Wiz Alternatives

Wiz is a cloud security posture management (CSPM) tool that connects to your cloud environment and provides complete visibility into critical misconfigurations, allowing your teams to improve cloud security posture.
Though it is a helpful tool, other CSPM tools are available that will better meet your requirements. In this article, we will cover eight alternatives to Wiz.
Using Wiz, you can visualize all layers of your cloud environment without needing agents, so you don’t miss anything in your cloud environment. Through APIs, the platform connects to AWS, Azure, GCP, VMware vSphere, OCI, Alibaba Cloud, Red Hat OpenShift, and Kubernetes across virtual machines, containers, serverless functions, and data stores such as public buckets, data volumes, and databases.
Let’s discuss the key features of Wiz.
Key features
- The tool continuously prioritizes critical risks based on a deep cloud analysis of misconfigurations, secrets, vulnerabilities, malware, sensitive data, and identities to create a single prioritized risk view for your cloud.
- With the graph-based network and identity engine, Wiz can prioritize network and identity misconfigurations by focusing on resources it has verified are exposed.
- Your teams can easily identify which misconfigurations can lead to lateral movement paths that harm high-value assets like admin identities.
- The Wiz Security Graph provides contextual insights into toxic combinations of real risk and attack paths in your cloud, allowing you to reduce your attack surface. You can prioritize misconfigurations based on operational, business, cloud, and data context.
- It automatically evaluates over 1,400 configuration rules, unified across runtime and IaC.
Drawbacks
The drawbacks of the Wiz platform are listed below:
- The re-assess functionality is limited to a few daily runs and does not always work.
- The platform does not support the custom report templates feature.
- The status of container discoveries is not automatically updated to resolved.
- Kubernetes integration is difficult to implement within CI/CD.
- There is a lack of support for on-premises platforms and services.
8 Alternatives to Wiz
Let’s discuss eight alternatives to Wiz, starting with our platform, Scrut.
1. Scrut Automation
Scrut Cloud Security is more than a traditional cloud security posture management tool. It scans and monitors misconfigurations in your public cloud accounts, including AWS, Azure, and Google Cloud Platform. The platform automatically compares your cloud configurations to 200+ cloud control across CIS benchmarks to ensure a strong information security posture.
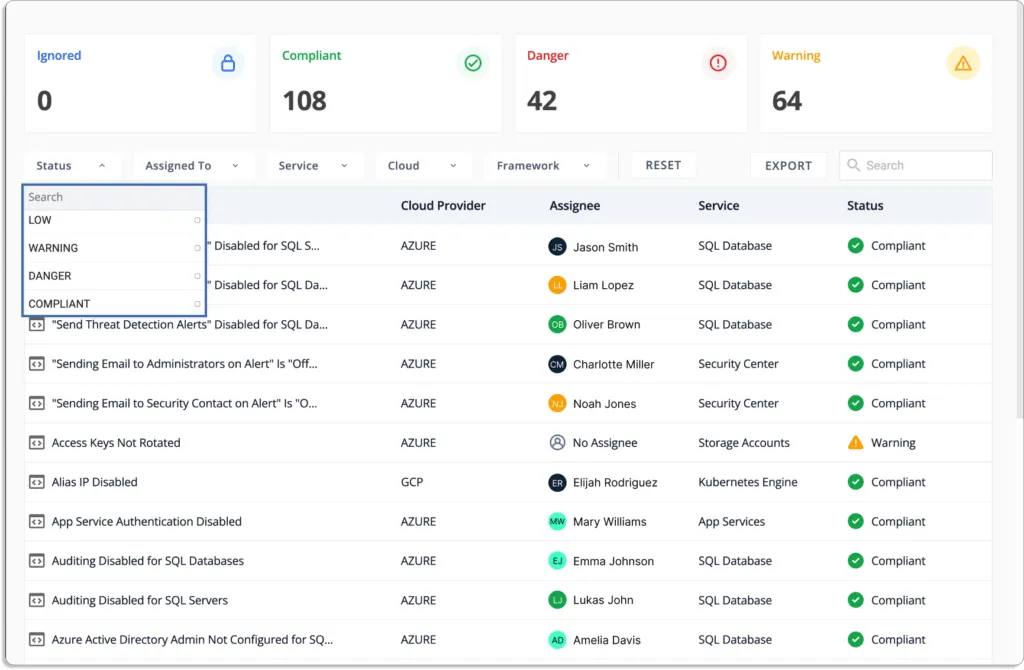
Scrut provides status information for all cloud resources, and if any cloud resource fails to meet your security standards, you will see one of the following statuses:
- Danger – The most critical issues that must be addressed immediately.
- Warning – After dealing with the “danger” issues, you can proceed to these.
- Low – These are low-level risks that can be addressed later.
- Ignored – Everything is fine as long as you are compliant.
Pros
- It ensures that your public cloud accounts are always secure and compliant. Scrut sends you alerts with actionable recommendations for correcting misconfigurations.
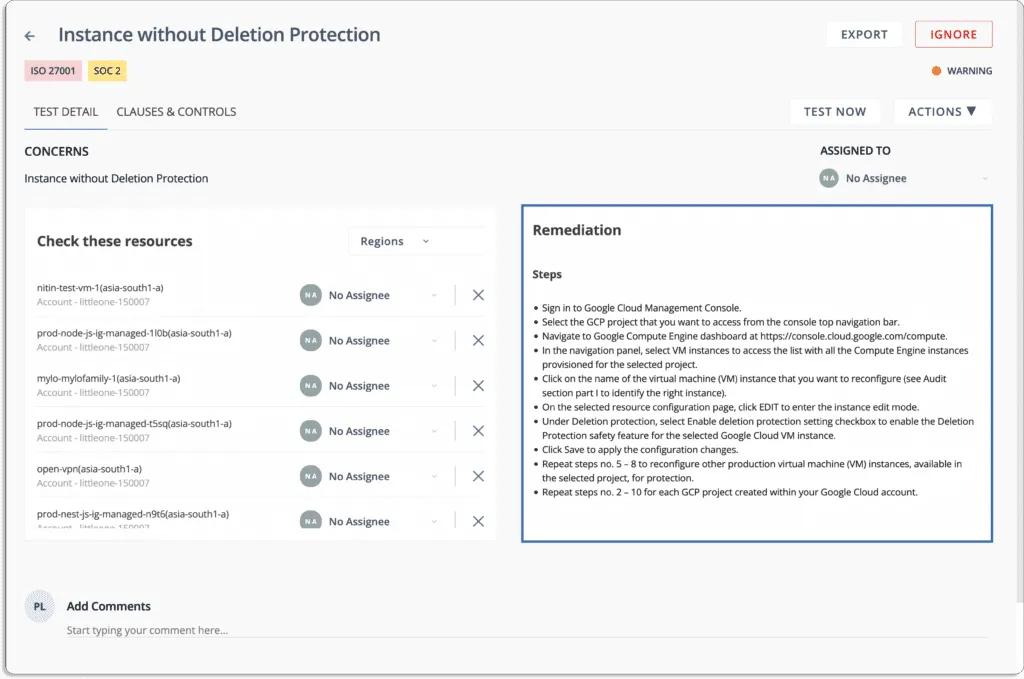
You can also assign tasks to team members to fix misconfigurations, as shown in the screenshot below:
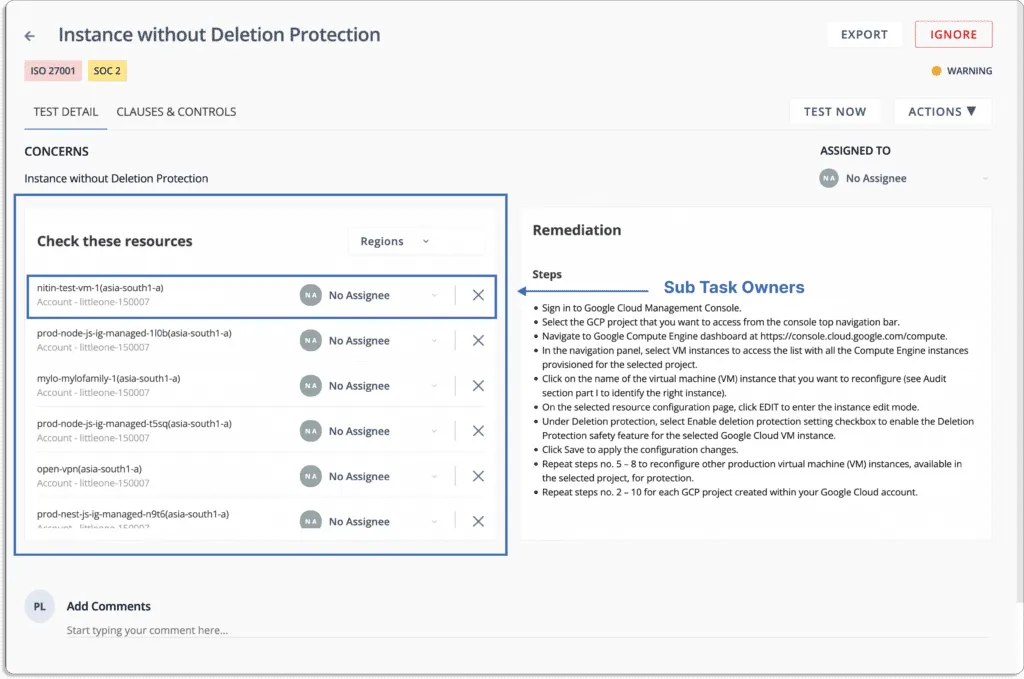
- Scrut Cloud Security enables you to implement best-practice security policies consistently across your hybrid and multi-cloud infrastructure to establish full-stack security for all your cloud-native deployments, including virtual machines (VMs), containers, and serverless.
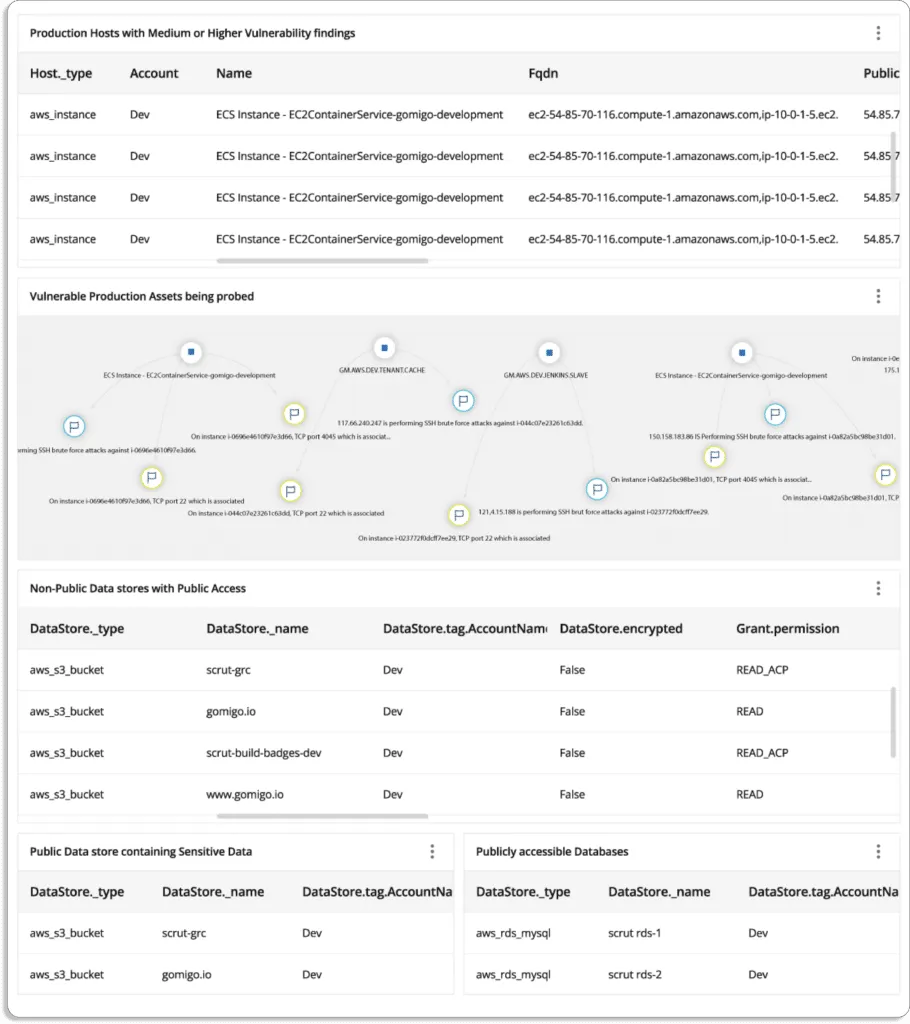
- The platform provides the visibility needed to understand your information security activities’ status, efficacy, and impact on your compliance posture. It offers a centralized repository for all information security tasks and artefacts, allowing you to close compliance gaps in real-time and remain compliant 24*7.
- The Scrut platform is compatible with multi-cloud and multi-account cloud environments. In less than 10 minutes, you can connect your entire cloud infrastructure, including AWS, Azure, GCP, and others, to the Scrut platform.
Customer Rating
- G2- 5/5
2. JupiterOne
JupiterOne unifies and standardizes asset data across your complex multi-cloud environments. The platform collects identity, code, security, endpoint, infrastructure, and ephemeral asset data and maps their relationships to create a complete picture of your digital environment. It provides comprehensive coverage for all of your cloud entities. The tool connects the dots between assets, users, endpoints, code repositories, and more to give your teams a complete picture of their environments. It creates and organizes resource entries automatically in order to continuously assess, audit, and evaluate the configurations of your cloud resources.
Pros
- This platform allows users to easily incorporate evidence for SOC, HIPAA, GDPR, and other compliance assessments.
- The tool provides inventory assets and configurations using GraphQL.
Cons
- There is a steep learning curve to understand the tools’ overall potential.
Customer Rating
- G2- 5/5
3. Lacework
Lacework uses a single platform for all AWS, Azure, Google Cloud, and Kubernetes configurations to provide a consolidated view of your cloud provider compliance. The platform discovers, monitors, and inventories all assets in your cloud environment. It records daily inventory in order to understand changes over time, even if assets are no longer available. The tool evaluates your security posture and compliance with hundreds of pre-built policies for standards such as PCI, HIPAA, NIST, ISO 27001, SOC 2, and others. Furthermore, it monitors and detects misconfigurations and suspicious cloud activity automatically.
Pros
- It alerts security teams in real-time by utilizing machine learning to identify potential security threats.
- Lacework offers a variety of security capabilities on a single platform, including threat detection, vulnerability management, compliance monitoring, and incident response.
Cons
- Because Lacework does not support two-way integration, it is difficult to synchronize solved issues in Jira.
Customer Rating
- G2- 4.5/5
4. Aquasec
Aqua Cloud Security Posture Management (CSPM) detects and resolves configuration issues in AWS, Azure, Google Cloud, and other cloud accounts. The tool discovers your cloud resources and maps out your multi-cloud environment using 100% agentless technology that rapidly scans all of your cloud workloads and begins delivering results in minutes. It uses a prioritized list of risk-based insights to solve critical issues. Aqua CSPM audits your cloud accounts continuously against hundreds of configuration settings and compliance best practices, enabling unified multi-cloud security for AWS, Azure, Google Cloud, and Oracle.
Pros
- In addition to seeing detailed results, the platform allows users to filter them according to certain criteria.
- It offers user-configurable dashboards for cloud security and image scanning.
Cons
- Aqua’s user interface have several issues, particularly with the sign-up/sign-in process, authentication, alerts, and results.
- The documentation for linking an Oracle Cloud account is out of date.
Customer Rating
- G2- 4.5/5
5. CloudGuard Management
CloudGuard allows you to seamlessly onboard new cloud accounts while managing compliance and security across AWS, Azure, Google Cloud, Alibaba Cloud, and Kubernetes. The platform automates governance across multi-cloud assets and services, such as security posture visualization and assessment, misconfiguration detection, and compliance framework enforcement. It manages compliance posture and assesses over 50 compliance frameworks and 2,400 security rulesets. Furthermore, the tool’s dashboards provide a summary and data from various Cloudguard sources, such as alerts, protected assets, and external integrations like Tenable.io and Kubernetes.
Pros
- With CloudGuard, users can keep track of every activity on their devices.
- It gives you better visibility into all of your cloud workloads and services.
Cons
- Limitation of integrating with any 3rd party systems.
- The platform does not allow access to remediation logs from the dashboard in order to detect failed remediation.
Customer Rating
- G2- 4.5/5
6. Prisma Cloud
Prisma Cloud is a Cloud Security Posture Management (CSPM) solution that simplifies compliance while reducing the complexity of securing multi-cloud environments. It offers comprehensive visibility across public cloud infrastructure, with continuous, automated monitoring providing insights into new and existing assets and potential threats. The platform automatically resolves policy violations in the Prisma Cloud console, such as incorrectly configured security groups. It detects dangerous security issues using machine learning and threat intelligence.
Pros
- Integration of CI/CD, IaC, Containers, and serverless functions is simple.
- Provides visibility in the multi-cloud environment.
Cons
- The UI is a little complicated because so many features are available to the end user.
- Expensive compared to other tools.
Customer Rating
- G2- 4.3/5
7. Orca Security
Orca is a cloud security posture management (CSPM) solution that monitors cloud environments for misconfigurations, policy violations, compliance risks, and cloud-native services. It prevents risks across every layer of your cloud estate, including workloads and configurations, from development to production, in a single, agentless platform and continuously monitors for active cloud attacks. The platform combines cloud workload, configuration, identity and entitlement security, container security, sensitive data discovery, and detection and response into a single platform that covers the entire SDLC.
Pros
- The platform is simple to manage.
- It provides comprehensive information on vulnerable cloud resources.
Cons
- Orca’s agentless technology, such as memory-loaded applications, provides less visibility into system activity.
- There is no customer community or advisory board.
Customer Rating
- G2- 4.7/5
8. Datadog
Datadog Cloud Security Posture Management (CSPM) checks the configuration of your cloud accounts, hosts, and containers. You can see your entire security posture context by leveraging Datadog’s Cloud Security Management, which includes continuous scanning that tracks all resources, whether ephemeral or long-lasting. The platform monitors compliance with industry benchmarks and controls such as CIS, PCI DSS, and SOC 2.
Pros
- It enables users to gather and correlate data from a variety of sources.
- The tool customizes the monitoring of the health of deployed services.
Cons
- The platform does not support automatic device detection and standard reporting.
Customer Rating
- G2- 4.3/5


















