NIST 800 Automation Tools

NIST 800 represents the desired state for cyber resilience. Businesses can benefit from NIST by implementing a subset of its controls. NIST 800-53 and NIST 800-171 are the most crucial NIST 800 requirements.
Here, we will cover the top 11 NIST 800 automation tools.
Intro
NIST’s 800 series publications, first published in 1990, present information that includes NIST’s cybersecurity guidelines, recommendations, technical specifications, and annual reports. NIST 800-53 and NIST 800-171 are the two specifications in focus of NIST 800. NIST 800-53 establishes security controls and privacy controls for businesses and organizations, except those involved in national security. The purpose of NIST SP 800-171 is to protect sensitive information residing with third parties, government contractors, or service providers.
Who must comply with NIST 800 series requirements?
Unless contractually obligated, entities outside the United States Federal Government may voluntarily adopt NIST’s SP 800-series publications. Compared to other standards, such as CIS and general security controls, NIST 800-53 and NIST 800-171 have many guidelines and cover many information security systems.
Senior management with prior experience with NIST may be more inclined to implement it in their organization. However, while NIST represents the desired state for cyber resilience, achieving it may not always be feasible. Instead, businesses can benefit from NIST by implementing a subset of its controls while avoiding those that aren’t as applicable or practical to implement.
Challenges in NIST 800 Compliance
Every NIST standard comes with its own set of challenges. With a focus on information security safeguards, NIST 800-171 primarily used to protects controlled unclassified information of non-federal systems and organizations. On the other hand, NIST SP 800-53 approaches cybersecurity from a low level; it uses precise instructions on applying particular controls.
- Integrating NIST 800 into Your IT Security Program:
NIST 800 is an evolving document, with each revision introducing updated requirements. NIST SP 800-53 focuses on the control aspect of risk management programs, with each control classified as low, moderate, or high impact. They are also divided into 18 distinct categories. The idea is that by categorizing controls, organizations can streamline control selection and specification.
Some examples of categories mentioned in NIST 800-53 include accountability and audit of access control, management of awareness and training configuration, identification and authentication in contingency planning, program administration, risk evaluation, etc.
- Ambiguity in the compliance requirements:
NIST 800-171 contains many ambiguous security controls. As a result of this ambiguity, there is a risk of breach of contract, and potentially false claims act liability for failing to implement these controls when required. Although there is no foolproof solution, NIST 800-171 is mapped to NIST 800-53, which provides more detailed information. Furthermore, most of the controls in NIST 800-171 map to only a few of the “control enhancements” categories in each control in NIST 800-53. Contractors may reasonably conclude that any control enhancements that are not expressly mapped are not required, thereby reducing the burden and ambiguity associated with implementing NIST 800-171.
How can automation help with these challenges?
Automation tools assist you in gaining the visibility you need to stay safe from threats and effectively communicate the impact of risk on critical business activities, all while documenting everything you need to pass the audit.
Automation tools for NIST 800 Compliance
There are many NIST 800 automation tools available in the market. Let’s discuss top 11 automation tools.
1. Scrut
Scrut is a risk-first GRC software solution that assists you with NIST SP 800-171 and NIST 800-53 framework controls. The tool allows you to continuously monitor your controls for 24X7 compliance and simultaneously manage multiple compliance audits and risks, all from a single window.

Scrut automatically compares your cloud configurations to 200+ cloud control across CIS benchmarks to ensure a strong information security posture.
You can use Scrut’s policy library, which includes more than 50 pre-built policies. Furthermore, you can customize these policies using the built-in editor and have them reviewed by our in-house compliance experts.
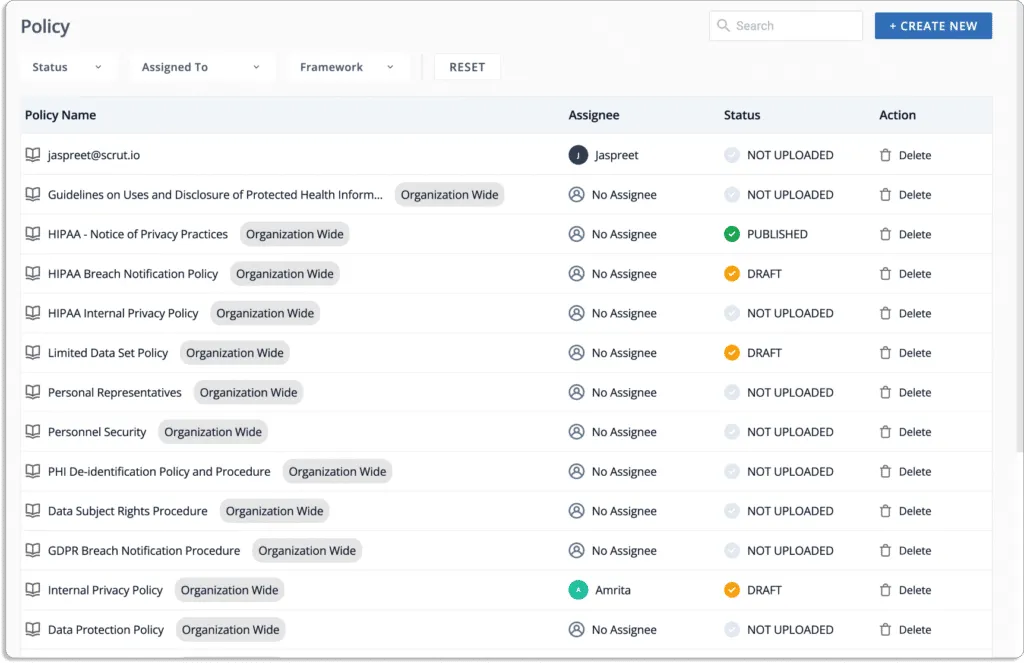
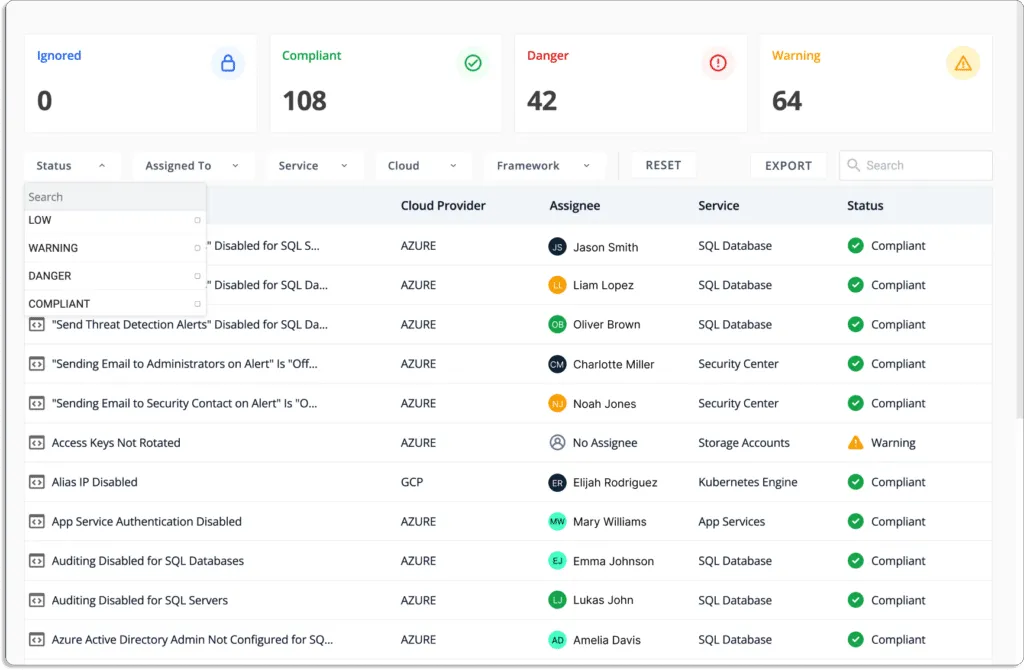
The platform displays the status of each cloud resource. And if any cloud resource does not meet your security requirements, you will see one of the following statuses:
- Danger – Issues that require immediate attention.
- Warning – Proceed to these after addressing the “danger” issues.
- Low – These are low-priority risks that can be dealt with later.
Scrut Risk Management module will identify risks throughout your environment. The tool analyzes your ecosystem for risks across the code base, infrastructure, applications, vendors, and employee access to automate risk identification.
Scrut prepares your risk register in minutes suitable for NIST 800. You can use the risk library that has already been pre-mapped. You can begin your risk assessments in minutes by eliminating the time spent creating and mapping risks and threats.
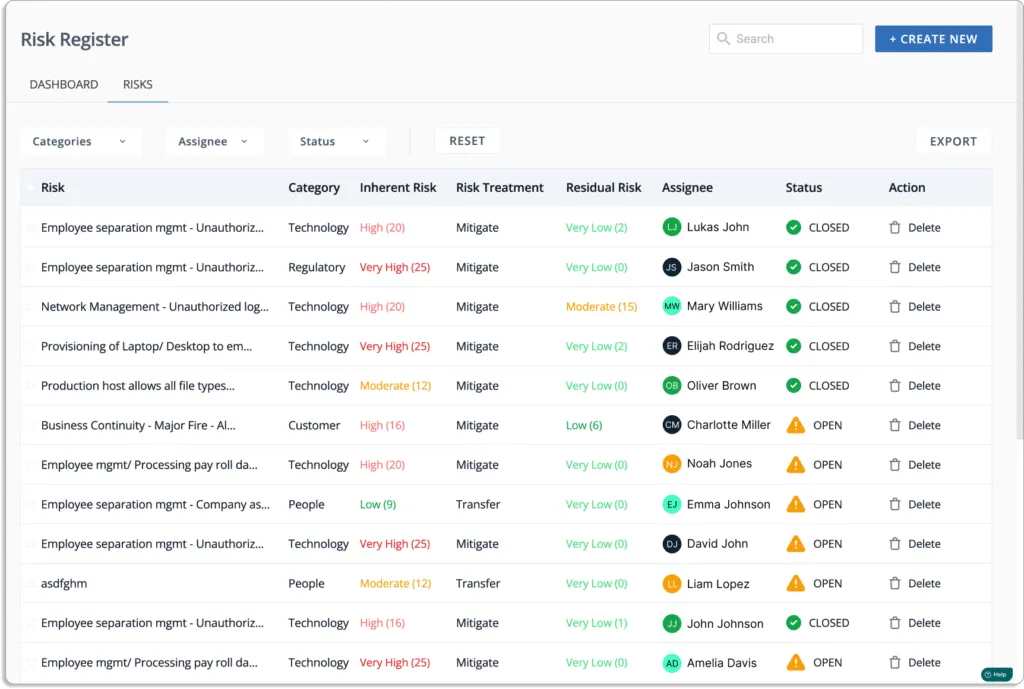
Scrut automates risk assessment by constantly monitoring your risk posture via continuous risk monitoring.
Features
- Easily manage evidence of compliance: The platform includes a module called Trust Vault, where customers can see your compliance posture in real-time without manual effort. Create and share an auto-populated company-branded security page with Scrut’s Trust Vault to highlight your information security posture. All evidence documentation required to demonstrate compliance can be stored and managed.
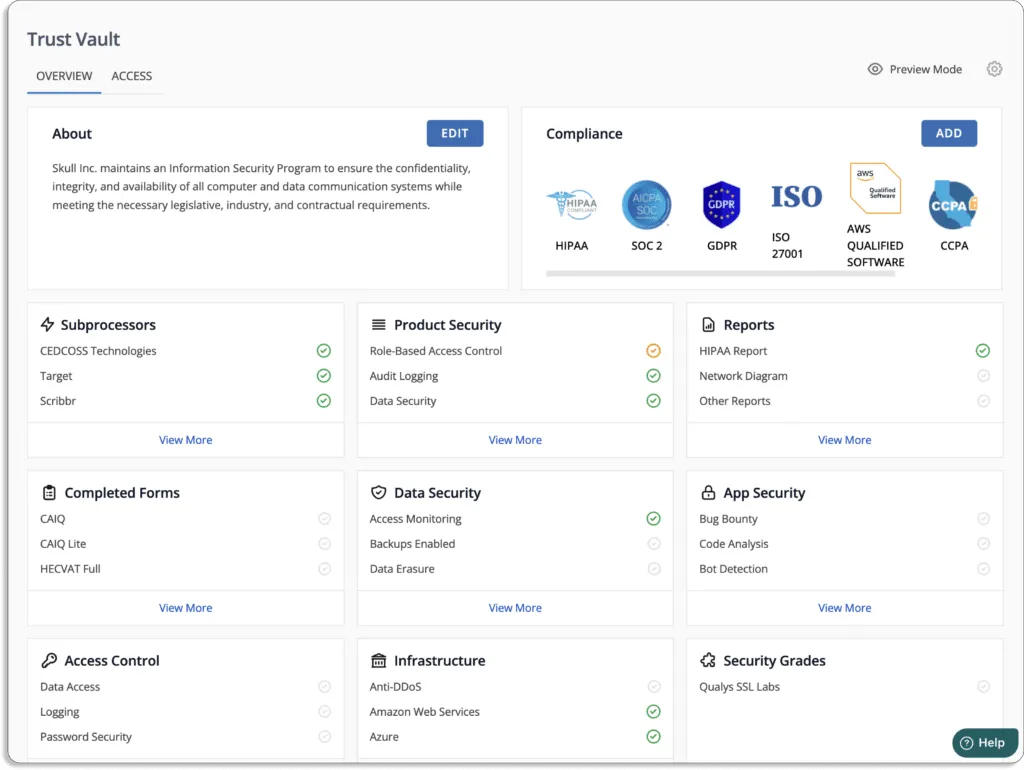
- Allows you to keep track of all compliance activities in one location: Scrut provides the visibility required to comprehend the status, efficacy, and impact of your information security activities on your compliance posture.

- A smooth auditing procedure: Scrut streamlines and automates time-consuming audit tasks, from planning to analysis. The platform streamlines collaboration with your auditors, increasing accountability and accelerating the completion of information security tasks while reducing manual work by up to 75%. It streamlines every audit-related task from audit readiness to examination. Furthermore, the customer success team will work directly with you to identify and resolve any open issues. Your journey will be nearly “zero-touch,” with the Scrut team accompanying you all the way to the finish line.
When you are ready for audit, you can schedule an audit directly from the platform, as shown in the screenshot below:

- Automated evidence gathering: Scrut eliminates the need to manually collect thousands of evidence artifacts by automating evidence collection across 70+ integrations across mapped controls.
Check out our customer reviews below:

To learn more about how to automate your NIST compliance with Scrut, schedule a demo.
Customer Rating
- G2 – 5/5
Also Read: Best NIST compliance software for 2025
2. Hyperproof
Hyperproof is a GRC software solution that assists businesses in accelerating the installation and implementation of NIST 800 controls. Using Hyperproof, you can monitor the results of organization-wide risk assessments and show how risks are continuously managed.
Pros
- Role-based security helps keep individual users focused on their assigned tasks, and tasks can be viewed as either a Kanban board or a grid.
- The Jumpstart feature allows you to track the progress of current programs against other programs.
Cons
- The inability to right-click on particular controls, groups of controls, document upload information, or other interface elements causes users to become distracted from their current tasks.
- Lack of control over configuring and customizing the notification system results in noise.
Customer Rating
- G2 – 4.6/5
3. AuditBoard
Auditboard is a connected risk platform that integrates NIST 800, SOC 2, ISO 2700x, CMMC, PCI DSS, and other risk management standards across your organization. You can automate manual tasks, avoid duplicate assessments, and streamline reporting with automation and a single source of truth.
Automated notifications and reminders to stakeholders will eliminate the need for manual follow-ups, allowing users to evaluate a control only once and use the results to satisfy numerous requirements.
Pros
- The ability to create custom reports in Excel to observe data assists in analyzing data trends without having to make custom requests with the IT team.
- The platform eliminate the manual follow-ups with automated notifications and reminders.
Cons
- Because it was designed as a SOX tool, the compliance and risk modules are not well developed.
- Users cannot access prior-year details due to a lack of access options to archived data.
Customer Rating
- G2 – 4.7/5
4. ISMS.online
ISMS.online allows you to manage your NIST requirements, policies, and controls all in one place. ISMS.online has everything you need, including a Virtual Coach, the Assured Results Method, live customer support, and an in-built knowledge base.
Pros
- The system’s checklists and progress bar are useful and keep users motivated to continue making progress.
- The Corrective Action Requests (CARs) can be linked to the report to see everything at a glance.
Cons
- When it comes to the tool’s ability to modify policy packs, it is not very flexible.
- Users may find it challenging to use if they are not trained on how to use it.
Customer Rating
- G2 – 4.6/5
5. Apptega
Apptega can assist you with your ongoing cybersecurity needs, including NIST, with its audit manager, which streamlines your cybersecurity and compliance audits, saving your organization valuable time and money and simplifying cybersecurity compliance.
Harmony, Apptega’s intelligent framework cross-walking capability, combines thousands of sub-controls from Apptega’s entire framework library into a unified set of common controls and sub-controls, resulting in time, effort, and resource efficiencies.
Pros
- You can connect with consultants through the tool who can help you manage the costs associated with Cybersecurity program compliance.
- The UI and templates on Apptega are easy to use.
Cons
- To generate your plan of action and milestones, you must either have Apptega upload a task pack, which is an additional purchase, or manually create tasks for each unfinished item.
- Users cannot edit documents in the platform live, which eliminates the possibility of maintaining version control, review, and approval cycles.
Customer Rating
- G2 – 4.7/5
6. ZenGRC
ZenGRC is GRC software that aids in every aspect of NIST compliance management, including risk assessment, identifying NIST compliance gaps, advising you of the controls you need to put in place, and guiding you through the process step-by-step. With just a few clicks, it can perform unlimited self-audits and keeps all your audit records in one location.
Pros
- Offers features for bulk editing tasks, such as bulk uploading audits and changing task ownership in bulk.
- Apart from existing vendor security questionnaires, risk assessment questionnaires, data audits, and so on, it allows you to create your questionnaires with branching logic.
Cons
- It is impossible to duplicate a request automatically without recurrence, and the parent request gets updated, but it does not affect the recurring requests that spin off from it.
- Vendor review requests submitted via Jira must be re-entered into the tool; they cannot be automatically copied.
Customer Rating
- G2 – 4.4/5
7. LogicGate Risk Cloud
LogicGate is a risk management solution that includes the most recent NIST Cybersecurity Framework version. A record for each subcategory includes the overall category and function to which it belongs, as well as informative references. Through LogicGate’s graph database technology, each NIST CSF subcategory can be linked to other common frameworks and regulations.
Pros
- The workflows are adaptable so that the privacy team can change them without technical knowledge.
- There is extensive content available as training for the average user.
Cons
- Currently, there is no global search function in the tool, so you must create custom reports and search that specific table for your information.
- In the testing and validation module, there is currently no way to evaluate the effectiveness of the controls.
Customer Rating
- G2 – 4.6/5
8. SureCloud
SureCloud is a cloud-based compliance platform that secures and centralizes all compliance management data, removing silos and providing your teams with unified, consistent workflows and tools to manage all activities baselined against 150+ global regulations, frameworks, and standards. The Cloud Security Alliance Cloud Controls Matrix (CCM) module is specifically designed to assist cloud vendors and potential cloud customers in determining the overall security risk of a cloud provider.
Pros
- Includes the ability to create custom scoring for each assessment question, custom tiers for third parties, and shelf assessments without additional integration support.
- The platform’s Data Privacy compliance module is simple, logical, and easy to scale.
Cons
- The steep learning curve for users transitioning from Excel to GRC or TPRM
- When creating new forms, loading larger forms, or dashboards, responsiveness may be slow due to the complexity of the form/dashboard being loaded or the dataset(s) underlying it.
Customer Rating
- G2 – 4.3/5
9. Ostendio
Ostendio is a platform for integrated security and risk management that enables you to assess risk, develop and manage crucial policies and procedures, deliver training on security awareness, and track ongoing compliance with more than 150 security frameworks. Organizations can build and manage activities simultaneously against more than 100 industry standards and regulations by utilizing the Ostendio MyVCM platform. Customers can choose NIST-800-53 in Ostendio MyVCM, and the software will automatically map each control to all other chosen frameworks.
Pros
- The ability to receive notifications about your current compliance status that reminds you to complete a pending module.
- MyVCM platform gives us the ability to build a Quality Management System.
Cons
- We must use the “quiz” feature in KnowBe4 to allow users to upload evidence of training completion, frequently resulting in the wrong piece of evidence being uploaded.
- Due to insufficient integration between MyVCM and KnowBe4, user training information is not automatically transferred to MyVCM.
Customer Rating
- G2 – 4.7/5
10. SecureFrame
Secureframe compliance monitoring software assists organizations that work with the federal government or handle federal data in becoming compliant quickly and easily. It includes dozens of policies developed and vetted by in-house compliance experts and auditors, including System Security Plan (SSP) and Plan of Action and Milestones (POAM) templates.
Pros
- You will have access to their customer support team through Slack and scheduled meetings as you get ready for your audit.
- Evidence that needs to be collected is broken down into clear deliverables.
Cons
- There is no real-time update; it takes 1-2 days to refresh the test results after the AWS resource is fixed. If an immediate update is required, only the SecureFrame can perform it.
- Because some of the jargon was difficult to understand, there is no clear appendix to provide a framework and context for tests.
Customer Rating
- G2 – 4.6/5
11. Tugboat Logic
Tugboat Logic is a compliance and security assurance platform with policies that meet the requirements of NIST 800-171 and include an entire library of editable controls for your framework. Those controls correspond to your evidence tasks, and any relevant evidence already part of your InfoSec program will automatically apply to your NIST 800-171. There is no need to repeat any work.
Pros
- The Tugboat “readiness check” feature is a good starting point for determining which controls are required for compliance.
- The tool includes evidence-collection reminders and filters for various periods such as annual, biannual, weekly, etc.
Cons
- There are too many options available when creating an audit report or questionnaire, which can be difficult when it is enough to focus on particular questions.
- There is no bulk update feature for the onboarding and off-boarding review and approval processes.
Customer Rating
- G2 – 4.6/5


















