Security Control Types
The main objective of putting security controls in place is to prevent or mitigate the effects of a security incident. A lack of security controls puts data confidentiality, integrity, and availability at risk.
In this article, we will discuss security control types, security control functions, and security control frameworks.
Controls are chosen based on the organization's risk assessment and how it addresses each risk. Because each organization's risk is unique, so are the controls designed to address that risk. Security controls are parameters put in place to protect various types of data and assets important to an organization. It is any safeguard to avoid, detect, or minimize security risks to physical property, information, or other assets.
Types of Security Controls
The types of security controls are mentioned below:
Technical Controls
Technical controls use technology to reduce hardware and software vulnerabilities. It consists of hardware, software, and firmware used to prevent unauthorized access to systems or data. These controls carry out a variety of vital tasks, such as preventing unauthorized users from accessing a system and identifying security violations. Technical functions are involved in managing and controlling employee access. These must be structured to protect data at rest (for example, data stored on a hard drive) and data in motion (for instance, data moving across a network). Some examples include Security Information And Event Management (SIEM), Firewalls, Intrusion Detection Systems (IDS), etc.
Administrative Controls
These controls define the human factors of security. It includes any security measures aimed at managing people. It refers to policies, procedures, or guidelines that define business practices in accordance with the security goals of the organization. It includes all employees and determines who has privileged access to data resources. Employees may not understand how to keep resources, systems, and data secure if critical policies are not in place. These policies could be used for various purposes, including hiring and firing team members, Internet use, job separation, data categorization, audits, employee awareness training, etc.
Physical Controls
Physical controls safeguard your resources and infrastructure against physical threats like theft or damage. It is the implementation of security measures within a defined structure to prevent unauthorized access to sensitive information. These controls are on-premises to assist you in managing the environment in which critical information exists. Examples of physical controls are - thermal alarm systems, security guards, picture IDs, etc. These controls include everything from guards to biometric controls to CCTVs, motion sensors, and sprinklers.
Functions of Security Controls
The functions of security controls are mentioned below:
Preventative Controls
Preventative controls are in place to prevent the likelihood of an information security incident. It refers to any security measure intended to prevent unwanted or unauthorized activity. Examples include - antivirus software, security awareness training, multi-factor authentication, alarm systems, data classification, etc.
Detective Controls
Detective controls are security measures or solutions that alert to unauthorized or unwanted activity in progress or after it has occurred. They can also assist you in determining whether your preventative controls are effective. Examples of detective controls include data leakage detection, door alarms, fire alarms, malware detection, and so on.
Corrective Controls
A corrective control is any action taken to repair damage or restore unauthorized activity's impact to its previous state. These controls are in place to correct flaws, improve processes, and guide corrective action. Corrective controls include error handling, process termination, incident management, planning, etc.
Security Control Frameworks
Your organization's criteria and requirements will determine how many controls you need to implement. Frameworks and standards assist an organization in managing security policies consistently across all its networks, systems, and devices. With frameworks, organizations can manage security controls seamlessly across different asset types using generally accepted and tested methods. Some of the security controls frameworks are mentioned below:
PCI DSS
The Payment Card Industry Data Security Standard is an information security standard developed by Visa, MasterCard, Discover Financial Services, JCB International, and American Express to ensure the security of organizations that process, store, or share credit card information.
SOC 2
The SOC 2 report ensures service providers protect their customers' data and privacy. The American Institute of Certified Public Accountants (AICPA) developed it to manage data based on five Trust Service Criteria (TSC): security, availability, processing integrity, confidentiality, and privacy. Organizations define controls, and your auditor will determine whether the controls you have in place meet the SOC 2 criteria for the categories in scope.
ISO 27001
ISO 27001 is the leading international security standard created to assist organizations of any size or industry in protecting their information through implementing an Information Security Management System (ISMS). ISO 27001 Annex A controls are defined in ISO 27002.
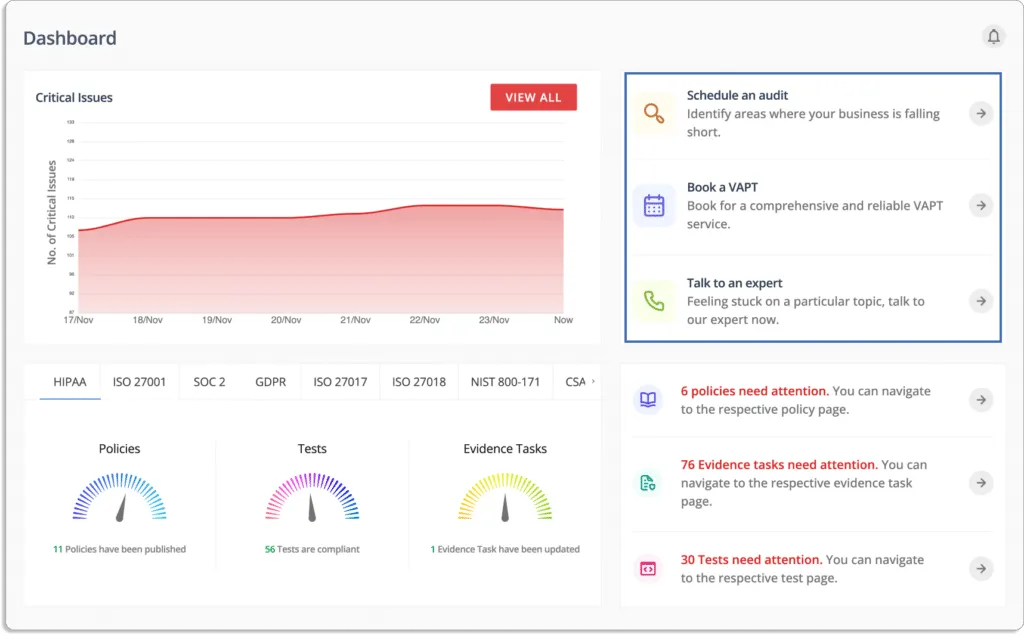
How Scrut helps to monitor your security controls
Scrut smartGRC simplifies compliance by eliminating time-consuming manual procedures and keeping you updated on the progress and overall status of your GRC program.

Scrut is a single window for all compliance-related tasks.
You can build your compliance program in minutes with a library of 50+ policies created and vetted by our in-house infosec experts.
It also gives you the flexibility to upload your policies.
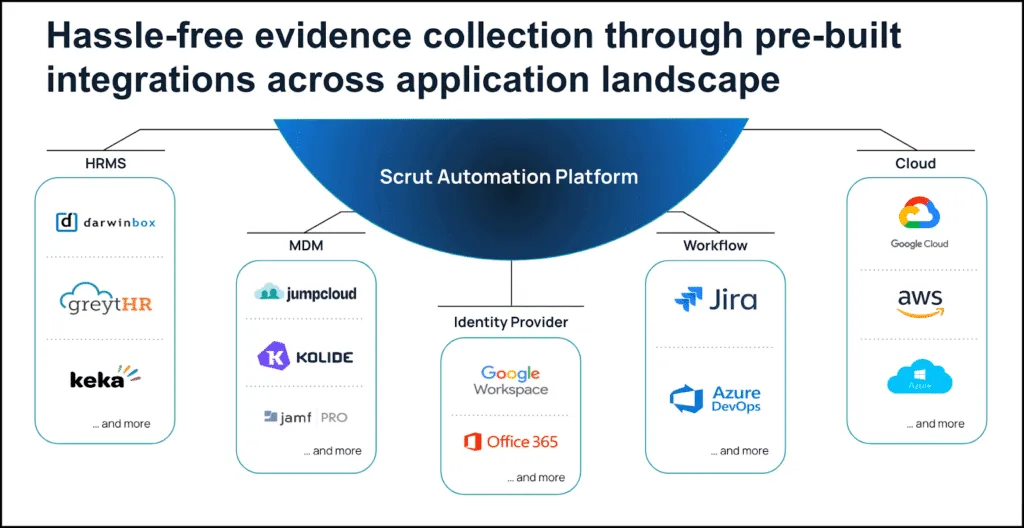
The platform integrates with your landscape to automate evidence collection and allows you to create, assign, and monitor compliance tasks. The built-in mapping to all popular information security frameworks allows you to easily manage your compliance posture.
Scrut provides a true single-window experience for ensuring compliance with multiple information security frameworks. You can map your custom controls to pre-built controls that are mapped to globally recognized frameworks. The platform supports the following frameworks, among others: SOC 2, SOC 3, ISO 27001, ISO 27701, ISO 27017, ISO 27018, ISO 22301, ISO 20000-1, GDPR, HIPAA, FedRamp, CMMC, CCPA, PCI DSS, CSA Star, CMMI - DEV, GLB, NIST 800 171.
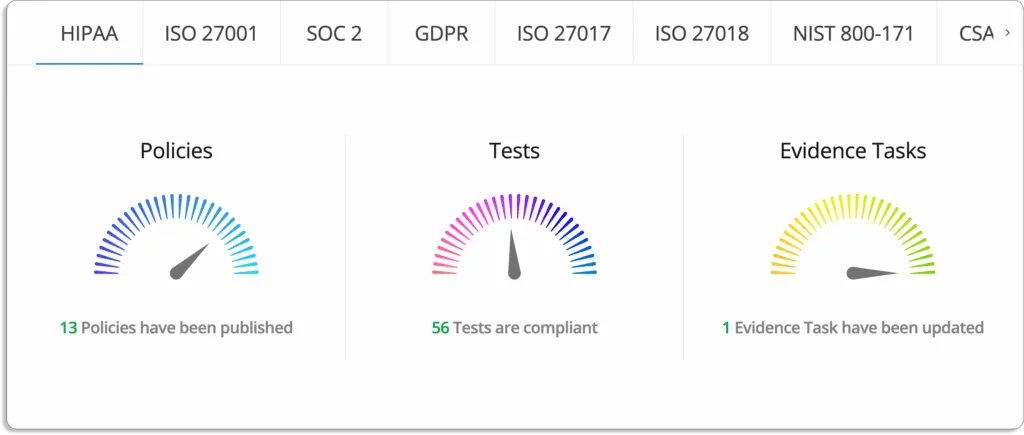
Scrut Cloud Security covers all CIS benchmarks (more than 200 controls) across popular cloud service providers (AWS, GCP, Azure, and Oracle). It continuously monitors your cloud accounts and detects misconfigurations.
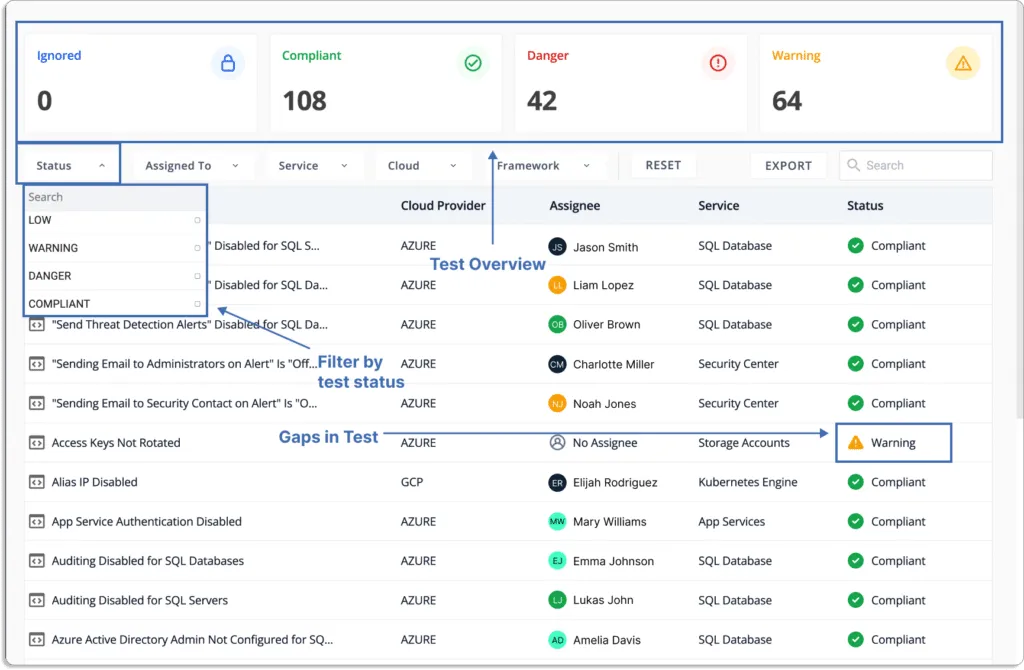
In addition, it provides actionable items that can be taken to fix issues as quickly as possible.
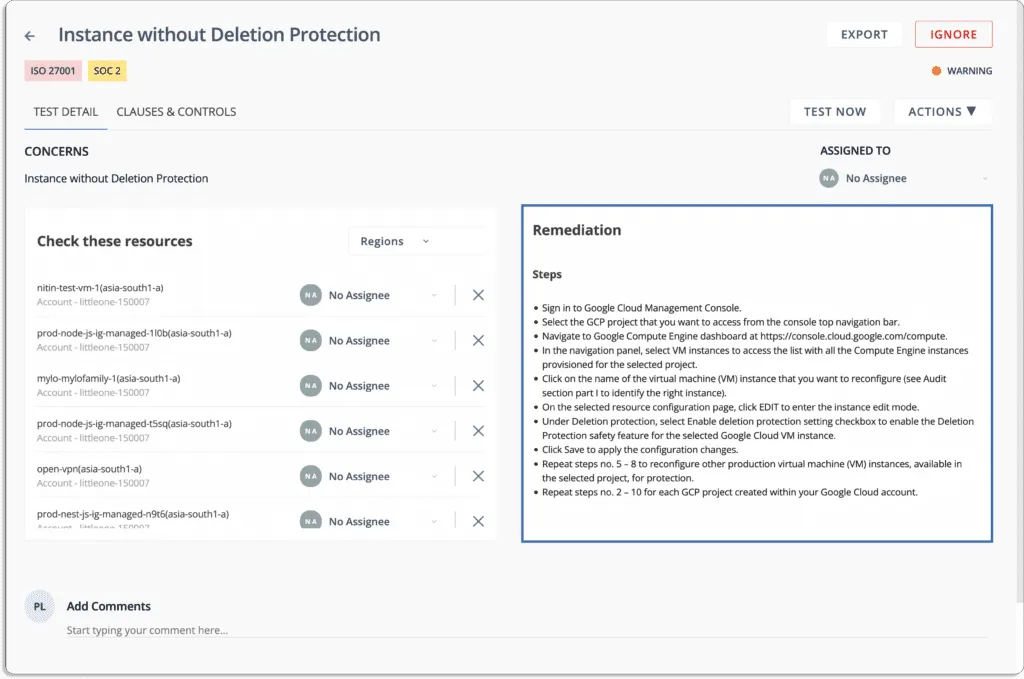
The platform identifies open hazards and critical issues, provides a single tracker to monitor what needs to be corrected and assists you in assigning and tracking activities - all from a single window. It automates and streamlines time-consuming audit tasks, from preparation to analysis.
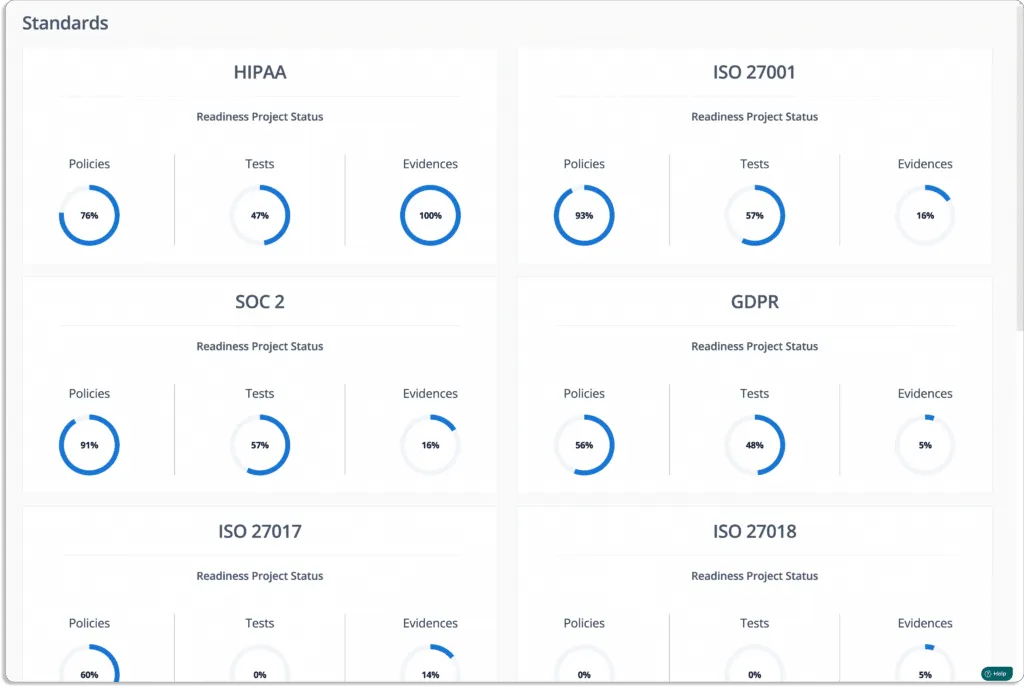
Scrut smartGRC makes evidence collection easier with integrations. It offers over 70+ integrations.
You can invite auditors to the platform and grant them access so that they can complete the audit. You have complete control over who has access to the platform. We have also established a network of pre-screened auditors and VAPT consultants who will be available to you as needed to streamline the audit process and assist you at every step of your compliance journey.
Schedule a demo with Scrut to learn how our solution can help you monitor your controls for SOC 2, GDPR, CCPA, HIPAA, and other regulations all in one place.


















