Noetic Alternatives

Noetic is a continuous cyber asset management and control platform that provides full-stack visibility into your organization’s assets. The tool takes a proactive approach to manage cyber assets and controls, enabling security teams to see, understand, and optimize their cybersecurity posture.
It is not the only CAASM tool available; other CAASM tools will meet your requirements better. If you’re looking for Noetic alternatives, this article will be useful. To help you save time, we’ve compiled a list of the top 7 Noetic alternatives.
Noetic combines top-down visibility into an organization’s business applications and processes with bottom-up visibility, then automates security monitoring and improvement across the entire cyber environment. With pre-built agent-less connectors, the platform breaks down the silos of existing security tools, resulting in a unified view of all assets and their current state across cloud and on-premises, highlighting coverage gaps and policy violations. The platform maps the cyber relationship between the assets of the organizations in order to identify security coverage gaps. The tool improves vulnerability management capabilities by providing a consistent view of your constantly changing security environment, allowing you to make decisions based on comprehensive and real-time data.
Key features
The key features of Noetic are listed below:
- Noetic easily integrates with and enhances existing endpoint security tools, providing enterprises with next-generation visibility into their security posture.
- Noetic enhances vulnerability management capabilities by providing a consistent view of your ever-changing security environment.
- The platform imports results from existing tools such as Rapid7, Tenable, and Qualys, allowing security teams to identify gaps, prioritize work based on a thorough understanding of asset ownership and context, and automate scanning and remediation.
- It integrates with identity and access management (IAM) systems such as Okta, AWS IAM, and others to create a consolidated graph that describes people, accounts, roles, permissions, and user activity about the assets and resources that you are safeguarding.
- Noetic’s dashboards enable teams to see the big picture by identifying and prioritizing critical security issues across endpoints, users, cloud systems, and others.
- Through Noetic’s orchestration and automation engine, teams can continuously find and fix unsecured or misconfigured assets, restoring them to a pre-approved state based on internal security policy or external control frameworks such as NIST or CIS.
Drawbacks
The drawbacks of Noetic are as below:
- The platform does not include pre-built dashboards or queries that output to business intelligence tools.
- The tool lacks automated prompts for security chaos engineering experiments.
Best 7 Alternatives
Now, let’s discuss the best 7 Noetic alternatives, starting with our platform, Scrut.
1. Scrut
Scrut CAASM enables you to gain visibility into your cyber assets, empowering IT and security teams to overcome cyber asset vulnerability challenges and establish a solid foundation for all security activities.
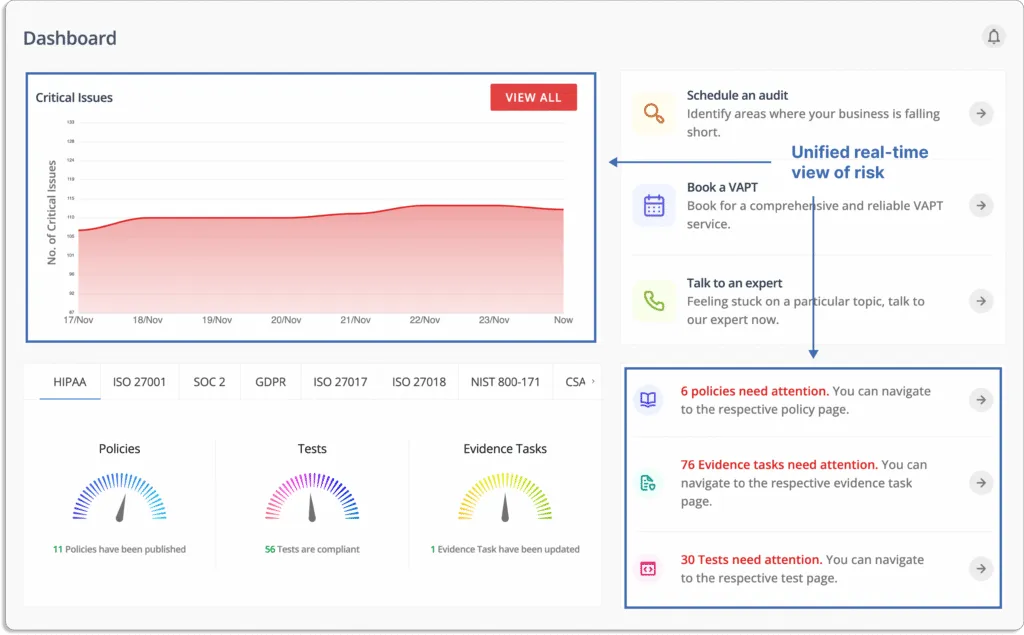
Scrut’s interactive visual asset map allows you to drill into asset details, identify threat areas, and significantly reduce your cyber attack surface. Keep both asset and relationship data for deeper security insights based on context. Scrut assists you in consolidating and standardizing asset data across distributed, multi-cloud environments. You can execute queries to find information from various cloud providers, applications, and services.
The platform generates a complete and up-to-date asset inventory automatically. It gives you a unified view of all cloud entities, allowing you to identify critical business assets and prioritize risks across your hybrid and multi-cloud environments. The tool provides complete visibility into your external and internal attack surfaces, allowing you to improve security control coverage and initiate custom and automated response actions.
Scrut supports the following frameworks: SOC 2, SOC 3, ISO 27001, ISO 27701, ISO 22301, ISO 20000-1, GDPR, CMMC, CCPA, PCI DSS, CSA Star, CMMI – DEV, CMMI – SVC, HIPAA, GLB, NIST 800 171, and others.
With seamless integrations across your application landscape, you gain a unified, real-time view of risk and compliance, providing the contextual insight required to make strategic decisions that keep your organization secure and earn the trust of your customers, partners, and employees.
Pros
- Scrut assists you in discovering and consolidating all of your cyber assets, regardless of where they are located. Get a centralized view of your cyber assets and prioritize risk by identifying business-critical assets.
- Monitor your cyber asset landscape continuously to identify issues affecting business-critical assets and the overall infrastructure.
- Users can gain complete visibility into external and internal attack surfaces, allowing them to improve security control coverage and initiate custom, automated response actions.
- Scrut assists you in consolidating and normalising asset data across scattered, multi-cloud setups. Run queries to find information from a variety of cloud providers, applications, and services.
- You can visualize the complex relationships between your cyber assets to identify security issues in your environment quickly.
- With Scrut’s interactive visual asset map, you can drill down into asset details, identify threats, and drastically reduce your cyber attack surface
- The platform provides the visibility required to understand your information security activities’ status, efficacy, and impact on your compliance posture. It provides a centralized repository for all information security tasks and artefacts, allowing you to close compliance gaps in real time and stay compliant 24*7.
- You can invite your auditor to participate in various audit tasks on the platform. Auditors can easily find all audit-related artefacts on the platform, allowing them to complete audits more quickly.
Customer Rating
- G2 – 5/5

2. JupiterOne
JupiterOne CAASM empowers your security teams to create a comprehensive asset inventory, gain a centralized view of all cloud entities, identify critical business assets, and prioritize risk across hybrid and multi-cloud environments. It assists businesses in consolidating cyber asset data from all of their tools into a unified view that serves as the foundation for all security activities. The platform provides your team with complete visibility into all cyber assets. The tool integrates with your cloud infrastructure, DevOps pipeline, and security tooling to collect reliable asset data in a single location. This comprehensive, unified view enables you to manage cyber assets across hybrid and multi-cloud environments properly.
Pros
- The platform can quickly visualize relationships in a digital environment by offering automated reports and evidence collection.
- It supports JSON, making it simple to create queries and run them quickly.
- It offers security categories to maintain secure environment and provides efficient observability of IT assets in your organization to control the attack surface.
Cons
- The graphical mapping does not appear to be the actual data result.
- Users cannot modify controls on the compliance page.
- Some desirable data elements are not pulled into JupiterOne.
Customer Rating
- G2 – 5/5
3. Axonius
Axonius CAASM provides full visibility into the external and internal attack surface to improve security control coverage and trigger custom, automated response actions by aggregating, normalizing, and deduplicating data from IT and security solutions. The platform’s asset inventory is constantly updated based on information from hundreds of previously deployed sources. The Axonius query wizard lets you quickly detect surface coverage gaps, validate policies and controls, and conduct investigations. It provides automated trigger customized actions whenever an asset deviates from policies.
Pros
- Axonius allows users to aggregate csv reports while also making API calls to a variety of data sources. For instance, a user can obtain records from antivirus, active directory, and vulnerability in a single report.
- The tool generates dashboards with all required data metrics, sends alerts about all security issues, and efficiently identifies security controls on endpoints.
Cons
- Sometimes the connectors don’t sync up properly.
- There is no way to organize the metric cards because they are sorted by creation date.
Customer Rating
- Capterra- 5/5
4. Sevco
Sevco is a cloud-native CAASM platform that improves your security posture and IT processes by automatically aggregating your inventory sources to provide a comprehensive, accurate, and real-time view of your asset ecosystem. The platform automatically aggregates inventory data from various sources to provide a unified and continuous view of your inventory. Sevco’s cloud-native platform auto-scales automatically and instantly, whether you’re adding new data sources or acquiring an entire organization. The tool identifies gaps and vulnerabilities in the deployment and coverage of security tools and provides appropriate risk mitigation strategies to protect your system from hackers.
Pros
- The tool provides feedback on ways to improve your organization’s overall security.
- Users can easily locate all assets and determine whether or not all security software is installed and operational.
Cons
- The tool needs to catch up on data sources and reporting features.
- The platform doesn’t provide customizable reporting.
Customer Rating
- Gartner- 4.9/5
5. Brinqa
Brinqa is a cyber risk management platform that comprehensively views your IT and security ecosystem. Through a unified asset inventory that consolidates and enriches profiles per asset, Cyber Risk Graph improves security control coverage and establishes definitive ownership. Strengthen your security posture by regularly evaluating cyber hygiene across your attack surface to identify security control coverage gaps and report on security program effectiveness. It provides a single platform for establishing a single source of truth for assets and their vulnerabilities, enabling multiple use cases to reduce your attack surface.
Pros
- The platform provides in-depth information on cyber security risks.
- Brinqa lets you quickly aggregate scan results and add contextual data to create visually appealing VM dashboards.
Cons
- The features are costly compared to others software.
Customer Rating
- G2- 4.6/5
6. Panaseer
Panaseer CAASM platform integrates data from your vulnerability, endpoint, and other security tools to provide complete visibility of your asset inventory and identify vulnerability control gaps. The platform allows you to efficiently prioritize remediation campaigns, allowing you to focus on fixing the vulnerabilities that pose the greatest risk to your business.
Pros
- The platform includes advanced risk management capabilities that assist users in identifying and blocking risks before they occur.
- It provides real-time visibility into our systems and security controls, ensuring they are properly deployed and operating.
Cons
- The platform stores data about systems, users, and their accounts on third-party, public clouds, which can cause data security and legal compliance problems.
- Limited integration capabilities and public cloud storage cause issues with large amounts of data, causing the product to be slow.
Customer Rating
- Gartner- 4.2/5
7. Lansweeper
Lansweeper organizes and contextualizes technology asset data so that it can be used in a variety of business scenarios. The platform’s pre-built and customizable dashboards assist you in understanding patch status, vulnerability exposure, security compliance, software licencing, hardware warranty information, and more.
Pros
- You can view a detailed history of public and private messages sent to customers and technicians.
- The tool allows users to track user support requests, inventory and report on our devices, and even remotely run scripts and commands.
Cons
- It requires administrative privileges to collect data, which raises security concerns.
- There is no support for Apple/Mac.
Customer Rating
- G2- 4.5/5


















