Streamlining compliance: Cyber resilience with EU DORA compliance

Protecting against cyber threats and operational disruptions is critical as financial services become more digital. The Digital Operational Resilience Act (DORA), introduced by the European Union (EU), sets requirements for managing technology risks, ensuring continuity, and safeguarding data.
Many institutions struggle to meet DORA’s complex requirements, particularly those with large, intricate operations and those in the financial sector. Aligning systems with DORA’s governance, cybersecurity, and third-party risk management demands can be a significant challenge.
DORA provides a valuable framework to boost operational resilience. Institutions can meet DORA requirements and enhance security by improving risk management, third-party assessments, and monitoring.
What is EU DORA compliance?
DORA compliance refers to adherence to EU regulations designed to strengthen the operational resilience of financial institutions against ICT (Information and Communication Technology) risks.
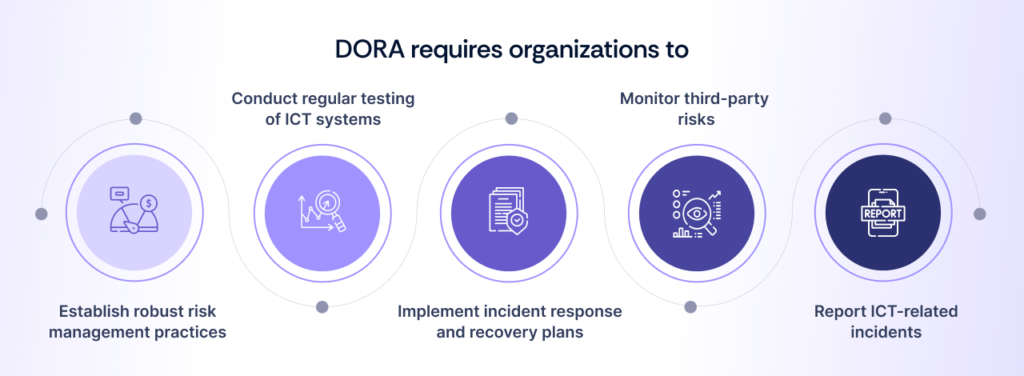
The goal is to ensure the continuity of critical services and enhance cybersecurity within the financial sector. DORA mandates comprehensive ICT resilience management, focusing on organizations’ ability to detect, prevent, and recover from disruptions caused by cyberattacks or other operational failures.
To ensure continuous service availability and data protection, financial entities must implement risk management frameworks, including cybersecurity measures, third-party oversight, and regular testing.
Scope of DORA – Entities covered
DORA applies to a broad range of entities within the financial sector.
Financial entities:
- Banks, investment firms, insurance companies, and crypto-asset service providers.
- Applies to all financial institutions, regardless of size or specialization.
Other entities covered:
- Critical infrastructure operators (e.g., energy, telecommunications, transportation).
- Healthcare organizations, government agencies, and third-party service providers such as:
- IT and cybersecurity service providers
- Cloud service providers
- Payment processors
- Data centers
These entities are required to ensure that their ICT systems are robust enough to handle disruptions, maintain business continuity, and safeguard the integrity of financial services.

Who enforces DORA and how?
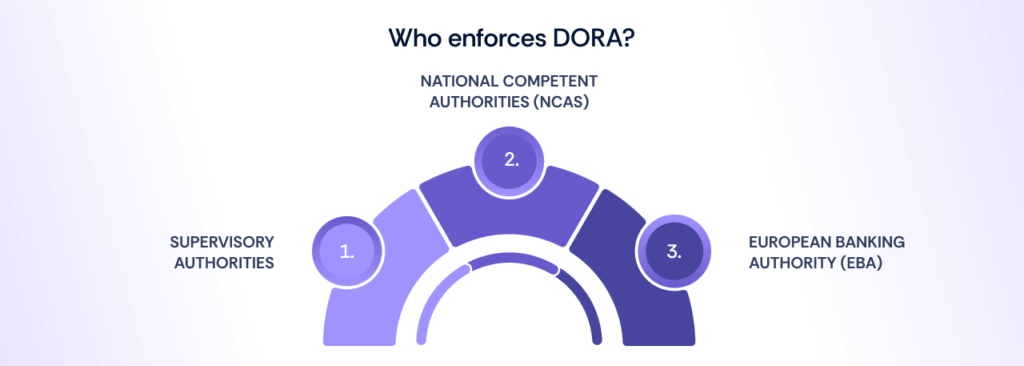
Supervisory authorities, including National Competent Authorities (NCAs) and the European Banking Authority (EBA), enforce DORA.
Their roles include:
- Evaluating operational resilience involves assessing institutions’ operational resilience plans, mapping critical services, and reviewing outsourcing arrangements.
- Conducting on-site inspections to verify compliance with DORA.
- Enforcing penalties for non-compliance.
- Providing guidance to financial institutions on DORA’s requirements.
- Fostering coordination across authorities to ensure consistent implementation and enforcement of DORA throughout the EU.
These authorities work together to ensure that financial institutions meet DORA’s stringent requirements for cybersecurity, business continuity, and operational resilience.
DORA’s rationale and evolution
DORA was introduced in response to the increasing sophistication of cyberattacks targeting the financial sector. The EU recognized the need for comprehensive legislation that goes beyond securing financial transactions to address broader ICT vulnerabilities that expose critical services to threats.
Before DORA, financial regulations focused on capital adequacy and liquidity, with less emphasis on cybersecurity and operational resilience. DORA fills this gap by requiring financial institutions to ensure their ICT infrastructure is secure and can quickly recover from disruptions.
The key shift in DORA is its holistic approach: it integrates resilience across an institution’s entire operational framework, including risk management, third-party oversight, and continuous service availability. DORA mandates risk assessments, contingency planning, and regular testing and monitoring to ensure institutions can maintain operations during crises.
Ultimately, DORA establishes comprehensive guidelines for operational resilience, promoting proactive risk management and compliance to protect against cyber threats and ICT disruptions.

Integrated overview of DORA: Key components, objectives, and provisions
DORA provides a comprehensive framework for strengthening the operational resilience of financial institutions, focusing on key components, objectives, and provisions aimed at mitigating ICT risks.
Key components and focus areas

- ICT risk management: Financial institutions must establish robust risk management practices to assess and mitigate ICT risks. This includes stress testing, vulnerability assessments, and regular risk mitigation strategies.
- Cybersecurity: Organizations must implement stringent cybersecurity measures, including encryption, access controls, and real-time monitoring to prevent, detect, and respond to cyber threats.
- Third-party risk management: DORA requires financial institutions to assess the operational resilience of third-party service providers and ensure they adhere to the same standards of ICT risk management and cybersecurity.
- Incident reporting and response: Financial entities must have clear protocols for detecting, managing, and recovering from ICT disruptions and report significant incidents to regulators within a specified timeframe.
- Operational resilience testing: Institutions are required to conduct regular resilience tests, including disaster recovery drills and cybersecurity simulations, to validate their operational and ICT continuity frameworks.
- Information sharing: Promote collaboration between institutions and third parties, sharing critical data to strengthen collective resilience.
Objectives of DORA

- Enhance cyber resilience: Strengthen the ability of financial entities to withstand cyber threats and ICT disruptions.
- Ensure service continuity: Maintain the availability of critical financial services, even during disruptions or crises.
- Mitigate systemic risk: Prevent the cascading effects of ICT failures from destabilizing the broader financial ecosystem.
- Foster collaboration: Encourage cooperation between financial entities, third-party service providers, and regulators to create a secure and resilient financial environment.
Core principles of DORA
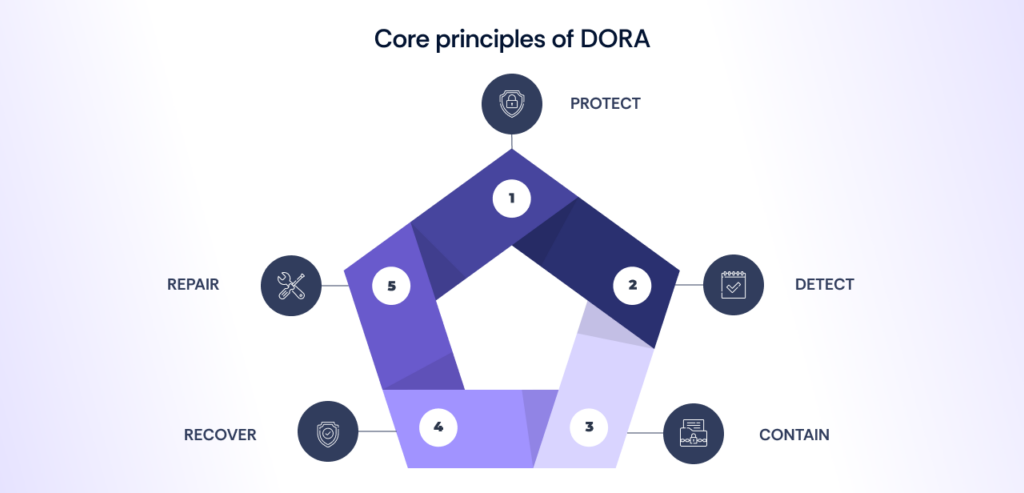
- Protect: Secure ICT systems through encryption, access controls, and awareness training to safeguard sensitive data.
- Detect: Implement tools and systems for real-time monitoring to detect and alert for cybersecurity incidents or system disruptions.
- Contain: Develop procedures to contain incidents and minimize impact, such as isolating systems and deactivating compromised accounts.
- Recover: Ensure rapid recovery with disaster recovery plans, data backups, and clear recovery protocols.
- Repair: Strengthen systems post-incident by addressing vulnerabilities through patches, security assessments, and remediation actions.
DORA timeline and implementation
The EU DORA compliance journey began on January 17, 2023, marking the start of a two-year implementation period for affected entities to align with DORA’s regulatory requirements.
Implementation period
During this period, organizations must assess their current operational frameworks, identify gaps in resilience, and develop strategies to address them. It’s also a key time to establish compliance mechanisms and integrate them into daily operations.
Preparing for key milestones
As the January 17, 2025 deadline approaches, organizations must prioritize:
- Finalizing compliance strategies
- Conducting risk assessments
- Implementing necessary infrastructure changes
- Providing employee training
By proactively preparing for these milestones, institutions can ensure smoother compliance and minimize disruptions.
DORA compliance deadlines
Organizations must be fully compliant with DORA by January 17, 2025. Meeting this deadline is crucial for avoiding penalties and maintaining operational resilience against emerging cyber threats.
Benefits of DORA compliance
Although compliance with DORA can be resource-intensive, its benefits are substantial:
- Enhanced operational resilience: DORA helps financial institutions identify vulnerabilities and prepare for potential disruptions, ensuring they can continue to provide services during crises.
- Improved security: DORA’s emphasis on cybersecurity strengthens an institution’s defenses against cyberattacks, safeguarding sensitive customer data and financial systems.
- Regulatory alignment: By complying with DORA, institutions reduce the risk of regulatory fines and penalties and ensure alignment with EU regulations.
- Customer trust: Financial institutions that demonstrate a commitment to operational resilience enhance their reputation and build stronger relationships with customers, who increasingly prioritize security.
Consequences of non-compliance with DORA

1. Penalties
Non-compliance with DORA can lead to fines, sanctions, or legal action, depending on the severity of the violation. Penalties can be substantial, with financial institutions facing significant fines, remedial measures, and potential compensation for damages.
2. Legal consequences
Failure to comply may also result in legal action, including public reprimands, withdrawal of authorization, or even criminal charges for individuals or organizations responsible. Non-compliance can damage an institution’s reputation, erode customer trust, and disrupt business operations.
3. Costs of data breaches
Data breaches are costly, with rising expenses for incident response, regulatory fines, and long-term reputational damage. Financial institutions and third-party service providers that fail to comply with DORA face escalating financial risks.
4. Financial implications
Non-compliance can lead to substantial fines, legal costs, and remediation expenses, threatening the financial stability of organizations. The financial burden of non-compliance can further disrupt operations and hinder profitability.
5. Reputational damage
Non-compliance can cause severe long-term reputational damage. Cybersecurity incidents and regulatory breaches can erode customer trust, harm brand perception, and reduce market competitiveness, ultimately impacting customer acquisition, retention, and revenue growth. Compliance with DORA is essential for safeguarding reputation and business success.
DORA’s implications
DORA impacts operational resilience across industries and there are specific implications for financial institutions.

Common challenges in achieving DORA compliance
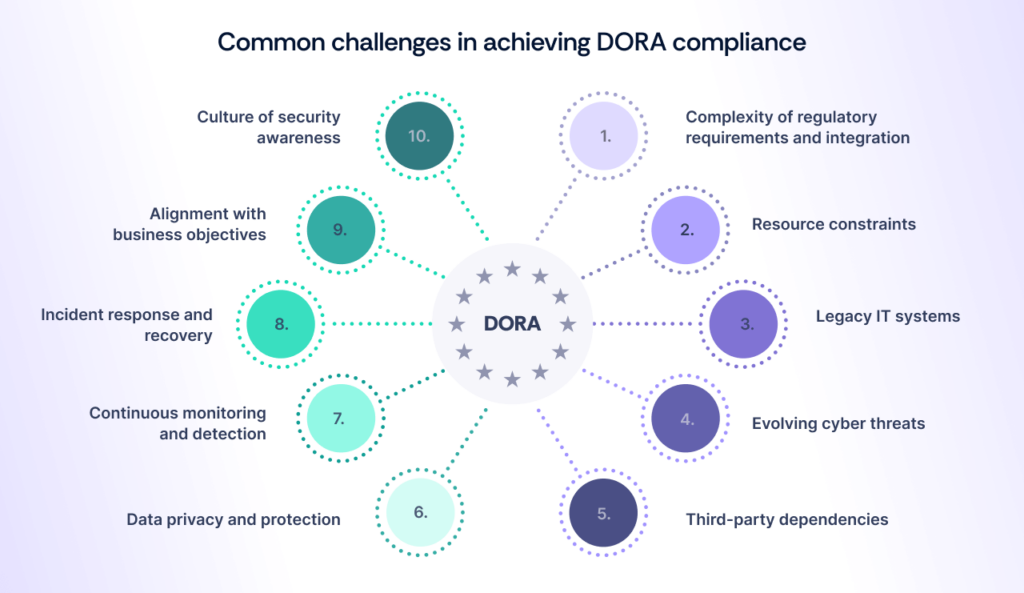
Navigating DORA compliance presents organizations with several common challenges.
- Complexity of regulatory requirements and integration: Understanding and implementing DORA’s intricate regulations can be challenging, especially for large institutions with complex IT systems and multiple third-party relationships. Integrating DORA’s requirements across governance, risk management, and cybersecurity measures requires significant time, resources, and coordination.
- Resource constraints: Limited budget, human resources, and expertise may hinder organizations’ ability to implement robust compliance measures, conduct thorough risk assessments, and invest in advanced cybersecurity solutions necessary for DORA compliance.
- Legacy IT systems: Outdated infrastructure and legacy systems may lack the necessary capabilities and security measures to meet DORA compliance standards, necessitating costly upgrades or replacements to align with regulatory requirements.
- Evolving cyber threats: The dynamic and sophisticated nature of cyber threats presents a constant challenge for organizations striving to maintain resilience against cyberattacks, requiring continuous monitoring, adaptation, and investment in cybersecurity measures.
- Third-party dependencies: Third-party Dependencies and Vendor Coordination: Organizations relying on third-party providers for critical IT and cybersecurity functions face challenges in ensuring compliance with DORA regulations. This requires robust oversight, contractual agreements, and risk management practices. Coordinating compliance across a global supply chain of vendors with varying security protocols demands ongoing monitoring and collaboration to maintain operational continuity.
- Data privacy and protection: Compliance with data privacy regulations such as GDPR adds complexity to DORA compliance efforts, requiring organizations to implement stringent data protection measures and ensure compliance with privacy requirements.
- Continuous monitoring and detection: Establishing effective mechanisms for continuous monitoring, detection, and response to cyber risks is crucial for DORA compliance but can be challenging due to the volume and sophistication of cyber threats and the need for real-time threat intelligence.
- Incident response and recovery: Developing and testing robust incident response and recovery plans is essential for DORA compliance but can be challenging due to the complexity of cyber incidents, coordination across departments, and the need for timely and effective response actions.
- Alignment with business objectives: Maintaining alignment between compliance efforts and broader business objectives can be challenging, requiring organizations to balance regulatory requirements with operational efficiency, innovation, and growth initiatives.
- Culture of security awareness: Fostering a culture of security awareness, accountability, and proactive risk management throughout the organization is crucial for DORA compliance but may face resistance or lack of buy-in from employees, requiring ongoing education and awareness initiatives.
- Organizational silos and resistance to change: Overcoming organizational silos, resistance to change, and internal politics can pose significant challenges in achieving DORA compliance, requiring strong leadership, communication, and collaboration across departments and stakeholders.

Future outlook: Adapting to DORA compliance
To stay compliant with evolving frameworks like DORA, organizations must:
- Stay informed about emerging regulations and industry trends.
- Proactively adjust compliance strategies to minimize risks and maintain alignment with regulatory changes.
- Regularly update compliance programs to enhances resilience against new threats.
Technology, including RegTech, AI, and automation, will improve compliance and streamline risk management. It will also strengthen operational resilience, helping organizations stay ahead of regulatory challenges.
Wrapping up
Organizations face various challenges and opportunities on their DORA compliance journey. As financial regulations change, staying proactive in compliance is crucial. It helps strengthen risk management and protect operations from emerging threats.
Taking proactive measures and investing in resilience can help organizations thrive in a complex business environment. This approach ensures compliance, helps adapt to changing regulations, and protects against new vulnerabilities.
For expert guidance and support to meet your DORA compliance needs, reach out to Scrut.
Frequently Asked Questions
1. What is DORA compliance, and why is it essential for organizations?
DORA, or the Digital Operational Resilience Act, is an EU financial regulation aimed at ensuring organizations can withstand, respond to, and recover from cyber threats and ICT-related disruptions. It’s crucial for organizations as it enhances operational resilience, protects sensitive data, and helps prevent costly data breaches.
2. What are the key components of DORA, and how do they impact businesses?
DORA encompasses requirements for risk management, incident reporting, ICT risk management, and operational resilience testing. These components impact businesses by necessitating robust cybersecurity measures, proactive risk management strategies, and thorough incident response protocols.
3. How does DORA compliance contribute to enhancing cyber resilience?
DORA compliance mandates that organizations implement measures to protect, detect, contain, recover, and repair their ICT capabilities. By adhering to these requirements, organizations enhance their cyber resilience, making them better equipped to withstand cyber threats and operational disruptions.
4. What steps can organizations take to ensure smooth DORA compliance implementation?
Organizations can ensure smooth DORA compliance implementation by conducting thorough risk assessments, establishing clear evaluation criteria for compliance solutions, conducting proof of concept tests, and providing comprehensive training for employees.
5. What are the potential penalties for non-compliance with DORA regulations?
Non-compliant organizations may face penalties such as public reprimands, withdrawal of authorization, remedial measures, compensation for damages, criminal charges, and administrative fines, as determined by the laws of each EU member country. It’s essential for organizations to prioritize DORA compliance to avoid these repercussions.


















