Ahead of the curve: Preparing for NHS MFA Multi-Factor Authentication policy

In the healthcare industry, the reliance on traditional authentication methods poses a significant security risk, jeopardizing the confidentiality and integrity of patient data. Cyber threats targeting healthcare organizations continue to escalate, with breaches potentially resulting in dire consequences for patient care and safety.
The recent mandate by the NHS (National Health Services) security manual for all entities to implement MFA offers a crucial solution to address the vulnerabilities inherent in traditional authentication methods.
By requiring multiple verification factors for access, MFA significantly enhances security, mitigating the risk of unauthorized access and data breaches. This proactive approach not only protects patient confidentiality but also upholds the commitment to ensuring the well-being of individuals relying on healthcare services provided by the NHS.
In this blog, we'll focus on the recent mandate by the NHS for all entities to implement MFA.
Why Multi-Factor Authentication matters in healthcare
Cybersecurity reports paint a sobering picture of the prevalence and impact of credential-based breaches in the healthcare industry.
According to the "2023 Healthcare Cybersecurity Report" published by a leading cybersecurity firm, credential-based attacks accounted for over 60% of all security incidents reported by healthcare organizations in the past year. These attacks encompassed various tactics, including phishing, brute force attacks, and credential stuffing, highlighting the diverse range of threats facing the sector.
Furthermore, the report revealed that the average cost of a credential-based breach in healthcare exceeded $5 million, encompassing expenses related to incident response, regulatory fines, legal fees, and reputational damage. Beyond the financial implications, such breaches also jeopardize patient confidentiality and trust, underscoring the urgent need for robust security measures like MFA.
MFA emerges as a critical safeguard in the healthcare industry's ongoing battle against cyber threats. By adding an extra layer of security and mitigating the risks of credential-based breaches, MFA helps protect sensitive patient data, uphold regulatory compliance, and preserve the integrity of healthcare systems.
The latest NHS cyber security manual requirement follows United States directives to enhance the country's cybersecurity. NHS cyber security measures help safeguard sensitive healthcare data and uphold the integrity of medical services.
NHS MFA policy requirements and implications
As healthcare organizations strive to enhance their cybersecurity posture, implementing MFA emerges as a crucial first step toward fortifying defenses and safeguarding sensitive patient data.
The NHS MFA policy mandates the adoption of Multi-Factor Authentication across all systems and applications handling patient data. However, the implementation of MFA within the NHS presents several challenges and complexities due to the organization's sheer size, diversity of systems, and legacy infrastructure.
Healthcare providers must navigate intricacies such as compatibility issues, user training, and resource constraints while ensuring seamless integration and minimal disruption to clinical workflows.
NHS policy recommended MFA methods
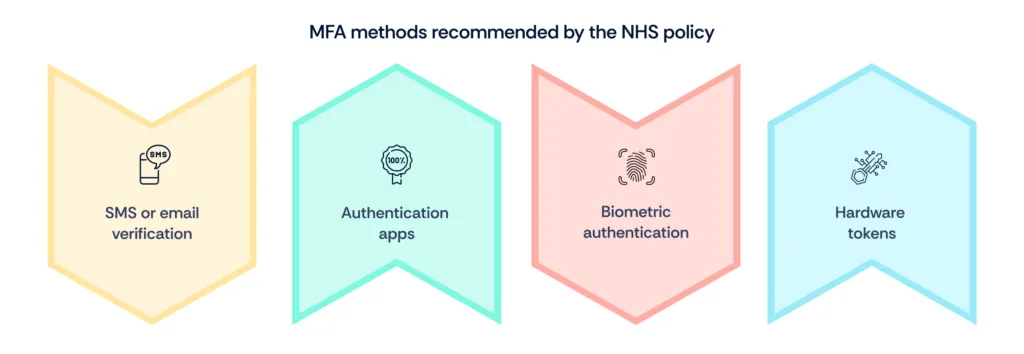
Deploying MFA within the NHS requires careful consideration of various factors, including feasibility, flexibility, and user experience.
The NHS policy recommends several MFA methods, each offering varying degrees of feasibility and flexibility:
- SMS or email verification: This method involves sending a one-time passcode to the user's mobile phone or email address. While convenient, SMS and email-based verification may pose security risks due to the potential for interception or account takeover.
- Authentication apps: Dedicated authentication apps, such as Google Authenticator or Microsoft Authenticator, generate time-based or event-based passcodes for secure authentication. Authentication apps offer greater security compared to SMS or email verification and are suitable for users without reliable internet connectivity.
- Biometric authentication: Biometric authentication methods, such as fingerprint or facial recognition, leverage unique physiological traits for identity verification. While biometrics offer strong security and user convenience, they may present interoperability challenges across different devices and platforms.
- Hardware tokens: Hardware tokens, such as smart cards or USB security keys, provide an additional layer of security by generating one-time passcodes or cryptographic signatures. However, the deployment and management of hardware tokens may entail higher costs and administrative overhead.
Practical tips for MFA implementation in NHS organizations
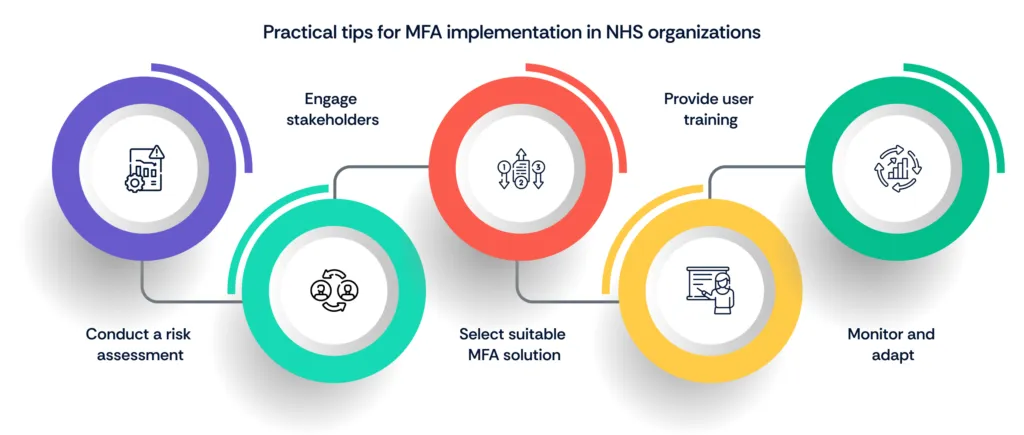
- Conduct a risk assessment: Begin by conducting a comprehensive risk assessment to identify security vulnerabilities and user authentication requirements specific to NHS systems and applications.
- Engage stakeholders: Involve key stakeholders, including IT personnel, clinical staff, and administrative teams, in the decision-making process to ensure buy-in and support for MFA implementation.
- Select suitable MFA solutions: Evaluate the feasibility, security, and user experience of different MFA methods recommended by the NHS policy and choose solutions that align with organizational needs and resources.
- Provide user training: Offer training and support to educate users on the importance of MFA, how to enroll and use MFA methods effectively, and best practices for safeguarding authentication credentials.
- Monitor and adapt: Continuously monitor MFA usage and effectiveness, gather feedback from users, and refine MFA policies and procedures as needed to address emerging threats and user requirements.
Limitations of MFA and continuous improvement
While MFA provides an additional layer of security, it is not without limitations. Threat actors have demonstrated the ability to bypass MFA through various techniques, such as phishing attacks, social engineering, and compromised devices. Moreover, MFA does not address vulnerabilities inherent in the underlying systems or protect against insider threats with legitimate credentials.
To address these shortcomings, healthcare organizations must embrace a culture of continuous improvement and adaptation in their cybersecurity strategies.
This entails implementing:
- Advanced threat detection mechanisms
- Proactive threat hunting, and
- Robust incident response protocols to detect and mitigate emerging threats
Moving beyond MFA: Towards zero trust security
While MFA represents a critical step towards enhancing security, healthcare organizations must adopt a comprehensive approach that goes beyond traditional perimeter-based defenses.
Embracing Zero Trust principles is paramount today when adversaries continually seek new avenues to exploit vulnerabilities and evade detection.
Zero Trust Security challenges the conventional notion of trust based on network boundaries and emphasizes continuous verification and least-privileged access controls. By adopting a Zero Trust mindset, healthcare organizations can strengthen their security posture, mitigate insider threats, and protect against sophisticated cyber attacks targeting sensitive patient data.
Conclusion
In conclusion, MFA implementation represents a tangible investment in patient safety and data security, reflecting the NHS's commitment to delivering high-quality healthcare in an increasingly digital terrain.
As we navigate the complexities of healthcare cybersecurity, it is imperative for NHS organizations to embrace MFA as a foundational measure while continuing to scrutinize and innovate their security strategies to stay ahead of emerging threats.
For organizations seeking guidance and support in implementing robust MFA solutions and evolving their cybersecurity posture, partnering with Scrut can provide invaluable expertise and resources to navigate this critical journey with confidence.
Frequently Asked Questions
1. What is Multi-Factor Authentication (MFA), and why is it important for NHS organizations?
Multi-Factor Authentication (MFA) is a security measure that requires users to provide two or more verification factors to access an account or system. This typically includes something the user knows (like a password), something they have (such as a smartphone or security token), or something they are (like a fingerprint or facial recognition). MFA is crucial for NHS organizations to strengthen their security posture and protect sensitive patient data from unauthorized access or breaches.
2. How does MFA enhance security compared to traditional authentication methods?
MFA adds an extra layer of security beyond just a username and password, making it significantly harder for unauthorized individuals to gain access to systems or accounts. Even if a hacker manages to obtain a user's password, they would still need access to the additional verification factor, which could be a physical device or biometric data. This drastically reduces the risk of unauthorized access, data breaches, and identity theft.
3. What are the key steps involved in preparing for MFA implementation within NHS systems?
a. Conduct a comprehensive assessment of current authentication methods and security protocols.
b. Identify suitable MFA solutions that align with NHS security requirements and regulations.
c. Develop a detailed implementation plan, including timelines, resource allocation, and stakeholder involvement.
d. Provide thorough training and education to staff members on the importance of MFA and how to use it effectively.
e. Perform thorough testing and evaluation of the chosen MFA solution before full deployment.
4. What are the potential challenges or obstacles NHS organizations may face during the transition to MFA?
a. Resistance to change from staff members accustomed to traditional authentication methods.
b. Integration complexities with existing systems and applications.
c. Budgetary constraints for acquiring and implementing MFA solutions.
d. Ensuring compatibility and usability across various devices and user groups.
e. Addressing concerns about privacy and data security related to biometric authentication methods.
5. How can NHS staff and administrators best support the adoption of MFA to ensure smooth integration and user acceptance?
a. Provide clear communication and training resources to educate staff about the benefits of MFA and how to use it.
b. Offer support channels for staff members to seek assistance or address any concerns during the transition.
c. Encourage feedback and input from users to identify any usability issues or areas for improvement.
d. Lead by example and demonstrate the importance of MFA by consistently following security protocols.
e. Recognize and reward staff members who actively embrace and promote MFA best practices within the organization.


















