Cyber security vs. information security: A comparative insight

During the third quarter of 2022, approximately 15 million data records were exposed worldwide through data breaches (Statista). This figure had increased by 37 percent compared to the previous quarter. With the constant rise in data breaches, a business organization must ensure that its information security and cybersecurity posture is on point. But what is the difference between cybersecurity and information security? Let’s find out.
“We shouldn’t ask our customers to make a tradeoff between privacy and security. We need to offer them the best of both. Ultimately, protecting someone else’s data protects all of us.”
Tim Cook
Often used interchangeably, cybersecurity and information security are not in fact, synonymous. A business person, a CISO, or an organization’s executive should be aware of the difference between the two to form and implement effective security practices in the organization. Knowing the exact difference between the two can lead to the formation of policies that effectively reduce cyber threats. Let us start by learning what the two terms – cybersecurity and information security – mean.
What is cybersecurity?
Cybersecurity can be defined as securing an organization’s assets, including software, hardware, firmware, and network, against possible cyber attacks. These assets include the employees’ personal devices or Internet of things (IoT) devices used to access the organization’s information.

The following sections are included in cybersecurity:
1. Application security
Application security prevents the application source code and data from being attacked by cybercriminals. It is applied to every application stage, namely design, development, and deployment.
2. Digital information or data security
Although we will discuss information security in detail in the later part of this article, what you should know at this stage is that digital information security is a part of cybersecurity.
Information security involves all the steps the organization takes to prevent any unauthorized person from accessing the organization’s data. It ensures that the organization’s data is not deleted, edited, copied, downloaded, or damaged by an unauthorized person.
Data can be digital or physical. However, only the security of digital data is covered under the realm of cybersecurity.
3. Network security
Network security includes protecting data, applications, networks, infrastructure, and systems from cyber threats.
4. Disaster recovery/business continuity planning
Disaster recovery and business continuity planning refer to the plan to be followed by an organization after cybercriminals have attacked it. A robust plan can minimize downtime after the attack and puts a break on inefficient system functions.
5. Operational security
Operational security is the process of identifying sensitive data, risks, adversaries, and vulnerabilities and taking appropriate measures to secure the data from adversaries.
6. Cloud security
Cloud security includes the protection of data, applications, infrastructure, and software in a cloud environment from threat actors.
7. Critical infrastructure security
Critical infrastructure is the computer system, network, and cyber assets that are crucial to the functioning of an organization, city, country, or the safety of the general public. The security of the critical infrastructure is imperative for the common good, making it a crucial part of cybersecurity.
8. Physical security
Physical and technological worlds are merging in previously unimaginable ways, and there are times when the boundary between the two is becoming blurred. A physical security breach can lead to a full-blown cyber attack in no time. Therefore, cybersecurity is not complete without physical security.
9. End-user education
IBM reports 21% of the breaches resulted from human errors, including employee or contractor negligence. Employee training can reduce the cost of a data breach by $247,758. Despite employing state-of-the-art security measures, the organization might face cyber attacks if the end users are not trained in using clean cybersecurity practices.
Figure:
What is information security?
Information security or infosec can be defined as the processes and policies designed to secure the data of an organization. This data can be digital or physical. It can be stored on a device or in transit from one node to another. Every type of data protection is included in information security.

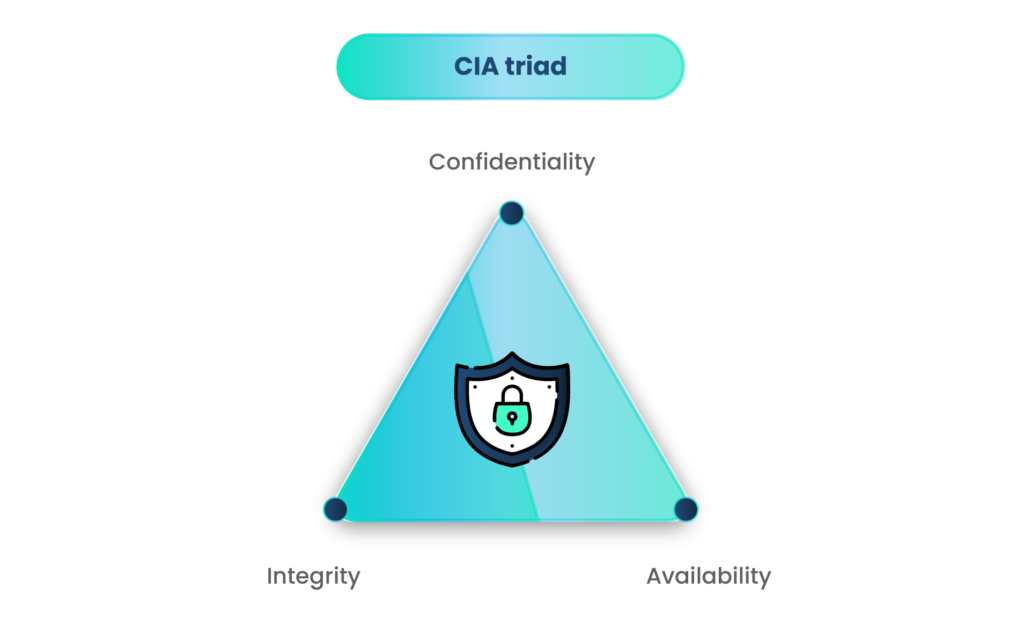
Three Principles of Infosec (CIA Triad)
Information security is based on three principles, popularly known as the CIA triad:
- Confidentiality – Confidentiality of the information ensures that no unauthorized access is ever given to an outsider or anyone working in the organization.
- Integrity – This means that the data is not compromised in any way, and no unauthorized person has viewed, changed, deleted, or downloaded the data.
- Availability – Information security ensures availability, meaning an authorized person gets access to the data whenever they need it and is fully aware that the data has not been tampered with.
Broadly, information can be classified into two categories:
- Digital information – This type of information is stored and transferred digitally. You would require a digital device to access this information. Managing the permissions for access to digital information is crucial for the cybersecurity of the organization. If an unauthorized person finds access, they can cause a cyber attack.
- Physical information – Physical or analog information is the old-school method of recording information. The handwritten notes or printed pages are called physical information. Although the amount of paper-based information is decreasing quickly, some documents are still not digitalized. Protecting the sanctity of these physical documents is crucial for the organization’s information security.
An organization must adhere to the information security requirements set by the government and non-government regulatory agencies and framework providers. Some data privacy regulations, like GDPR and CRPA, and frameworks like SOC 2. These regulations and frameworks are applicable to organizations handling or managing customer data under different circumstances, such as the location of the business, type of data collected, or inventory dealt in. Failure to comply with these data protection laws can land an organization in serious legal and financial trouble.
What is the difference between cybersecurity and information security?
If you draw a Venn diagram for cybersecurity and information security it will look like the following:
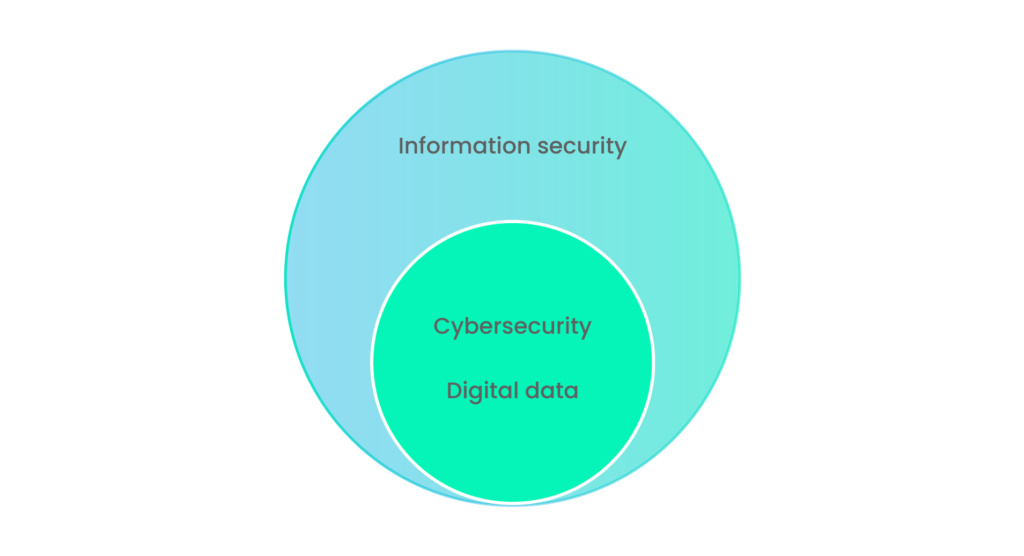
As you can see in the figure above, information security includes the protection of digital and physical data. However, the protection of digital data is covered under the cybersecurity domain. Therefore, for complete information security, an organization must take appropriate steps to secure its physical records as well.
The differences between cybersecurity and information security are discussed in the table below:

Where do cybersecurity and information security coincide?
While comparing cybersecurity and information security, we can see that cybersecurity is basically a part of information security. With the increase in digital data and the decrease in the physical formats of data, the gap between the two is reducing at a fast rate.
Only a small percentage of organizations have different cybersecurity analysts and information security analysts. In most organizations, both functions are handled by cybersecurity analysts only. However, in large organizations, assigning different people to these roles is crucial for security.
As the border between the physical and cyber world is becoming thinner, the role of cybersecurity experts becomes enhanced. A higher percentage of digital data means a higher need for cybersecurity experts.
A breach in information security might lead to cybersecurity incidents and vice versa. For example, an employee is entrusted with handling customer information on a sheet of paper as a part of their duty. Protecting this information from outsider and insider threats is the organization’s responsibility. If this data is stolen by an inside person with malicious intent and sold online, the information breach is converted into a cybersecurity incident.
Ultimately, the purpose of either cybersecurity or information security is to protect the organization’s data. Therefore, the goal between the two is the same CIA triad we saw earlier – confidentiality, integrity, and accessibility.
To sum up
Cybersecurity includes all the processes and procedures for securing all your assets from cyber threats. On the other hand, information security is protecting information, whether physical or digital, from unauthorized access. We saw what the distinctive features of cybersecurity and information security are. Also, the difference and similarities between the two types of security areas. Although both types of security are different, both are crucial for every organization.
Scrut can be a trustworthy partner in compliance, which is a massive part of information security. If you want to know more about how Scrut can help your organization’s cybersecurity, you can contact our experts.
FAQ
1. What is the difference between a cyber threat and a cyber attack?
A known or unknown flow in the organization’s hardware, software, or infrastructure is called a vulnerability. A cyber threat is a potential act that is based on the exploitation of the vulnerability in an organization’s online networks resulting in unwanted changes in computer systems.
A cyber attack is when a cyber criminal launches a series of steps to steal, alter, delete, or disable the data system of the organization.
2. Is data security and information security the same?
No. Data security is just another way of saying information security.
3. Is cybersecurity a subset of information security?
No. Cybersecurity and information security are two areas with a common ground covered between them. However, both have more sections covered under them except the said common ground.


















