Unlocking the NIS Directive: Your in-depth manual
Businesses must implement the NIS Directive because it improves their cybersecurity posture and guarantees the safety of sensitive data and systems from online attacks. Businesses can avoid harsh legal penalties and promote a risk-management culture—which is essential for detecting and reducing vulnerabilities—by following this directive.
The order also requires executive accountability, which means that senior management is in charge of supervising cybersecurity measures and encouraging a proactive approach to security.
Moreover, stronger cross-border cybersecurity collaboration supports the EU’s overall digital resilience and fosters a safer business climate. In addition to reducing risks, compliance with the NIS Directive gives businesses a chance to build stronger relationships with partners and consumers by showcasing a dedication to strong cybersecurity practices.
Understanding the NIS Directive
A. What is the NIS Directive?
The “Directive on security of network and information systems” is known as the “NIS Directive”. It is a directive from the European Union with the goal of raising cybersecurity standards in all EU member states. August 2016 marked the implementation of the EU NIS Directive, which was approved in 2016.
EU member states had until May 9, 2018, to transpose the NIS Directive into their national laws and regulations and until November 9, 2018, to identify the operators of essential services (OES) and to designate competent authorities to oversee the implementation and enforcement of the directive. This timeline provided member states with approximately two years to incorporate the requirements of the NIS Directive into their national cybersecurity frameworks and to establish the necessary mechanisms for compliance and enforcement.
Its primary goals are to strengthen the EU’s overall cybersecurity posture, foster better cross-border collaboration on cybersecurity matters, and boost the resilience of vital services and infrastructure against cyberattacks. The directive compels member states to set up national cybersecurity frameworks and imposes specific cybersecurity requirements on operators of essential services (OES) and digital service providers (DSPs).
B. Scope of NIS Directive
The NIS Directive cyber security covers a wide range of topics related to cybersecurity policy in the European Union. Its main goal is to improve the cybersecurity resilience of important service providers and operators of critical infrastructure. Here’s an overview of the scope of the EU NIS Directive:

C. Objectives and goals of NIS Directive
The NIS Directive cyber security seeks to improve cybersecurity resilience across the European Union by achieving a number of important targets and goals. The directive’s primary aims and objectives are as follows:
- Enhance cybersecurity resilience: Strengthen the overall cybersecurity posture of EU member states by promoting the adoption of robust security measures and practices across critical infrastructure operators and essential service providers.
- Protect critical infrastructure: Safeguard critical infrastructure sectors, such as energy, transportation, banking, healthcare, and digital services, from cyber threats that could disrupt essential services and harm national security and public safety.
- Ensure continuity of essential services: Ensure the continuity of essential services by requiring OES to implement appropriate security measures and incident response capabilities to mitigate the impact of cyber incidents.
- Foster cross-border cooperation: Promote cooperation and information sharing among EU member states to effectively manage cross-border cybersecurity incidents and address emerging cyber threats that may have transnational implications.
- Facilitate incident reporting and response: Establish a framework for timely reporting and response to significant cybersecurity incidents by OES and DSPs to enable swift action and mitigation efforts.
- Improve security awareness and preparedness: Raise awareness about cybersecurity risks and best practices among OES, DSPs, and relevant stakeholders to enhance preparedness and resilience against evolving cyber threats.
- Promote public-private collaboration: Encourage collaboration between public authorities, industry stakeholders, and cybersecurity experts to exchange information, share best practices, and develop innovative solutions to address cybersecurity challenges effectively.
Requirements of the NIS Directive
A. Obligations of entities covered under the NIS Directive
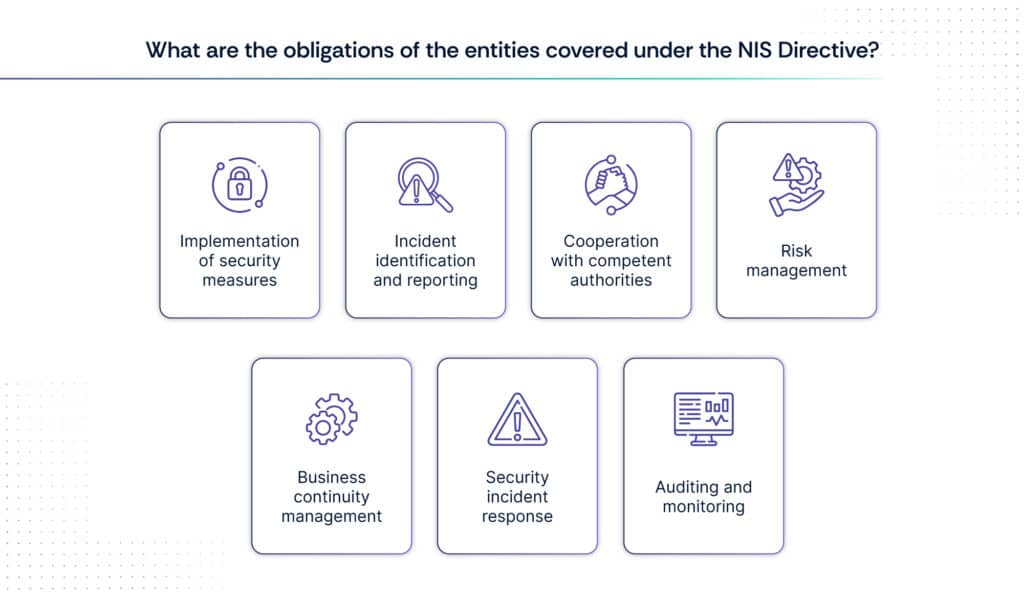
The NIS Directive outlines specific obligations for operators of essential services (OES), Digital Service Providers (DSPs), and critical infrastructure and essential services covered to enhance cybersecurity resilience and ensure the continuity of essential services within the European Union. Here are the key obligations for such entities as specified in the directive:
1. Implementation of security measures
Entities covered under the NIS Directive are required to implement appropriate technical and organizational security measures to manage the risks posed to the security of their network and information systems. These measures should be proportionate to the security risks identified and aim to ensure a level of security appropriate to the risks faced.
2. Incident identification and reporting
Covered entities must establish procedures for identifying, handling, and reporting significant cybersecurity incidents. They are required to notify the competent authorities of such incidents without undue delay and provide relevant information necessary for assessing and managing the incident.
3. Cooperation with competent authorities
Such entities are obligated to cooperate with the competent authorities designated by member states to implement and enforce the NIS Directive. This includes providing information and assistance to facilitate the investigation of cybersecurity incidents and compliance assessments.
4. Risk management
Entities covered under the said directive must conduct regular risk assessments to identify, assess, and prioritize cybersecurity risks to the security of their essential services. Based on the outcomes of these assessments, they should implement appropriate risk mitigation measures to reduce the likelihood and impact of potential cybersecurity incidents.
5. Business continuity management
The said entities are required to establish and maintain appropriate business continuity management processes to ensure the continuity of essential services in the event of a cybersecurity incident or other disruptive events. This includes developing contingency plans, backup procedures, and recovery strategies to minimize service disruptions.
6. Security incident response
Entities covered under the NIS Directive must establish and maintain incident response capabilities to effectively detect, respond to, and recover from cybersecurity incidents. This includes establishing incident response teams, procedures for incident handling, and coordination mechanisms with relevant stakeholders. (more on the incident reporting requirements in section B)
7. Auditing and monitoring
Such entities are expected to implement monitoring and auditing mechanisms to assess the effectiveness of their security measures and ensure compliance with the requirements of the NIS Directive. Regular audits and assessments help identify weaknesses and gaps in cybersecurity defenses and inform continuous improvement efforts.
B. Incident reporting requirements under the NIS Directive
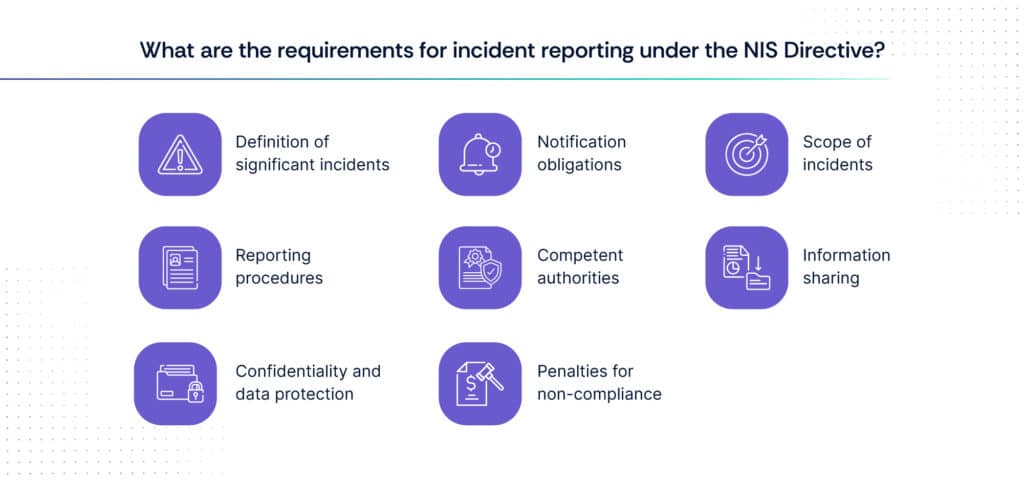
Under the EU NIS Directive, incident reporting requirements play a crucial role in ensuring timely response and mitigation of significant cybersecurity incidents affecting critical infrastructure and essential services. Here are the key aspects of incident reporting under the directive:
1. Definition of significant incidents
The directive defines criteria for determining the significance of cybersecurity incidents that warrant reporting. Significant incidents are those with a substantial impact on the continuity of essential services or the security of digital services covered by the directive.
2. Notification obligations
OES and DSPs are obligated to notify the competent authorities of significant cybersecurity incidents without undue delay. Notification should include relevant information necessary for assessing the impact of the incident and coordinating response efforts.
3. Scope of incidents
Significant incidents that must be reported include those affecting the security and availability of essential services, such as disruptions to critical infrastructure, unauthorized access to sensitive data, denial-of-service attacks, and other cybersecurity breaches with a significant impact.
4. Reporting procedures
OES and DSPs are required to establish procedures for the identification, handling, and reporting of significant cybersecurity incidents. These procedures should outline the steps to be taken when a significant incident occurs, including the notification process and the information to be provided to the competent authorities.
5. Competent authorities
Member states designate competent authorities responsible for receiving incident reports and coordinating response efforts within their jurisdictions. OES and DSPs must notify the competent authority designated by the member state where they are established or provide services.
6. Information sharing
Incident reporting facilitates information sharing and collaboration among OES, DSPs, competent authorities, and other stakeholders. Timely reporting enables competent authorities to assess the impact of incidents, coordinate response efforts, and share threat intelligence to mitigate future risks.
7. Confidentiality and data protection
Incident reports may contain sensitive information about cybersecurity vulnerabilities, threats, and impacts. Competent authorities are responsible for handling incident reports in accordance with data protection laws and ensuring the confidentiality of sensitive information.
8. Penalties for non-compliance
Failure to comply with incident reporting requirements may result in penalties imposed by competent authorities. Penalties may include administrative fines and other measures necessary to ensure compliance with the NIS Directive.
Penalties and enforcement of NIS Directives

Best practices for NIS Directive compliance

A. Establishing a robust cybersecurity framework
- Develop a comprehensive cybersecurity framework that aligns with the requirements of the NIS Directive.
- Define clear roles, responsibilities, and accountability for cybersecurity within the organization.
- Implement security policies, standards, and procedures to guide cybersecurity efforts and ensure consistency.
- Establish mechanisms for continuous monitoring, evaluation, and improvement of cybersecurity practices.
B. Conducting risk assessments and vulnerability management
- Regularly assess and prioritize cybersecurity risks to critical infrastructure and essential services.
- Identify vulnerabilities in systems, networks, and applications and prioritize remediation efforts based on risk.
- Implement proactive measures to mitigate known vulnerabilities and reduce the likelihood of cyber incidents.
- Continuously monitor for emerging threats and vulnerabilities and adapt cybersecurity measures accordingly.
C. Developing incident response plans
- Develop and maintain incident response plans tailored to the organization’s specific risks and operational requirements.
- Define clear procedures for detecting, reporting, and responding to cybersecurity incidents promptly.
- Establish communication protocols, escalation procedures, and coordination mechanisms with relevant stakeholders.
- Conduct regular exercises and simulations to test the effectiveness of incident response plans and improve preparedness.
D. Enhancing collaboration and information sharing
- Foster collaboration and information sharing with industry peers, government agencies, and cybersecurity organizations.
- Participate in information sharing forums, threat intelligence sharing platforms, and sector-specific information-sharing and analysis centers (ISACs).
- Share insights, lessons learned, and best practices to improve cybersecurity resilience across the sector and the broader cybersecurity community.
- Engage in public-private partnerships, joint exercises, and initiatives to address cybersecurity challenges collectively.
Challenges and considerations of the NIS Directive
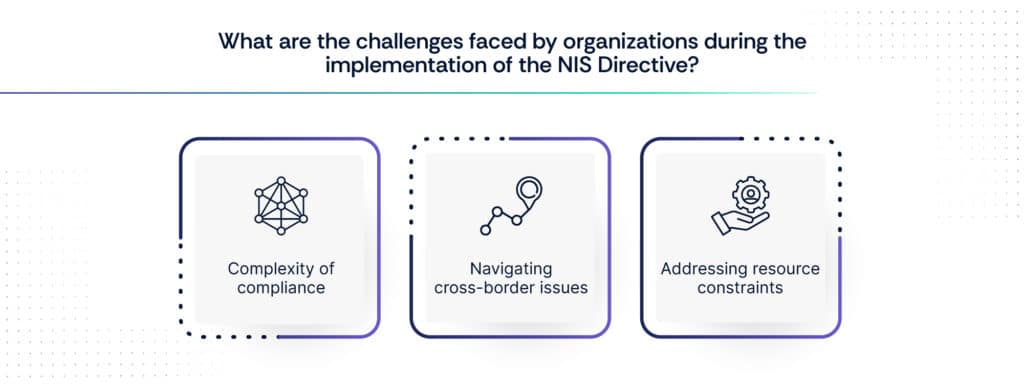
A. Complexity of compliance
- The NIS Directive introduces complex regulatory requirements that may vary across different sectors and member states.
- Compliance efforts require significant resources, expertise, and coordination among various stakeholders within organizations.
- Understanding and interpreting the directive’s provisions, guidelines, and technical standards can be challenging for organizations.
B. Navigating cross-border issues
- Organizations operating across multiple EU member states must navigate differences in regulatory frameworks, enforcement practices, and reporting requirements.
- Cross-border incidents may involve coordination with multiple competent authorities, national cybersecurity agencies, and other stakeholders, leading to complexity and delays in incident response.
C. Addressing resource constraints
- Many organizations, particularly small and medium-sized enterprises (SMEs), may face resource constraints, budget limitations, and skill shortages when implementing the EU NIS Directive compliance measures.
- Allocating sufficient resources for cybersecurity initiatives, training programs, and technology investments may pose challenges for organizations with limited financial and human resources.
Introduction of NIS 2 Directive
NIS 2 Directive or NIS-2 DIrective is the name of the legislative act released on December 14, 2022, that aims to achieve a high common level of cybersecurity across the European Union. The member states must adopt the NIS 2 Directive by 17 October 2024 and apply those measures by the next day.
The new Commission proposal aims to enhance and modernize the NIS Directive by expanding its scope to include additional sectors crucial to the economy and society. It introduces a size cap to include medium and large companies within selected sectors and eliminates the distinction between operators of essential services and digital service providers. The proposal strengthens security and reporting requirements by imposing a risk management approach and introducing more precise provisions for incident reporting.
Additionally, it addresses cybersecurity risks in supply chains and supplier relationships and proposes more stringent supervisory measures and harmonized sanctions regimes across Member States. The proposal enhances cooperation between Member State authorities, increases operational cooperation for cyber crisis management, and establishes a framework for coordinated vulnerability disclosure across the EU. Read our article here to learn more about the differences between NIS 1 and NIS 2.
How can Scrut help implement the NIS Directive?
Scrut can play a pivotal role in the implementation of the NIS Directive by providing comprehensive cybersecurity solutions tailored to the specific requirements outlined in the directive. Here’s how Scrut can help:
1. Compliance assessment
Scrut can conduct thorough assessments to ensure your organization meets the compliance requirements outlined in the NIS Directive. This includes evaluating existing cybersecurity measures, identifying gaps, and recommending necessary actions to achieve compliance.
2. Risk management
Scrut offers robust risk management tools and frameworks to help organizations assess, prioritize, and mitigate cybersecurity risks effectively. By aligning risk management practices with NIS Directive requirements, Scrut enables organizations to strengthen their overall cybersecurity posture.
3. Incident response
Scrut equips organizations with advanced incident response capabilities to detect, analyze, and respond to cybersecurity incidents promptly. With automated incident detection and response mechanisms, Scrut helps minimize the impact of security breaches and ensure timely reporting as mandated by the NIS Directive.
4. Security measures implementation
Scrut assists organizations in implementing the technical and organizational security measures required by the NIS Directive. This includes deploying intrusion detection systems, access controls, encryption protocols, and other cybersecurity defenses to protect networks and information systems.
5. Continuous monitoring
Scrut provides continuous monitoring and real-time threat intelligence to help organizations stay vigilant against evolving cyber threats. By monitoring networks, systems, and applications round the clock, Scrut enables proactive threat detection and mitigation in line with NIS Directive objectives.
6. Reporting and documentation
Scrut simplifies the process of incident reporting and documentation as mandated by the EU NIS Directive. By generating comprehensive reports and maintaining audit trails of security incidents, Scrut ensures organizations remain compliant with regulatory requirements.
Final thoughts
In summary, the NIS Directive emerged as a crucial tool in fortifying cybersecurity resilience across the EU, addressing escalating cyber threats to vital services and infrastructure. By standardizing measures, fostering cross-border collaboration, and mandating incident reporting, the directive aimed to enhance cybersecurity posture.
Despite challenges, such as compliance complexities, its significance remains undeniable. The introduction of the NIS 2 Directive underscores the EU’s commitment to evolving cybersecurity measures. Embracing best practices and collaboration is vital for organizations to mitigate cyber risks and contribute to a safer digital landscape.
Empower your cybersecurity strategy with Scrut. Seamlessly navigate NIS Directive compliance, fortify your defenses, and protect your vital services. Elevate your cybersecurity posture with Scrut today!
FAQs
1. What is the NIS Directive?
The NIS Directive, short for the “Directive on security of network and information systems,” is a legislative act enacted by the European Union to enhance cybersecurity standards across member states and protect essential services from cyber threats.
2. What are the main objectives of the NIS Directive?
The primary goals of the NIS Directive include improving cybersecurity resilience, protecting critical infrastructure, ensuring continuity of essential services, fostering cross-border cooperation, and promoting incident reporting and response capabilities.
3. How can organizations ensure compliance with the NIS Directive?
Organizations can ensure compliance with the NIS Directive by conducting thorough assessments, implementing security measures, establishing incident response plans, cooperating with competent authorities, and staying informed about regulatory updates and best practices.


















