Vendor Risk Management Best Practices

In an interconnected business world, where organizations increasingly rely on external vendors for a range of services, the need for robust vendor risk management has never been more crucial.
Whether it’s outsourcing critical business functions or utilizing third-party technologies, every collaboration introduces a unique set of risks that, if not managed effectively, can jeopardize the integrity and security of your operations.
This blog takes a deep dive into the dynamic field of vendor risk management, uncovering best practices that empower businesses to leverage the advantages of vendor partnerships while effectively guarding against potential pitfalls. It also explores Scrut’s solutions for streamlining vendor management for your organization.
What is vendor risk management?
The term vendor refers to an outside entity that provides goods or services to an organization, often as part of its supply chain. These include cloud service providers, consultants, software developers, payment processors, etc.
Vendor Risk Management (VRM) is a comprehensive approach that organizations adopt to identify, assess, monitor, and mitigate risks associated with their third-party vendors or suppliers.
As businesses increasingly rely on external partners to provide goods, services, or technologies, the potential for various risks also rises. Vendor risk management aims to minimize the impact of these risks on the organization’s operations, reputation, and overall stability.
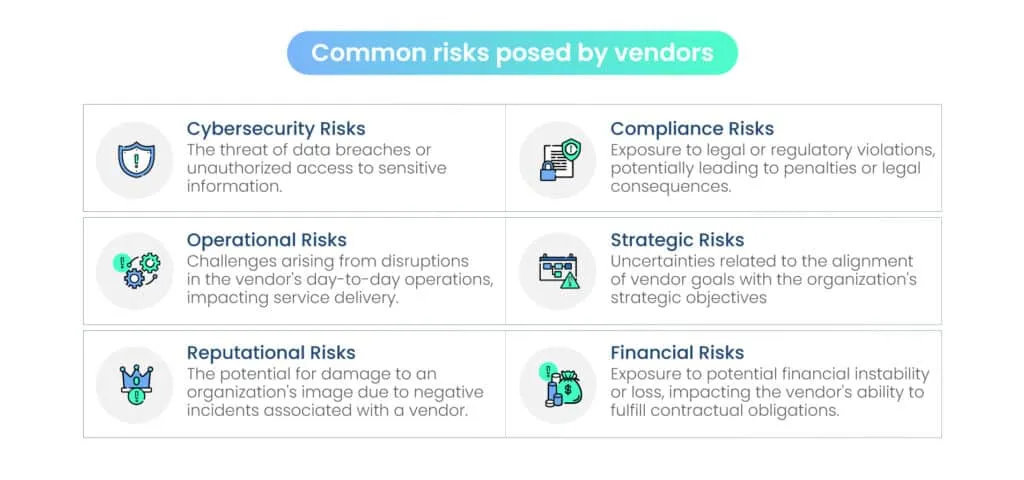
Common risks posed by vendors
What does vendor risk management entail?
Vendor Risk Management (VRM) involves a systematic approach to identify, assess, monitor, and mitigate risks associated with third-party vendors. The key components of vendor risk management include:
1. Risk identification
The process begins with identifying potential risks associated with third-party vendors. These risks can span various areas, including financial stability, data security, compliance with regulations, operational resilience, and more.
2. Risk assessment
Once identified, risks are assessed in terms of their likelihood and potential impact. This involves evaluating the vendor’s practices, controls, and overall risk posture to determine the level of risk associated with the partnership.
3. Due diligence
Thorough due diligence is crucial before entering into any vendor relationship. This involves evaluating the vendor’s financial health, reputation, security protocols, compliance with industry regulations, and any past incidents that may indicate a history of unreliability or security breaches.
4. Contractual safeguards
Implementing robust contracts and service level agreements (SLAs) that clearly define expectations, responsibilities, and obligations of both parties. These agreements should include provisions for risk mitigation, data protection, confidentiality, and compliance with relevant laws and regulations.
5. Monitoring and auditing
Regular monitoring of vendor performance and compliance is essential to ensure that they continue to meet the agreed-upon standards. Periodic audits may be conducted to assess the ongoing effectiveness of the vendor’s risk management practices.
6. Contingency planning
Developing contingency plans for potential disruptions caused by the vendor, such as financial instability, data breaches, or service outages. This ensures that the organization is prepared to respond promptly and effectively in case of unforeseen events.
7. Continuous improvement
Vendor risk management is an ongoing process that requires continuous improvement. Organizations should regularly review and update their risk management strategies, taking into account changes in the business environment, regulations, and the vendor landscape.
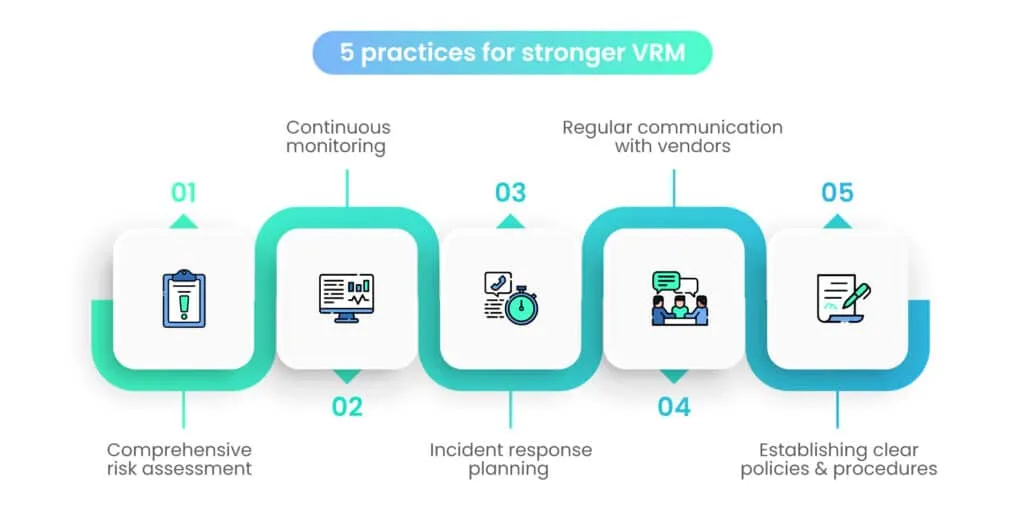
VRM Best Practices
By integrating the following best practices into your Vendor Risk Management program, your organization can not only mitigate potential risks but also foster a proactive and collaborative vendor ecosystem. These practices are essential for creating a resilient and secure vendor ecosystem:
1. Comprehensive risk assessment
Conduct a thorough risk assessment during the vendor onboarding process and periodically thereafter. This should include an evaluation of the vendor’s financial stability, security protocols, compliance history, and overall risk posture.
Consider using risk assessment frameworks and tools to streamline this process and ensure a comprehensive analysis.
2. Establish clear policies and procedures
Develop and communicate clear policies and procedures governing vendor relationships. These documents should outline expectations, responsibilities, and the steps to be taken in case of identified risks.
Ensuring that all stakeholders are aware of and adhere to these guidelines is crucial for the success of any VRM program.
3. Continuous monitoring and auditing
Regularly monitor vendor performance and compliance with established standards. Implementing automated monitoring tools can provide real-time insights into vendor activities.
Periodic audits, both internal and external, help verify the effectiveness of the vendor’s risk management practices and ensure ongoing compliance.
4. Regular training and awareness
Educate employees and stakeholders involved in vendor management about the importance of VRM. Provide training on identifying potential risks, understanding contractual obligations, and reporting any unusual activities.
Creating a culture of awareness ensures that everyone plays a role in maintaining a secure vendor environment.
5. Contractual clarity
Develop robust contracts and Service Level Agreements (SLAs) that clearly define expectations, responsibilities, and obligations of both parties. Include specific provisions related to risk mitigation, data protection, confidentiality, compliance with regulations, and the right to audit. Ensure legal experts review and validate these agreements.
6. Escalation protocols
Establish clear escalation protocols for handling identified risks. Define a hierarchy of steps to be taken in case of a potential issue, ensuring that critical risks are escalated promptly to the appropriate levels of management. This enables swift decision-making and action when necessary.
7. Regular communication with vendors
Foster open and transparent communication with vendors. Regularly discuss performance expectations, any changes in business operations, and potential risks. Building a collaborative relationship based on communication helps in addressing issues proactively and strengthens the overall partnership.
8. Incident response planning
Develop and regularly update incident response plans specific to vendor-related disruptions. Ensure that both the organization and the vendor understand their respective roles and responsibilities in the event of a security breach, service outage, or other emergencies. This preparedness minimizes the impact of incidents on business operations.
9. Stay informed about industry trends
Keep abreast of industry trends, emerging technologies, and evolving risks. The business landscape is dynamic, and staying informed enables organizations to adapt their VRM strategies to new challenges. Participate in industry forums, attend conferences, and engage with peers to share insights and best practices.
10. Continuous improvement
Vendor Risk Management is an evolving process. Regularly review and update your VRM strategies based on changes in the business environment, regulations, and the vendor landscape. Collect feedback from stakeholders and use it to refine and enhance your VRM program continually.
How Scrut can boost your VRM program
Scrut’s comprehensive VRM capabilities can empower your organization to navigate the complexities of vendor relationships with confidence. To elevate your VRM strategies and streamline the process, Scrut introduces powerful features designed to enhance vendor discovery, risk scoring, questionnaire management, and mitigation task tracking.
1. Vendor Discovery: Analyzing your vendor landscape
Effectively managing vendor risks begins with a comprehensive analysis of your vendor landscape. Scrut’s innovative ‘vendor discovery’ feature, integrated into the VRM module, takes the guesswork out of identifying vendors. This feature automatically scans your multi-cloud infrastructure for third-party applications that could potentially be vendors.
Once identified, Scrut presents a detailed register of these applications, allowing you to determine their vendor status. This not only facilitates better planning but also ensures that all vendors, whether existing or incoming, are accounted for in your risk management strategy.
2. Risk Score: Proactive monitoring and classification
While understanding the impact of risks during vendor onboarding is crucial, ongoing monitoring is equally vital. Scrut’s risk scoring system provides a real-time snapshot of each vendor’s current status. This proactive approach enables you to treat risks promptly and effectively.
The risk scores are calculated based on responses from questionnaires submitted by vendors. These scores are broken down by domain and contribute to an overall risk score associated with each vendor.
This comprehensive overview allows you to prioritize and allocate resources efficiently.
3. Questionnaires: Customizable assessments for deeper insights
Scrut empowers you to create and manage questionnaires directly on the platform. Choose from four pre-built templates or craft custom questionnaires from scratch. The flexibility extends to specifying submission and review dates, sending reminders, scoring responses, and accepting or rejecting submissions.
Recipients of questionnaires are directed to a unique, customized portal, simplifying the response process.
Scrut’s intuitive interface allows for manual searches, segmentation by status, and provides a high-level pictographic view through an actionable pie chart on the vendor overview page.
4. Mitigation Tasks: Collaborative remediation efforts
Identifying risks is only the first step; effective collaboration is essential for successful remediation. Scrut facilitates this collaboration by allowing stakeholders to create, track, and manage mitigation tasks directly from the platform.
Inside each mitigation task, stakeholders can add attachments, communicate progress, and document changes. Audit logs provide transparency and a historical perspective on the remediation process.
Just like with questionnaires, Scrut offers a high-level pie chart view and detailed segmentation, along with a search functionality, ensuring that nothing falls through the cracks.
Conclusion
As organizations increasingly rely on external vendors for a multitude of services, the need for a robust and adaptive VRM strategy cannot be overstated.
VRM is crucial for safeguarding an organization against potential threats and ensuring the smooth functioning of its operations. By implementing best practices in VRM, businesses can not only mitigate risks but also foster stronger, more resilient vendor relationships.
From comprehensive risk assessments and due diligence to regular monitoring and communication, each step in the VRM process plays a pivotal role in enhancing cybersecurity and promoting overall business continuity.
By staying informed, adapting to changing landscapes, and fostering a culture of collaboration, organizations can build a robust VRM framework that not only protects sensitive data but also contributes to long-term success in an ever-changing business environment.
Scrut, with its innovative features for vendor discovery, risk scoring, questionnaire management, and mitigation task tracking, offers a comprehensive solution to empower businesses in navigating the complexities of vendor relationships. Schedule a demo today to learn more!
FAQs
1. What is Vendor Risk Management (VRM)?
Vendor Risk Management (VRM) is a systematic approach to identifying, assessing, and managing potential risks associated with third-party vendors and suppliers. It involves evaluating the impact of vendor relationships on an organization’s operations, data security, and overall risk posture.
2. Why is Vendor Risk Management important for businesses?
Vendor Risk Management is vital for businesses as it helps mitigate the risks associated with outsourcing various services. By implementing robust VRM practices, organizations can protect sensitive data, ensure compliance with regulations, and establish a resilient framework that safeguards against potential disruptions and threats.
3. What are some Vendor Risk Management best practices?
Several best practices contribute to effective Vendor Risk Management:
- Comprehensive Risk Assessments: Regularly evaluate and categorize vendor risks based on their potential impact on the organization.
- Due Diligence: Conduct thorough background checks and due diligence before engaging with a new vendor.
- Continuous Monitoring: Implement ongoing monitoring processes to stay informed about changes in vendor risk profiles.
- Clear Communication: Foster open and transparent communication with vendors to address and resolve potential risks collaboratively.
These practices, among others, contribute to a proactive and resilient approach to managing vendor-related risks within an organization.


















