Security Compliance: How to Secure Your Business & Meet Regulations

In 2022, Ireland levied a hefty GDPR-non-compliance fine of €405 million on the Meta-owned messaging platform Instagram. It is the second-highest fine to date after Amazon’s €746 million fine in 2021.
These statistics exemplify how non-compliance with regulations can result in heavy penalties and fines for infringing organizations. This article will summarize what security compliance is and how you can secure your business and meet regulations with its help.
What is compliance in information security?
Security compliance refers to the adherence to a set of established standards, regulations, policies, and best practices designed to ensure the security and protection of sensitive data, information systems, and assets within an organization.
Maintaining security compliance requires an organization to comply with rules, regulations, policies, and procedures formed by government and non-government bodies to protect the data collected, stored, or transmitted by the organization.

Most regulatory bodies mandate periodic audits of the organizations to ensure compliance with the rules and regulations.
Moreover, if the organization is found to infringe these rules and regulations, it is subject to fines and penalties by the governing bodies.
Some examples of security compliance are
An organization must follow compliance procedures to avoid penal repercussions and secure its data. However, following compliance procedures alone does not guarantee the security of its digital assets. This is why the organization must take other IT security measures to ensure data security.
What is IT security?
IT security is the set of policies and procedures an organization implements to protect its IT assets, including hardware, software, firmware, and infrastructure, from unauthorized access. The IT security measures are not mandated by the government or any other regulatory body but are designed and followed by the organization itself.

IT security includes:
- Information security: Information security refers to protecting data or information from unauthorized access. This data can be physical data or digital data. An unauthorized person should be unable to access, change, delete, or copy the organization’s data.
- Cybersecurity: Cybersecurity protects the organization’s cyber assets, including hardware, software, firmware, and infrastructure, from unauthorized access. Securing anything connected to the internet or accessed via the internet is included in cybersecurity.
- Physical security: Physical security refers to securing the physical assets of the organization, including printed documents, the organization’s sensitive areas, and physical assets.
The goals of IT security involve three main functions popularly known as the CIA triad:
- Confidentiality: Confidentiality ensures no unauthorized person can ever access the organization’s data.
- Integrity: The integrity function of the IT security management system allows the authorized person accessing the data to know that the data has not been tampered with.
- Availability: The data should be readily available for authorized users whenever needed.
What is the difference between IT security and compliance?
So, is IT security needed even if you follow compliance? After all, IT security and compliance follow the same goal – protecting the organization’s data. Compliance does not equal security. Although compliance improves the organization’s cybersecurity posture, it does not guarantee security.
Compliance defines the minimum standard of security measures to be fulfilled by an organization. On the other hand, security measures go above and beyond the minimum requirements. They are different for every organization depending on the type of business, inventory, complexity, budget, and location. Security measures can mitigate cyberattacks on the organization.
Let’s look at some of the differences between security and compliance.
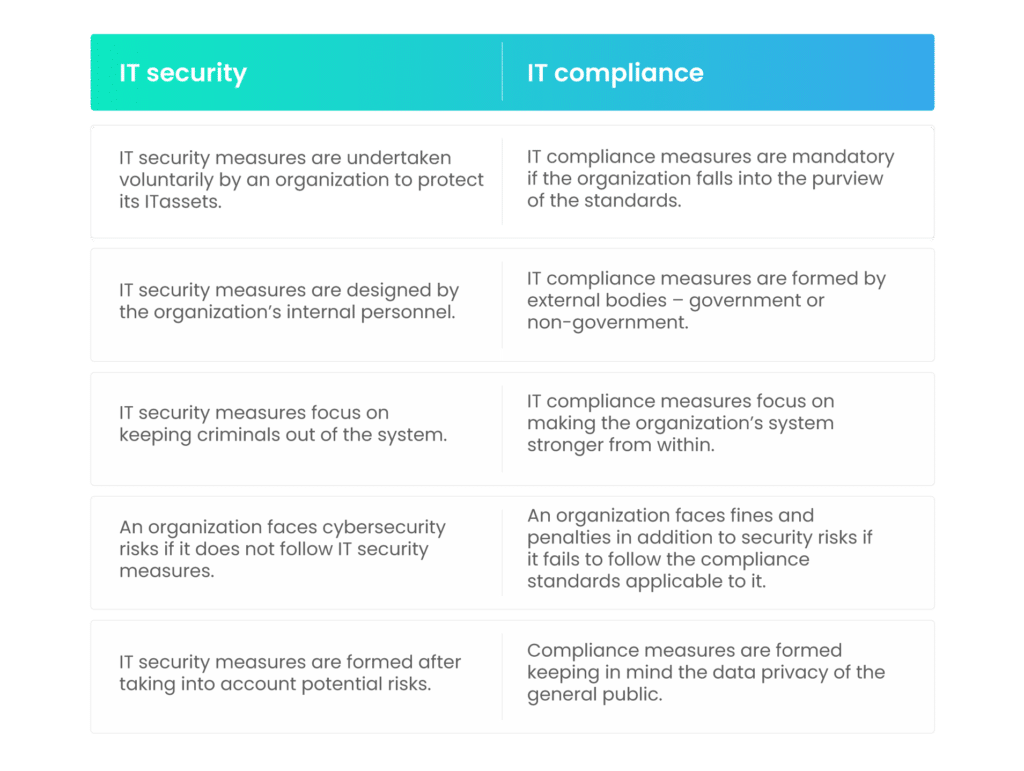
What are the similarities between IT security and compliance?
Despite their differences, IT security and compliance have many similarities.
The first similarity is in their goals. Both IT security and compliance procedures are designed to keep the bad guys out of the organization’s system while giving the good guys access to untampered data.
Secondly, both IT security and compliance play a crucial role in building trust with consumers. According to Thales, a staggering 21% of consumers discontinue their association with an organization following a data breach, with 42% requesting the deletion of their information. Considering the significant investments in both time and resources required for customer acquisition, the loss of customers due to a data breach can substantially amplify the overall cost of such an incident.
Although both IT security and compliance incur costs for the organization, they must be treated as a source of value creation. If both security and compliance costs are treated as security and compliance assets, the organization’s management can be more open to spending. Ultimately, security costs save the organization from cybersecurity incidents, while compliance costs protect the organization from fines and penalties.
What is the role of IT security compliance?
The role of IT security compliance is multifold in the organization and market as a whole. Let’s look at the basic importance of IT security compliance.
1. Preventing security breaches
The principal goal of IT security compliance is to prevent data breaches in the organization. The average cost of a data breach is $4.35 million in 2022 (IBM). Moreover, 83% of the organizations surveyed had more than one data breach. The chances of a second security breach are scarily high if you suffer one data breach.
The average cost of a data breach in organizations with high-level compliance failures has increased to a whopping $5.57 million. The IBM report clearly shows how critical compliance is for an organization.

Compliances are not only legal formalities but well-thought-out processes and procedures that can help prevent or avert data breaches. Let’s take the example of HIPAA. The Health Insurance Portability and Accounting Act (HIPAA) is an act by the US government to protect its citizens’ personal health information (PHI).
One of the HIPAA compliance regulations includes the encryption of the organization’s network. If you are covered under HIPAA, you hold, process, or transmit the PHI of US residents. If your network is not secure, you are susceptible to data breaches. Cybercriminals, also called actors, can use the vulnerability of your insecure network to enter your systems.
The ultimate goal of HIPAA compliance is to protect PHI, and if you follow compliance regulations, you can improve your cybersecurity posture.
2. Avoiding fines and penalties for infringement
Following compliance standards can help you avoid fines and penalties. Most compliance regulators impose fines and penalties for the non-fulfillment of the conditions mentioned in the act/law.
Let us continue with the above example of HIPAA. Suppose you are an organization covered under HIPAA, and you violate one or more provisions of the Act. In that case, you will be liable to pay the fines and penalties applicable to you. The following table shows the fine structure of HIPAA:
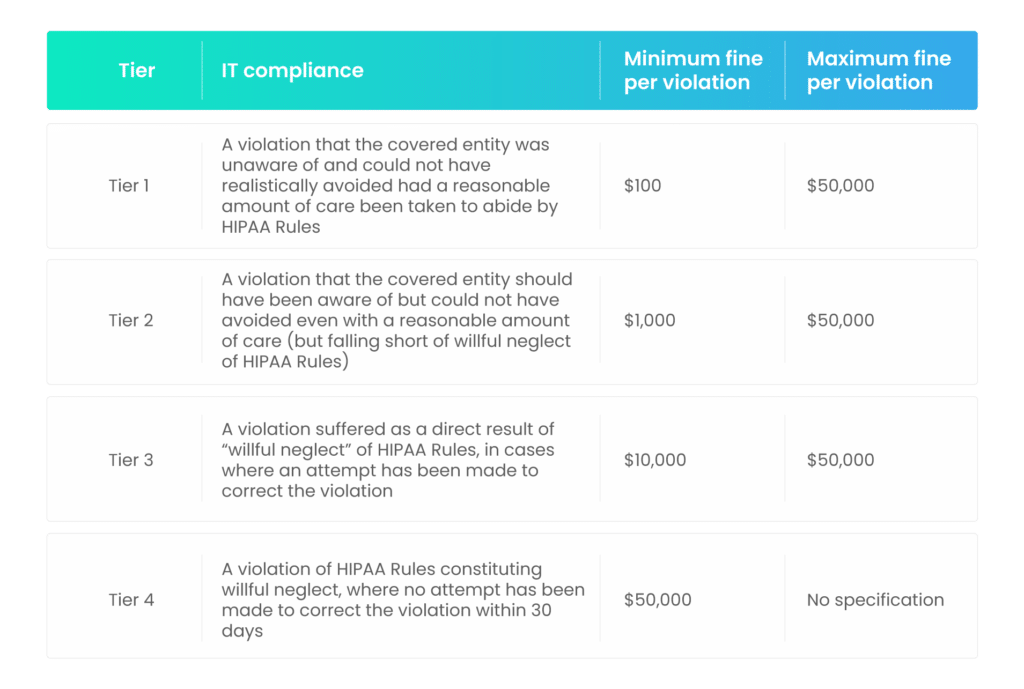
Please note that the above table depicts the fines for HIPAA violations. The fines for not adhering to other compliance laws will be different.
3. Retaining business reputation
Did you know that out of a total cost of a data breach of $4.35 million, $1.42 million was attributable to the lost business cost? The total business cost is the total of business disruption and revenue losses from system downtime, cost of lost customers and acquiring new customers, reputation losses, and diminished goodwill.
A security-compliant organization can reduce the chances of data breaches considerably. And therefore, the lost business cost can be saved. If you think compliance is expensive, consider the data breach loss you will have to bear in addition to the fines.
4. Proving competency in case of a data breach
In an unfortunate situation where your organization’s security is compromised, you will have to notify the relevant authorities. The authorities will consider the facts of the case and levy fines and penalties.
In such instances, a breached organization can present how they have followed the compliance procedures to ensure a reasonable amount of care to avoid a breach. Such details can work in your favor and save you from high penalties.
For example, if you are covered under HIPAA and your security is compromised, leading to a data breach, you can prove that you have taken reasonable steps to avoid the breach. Also, you informed the relevant parties about the breach immediately. This might put you in the Tier 1 category, considerably reducing your fines.
How do you ensure security compliance?
Ensuring security compliance involves a comprehensive and ongoing effort to meet regulatory requirements and maintain a secure environment. Here are steps to help you ensure security compliance:
1. Design a detailed compliance plan
With every passing year, more and more managers realize the importance of cybersecurity as a part of overall risk management.

Additionally, most cyber and business leaders agreed that cyber-resilience governance must be integrated into their business strategy to increase its impact. Most organizations are aware of the compliances they need to follow; however, they are not sure how to follow them. Even IT employees are sometimes confused about the procedural aspects of the compliance process.
Form a detailed plan that includes the roles and responsibilities of every employee and the managerial people. There must not be any overlaps regarding the duties of every person.
The plans must include the procedures to be followed in case of a breach. A well-formed plan can reduce the time it takes to restart the business after the breach.
2. Train your employees
Verizon reported that 82% of the breaches involved the human element. It includes using stolen credentials, phishing, misuse, or simply an error. Moreover, 2.9% of employees may actually click on phishing emails. Stolen or lost devices, including mobile phones, laptops, and tablets, result in many security incidents in the organization.

Even if you have a top-grade plan, communicating it to the employees is very important. Moreover, your employees must receive expert training on how to behave online. They must be aware of the latest methods threat actors use to protect themselves and the organization. Compliance security awareness training is one of the most critical aspects of the organization’s security compliance program.
3. Update your software regularly
Do you remember the Equifax breach of 2017? Let us recount the facts of the breach to understand the importance of updating or patching. Equifax was one of the thousands of users of Apache Struts, an open-source framework for creating enterprise Java applications.
A vulnerability was found, and a patch was issued for Struts in March 2017. On March 9, the administrators of Equifax asked an employee to apply the patch to the affected systems; however, they didn’t. On March 15, a scan was carried out to check the updates, which failed to detect the vulnerability.
The initial attack began on March 10 when the Struts vulnerability breached the web portal. On March 13, the attackers began moving into the other parts of the Equifax systems. After a series of errors and omissions, it was discovered that the data of 143 million users were exposed – more than 40% of the US population.
The above incident proves how important it is to update your software regularly. Security patches must be applied as soon as they are released, as they cover known vulnerabilities.
4. Monitor regularly
It is critical that you monitor your computer systems, your partner’s/contractor’s systems, and the adversaries’ scenario.
Continuously monitoring your systems can help you identify threats sooner. You can patch your vulnerabilities to stop the threat actors before they can cause more damage.

The third part of the monitoring system is the cyber threat landscape. If you are monitoring the threat landscape deeply, you will be able to identify the threats that can affect your organization. You can remain vigilant of the situation and change your cyber resilience posture to protect yourself.
5. Implement a zero-trust model
The cost of a data breach of critical infrastructure was $4.82 million – $1 million more compared to the cost of other industries (IBM). However, 79% of the critical infrastructure organizations did not employ zero trust architecture.
In a zero-trust model, employees are only given access to the data required to fulfill their duties. It is also called the model of least privilege. The data is divided into sections and segregated to ensure that the right to access this information is limited.
A zero-trust model can reduce the attack surface and prevent cyber attacks. On the compliance side, the zero-trust model is adopted more to fulfill various regulations’ requirements.
6. Carry out compliance and internal audits regularly
Compliance audits are a way to verify adherence to regulatory guidelines for an organization. Many regulations require periodic audits, while some organizations opt for voluntary compliance audits. The type and depth of compliance audits vary from organization to organization depending on factors such as the business and location of the organization, the type of data it handles, and the nature of the government regulations.

The audit report is submitted to the authorities responsible for testing compliance. It is used as a base to levy penalties and fines if the organization violates the laws.
Automate compliance management
As a result of an increase in cyber attacks, more and more regulations and frameworks are being levied to ensure data privacy. Sometimes, it becomes difficult to maintain all the formats without breaking the law. Oftentimes, organizations make errors in understanding or implementing the laws resulting in penalties.
One way to manage compliance is to automate manual procedures. Many compliance software available in the market can effectively reduce the time spent by employees on compliance requirements. By doing a thorough cost/benefit analysis, many organizations realize that the cost of automation is much less than the amount of penalty to be paid in case of non-compliance.
Secondly, an organization can employ an external agency to carry out compliance and risk management activities. This reduces the burden on the organization, leaving the employees available for more productive tasks.
How can Scrut help you implement robust security compliance?
Scrut is a comprehensive solution for all your compliance needs. It provides a variety of services, including, but not limited to, GRC management, CAASM, cloud security, and risk management.
Scrut can automate continuous risk and compliance management tasks so that you and your employees can focus on more important activities. You can receive notifications and alerts about the areas of your business that need attention. Scrut also helps you in external compliance audits so that you can fast-track your compliance.
If you have any questions about how Scrut can help you achieve your compliance goals, you can book an appointment with our experts.
FAQs
1. What is regulatory compliance in security?
Regulatory compliance in security refers to the adherence to the rules and regulations applicable to the organization. The government or non-governmental bodies can set up these frameworks and regulations.
2. What are the eight steps to ensure security compliance in your organization?
The following are the eight steps to ensure security compliance in your organization:
– Design a detailed compliance plan
– Train your employees
– Update your software regularly
– Monitor regularly
– Implement a zero-trust model
– Carry out compliance and security audits
– Implement strong GRC policies
– Automate compliance management
3. What is the fundamental difference between security and compliance?
The primary difference between IT security and compliance is their origin. IT security procedures are formed internally by the organization. On the other hand, compliance regulations are formed and implemented by external regulatory bodies.


















