6: Develop maintenance strategies
Develop tailored maintenance strategies for each prioritized failure mode. Select appropriate maintenance tasks, such as preventive, predictive, or proactive maintenance, to mitigate or eliminate identified risks effectively.
Step 7: Implement RCM program
Implement the developed RCM risk control matrix program by integrating maintenance strategies into existing maintenance management systems. Ensure proper training and communication to facilitate smooth implementation.
Scrut offers an excellent program for the training and development of your employees. It also helps you to design the program based on your requirements. You can not only train your employees but also test them on the Scrut platform.
Step 8: Continuous improvement
Establish mechanisms for continuous monitoring, evaluation, and improvement of the RCM program. Regularly review asset performance, update maintenance strategies as needed, and incorporate lessons learned to enhance the effectiveness of the RCM process.
Best practices for documenting and maintaining RCMs
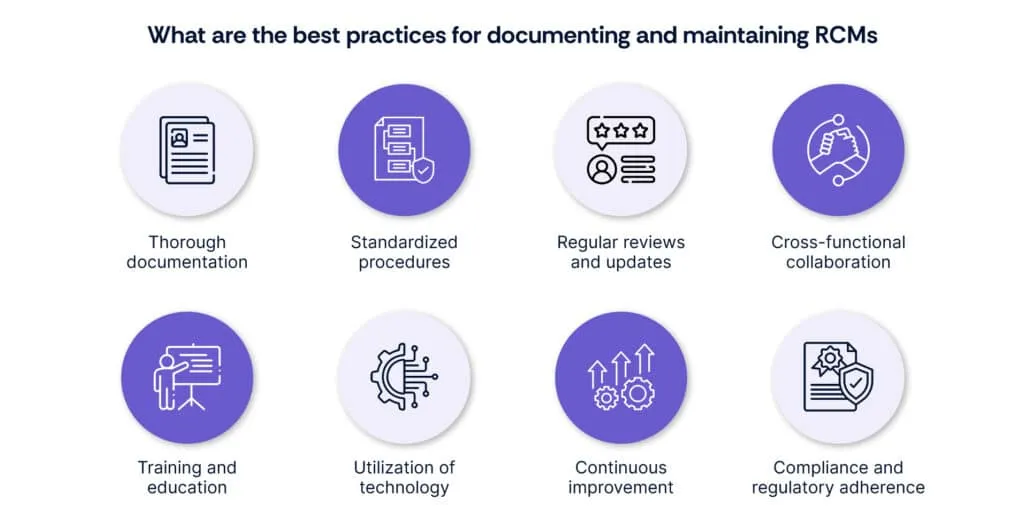
- Thorough documentation:
- Document all steps of the RCM process, including risk identification, assessment, control measures, and monitoring.
- Ensure documentation is clear, concise, and accessible to relevant stakeholders.
- Standardized procedures:
- Establish standardized procedures for RCM implementation to ensure consistency and reliability in risk management practices.
- Regular reviews and updates:
- Conduct regular reviews of RCM documentation to reflect changes in organizational processes, technologies, and regulations.
- Update RCMs as necessary to address emerging risks and improve effectiveness.
- Cross-functional collaboration:
- Foster collaboration between different departments involved in risk management to gather diverse perspectives and expertise.
- Encourage open communication channels to facilitate the sharing of insights and best practices.
- Training and education:
- Provide training to staff involved in RCM development and implementation to ensure understanding of methodologies and best practices.
- Keep staff updated on industry trends, regulatory changes, and advancements in risk management techniques.
- Utilization of technology:
- Leverage technology and automation tools to streamline RCM processes, enhance data analysis capabilities, and improve efficiency.
- Implement software solutions tailored to RCM needs for enhanced documentation and reporting.
- Continuous improvement:
- Foster a culture of continuous improvement within the organization, encouraging feedback loops and opportunities for refinement of RCM practices.
- Monitor key performance indicators to assess the effectiveness of RCM risk control matrix implementation and identify areas for enhancement.
- Compliance and regulatory adherence:
- Ensure RCMs align with relevant industry standards, regulations, and compliance requirements.
- Regularly audit RCM processes to verify compliance and address any gaps or deficiencies.
Explore simplified continuous compliance automation with Scrut
Scrut is a compliance automation platform designed to streamline information security for cloud-native companies. Scrut offers features that contribute to the risk management process:
- Risk-focused approach: Scrut emphasizes a risk-focused approach to compliance automation, aligning with the principles of risk management and control.
- Expert-vetted scoring methodologies: Scrut incorporates built-in expert-vetted scoring methodologies, enabling users to quantify their organization’s risk profile. This feature can assist in assessing and prioritizing risks, which is a fundamental aspect of creating RCMs.
- Continuous monitoring: Continuous monitoring capabilities provided by Scrut can help organizations stay updated on their compliance status and identify emerging risks promptly. This real-time insight can inform the development and refinement of RCMs as the organization’s risk landscape evolves.
- Compliance automation: By automating compliance processes, Scrut helps save time and resources that can be allocated to strategic initiatives, including the development and implementation of RCMs.
Conclusion
In conclusion, effective risk management is essential for organizational success. Without it, organizations face financial losses, reputation damage, and operational disruptions. The Risk Control Matrix (RCM) is a valuable tool for systematically identifying, assessing, and managing risks.
By prioritizing risks, implementing control measures, and fostering a culture of accountability and innovation, organizations can enhance their resilience and achieve strategic objectives.
Through best practices and tools like Scrut, they can streamline risk management processes, ensure compliance, and adapt to evolving threats, ensuring long-term success in today’s dynamic business environment.
Streamline risk management with Scrut. Simplified compliance automation tailored to your needs. Get started now!
FAQs
1. What is a Risk Control Matrix (RCM)?
A Risk Control Matrix (RCM) is a structured tool used by organizations to systematically identify, assess, and manage risks and controls. It provides a comprehensive overview of an organization’s risk landscape by mapping potential risks against established control measures.
2. What is a Risk Control Matrix (RCM)?
A Risk Control Matrix (RCM) is a structured tool used by organizations to systematically identify, assess, and manage risks and controls. It provides a comprehensive overview of an organization’s risk landscape by mapping potential risks against established control measures.
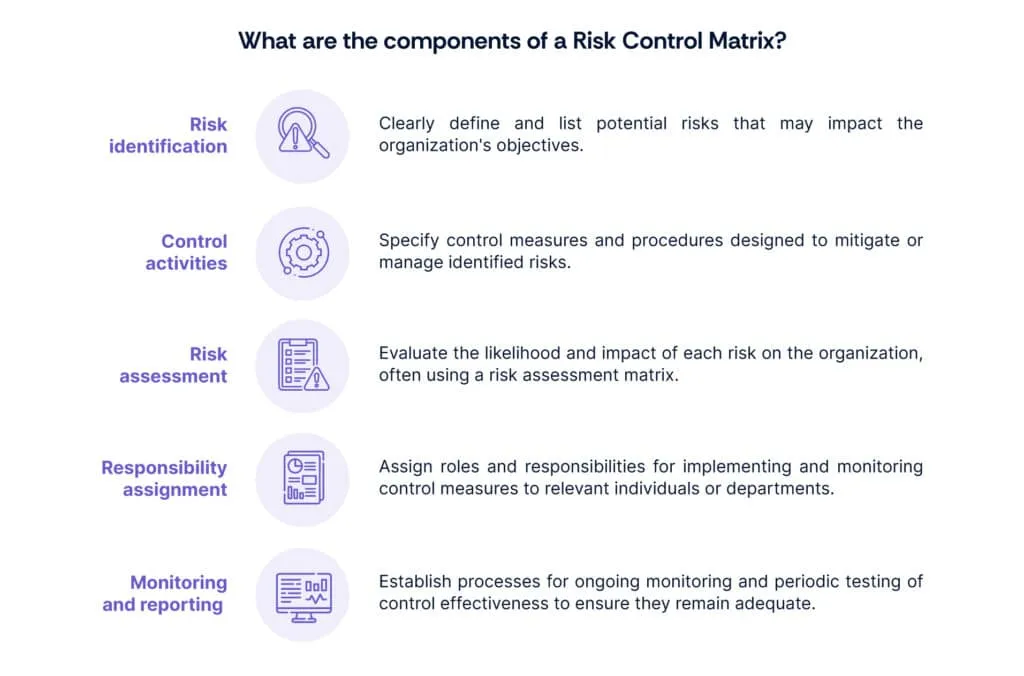
3. What are the components of a Risk Control Matrix?
The components of a Risk and Control Matrix typically include risk identification, control activities, risk assessment, responsibility assignment, and monitoring and reporting. These components collectively facilitate the systematic evaluation and management of risks within an organization.
Table of contents