How to evaluate your company's security posture?

In the latest Global Threat Report 2023, CrowdStrike reported that the breakout time of eCrimes decreased from 98 minutes in 2021 to 84 minutes in 2022. Breakout time is the time taken by a threat actor to move laterally, from the initial compromised host to another host, within the victim’s environment.
The defenders can defend themselves by responding to the attack within that time window to minimize the effects of the attack. As the breakout time decreased to 84 minutes, the security teams were encouraged to follow the 1-10-60 rule. One minute to detect the threat, 10 to understand it, and 60 minutes to respond to the threat.
A quick response is only possible if the security posture of the company is flawless. So what is the security posture of the company, and how do you evaluate it?
What is security posture?
The National Institute for Standards and Technology ( NIST) describes security posture as: “The security status of an enterprise’s networks, information, and systems based on information security resources (e.g., people, hardware, software, policies) and capabilities in place to manage the defense of the enterprise and to react as the situation changes.”
Security posture refers to the overall capacity of the company to predict, prevent, and respond to the evolving cyber threat landscape. The awareness of the cybersecurity posture of the company requires technical, operational, business, and external factors.
What are the components of security posture?
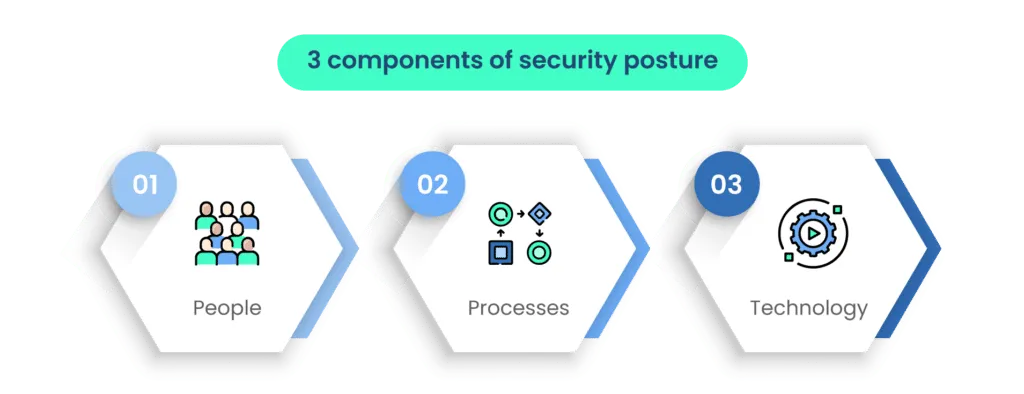
The following three components are interconnected and must work in harmony to create a strong security posture. For example, people need to follow established processes, and technology is often used to automate and enforce these processes. Regular assessment and continuous improvement of each component are essential to adapt to evolving security threats and challenges. Additionally, compliance with relevant regulations and standards, such as GDPR or ISO 27001, can help guide and enhance an organization’s security posture.
1. People
People are a crucial component of any security posture. This includes employees, contractors, and even third-party vendors who have access to an organization’s systems and data. Security awareness training and education for employees are essential to ensure that they understand their roles and responsibilities in maintaining security. Additionally, having a security team in place to monitor and respond to security incidents is vital.
2. Processes
Security processes refer to the established procedures and policies that govern how an organization manages and protects its assets, data, and systems. These processes can include incident response plans, access control policies, data encryption policies, and more. Effective processes help ensure consistency and compliance with security best practices.
3. Technology
Technology encompasses the tools and solutions an organization uses to protect its systems and data. This can include firewalls, antivirus software, intrusion detection systems, encryption tools, and other security technologies. The choice and configuration of these technologies should align with the organization’s security goals and policies.
Why assess your security posture?

Assessing your security posture is a critical practice for organizations to ensure they can protect their assets, comply with regulations, maintain customer trust, and effectively manage security risks. Here are some key reasons why assessing your security posture is essential:
1. Identifying vulnerabilities
Regular security assessments help organizations identify vulnerabilities in their systems, processes, and technology. This proactive approach allows them to discover weaknesses before cybercriminals do, reducing the risk of data breaches and other security incidents.
2. Regulatory compliance
Many industries and regions have specific regulations and compliance requirements related to data security and privacy (e.g., GDPR, HIPAA, PCI DSS). Assessing your security posture helps ensure that you are meeting these regulatory obligations, which is crucial to avoid legal penalties and fines.
3. Protecting assets and data
Assessments help organizations protect their valuable assets, including sensitive data, intellectual property, and customer information. By understanding potential risks and vulnerabilities, organizations can implement safeguards to prevent unauthorized access or data breaches.
4. Reputation and customer trust
A strong security posture contributes to a positive reputation and fosters customer trust. Customers and clients are more likely to do business with organizations they believe will protect their data and privacy. Security breaches can lead to significant damage to an organization’s reputation and customer trust.
5. Cost savings
Identifying security weaknesses early can lead to cost savings in the long run. It’s often more expensive to respond to a security incident after it has occurred than to invest in preventive measures and security assessments upfront.
6. Continuous improvement
Security assessments are not one-time activities. They are part of an ongoing process of security management. Regular assessments help organizations continuously improve their security posture by adapting to new threats and technologies.
7. Risk management
Assessing security posture allows organizations to assess and manage risk effectively. By understanding where vulnerabilities exist and the potential impact of security incidents, organizations can make informed decisions about risk mitigation strategies.
8. Business continuity
Ensuring a robust security posture is crucial for business continuity. Cyberattacks or security incidents can disrupt operations, leading to financial losses. Assessing and enhancing security helps maintain business continuity and resilience.
9. Competitive advantage
A strong security posture can also serve as a competitive advantage. Organizations that can demonstrate their commitment to security may have an edge over competitors, especially when dealing with security-conscious customers or partners.
In summary, assessing your security posture is a fundamental practice for organizations to protect their assets, comply with regulations, maintain customer trust, and effectively manage security risks.
Steps to evaluate your security posture
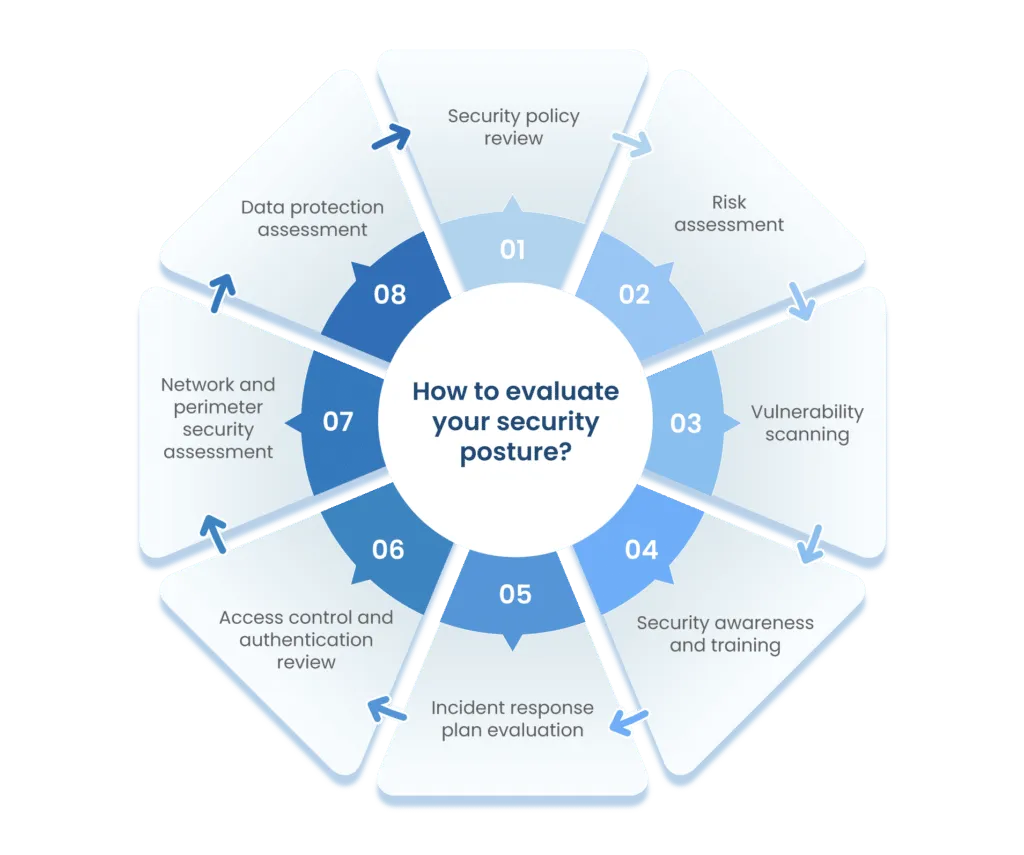
1. Security policy review
- Document review: Examine your organization’s security policies and procedures to ensure they are up-to-date and align with current best practices and regulatory requirements.
- Policy effectiveness: Assess the effectiveness of your security policies in practice, considering how well they are followed and whether they adequately protect your assets.
2. Risk assessment
- Identifying risks: Identify potential security risks and vulnerabilities within your organization, including threats to data, systems, and physical assets.
- Risk prioritization: Prioritize identified risks based on their potential impact and likelihood, helping you focus on the most critical security issues.
3. Vulnerability scanning
- Identifying weaknesses: Conduct regular vulnerability scans and assessments to pinpoint weaknesses in your systems, applications, and network infrastructure.
- Patch management: Develop a strategy for addressing and patching vulnerabilities promptly to reduce the window of opportunity for attackers.
4. Security awareness and training
- Employee training: Provide security awareness training to educate employees about security best practices, threats, and how to respond to incidents.
- Phishing tests: Test employees’ susceptibility to phishing attacks through simulated phishing campaigns to identify areas for improvement.
5. Incident response plan evaluation
- Incident simulation: Test your organization’s incident response plan through simulations of various security incidents to evaluate its effectiveness.
- Plan updates: Continuously update and refine your incident response plan based on lessons learned from simulations and real incidents.
6. Access control and authentication review
- User access auditing: Continuously update and refine your incident response plan based on lessons learned from simulations and real incidents.
- Multi-factor authentication: Implement multi-factor authentication (MFA) wherever possible to enhance authentication security.
7. Network and perimeter security assessment
- Firewall and intrusion detection: Evaluate the configuration and effectiveness of your firewalls and intrusion detection systems to protect against external threats.
- Security of remote access: Ensure that remote access methods are secure and that remote workers follow secure access practices.
8. Data protection assessment
- Data encryption: Implement encryption measures to protect sensitive data both in transit and at rest, and assess the effectiveness of existing encryption mechanisms.
- Data backup and recovery: Regularly back up critical data and test data recovery processes to ensure business continuity in case of data loss or ransomware attacks.
Tools and resources for security posture assessment

When conducting a security posture assessment, it’s important to leverage various tools and resources to ensure a comprehensive evaluation. Here are some essential tools and resources:
1. Security assessment tools
- Vulnerability scanners: Tools like Nessus, Qualys, and OpenVAS can help identify vulnerabilities in your systems and networks.
- Penetration testing tools: Tools such as Metasploit, Burp Suite, and Nmap are used by ethical hackers to test the security of systems and applications.
- Security information and event management (SIEM) systems: SIEM solutions like Splunk and ELK Stack can help monitor and analyze security events and incidents.
- Security assessment frameworks: Frameworks like OWASP (Open Web Application Security Project) provide guidance and tools for web application security testing.
2. Third-party assessors
- Penetration testers: Independent security experts or firms can conduct penetration tests to evaluate your organization’s security by simulating attacks.
- Certification and compliance auditors: Organizations may hire third-party auditors to assess compliance with specific regulations or standards, such as PCI DSS or ISO 27001.
- Red team assessors: Red teams are groups of skilled security professionals who simulate real-world attacks to test an organization’s defenses.
3. Industry standards and frameworks
- ISO 27001: This international standard provides a framework for information security management systems (ISMS) and is widely recognized for establishing security best practices.
- NIST cybersecurity framework: Developed by the U.S. National Institute of Standards and Technology, this framework offers guidance for improving cybersecurity risk management.
- CIS critical security controls: The Center for Internet Security (CIS) provides a set of best practices to help organizations enhance their security posture.
- PCI DSS: The Payment Card Industry Data Security Standard is essential for organizations that handle credit card data.
4. Security consulting services
- Security consultants: Security consulting firms or individuals can provide expertise in security strategy, risk assessment, and overall security program development.
- Incident response services: In the event of a security incident, incident response consulting firms can help organizations investigate, contain, and recover from the incident.
- Security architecture review: Consultants can assess and recommend improvements to an organization’s security architecture and infrastructure.
Analyzing assessment results
Analyzing assessment results is a crucial step in the security posture assessment process. It involves reviewing the data collected during assessments and making informed decisions about how to address security issues. Here are the key steps in analyzing assessment results:
1. Data interpretation
Begin by carefully reviewing all the data collected during the assessment, which may include vulnerability reports, security logs, audit findings, and assessment reports. Interpret the data to understand the security posture accurately, identifying areas of strengths and weaknesses.
2. Identifying critical issues
Prioritize security issues based on their severity and potential impact on the organization. Critical issues may include vulnerabilities that are actively exploited, misconfigurations that expose sensitive data, or high-risk threats. Distinguish between issues that require immediate attention and those that can be addressed over time.
3. Prioritizing remediation
Develop a clear and structured process for prioritizing the remediation of identified security issues. Consider factors such as the potential impact of each issue, the ease of exploitation, the relevance to the organization’s assets, and any regulatory or compliance requirements. Additionally, create a risk matrix or scoring system to assist in prioritization.
4. Creating an action plan
Develop a comprehensive action plan that outlines the steps required to address each identified security issue. Assign responsibilities to individuals or teams for each remediation task. In addition, set clear timelines and deadlines for completing remediation efforts. Also, consider implementing short-term mitigations for critical vulnerabilities while more comprehensive solutions are being developed.
Throughout the analysis process, it’s essential to involve key stakeholders, including IT teams, security professionals, and management, to ensure that everyone is aligned on the priorities and actions needed to improve the security posture. Regular communication and monitoring are critical to tracking progress and adapting the action plan as necessary.
Remember that security posture assessment is an ongoing process. After remediation efforts are completed, it’s important to conduct follow-up assessments to verify that the issues have been adequately addressed and to identify any new security concerns that may have arisen. This iterative approach helps organizations continuously improve their security posture and adapt to evolving threats.
Implementing security improvements

Implementing security improvements is a crucial step in enhancing your organization’s security posture. Here are key elements and strategies for effectively implementing security improvements:
1. Remediation strategies
- Patch management: Regularly apply security patches and updates to software, operating systems, and firmware to address known vulnerabilities.
- Vulnerability remediation: Prioritize and remediate vulnerabilities based on their severity and potential impact. Implement fixes or mitigations for identified weaknesses.
- Configuration management: Review and improve the configuration of systems and network devices to minimize security risks, such as unnecessary open ports or weak access controls.
- Access control: Enhance access controls by implementing the principle of least privilege (PoLP) to restrict users and systems’ access to only what is necessary for their roles.
- Data encryption: Encrypt sensitive data at rest and in transit to protect it from unauthorized access.
- Multi-factor authentication (MFA): Implement MFA for critical systems and accounts to add an extra layer of security.
- Incident response plan: Ensure that your incident response plan is updated and tested regularly, and that all staff are familiar with their roles and responsibilities during security incidents.
2. Employee training and awareness
- Conduct regular security awareness training for employees to educate them about security best practices, social engineering threats, and recognizing phishing attempts.
- Provide training specific to employees’ roles and the security policies and procedures relevant to their job functions.
- Test and measure the effectiveness of training through simulated phishing exercises and security quizzes.
3. Continuous monitoring
- Implement continuous security monitoring solutions to detect and respond to security incidents in real-time.
- Monitor network traffic for unusual patterns or signs of malicious activity.
- Utilize intrusion detection and prevention systems (IDS/IPS) to identify and mitigate threats.
- Employ Security Information and Event Management (SIEM) systems to aggregate and analyze security event data.
4. Incident response plan
- Ensure that your incident response plan is ready for activation in case of a security incident.
- Establish clear communication channels and escalation procedures for reporting and responding to incidents.
- Regularly conduct tabletop exercises or simulations to test and improve the effectiveness of your incident response procedures.
5. Audit and compliance
- Conduct regular security audits to ensure ongoing compliance with security policies, standards, and regulations.
- Engage third-party auditors if necessary to assess and validate your security controls.
- Document audit findings and take corrective actions to address any non-compliance issues.
6. Documentation and documentation review
- Maintain thorough documentation of security policies, procedures, and remediation activities.
- Review and update documentation regularly to ensure it remains current and relevant to evolving security threats and organizational changes.
Maintaining ongoing security posture assessment

Maintaining ongoing security posture assessment is critical to ensure that your organization remains resilient against evolving threats and compliant with changing regulations. Here are key considerations for this ongoing process:
1. Regular assessments
- Conduct security assessments and audits at regular intervals, such as annually or quarterly, to continuously evaluate your security posture.
- Perform vulnerability assessments and penetration testing to identify and remediate security weaknesses.
- Regularly review and update security policies, procedures, and incident response plans to reflect changes in technology and threat landscape.
2. Evolving threat landscape
- Stay informed about emerging cybersecurity threats and vulnerabilities by monitoring security news, threat intelligence feeds, and industry reports.
- Adapt security measures and controls to address new and evolving threats. This may involve revising security policies, adding new security technologies, or enhancing employee training programs.
- Consider threat hunting and proactive threat detection techniques to identify threats before they can cause significant harm.
3. Regulatory changes
- Keep abreast of changes in relevant regulations and compliance requirements that affect your industry or region.
- Adjust security practices and policies to align with new regulatory requirements, ensuring that your organization remains in compliance.
- Engage legal or compliance experts when necessary to ensure that your organization’s practices meet legal standards.
In addition to these considerations, fostering a culture of security awareness among employees is crucial. Encourage a proactive approach to reporting security incidents or potential threats and provide ongoing security training and awareness programs.
Regularly communicate the importance of security to all employees and stakeholders, emphasizing that security is a shared responsibility. By maintaining a strong security posture through ongoing assessment and adaptation, organizations can better protect their assets, data, and reputation in an ever-changing threat landscape.
Conclusion
Assessing your security posture is crucial for various reasons, including identifying vulnerabilities, compliance, asset protection, and customer trust. Key steps involve policy review, risk assessment, vulnerability scanning, employee training, incident response planning, access control review, network security assessment, and data protection review.
Once assessments are done, interpret results, prioritize critical issues, and create an action plan. Implement improvements, such as patch management, employee training, monitoring, and robust incident response.
Maintaining ongoing security posture assessment is vital. Regular assessments, staying updated on emerging threats, adapting to regulations, and promoting a security-aware culture are essential practices.
By prioritizing and continually investing in security posture, organizations can better mitigate risks and maintain trust in an ever-changing cybersecurity landscape.
Take control of your compliance journey with Scrut. Schedule a demo today to see how we can streamline your compliance processes and ensure peace of mind.
FAQs
1. What are the key components of a company’s security posture?
The key components include people (employees and vendors), processes (security policies and procedures), and technology (security tools and solutions). These elements must work together to create a strong security posture.
2. Why should organizations assess their security posture regularly?
Regular assessment helps identify vulnerabilities, ensure compliance with regulations, protect assets, maintain customer trust, and manage security risks effectively. It’s a proactive approach to cybersecurity.
3. Why is maintaining ongoing security posture assessment important?
Maintaining ongoing assessment helps organizations adapt to evolving threats, regulatory changes, and organizational needs. It ensures they remain resilient in the face of ever-changing cybersecurity challenges.


















