ZenGRC vs RSA Archer Vs Scrut

ZenGRC is a GRC software that assists businesses with risk and compliance management. The software automates information security programs and facilitates compliance with several standards like SOC 2, ISO 27001, GDPR, and HIPAA. On the other hand, RSA Archer GRC assists businesses in managing policies, controls, risks, assessments, and defects across their entire organization. It assists organizations in remaining compliant with industry compliance laws such as HIPAA, SOC 2, GDPR, etc.
Scrut smartGRC is a single platform for compliance-related tasks. With the library of 50+ policies, users can start building compliance program in minutes. It integrates across the landscape to automate evidence collection and to create, assign, and monitor compliance tasks.
Wondering which of these software is most suited to your company? Let us discuss ZenGRC, RSA Archer, and Scrut to find out.
What Is ZenGRC?
Ken Lynch started RiskOptics (formerly known as Reciprocity) in 2009 with the objective to assist businesses in achieving societal goals such as improving customer privacy or protecting the environment.
ZenGRC by Reciprocity is an enterprise-class security solution for compliance and risk management. It includes a system-of-record for compliance, risk assessment, centralized dashboards, improved workflow, and unified control management. In addition to automating and simplifying compliance and risk management, ZenGRC tackles critical obstacles at scale and can be adapted to match your company’s specific needs. The platform provides an overview of all the components of your compliance and risk programs, such as objectives, assets, controls, and history.
With a unified, real-time view of risk and compliance that is framed around your business priorities, you will have the contextual insight needed to communicate the impact to key stakeholders and make strategic, risk-informed decisions to protect your organization as well as earn the trust of your customers, partners, and employees.
ZenGRC generates real-time risk scores that are dynamically updated to reflect risk changes. The platform communicates the financial impact of risk, the amount mitigated, and the remaining risk exposure. Furthermore, users can take proactive steps to minimize risk to acceptable levels by prioritizing essential risks. It reduces audit fatigue by reusing controls and evidence across frameworks and continuously monitoring control efficacy to guarantee the organization is always audit-ready.
Users can reuse controls and evidence across frameworks and interface with the systems on which their firm relies. With connectors to cloud providers, code repositories, HR and CRM systems, and other systems, they can avoid manual work, reduce audit fatigue, and constantly be on top of the compliance posture and audit-ready.
ZenGRC offers a free trial. The pricing details are as follows:
- For a start-up, there is a monthly fee of $2500.
- For professionals, the monthly fee is $3500.
- For an enterprise, the monthly fee is $6000.
What Is RSA Archer?
RSA Archer Insight is a set of enterprise-wide risk quantification tools designed to provide risk and business leaders with a comprehensive perspective of company risks to improve resilience and ensure that the strategic goals are met. The platform offers company leaders a consolidated view of hazards, allowing them to safeguard their businesses against disruption and handle risks associated with new opportunities.
The tool allows users to create, maintain, and distribute company and regulatory policies, standards, and procedures in a single governance system of record. It eliminates manual, non-scalable compliance activities by providing a uniform, repeatable procedure for managing new and changing requirements.
RSA Archer will help you create a scalable, adaptable governance framework to manage IT and security policies and guarantee compliance obligations are met. Archer IT & Security Policy Program Management facilitates the documentation of policies and standards, as well as the assignment of ownership and the mapping of policies to important business sectors and objectives. Users can obtain visibility into critical risks and underperforming controls through aggregated data and analytics and access to information, resources, and outcomes from risk and compliance teams.
A GRC software, Scrut, is a better option for growing business. Scrut is a global service provider that does not limit its services to organizations from a particular country. With the platform, organizations can build a robust information security system and comply with the standards most applicable to their business needs. Here’s a quick overview of Scrut.
Scrut – A Better Option
Now, let’s discuss our platform, Scrut.

Scrut smartGRC includes pre-built policies that are aligned with popular security and privacy frameworks. Users can start constructing their compliance program in minutes with a library of 50+ policies established and vetted by in-house infosec specialists.
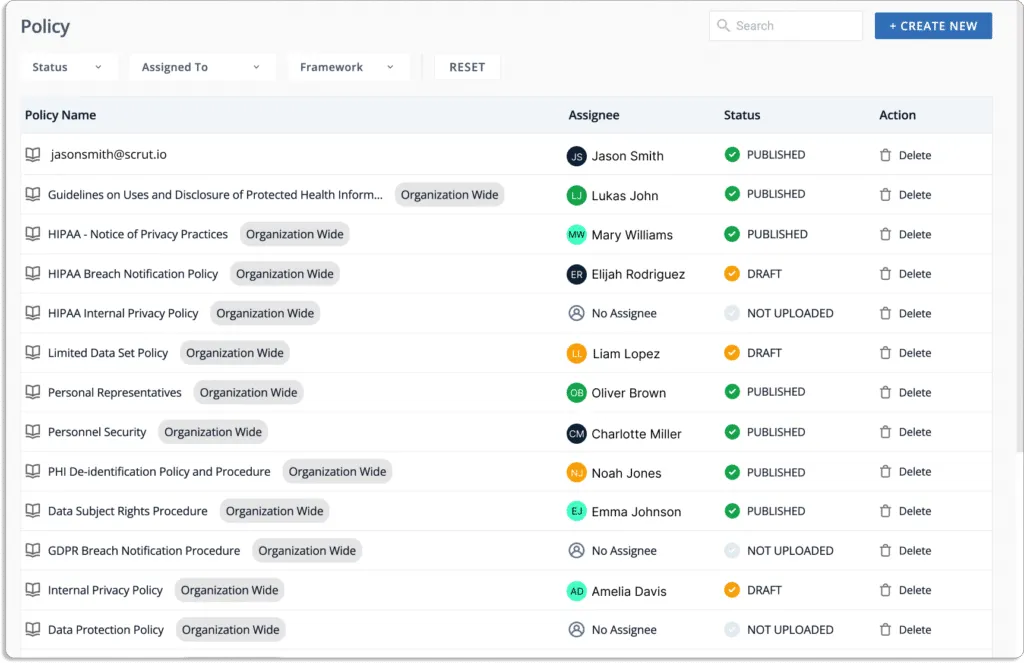
These policies are mapped to different compliance frameworks for your understanding.
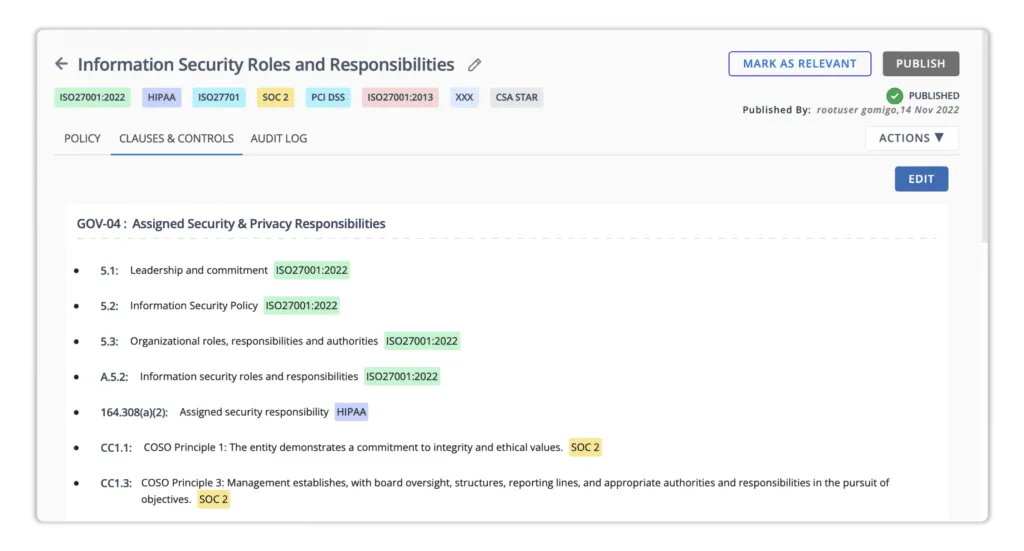
The platform informs users about the overall status of the GRC program, as shown in the screenshot below.
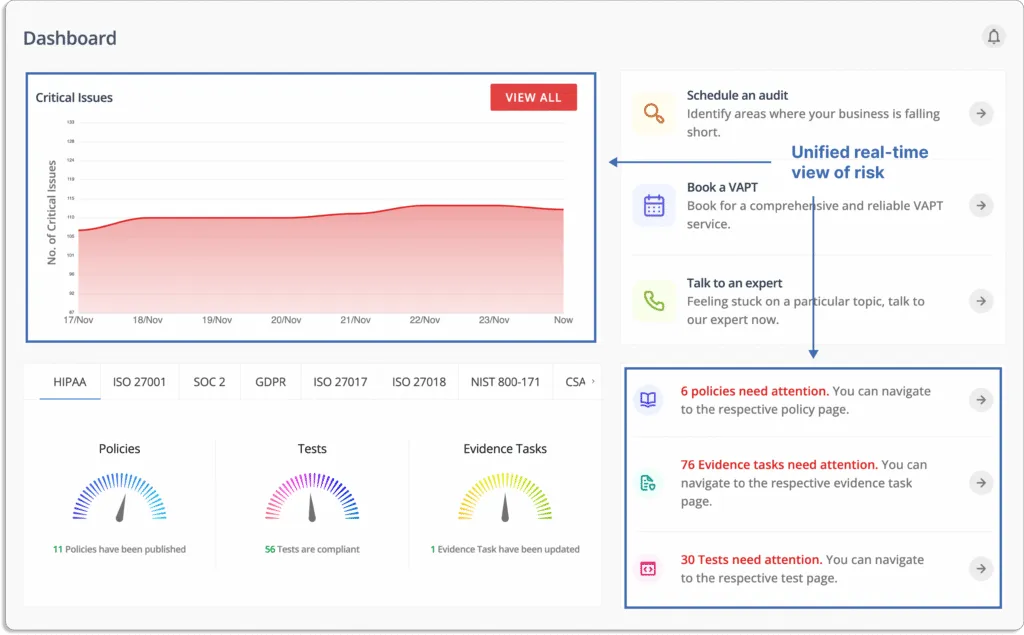
Users can obtain a unified, real-time view of risk and compliance with seamless integrations throughout the application landscape. The tool delivers the contextual data needed to make strategic decisions that keeps organization secure and earn the trust of customers, partners, and workers.
Let’s discuss in detail why Scrut platform is a better option.
Scrut Cloud Security – Scrut offers continuous cloud security monitoring to assist users in remaining compliant and proactively securing their data. The platform automatically compares your cloud configurations to 200+ cloud control across CIS benchmarks to ensure a strong information security posture.
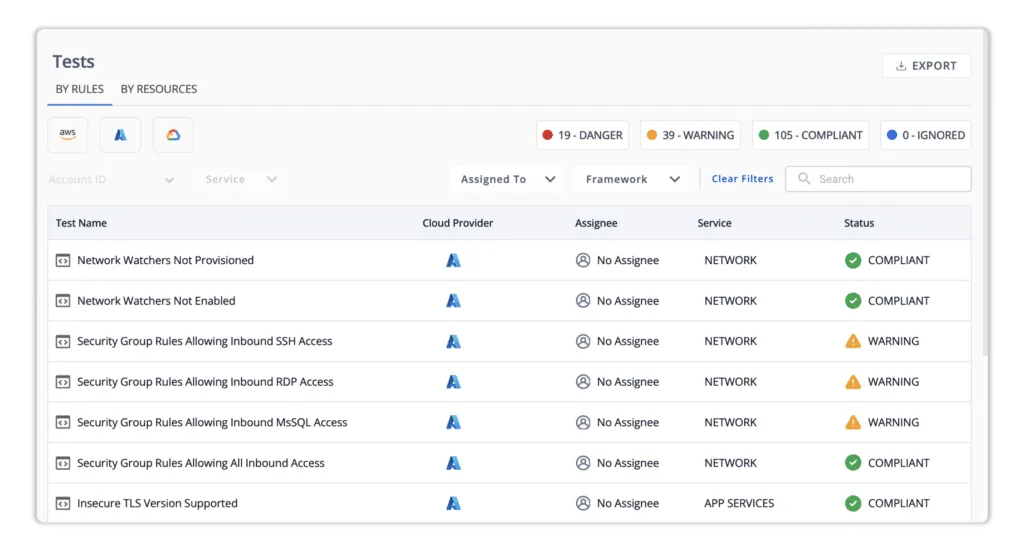
It ensures full-stack security for all cloud-native deployments, including virtual machines (VMs), and containers. The platform keeps track of your cloud misconfigurations via centralized dashboards. It gives automated classification for danger, warning, and safe configurations to keep users up-to-date on vulnerabilities.
- Danger – The most serious issue.
- Warning – After completing the issues indicated as dangerous, you can go on to these.
- Low – These threats should be addressed last.
- Ignored – You can choose to ignore.
- Compliant – Everything is fine if you are compliant.
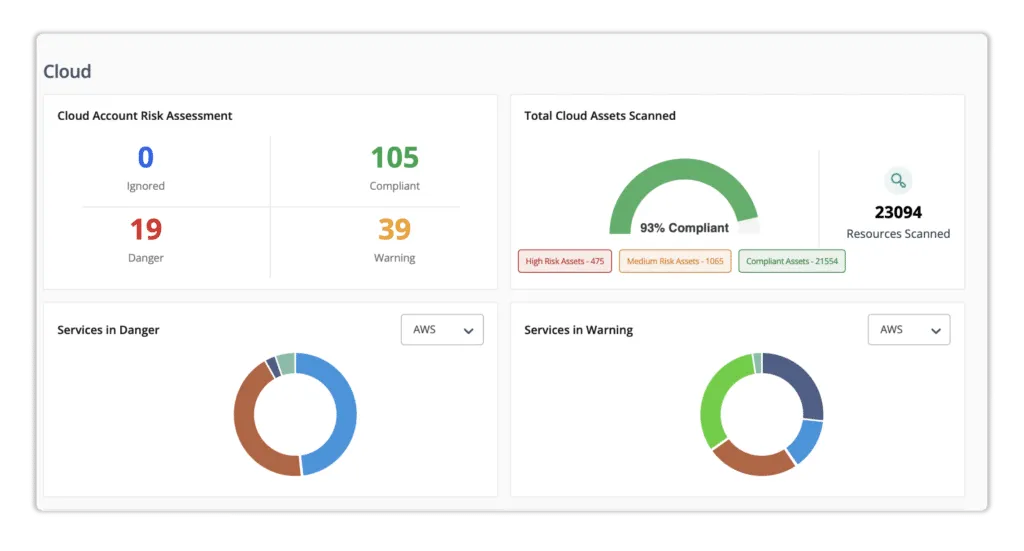
Scrut Cloud Security ensures that your public cloud accounts are always compliant. When misconfigurations occur, it sends you alerts with actionable recommendations for correcting them.
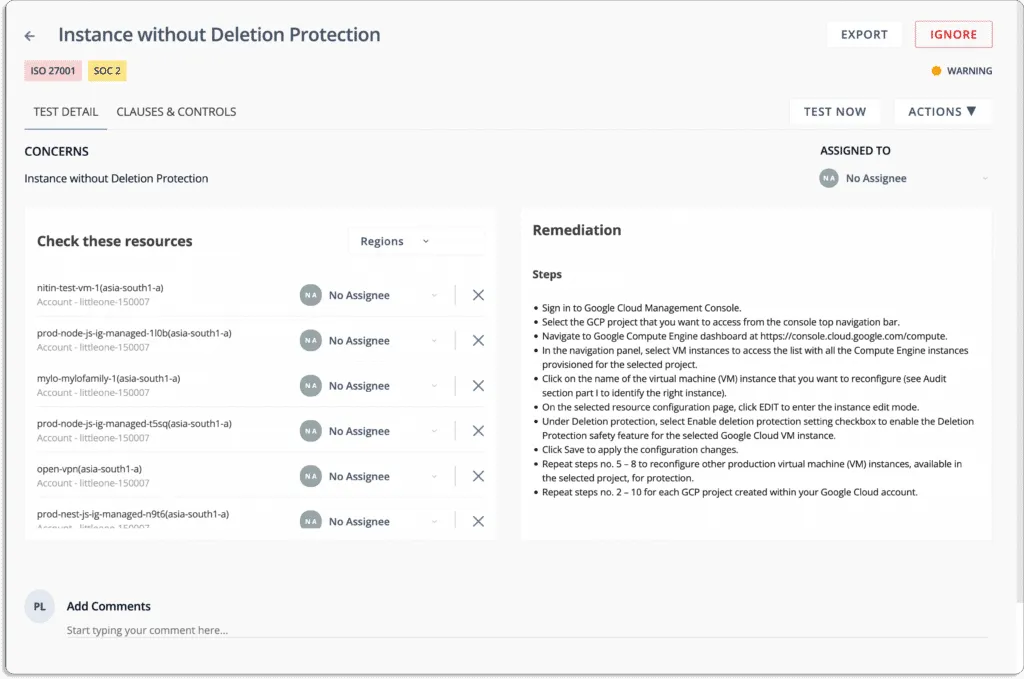
Scrut Risk Management – Scrut Risk Management gives actionable insights into your business operations to detect, assess, and treat IT and cyber threats. The platform scans your ecosystem for risks across the code base, infrastructure, applications, vendors, employees, and access to automate risk identification. It enables users to explore through a pre-built library of controls to identify company risks. Users can identify high-risk areas by integrating data with built-in industry-standard scoring techniques and expert-recommended rankings. The software automatically maps your risks to various controls across standards such as ISO 27001, SOC 2, GDPR, and HIPAA.
Scrut’s risk management will assist users in building the risk register, as shown in the screenshot below.
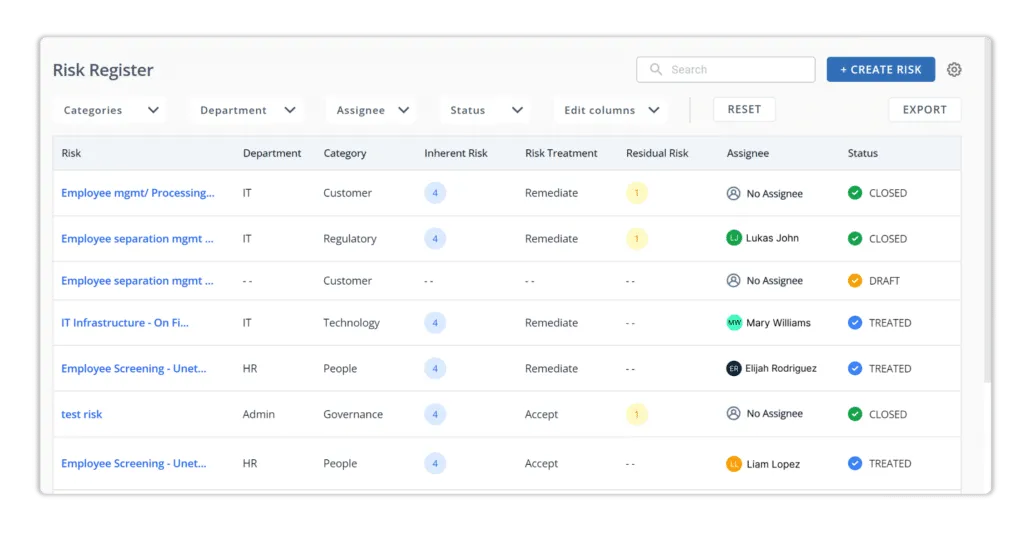
Users can start risk assessment in a few minutes instead of spending hours in developing and mapping risks, threats, controls, etc.
Consider the following example of change management risk.
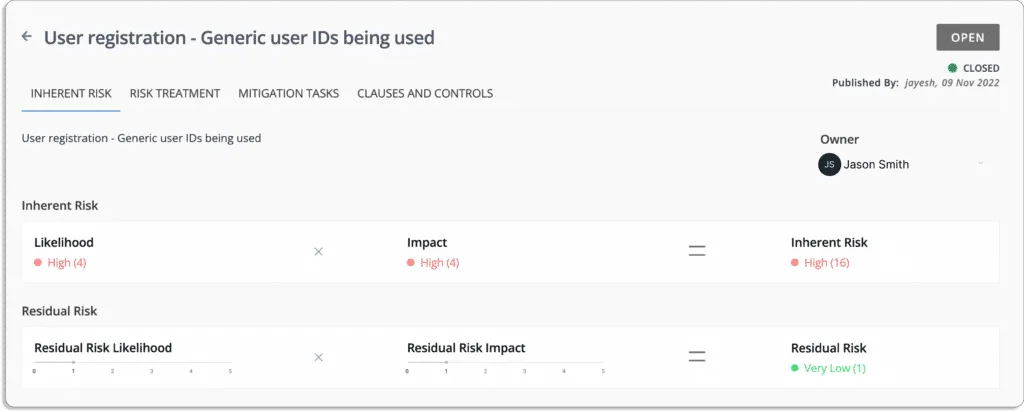
Likelihood = 5 and Impact = 4
Thus, the inherent risk associated with this event = 20
Risk = Likelihood * Impact = 5 * 4 = 20
The final score lies between 0 & 25, as shown in the table below.
With Scrut, risk can be treated in four ways: remediation, mitigation, transference, and acceptance.
- Risk remediation is the process of eliminating a risk.
- Risk mitigation is the process of reducing the risk’s impact or likelihood.
- Risk transfer involves transferring the risk to another party.
- Risk acceptance involves accepting the risk.
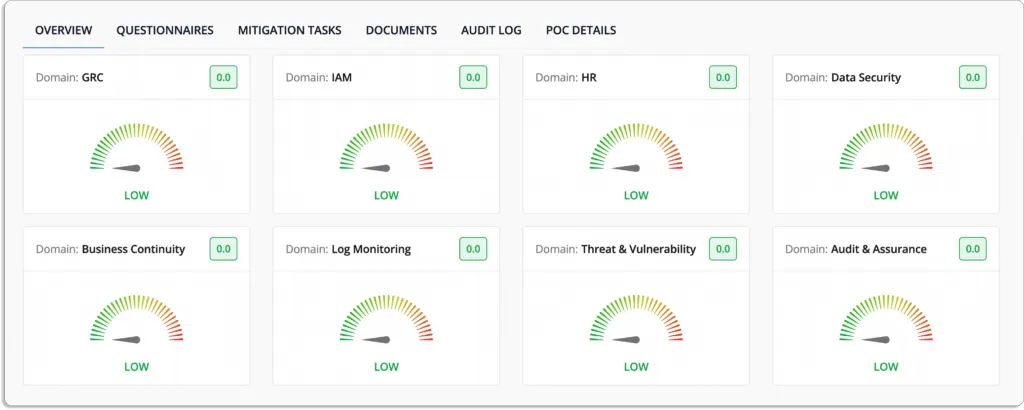
Scrut divides risk into seven categories: governance, people, customers, regulatory, resilience, technology, and vendor management. The platform automatically maps these risks against various compliance frameworks and controls, as demonstrated in the screenshot below.

Security Awareness Training For Employees – Scrut automates employee’s security awareness training with pre-built courses. It provides up-to-date data on the general status of the training programs, as shown in the screenshot below.

As an administrator, users are continually aware of the overall features of their employees’ training programs. They can connect HRM or identity provider to Scrut to import all employee data. It also allows users to generate alerts, set reminders, and send personalized messages to staff for them to complete the training.
Vendor Risk Management – The tool assists users in assessing, monitoring, and managing risks linked with vendors. With Scrut, users can gain insight into their providers’ security posture.
This enables users to determine whether a provider meets their compliance requirements or not. It streamlines your vendor compliance check with security questions. Users can construct custom questionnaire or can use pre-built questions. Furthermore, users can also invite vendors to the tool to complete the security questionnaires.

Automate Evidence Collection – The platform interacts with over 70 tools (AWS, GCP, Okta, Datadog, JAMF, GitLab, and others). It allows users to automate over 70% of evidence-collection activities while reducing manual work. Scrut keeps all evidence-related tasks in one location, allowing the auditor to go through them easily. This also reduces the need to manage many sheets or documents for evidence. The tool collects reports and evidence using pre-built cloud-based connectors across your cloud, HRMS, DevOps, and other systems.

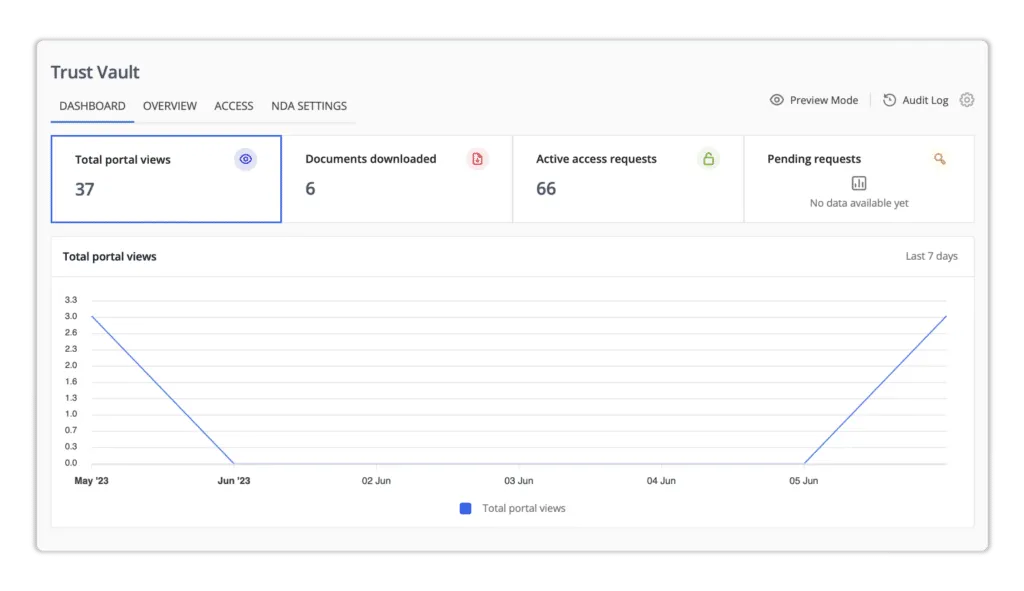
Scrut’s Trust Vault – With Scrut’s trust vault, users can demonstrate security and compliance posture in real time to partners, customers, and others.
The Trust Vault lets users publicly and transparently demonstrate their security and compliance posture. Users can create a security page on their website that is tailored to the company’s identity. It automates demands for security and compliance practices through the public display of information security-related certifications, reports, and attestations, as well as gated NDA-backed access to in-depth reports. Furthermore, it helps to demonstrate your daily compliance management and security actions to internal and external stakeholders.
The Trust Vault page is simple to add to your website and can be customized to fit your brand’s personality. Users can change their company description, add colors, logo, and favicon, select which controls to emphasize and upload relevant documents to share with their customers. Scrut GRC solution, once enabled, automatically pulls all controls, records, and sub-processors in a real-time.
Comparison Table
The following are the 3 parameters we have used to compare ZenGRC, RSA Archer, and Scrut:
Scrut allows efficient collaboration with your auditors. You and your auditor can communicate directly through the platform, avoiding unnecessary delays by providing the auditor access to your account. Users have complete control when it comes to granting access to essential parties. The auditor can approach the platform and go through each control individually. They have access to policies, exams, and proof. Collaborating with your auditors and performing audits is easier when rules, processes, controls, and evidence are all stored in one location. Click here to book Scrut demo.



















