The Fundamentals of a Risk Management Plan
Risk refers to any unpredictable event that could disrupt operations or cause financial or reputational harm to the company. It can take many forms, from financial to cyber-attacks. Understanding the threats your organization faces is important, but so is understanding how risk treatment plans can mitigate the effects of those threats.
What Is A Risk Treatment Plan?
A risk treatment plan, also known as a risk mitigation plan, is a document that outlines the strategies and actions to be taken to address and manage risks identified in a project, organization, or any other context.
Before you implement any risk treatment action, you must first understand what risks you are facing. There are two kinds of risks:
- Inherent risk: The amount of risk in the absence of controls is inherent. It is based on probability and impact.
- Unavoidable risk: It is the kind of risk that remains even after a safeguard or control has been implemented.
A risk treatment plan aims to minimize the potential negative impact of risks on objectives and increase the likelihood of achieving desired outcomes. It involves analyzing risks, evaluating their potential consequences and likelihood of occurrence, and developing appropriate responses to handle them effectively.
Here are the key components typically included in Risk Treatment Plan:
- Risk Identification: Determine and document the specific risks that have been identified through a risk assessment process. Each risk should be described in detail, including its potential impact and probability.
- Risk Analysis: Evaluate the identified risks to determine their significance and prioritize them based on their potential impact on the project or organizational objectives. This analysis helps understand which risks require immediate attention and which can be addressed later.
- Risk Response Strategies: Define strategies to address each identified risk. There are four primary risk response strategies:
- Avoidance: Implement measures to eliminate the risk or its causes.
- Mitigation: Take actions to reduce the likelihood or impact of the risk.
- Transfer: Transfer the risk to a third party, such as insurance or outsourcing.
- Acceptance: Acknowledge the risk and its potential consequences without taking specific action.
- Risk Response Actions: Specify the actions that will be taken to implement each risk response strategy. These actions should be detailed and actionable, with assigned responsibilities and timelines.
- Risk Monitoring and Review: Outline the process for monitoring and reviewing the effectiveness of the risk treatment plan. This includes defining key performance indicators or metrics to track progress, establishing reporting mechanisms, and conducting regular reviews to ensure ongoing risk management effectiveness.
- Communication and Reporting: Identify the stakeholders who need to be informed about the risks, their treatment strategies, and the progress in implementing the plan. Determine the frequency and method of communication to keep relevant parties informed.
Risk Treatment Options
Risk treatment options are actions to manage or mitigate risks identified in a particular context. There are four risk treatment options:
- Accept
Risk must be accepted when there is no way to avoid, mitigate, or transfer it. Accepting the risk is the best option when the risk is unlikely to occur, or the impact is minor. This option is typically chosen when the cost to treat the risk outweighs the potential impact.
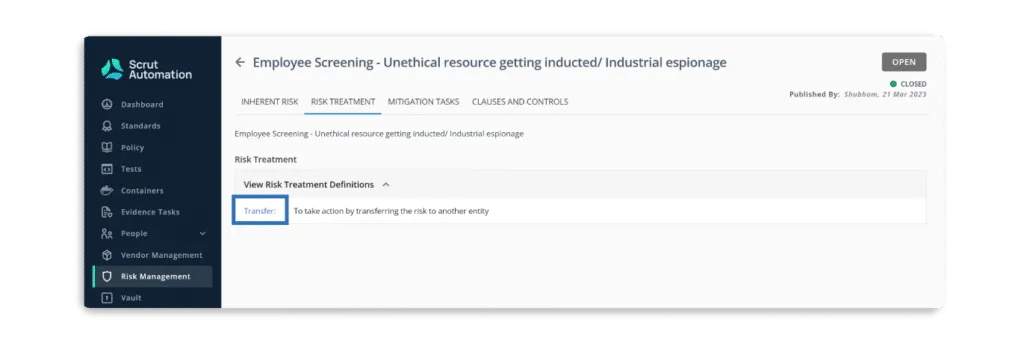
- Transfer
Sometimes, you or your team cannot avoid, accept, or mitigate issues. One effective risk management strategy is passing a portion of the threat to another party to reduce its likelihood or impact on the organization. For example, purchasing an insurance policy transfers the financial risk of a potential loss to the insurance company. You can also outsource the process that contains the risk to another provider, transferring the risk to the outsourced provider. This type of risk management could be done by entering into a contract with a service provider or purchasing error insurance.
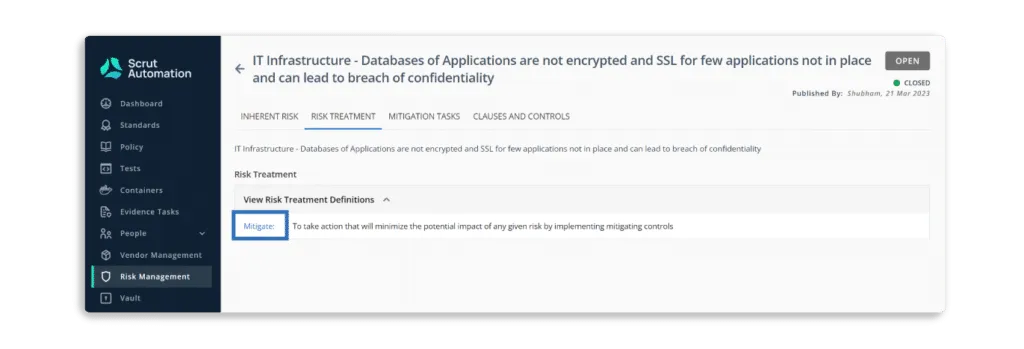
- Mitigate
Risk mitigation is a control process that stops a risk from becoming a problem and reduces it to an acceptable level. This means taking action that will result in as little damage to your project as possible. This includes identifying the risk, evaluating all potential solutions, developing a plan, acting, and monitoring the results. For example, installing fire sprinkler systems in buildings mitigates the potential damage from a fire.
- Avoid
Avoidance is a strategy that eliminates the possibility of a risk becoming a reality. For example, if there is a high risk of financial investment, you may avoid investing in it. Risk avoidance begins with identifying the risks. The ones that tend to arise at the start of a project are then examined. Finally, a course of action is determined after considering the relative importance of the risks.
Steps In Developing A Risk Treatment Plan?
The steps of risk treatment plan development are as below:
Step 1- Risk treatment: The first step in creating a treatment plan is deciding which treatment option you will choose based on the requirement: acceptance, transfer, sharing, or something else.
Step 2- Assign accountability for tasks: Determine what needs to happen in the event of a disaster and who is responsible for each action. Clear directions are one of the most basic and effective tools for a quick recovery. Ensure the treatment plan’s owner can specify how implementation will be tracked, including critical indicators that indicate rising or falling risk levels.
Step 3- Document: You’ll need to create a treatment plan document that outlines your strategy.
Step 4- Create backup plans: Prepare plans for continuing or resuming operations during a crisis. Your detailed plans will be determined by the following factors: the type, style, and size of your business and the extent of the damage.
Step 5- Set a resolution date: This is the deadline by which the situation should be resolved.
Step 6- Keep an eye out for new risks: Continuous risk monitoring will assist you in developing realistic and effective strategies for dealing with issues as they arise.
How Does Scrut Help?
Scrut risk management is more than just an assessment tool; it also functions as a dashboard in a single window for managing your organization’s risk status. The tool provides the visibility required to avoid threats and effectively communicate the impact of risk on critical business activities.
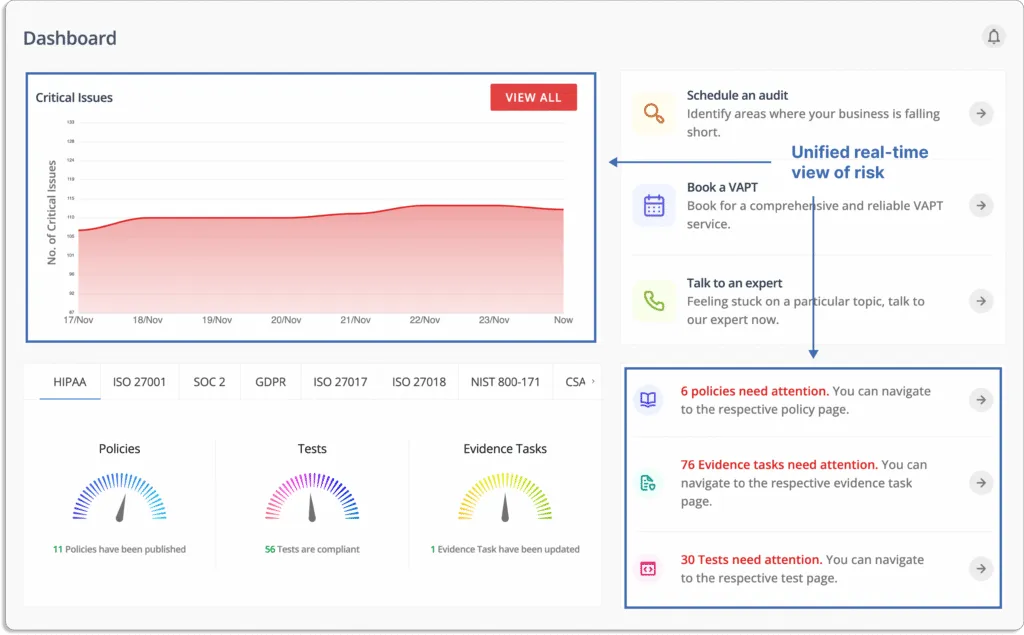
As shown in the screenshot below, it provides complete visibility into your risk posture.

The platform detects risks throughout your landscape. It scans your ecosystem for risks across the code base, infrastructure, applications, vendors, employees, and access to automate risk identification.
With Scrut, you can build your risk register in minutes with scoring methodologies, expert-provided inherent risk scores, and automated workflows. Choose from Scrut’s library of most common risks across seven categories (Governance, People, Customer, Regulatory, Resilience, Technology, and Vendor management).
To build your risk library, click on Create New button.

A dialogue box will appear, as shown in the screenshot below:
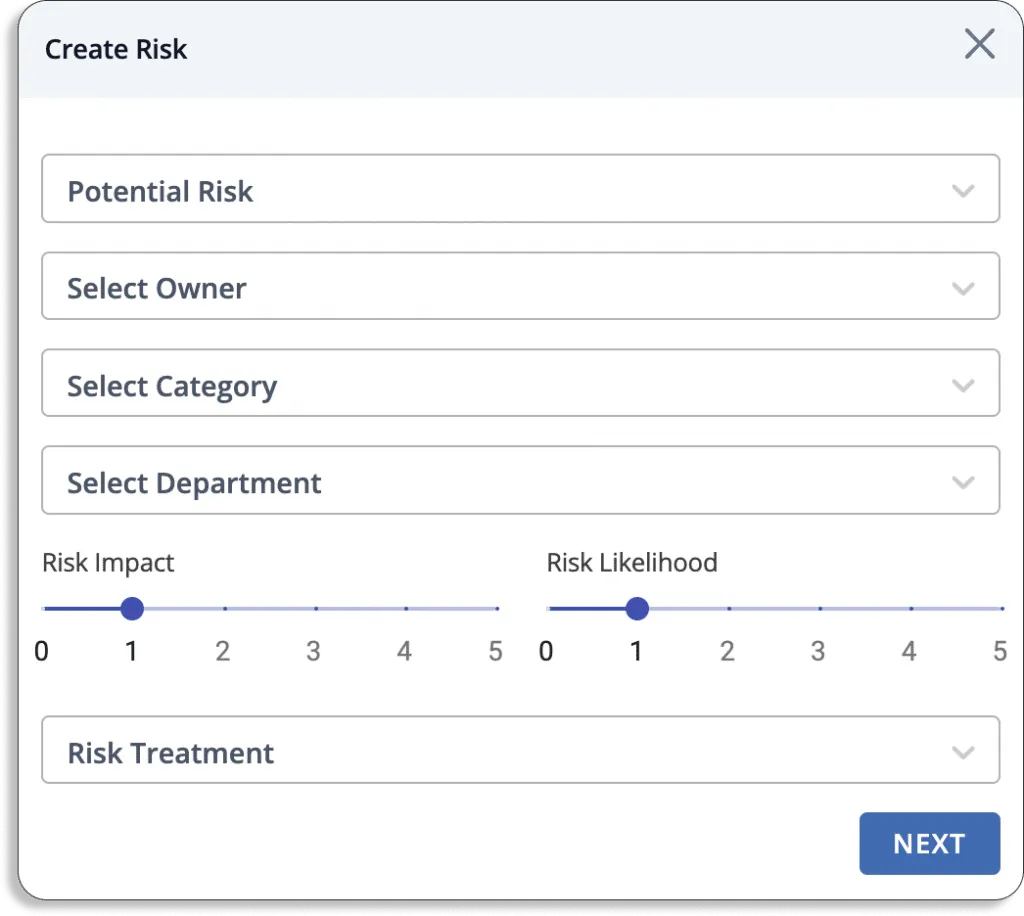
You can select any risk from our risk library or develop custom risks.

At the end of this procedure, you will get a list of all the risks linked to your organization, as shown in the screenshot below.
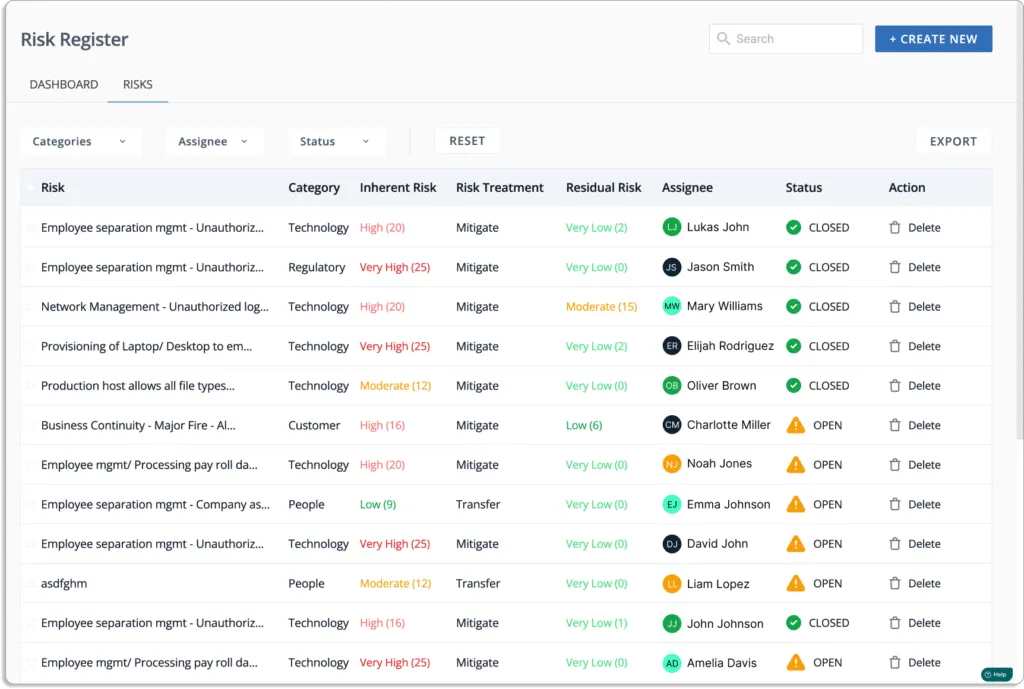
A robust, pre-loaded risk library enables you to select the appropriate controls, risks, and threats to assess the risk of your business process or initiative.
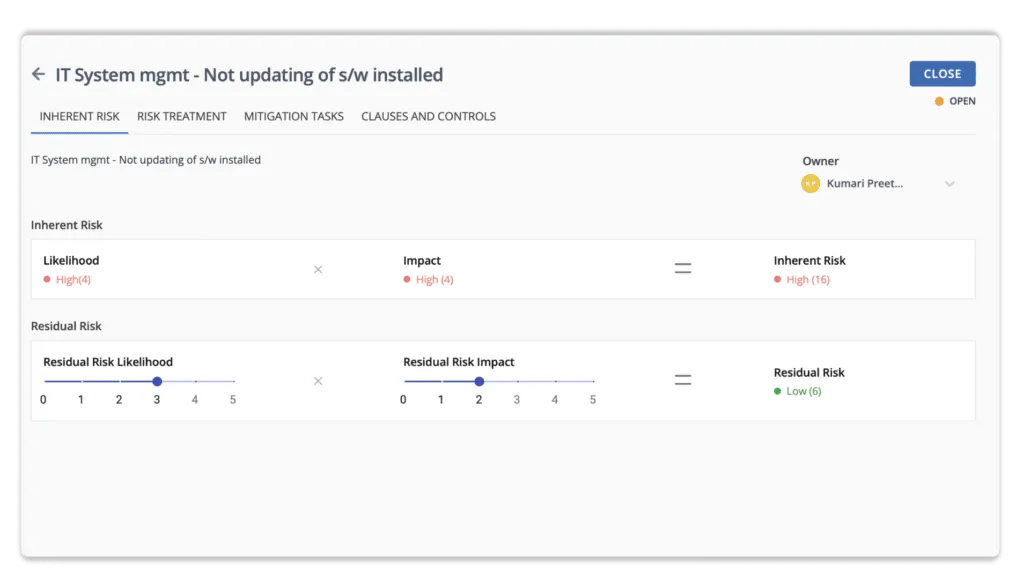
Scrut simplifies your risk exposure by identifying and mitigating major risk areas. The tool allows you to evaluate your risk profile using automated risk scoring. It generates risk scores based on the likelihood and impact of events.
Risk = Likelihood * Impact
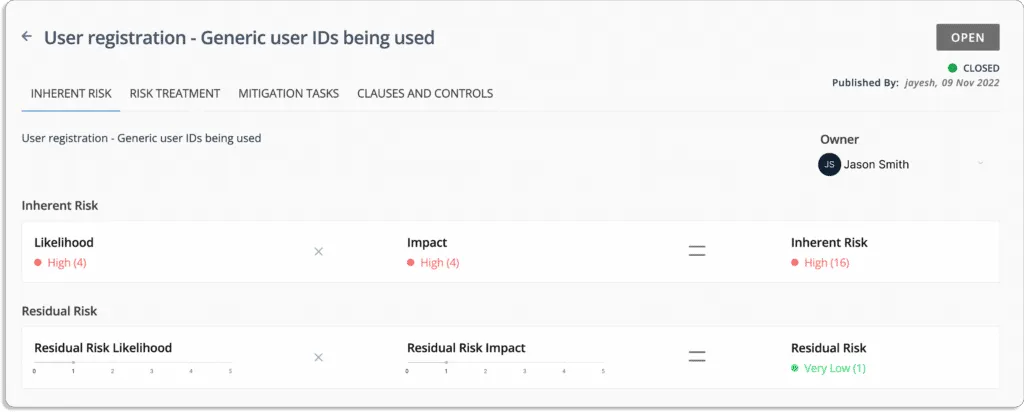
The likelihood of this event = 5
The impact in case the event occurs = 4
Thus, the inherent risk associated with this event is also high = 20
Likelihood (5) * Impact (4) = 20
The screenshot below shows that risks can also be assigned to team members for treatment.

Scrut’s expert-vetted scoring methodologies allow you to quantify your risk profile and evaluate the impact of your treatment plans using inherent and residual scores.
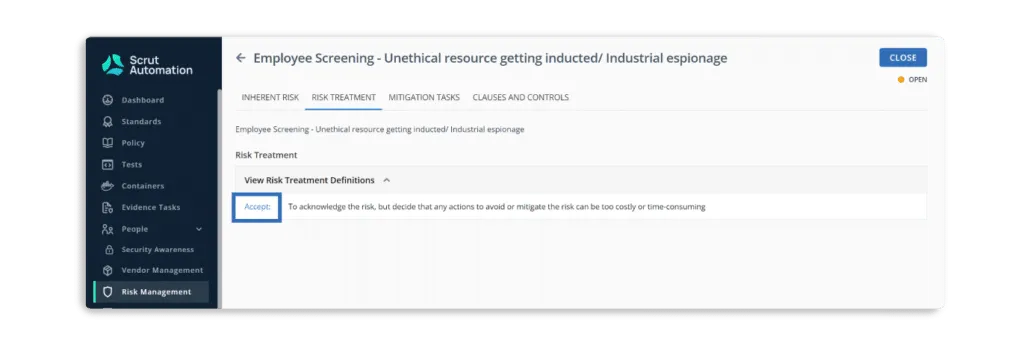
Using the Scrut risk management tool, you can free your teams from time-consuming manual work and optimize their talent by selecting your treatment plan — accepting, transferring, or mitigating each risk.
- Risk Remediation – eliminates the risk.
- Risk Mitigation – minimizes the impact or likelihood of the risk.
- Risk Transfer – transfers the risk to another party. For example, an insurance company.
- Risk Acceptance – accepts the risk.
You get an overall view of your risk posture with all the details close at your disposal by providing a quantified summary of risks by status and residual risk score and the details for each risk, its related threats, and controls. As a result, risk can be effectively avoided, mitigated, and communicated to justify investments and strategic decision-making.
As shown in the screenshot below, you can also create mitigation tasks.

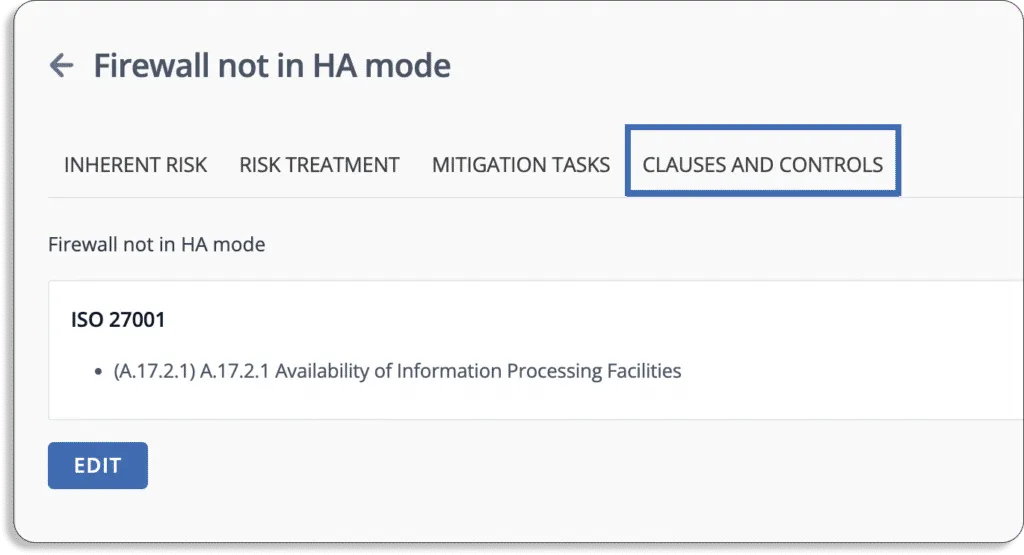
Scrut Risk Management automatically maps all risks to compliance frameworks. It maps risks to controls in popular frameworks such as ISO 27001, HIPPA, SOC 2, etc. You don’t have to go through thousands of risk sources to stay compliant.
Read how Apty implements automated risk monitoring for compliance with ISO 27001, SOC 2, HIPAA, GDPR, ISO 27017, and ISO 27018.
Scrut Risk Management provides a centralized interface for identifying, assessing, and mitigating IT and cyber risk. It gives organizations the awareness they need to avoid risks and communicates the risk implications on high-priority strategic targets. With built-in scoring techniques, expert-provided inherent risk scores, and automated workflows, it’s quick and easy to establish new IT risk programs to better avoid, control, and mitigate risk. Click here for more details on how Scrut helps in risk treatment.



















