What is CAASM? — Everything You Need to Know in 2023

Cybersecurity is not just about protecting your cyber assets, it’s way beyond that.
To achieve the highest level of cyber security, organizations must understand it in the context of cyber assets as well as attack surface management.
Nowadays, organizations get hacked because of insecure entry points such as software, code repositories, applications, cloud assets, ephemeral devices, etc.
The rapid adoption of cloud platforms, APIs, and digital transformation have indeed accelerated new product innovations, the development of new business initiatives, and enhanced experiences for customers. Not to mention the rise of remote work that improves employee productivity & satisfaction, workforce flexibility, and business continuity.
But all these benefits came with a dire cost. To maintain the security of these cyber assets, security teams are now required to use a plethora of security tools such as endpoint security tools, CSPM tools, network security tools, and IAM tools to name just a few.
Furthermore, most of these security tools only solve a specific use case, forcing security teams to juggle between all security tools, which is not an efficient way at all.
To make things worse, none of these security tools can provide complete visibility of security issues in your organization. This is because these tools are not connected or synchronized with each other, which makes it difficult for security teams to prioritize which issue to remediate or mitigate.
Thankfully, CAASM can solve these issues by not just giving you complete visibility over your cyber assets but also helping in understanding the context in terms of cybersecurity so that you can prioritize what issues to work on first.
For the uninitiated, CAASM is short for Cyber Asset Attack Surface Management. It’s an all-in-one solution that enables organizations to strengthen their existing entry points for hackers & creating a unified view of your cyber assets universe.
According to Gartner, CAASM is an emerging technology that will disrupt the cybersecurity industry in the coming years by providing organizations with continuous cyber asset visibility and eliminating vulnerability issues.In the mega guide, we have shared everything there is to know about CAASM including
- Definition
- History
- Benefits
- Use cases
- and much more…
…To help you understand its significance, and how to find the right CAASM security solution for your organization.
What is CAASM?
To fully understand CAASM, you’ll have to first understand the following:
What is Asset Management?
Asset management is generally defined as the cataloging, tracking, and monitoring of all assets (i.e. hardware, software, etc.) used by an organization and its employees. It helps to make sure all assets are deployed, maintained, upgraded, accounted for, and destroyed when necessary.

Asset management is critical for numerous reasons as it helps to improve asset utilization, boost employee productivity, and enhance overall IT infrastructure security.
What is the Problem with Traditional Asset Management?
Traditional asset management strategies have become outdated & are no longer effective for most organizations today because of distributed workforces, cloud data storage, and modern IT strategies.
This means that sensitive data storage is no longer confined to the four walls of an organization, which has resulted in a limitless attack surface. And without complete attack surface visibility, organizations are left with countless blind spots & more vulnerable to increasing cyber threats.
The crux of the matter is that asset management has changed. Today, for organizations to protect their assets & data completely, they must understand the importance of cyber asset attack surface management (CAASM). But even before that, they need to understand what is a cyber asset & cyber asset attack surface first.
What is a Cyber Asset?
A cyber asset is basically a potential entry point for hackers or cybercriminals into your organization’s IT infrastructure which is often referred to as an attack surface.

Depending on your organization, these cyber assets can include software, SaaS applications, mobile & IoT devices, code repositories, websites, operating systems, web servers, IAM policies, data centers, and all sorts of hardware equipment.
Generally, all cyber assets can be classified into one of the following three categories:
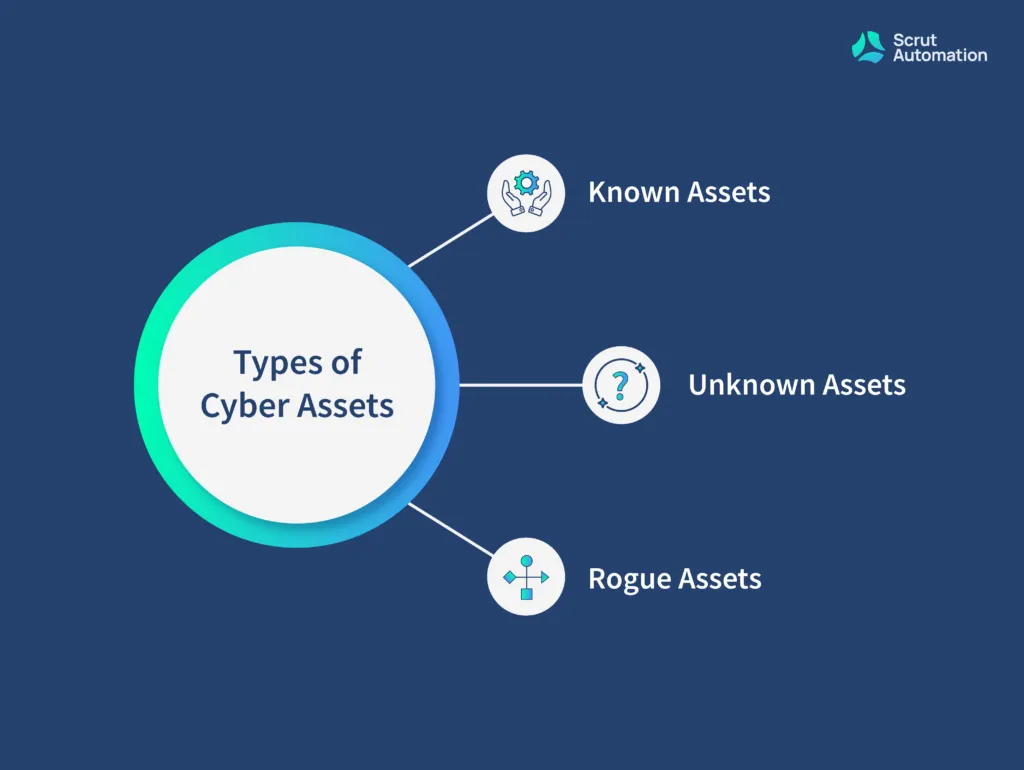
- Known Assets — Known assets are those cyber assets that are already visible to & managed by your security team. These types of assets mostly include websites, web servers, and all the dependent assets running on them.
- Unknown Assets — Unknown assets are those cyber assets that are not visible to your security team and often introduce flaws into your attack surface. Some examples of unknown assets include shadow or abandoned IT infrastructure that was developed without informing your security team. It is nearly impossible to capture details of unknown assets without proper systems, processes, and tools.
- Rogue Assets —Rogue assets mostly include malicious malware of infrastructure created by hackers or cybercriminals for their own benefit. URL hijacking, mirror websites, and mobile apps that impersonate your cyber assets are called rogue assets.
Additionally, risks to your cyber assets are not limited to just your internal sources. They can arise from an external source as well (i.e. cyber assets of your vendors, partners, etc.).
Equifax, a credit monitoring company, is a famous example of this.
In 2017, a vendor breach costed Equifax around $1.38 billion. The hackers discovered a vulnerability in Apache Struts and managed to gain access to sensitive data of approximately 147 million Equifax customers such as name, social security number, address, date of birth, driver’s license, and more.
The point is, traditional cybersecurity solutions can no longer protect your organization from cyber-attacks.What organizations truly need is an emerging technology like CAASM that is not limited to devices, servers, applications, users, and endpoints, but can cover the entire cyber asset attack surface.
What is a Cyber Asset Attack Surface?
In layman’s terms, a cyber asset attack surface refers to all entry points that can serve as potential attack vectors to gain access inside an organization’s system for the purpose of launching a cyber attack or stealing information.

Lately, the cyber asset attack surface has grown exponentially post-COVID-19 Pandemic that accelerated remote working, mobility, digitalization, and cloud computing.
This has forced organizations to now keep track of both, physical as well as digital assets along with their operational technology and Internet of Things (IoT) devices.
Unfortunately, the majority of organizations have no idea what and how many assets they have, making it impossible to protect them. However, it is now possible to not only keep track of all your cyber assets but also protect them from all kinds of cyber threats using CAASM.
What is Cyber Asset Attack Surface Management (CAASM)?
CAASM is an acronym for Cyber Asset Attack Surface Management.
As the name suggests, it is a process of understanding, managing, and protecting the expanding attack surface from potential threats & risks. In simple terms, CAASM is a technology solution that helps organizations to detect & recognize all cyber assets connected to their networks, and uncover vulnerabilities in those cyber assets that could be exploited for a cyber attack.
CAASM solutions provide complete visibility across the entire IT infrastructure, giving organizations better governance & control over their cyber assets, and information required to manage & protect the attack surface or act promptly to prevent the bleeding in case an attack occurs. But to realize the full power of CAASM, organizations must grant access to accurate & complete data of their cyber assets. Additionally, the cyber assets data must also be instantly accessible so that the security team can isolate cyber assets which pose a risk and take corrective action immediately.
A Brief History of CAASM
IT asset management (ITAM) has been around for over a decade.
The practice of IT asset management was originally born out of the need for keeping track of the software, hardware, licensing, and other IT assets of an organization.
But over the past couple of years, cybersecurity has gradually started becoming an important priority for organizations. And the traditional cyber asset management challenges that served well in the past can no longer protect the evolving cyber assets of modern organizations.
This ultimately led to the birth of CAASM for addressing the specialized cybersecurity use cases & vulnerabilities around cyber asset visibility and attack surface management.
How Does CAASM Work?
Maintaining an accurate IT asset inventory system is the foundation of setting up a cybersecurity program in every organization. But at the same time, it’s not an easy feat.
Nowadays, organization assets change more frequently than ever, with new attack surface management tools, platforms, and devices being added and retired, while stakeholders & employees also install and update software with & without approval.
All of these can disrupt cyber asset visibility and management within an organization. Additionally, it can incur countless vulnerabilities to cyberattacks.
To overcome this, most organizations are now turning to CAASM.
CAASM can help to provide complete visibility across your cyber assets, understand the context, and elevate cybersecurity in your organization.
CAASM does this by
- Maintaining an accurate cyber assets inventory
- Updating asset inventory in real-time
- Making cyber assets instantly available
- Taking both cloud & on-premises assets into account
- Sharing information about each cyber asset is being used
Why is CAASM an Essential Cybersecurity Solution?
The reason is pretty simple — the world has moved onto modern & better technology solutions.
Digital transformation, cloud adoption, and API-first architecture have nearly changed everything when it comes to building, managing, and securing an organization’s network.
Furthermore, organizations use a plethora of specialized IT infrastructure and security tools, and most of the time, they don’t even know what assets they have across teams.
CAASM can help organizations in gathering a complete picture of all cyber assets and their relationships, providing the required context to build a comprehensive cybersecurity program within the organization.
This, in turn, can be tremendously beneficial to organizations in several ways.
What are the Benefits of CAASM?
CAASM is a powerful solution to gain complete visibility across cyber assets and expedite SecOps actions.
The right CAASM security solution can help organizations to obtain detailed context along with a unified & real-time view across all cyber assets as well as attack surface management tools for composing a highly-effective cybersecurity program.
A CAASM solution does this by empowering organizations to take inventory of all internal as well as external cyber assets using API integrations, group them, and remediate vulnerability gaps & security controls continuously.
In return, organizations get to avail the following benefits of CAASM after adoption & implementation within their network.
Better Cyber Asset Hygiene & Cloud Security Posture Management
Today, most organizations have either incomplete or obsolete cyber assets inventory.
To remedy this, CAASM can create a single source of truth to gain complete visibility on all cyber assets. Plus, it can even provide helpful information about a system’s health-based patterns & emerging properties.
This, in turn, results in improved cyber asset security hygiene and posture management across your entire organization.
Bird’s Eye View into All Your Software & Hardware Assets
The definition of a cyber asset is no longer restricted to physical devices with IP addresses, it refers to all operational entities such as people, security controls, cloud data stores, code repositories, and more.
A CAASM solution can give you a bird’s eye view of all your software & hardware assets in one platform. CAASM does this by helping you discover & merge your cyber assets data across all your IT infrastructure & tools, saving your security team plenty of time and effort.
Adding Context: Understanding Relationships Between Assets
Understanding your cyber assets through their contextual relationships can be significantly helpful in building a rock-solid cybersecurity program. The best CAASM solutions not only allow organizations to track and monitor all their cyber assets but also investigate and tie all intra-asset relationships.
This, in turn, adds context to your organization’s IAM, cloud security, compliance, and vulnerability management processes.
Maintain Consistency Across Levels
The biggest benefit of having complete visibility over all your cyber assets and their contextual relationships is the ability to maintain consistency across all levels of your organization.
Advanced CAASM solutions allow organizations to create & maintain consistency in their entire asset universe and get quick answers to all queries. For example, organizations can ask what are all my cyber assets, which assets are currently in use and by whom, which SaaS tools are vulnerable and much more.
Instant Risk Detection & Response Across all Operations
The best CAASM solutions like Scrut Automation can help your security team instantly detect risks and the blast radius across your entire attack surface, accelerate investigation, and respond to them by visually exploring the IT security infrastructure for actionable context.
Automated Security Enforcement for Asset Compliance Monitoring
As organizations scale, automation becomes an essential requirement, and the same applies to security as well.
An effective CAASM security solution can automate the discovery & management of cyber assets and enforce them to align with the necessary security compliances.
Compliance Drift Monitoring Across All Cyber Assets
Whether your organization has no cybersecurity problem, a security team distributed across departments, or a mature cybersecurity model, CAASM can help to elevate and automate the collection, analysis, and rectification of cyber asset data to bridge any compliance gaps and security issues you may have.
What are the Different Use Cases of CAASM?
Now that you know about the main benefits of CAASM, let’s look at the different use cases where CAASM would be useful.
Cloud Security
CAASM enables organizations to gain a complete understanding of their cloud security environment including your GCP, AWS, Azure cloud asset inventory, and cloud security posture.
This, in turn, can help your cybersecurity team to discover misconfigurations and allow them to continuously monitor cloud assets for any possible compliance drift.
Put it simply, CAASM can provide answers to the following cloud security-related questions:
- Are any of our organization’s cloud data stores exploitable?
- Do we have any overprivileged users or workloads?
- Can our cloud assets withstand general misconfigurations?
- Are there any assets that are internet-facing which shouldn’t?
Cyber Asset Management
On top of cloud security, CAASM provides a complete view across your entire cyber asset inventory that helps to improve the security posture as well as overall cybersecurity hygiene.
Additionally, CAASM adds cyber asset context and maps relationships among all cyber assets to take necessary actions and expedite response times.
This, in turn, helps organizations answer the following questions:
- How many assets do we have?
- What are our most important cyber assets and problems?
- Which discovery has the highest risk of serious consequences?
- What is the approximate blast radius of a compromised asset?
Vulnerability & Incident Response Context
In addition to cloud security & cyber asset management, CAASM helps to supplement incidents & vulnerabilities with the required context for preliminary assessment and response.
An effective CAASM would elevate the SecOps response times by unraveling specific & highly-critical risks, and the blast radius linked with vulnerability discovery as well as incidents.
Ultimately, CAASM helps to find answers to the below questions:
- What cyber attack instances would have the highest chances of impact & consequences of it?
- What is the precise blast radius of a compromised cyber asset?
- Which applications are currently at risk of getting compromised & where are they operating?
- How can we lower noise from scanners & emphasize the most critical vulnerabilities?
Governance Access & Identification
CAASM comes with a built-in user identity inventory that automates user access reviews and examines permission as well as entitlement-related issues.
Because of this, organizations are able to answer the following questions through CAASM:
- What are our external users?
- Who & what can access a specific service, device, and even a data store?
- Are all access rights completely revoked for the offboarded users?
- Are there any users with surplus permissions currently?
- Which users have been inactive for the past 90 days?
Compliance Testing & Evidence Collection
In any organization, automation is crucial, especially if the teams have limited time, budget, and resources.
In such situations, CAASM can help to automate testing and evidence collection for all cybersecurity policies as well as compliance frameworks such as SOC2 Security, CIS Benchmarks, HIPAA Compliance, NIST Cybersecurity, PCI DSS, and more.
Furthermore, CAASM can even help to map the relationship between all controls and frameworks.
Thanks to this, organizations can learn answers to the following questions:
- What are our cybersecurity gaps?
- Whose endpoint is not in compliance with baseline configurations & patch management?
- What is our compliance status for custom SOC2 controls?
- What is the proof that we’re compliant with a specific compliance framework?
- How are our overall compliance gaps compared to frameworks?
How is CAASM Different from CSPM & Other Similar Technologies?
Let’s face it — you cannot make a clear and well-informed decision until you have compared your desired item with its competition. And this applies to the CAASM solution as well.
So below, we have compared CAASM with its cybersecurity predecessors to help you get to the bottom with an easy-to-understand comparison.
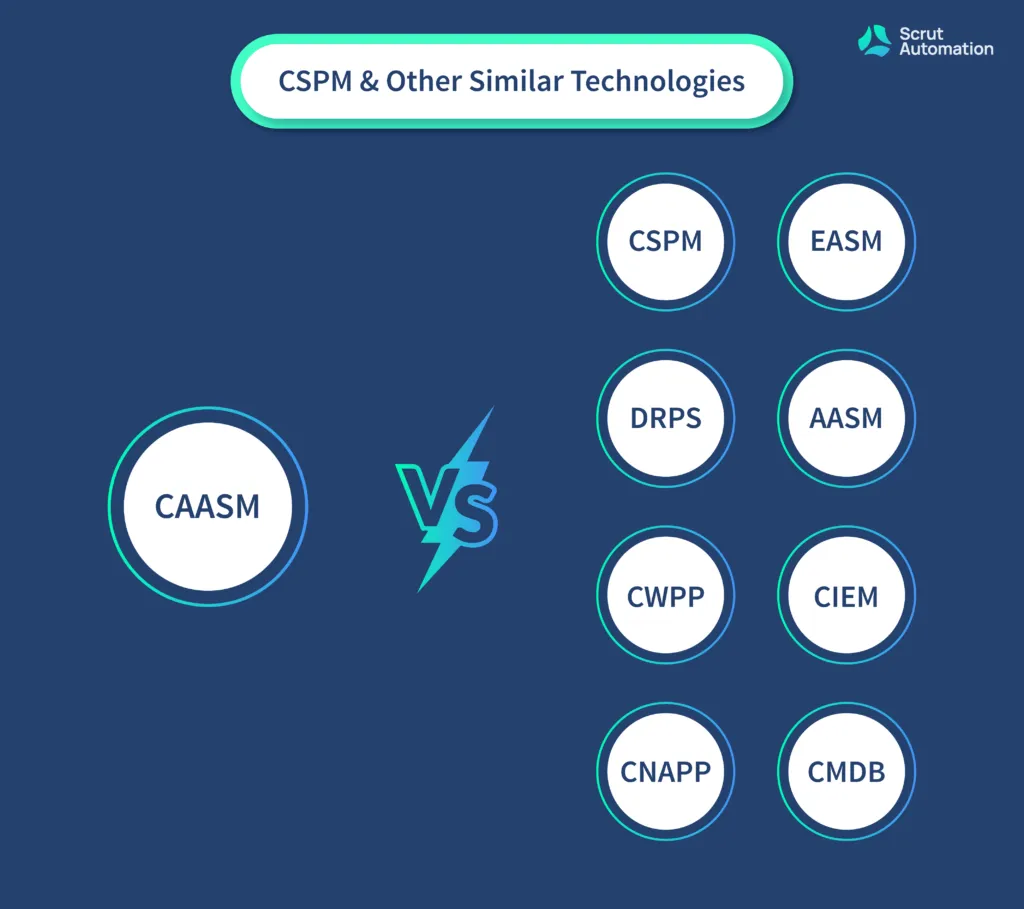
CAASM Vs CSPM
CSPM stands for Cloud Security Posture Management. It’s a collection of IT security tools that are specially designed to identify misconfigurations & compliance risks across a diverse cloud infrastructure. CSPM does this by continuously monitoring the cloud environment for discovering gaps in security policy enforcement.
Unfortunately, CSPM has not evolved to keep pace with the advancing complex requirements of cloud-native organizations. At best, CSPM can offer a common set of misconfiguration checks but without any depth, visibility, or even flexibility for monitoring rules.
In a nutshell, CSPM has extremely limited capabilities to comprehend compliance requirements with configuration baselines.
CAASM, on the other hand, can do everything CSPM does and more. Unlike CSPM, CAASM is extensible, which goes way beyond the basic cloud configuration checks, and monitors custom configurations that are critical to the unique security architecture of your organization.
Furthermore, CAASM continuously monitors the entire attack surface including private & public clouds and beyond, uncovering toxic combinations of misconfigurations and relationships that a CSPM cannot comprehend.
CAASM Vs EASM
EASM stands for External Attack Surface Management. These types of solutions are largely used for identifying unknown external threats and toxic networks. An EASM solution does this by identifying environment-based vulnerabilities for the security operations program of an organization.
However, the main problem with EASM is that it cannot define what’s exactly inside your cloud environment.
CAASM solutions, on the other hand, mirror the common EASM tooling and current external asset data by merging all data to form complete visibility across all cyber assets through API integrations.
This merged structural data gives organizations the complete context they require to boost their cybersecurity operations.
CAASM Vs DRPS
DRPS stands for Digital Risk Protection Services. It is a managed service that provides visibility into open-source assets like the dark web, deep web, and social media.
The primary purpose of DRPS is to perform risk assessments and brand protection by providing contextual information about threats, their strategy & malicious activities for threat-intelligence analysis.
However, it is not capable of providing an inventory of cyber assets managed by your organization.
Conversely, CAASM provides a comprehensive view of your entire cyber assets infrastructure. While CAASM is not the source of record, it aggregates data from other sources. This helps organizations overcome cyber asset visibility & vulnerability challenges.
CAASM Vs AASM
AASM stands for API Attack Surface Management. Unlike CAASM, AASM focuses primarily on application software, rogue API discovery, and API vulnerability management.
CAASM has much better capabilities when it comes to prioritizing all risks in order of their impact on the organization. Overall, CAASM can provide a better level of visibility, inclusivity, and context, making it a better attack surface management tool.
CAASM Vs CWPP
CWPP stands for Cloud Workload Protection Platform. As the name suggests, it provides workload-focused security protection for all kinds of workloads such as physical servers, serverless workloads, containers, and virtual machines.
The primary purpose of CWPP is to scan cloud environments for misconfigured security settings and identify which of them are violating regulatory compliance requirements and corporate security policies.
Compared to CWPP, CAASM is better poised for identifying unknown risks across the entire cloud infrastructure of an organization, continuously monitoring for compliance misconfigurations, and drift prevention for checking the cloud environment against security & compliance violations.
CAASM Vs CIEM
CIEM stands for Cloud Infrastructure and Entitlement Management. Compared to other cloud security tools, CIEM is relatively new in the market.
For the uninitiated, CIEM is a cloud-based approach to managing access and entitlements to a company’s cloud infrastructure. This includes the management of user access, permissions, and roles, as well as the management of resources such as virtual machines and storage.
CIEM helps organizations to make sure that only authorized users have access to the company’s cloud infrastructure and that resources are used in a compliant and secure manner.
While CIEM provides a cloud-based approach to managing access and entitlements to a company’s cloud infrastructure. Without CAASM, an organization may have potential vulnerabilities that it is not aware of.
In a nutshell, CAASM focuses on identifying and mitigating potential vulnerabilities, while CIEM focuses on managing access and entitlements to the company’s cloud infrastructure.
CAASM Vs CNAPP
Cyber Asset Attack Surface Management (CAASM) and Cloud-Native Application Protection Platform (CNAPP) are two different approaches to securing a company’s digital assets.
CAASM is a proactive approach to identifying and mitigating potential vulnerabilities in a company’s digital assets. This includes identifying and analyzing the attack surface of an organization’s IT infrastructure, applications, and data.
The goal is to minimize the potential for successful cyber attacks by identifying and mitigating vulnerabilities before they can be exploited.
CNAPP, on the other hand, is a cloud-native approach to protecting a company’s applications and data. This includes using a range of security technologies such as firewalls, intrusion detection systems, and encryption to secure the infrastructure and data.
CNAPP also focuses on protecting the runtime environment of cloud-native applications, including containerized and serverless architectures.
CAASM Vs CMDB
Configuration Management Database (CMDB) centralized database for managing and securing a company’s digital assets.
It stores and manages information about an organization’s IT infrastructure and the relationships between the different components.
The goal of a CMDB is to provide a clear and accurate view of the organization’s IT assets, including hardware, software, and network devices.
This information is used to support IT operations and change management processes, such as incident management, problem management, and release management.
The goal of CAASM, on the other hand, is to identify and analyze the attack surface of an organization’s IT infrastructure, applications, and data. By doing so, it minimizes the potential for successful cyber attacks by identifying and mitigating vulnerabilities before they can be exploited.
In a nutshell, CAASM is focused on identifying potential attack vectors and securing them, while CMDB is primarily used for IT operations and change management.
Although, both CAASM & CMDB have some points of intersection. For example, the information stored in CMDB can be used to identify and mitigate vulnerabilities that might exist in the IT environment using CAASM.
How can CAASM Improve the Cybersecurity of your Organization?
Adopting a CAASM security solution helps to create a knowledge base for your entire security posture and automatically analyzes complex attack surfaces.
This, in turn, improves the overall security of your organization in many different ways.
Comprehensive Visibility
Before CAASM, IT and security teams in organizations had limited options for producing an accurate, up-to-date, and complete inventory of assets.
- Excel – Exporting data into CSVs from multiple sources to create a master sheet with pivot tables.
- CMDB – Creating Configuration Management Database for storing asset data and up-to-date information.
- Scripts – Writing, updating, and maintaining scripts to pull data from tools; deconflicting and normalizing the outputs.
With the arrival of CAASM, all these methods for asset inventory management have become obsolete.
Unlike these manual options, CAASM can be connected to hundreds of security as well as management solutions that have an inventory of all your cyber assets.
Thanks to this, organizations can now form a single system of record of their entire asset infrastructure.
Identification of Critical Assets or Crown Jewels
Identifying the critical assets that need to be protected is one of the key aspects of CAASM.
There are several ways using which CAASM identifies critical assets including
- Asset Inventory – CAASM creates a comprehensive inventory of all the assets within an organization, including hardware, software, and network devices. This is usually performed via automated tools.
- Risk Assessment – Once the inventory of assets has been created, a risk assessment is performed to identify the critical assets that need to be protected. This assessment takes several factors into consideration such as the value of the asset to the organization, the potential impact of a successful attack, and the likelihood of an attack.
- Vulnerability Scanning – Vulnerability scanning tools are used to identify known vulnerabilities in the organization’s IT environment. These tools can be used to scan hardware, software, and network devices, and identify vulnerabilities that need to be addressed.
- Threat Intelligence – CAASM enables organizations to use threat intelligence feeds for identifying potential threats and the assets that are most likely to be targeted. This information is then used to prioritize the protection of critical assets.
- Network Mapping – Network mapping tools allow organizations to create a visual representation of the organization’s network infrastructure. This, in turn, helps to discover potential attack vectors and the critical assets that need to be protected.
By using a combination of these strategies, CAASM identifies the critical assets that need to be protected and prioritizes the mitigation of vulnerabilities that have the highest risk to your critical assets.
Prioritize Security Measures
Another way CAASM improves the security of an organization is by prioritizing security measures. Below are the most important practices CAASM follows to prioritize security measures.
- Compliance – CAASM makes sure that organizations are in compliance with the necessary set of regulations and standards, such as PCI-DSS, HIPAA, SOC2, etc. These regulations may require certain security measures to be implemented, and they can be used to prioritize the security measures that need to be taken.
- Business Impact – CAASM The organization’s business continuity and recovery plan can be used to prioritize the security measures that need to be implemented. The security measures that are critical to the continuity of the business are given priority.
- Resources – Since organizations have limited resources and budgets, CAASM prioritizes security measures based on the resources available, factoring in the cost-benefit ratio.
By using the above techniques, CAASM can effectively prioritize the security measures that need to be implemented for identifying vulnerabilities, mitigating the associated risks, and protecting the critical assets of an organization.
IMPORTANT NOTE — The prioritization of security measures is a continuous process that must be reviewed and updated regularly to adapt to the growing attack surface and the organization’s requirements.
Ability to Query Across All Sources
As stated earlier, a CAASM security solution can discover all your cyber assets, consolidate their data using different tools, and create a unified view of all assets. This enables organizations to query across all data sources on their cloud environment.
Furthermore, organizations can even ask questions that expand their data sources. This includes most basic questions as well as more in-depth and complex ones as below
- How many devices do we have?
- How many of our Mac devices are running a vulnerable Chrome version?
- What are the riskiest cyber assets in my environment?
- How many known and unknown cyber assets are there in my organization?
- What is the potential blast radius for my vulnerable cyber assets?
On top of this, organizations can even plan how they can respond to a security breach incident by asking relevant questions.
Fewer Manual Audits & Compliance Reporting
With a complete picture of all cyber assets combined with the ability to query how assets either comply with or deviate from policy expectations, organizations can save plenty of effort by saving queries to automatically map to regulations and satisfy the audits.
In simple terms, CAASM achieves fewer manual audits and compliance reporting by automating many of the processes involved in identifying and mitigating vulnerabilities, and by providing a centralized system for storing and managing information about the organization’s IT assets and vulnerabilities.
One way that CAASM automates many of the processes involved in identifying and mitigating vulnerabilities is through the use of automated scanning tools and vulnerability management systems. These tools are configured to scan the organization’s IT environment for vulnerabilities regularly. And the moment new vulnerabilities are discovered, it immediately alerts the appropriate teams within an organization.
Apart from this, CAASM uses automated workflows and incident management systems to coordinate the work of different teams and ensure that all vulnerabilities are addressed in a timely manner.
Additionally, this system can also be configured to automatically generate compliance reports based on the information stored in the system, which eliminates the need for manual audits and compliance reporting.
Collaboration Via Single Source
CAASM allows different teams within the organization to work together to identify and mitigate potential vulnerabilities in a coordinated and efficient manner.
To do this, it creates a single source of truth by using a centralized system or platform that stores and manages information about the organization’s IT assets and vulnerabilities. This system can be accessed by different teams within the organization, such as IT operations, security, and compliance teams, allowing them to work together to identify and mitigate potential vulnerabilities.
Furthermore, the centralized system also provides a common set of metrics and reports that can be used to track the progress of the process and identify areas where collaboration is needed. As a result, it becomes easy for organizations to identify vulnerabilities on the attack surface, and collaborate to develop and implement necessary risk mitigation measures.
Additionally, the system also provides automated workflows and processes that can be used to coordinate the work of different teams and ensure that all vulnerabilities are addressed in a timely manner. This includes automated notifications, ticketing systems, and incident management workflows.
Allow Replacing Tools without Any Consequences
CAASM allows for the replacement of tools without any consequences by utilizing a modular and flexible architecture. This architecture enables the integration of different tools and technologies to be used in the organization, without affecting the overall functionality of the system.
One of the key aspects of a modular architecture is the use of APIs and integration points that allow different tools and technologies to be easily integrated into the organization.
Additionally, CAASM uses standard protocols and data formats. This helps to ensure that data can be easily exchanged between them.
So when a specific tool or technology is no longer needed or becomes obsolete, it can be easily replaced without affecting the overall functionality of the system.
Furthermore, the modular architecture even allows organizations to utilize a different set of tools and technologies for different parts of the CAASM process.
For example, one tool can be used for vulnerability scanning, another tool for network mapping, and another tool for threat intelligence. This makes it possible for organizations to use only the best solutions and to replace them when better tools & solutions become available.
Factors to Consider for Choosing a CAASM Solution
In addition to providing a complete asset inventory and eliminating vulnerability across cloud, security, and IT operations, a CAASM solution must be able to tackle difficult problems by understanding the context.
The best CAASM solutions provide actionable intelligence that helps to solve the most complicated problems.
However, you must know how to identify the right CAASM solution for your organization.
Specifically, you should consider the following four factors before making an investment decision.
Creates Comprehensive View of All Assets
A cyber asset attack surface management (CAASM) solution must be able to integrate with an organization’s all cyber assets, security infrastructure, and management solutions.
This especially includes authentication with all relevant systems, such as vulnerability detection systems and incident response platforms. This allows organizations to ensure that the solution has access to the most up-to-date information about their attack surface.
In addition to providing a comprehensive view of all cyber assets, the CAASM solution must also provide detailed information about the context, interactions, and access to files for each asset, including information about which files were accessed by whom and when.
This level of visibility is critical for identifying and prioritizing vulnerabilities, and for generating actionable remediation plans.
Additionally, the CAASM solution should be able to easily integrate with existing security infrastructure and management solutions to create a single view of the organization’s cyber assets.
Provides Actionable Intelligence
A CAASM solution must address the common use-case problems out-of-the-box. This means that the solution should be pre-configured to identify and prioritize vulnerabilities and generate actionable remediation plans without the need for extensive customization or tuning.
Furthermore, the solution should also provide the flexibility to refine the views into the respective environments, allowing organizations to tailor the solution to fit their specific needs. This, in turn, will help to minimize the amount of time and resources required to configure and maintain the solution.
Typically, an organization should only have to tune the last 5-10% of the solution. This way, organizations can quickly and easily identify and prioritize vulnerabilities, and implement effective remediation strategies without the need for technical expertise.
Automates Audit Actions and Compliance Prevention & Mitigation
The CAASM security solution must be equipped with a holistic view of all assets. Furthermore, it should be able to analyze and understand how assets align or deviate from policies and procedures through Machine Learning.
This helps organizations to eliminate the need to hire dedicated personnel to conduct manual audits and manage crisis situations. Besides, as workloads, assets, and users become increasingly dynamic, the use of Machine Learning becomes crucial for the success of a CAASM solution.
Open API
When choosing a CAASM solution for your organization, it is critical to make sure that the cyber assets data it collects is not locked in and can be used in other systems. Almost all CAASM solutions can gather, process, and link data from various sources, but it’s essential that the data is not restricted to the CAASM solution alone.
The value of a CAASM solution can only be realized if it allows enriching other operational tools in your organization such as configuration management databases (CMDBs), financial tools, and other day-to-day platforms.
In short, A CAASM solution that can tailor, refine and enhance cyber assets data, which can be later integrated with other systems to provide accurate and consistent information is a must-have.
Questions to Ask for Choosing the right CAASM Solution
Apart from the above factors, there are a few questions organizations must ask before deciding on a CAASM security solution.
The below questions will allow an organization to identify a CAASM security solution that is best suited to their individual needs.
- What does my environment consist of? Does it contain cloud assets, on-promises devices, or is it a hybrid of both?
- Where does my asset inventory data are currently stored?
- How many security tools do I currently have? Which (if not all) do I want to ingest into the cyber asset attack surface management platform?
- Which teams will be involved? And which stage of the asset lifecycle process each team is responsible for?
- Which are trustable sources for understanding the context of overall business risk?
- What method my incident response team currently uses to assess the blast radius in the event of an incident?
- What cybersecurity outcomes are most critical to my organization?
As we said earlier, answering the above questions will give you a better idea about which CAASM solution will best fit your organization on different levels including scalability, complexity, and support of your infrastructure.
How to Get Started with CAASM? – Conclusion
As you have just learned extensively, CAASM is not just another security solution.
It’s an all-in-one cybersecurity platform that gives organizations a complete cyber assets inventory, unravels gaps, and validates as well as enforces compliance policies automatically.
To get started with CAASM, you need to figure out a CAASM solution that best fits the requirements of your organization.
Book a Demo to learn more about how Scrut can help your organization in risk monitoring and compliance automation.
Frequently Asked Questions (FAQs)
What is Attack Surface Management?
Attack surface management is a process of continuously detecting, examining, addressing, and monitoring potential entry points and vulnerabilities for cyber attacks that make up an organization’s attack surface.
What is External Attack Surface Management?
External attack surface management is a relatively new cybersecurity approach that discovers and addresses the potential risks, threats, and vulnerabilities of internet-facing cyber assets and systems.
What is CAASM?
CAASM (Cyber Asset Attack Surface Management) is an emerging technology solution that empowers organizations to solve persistent cyber assets visibility problems and cybersecurity vulnerability challenges.
How Does Scrut Automation Help in CAASM?
Scrut Automation CAASM solution is capable of integrating with hundreds of different data sources to control complexity by navigating risks, mitigating threats, lowering incidents, and automating response actions.


















