Ready, set, NIS 2: Tasks to meet directive requirements

The NIS 2 Directive is a comprehensive cybersecurity framework designed to strengthen resilience and security measures across various critical sectors within the European Union. This updated directive is a successor to the original NIS (Network and Information Systems) Directive and aims to address the increasing sophistication and frequency of cyber threats.
By expanding the scope from seven to eighteen critical industries, the NIS 2 Directive significantly impacts a broader range of businesses and sectors, enforcing stricter compliance requirements and enhancing the overall cybersecurity posture of the EU. It also establishes enhanced cybersecurity standards to bolster the security and resilience of network and information systems across these critical sectors.
Furthermore, the NIS 2 Directive mandates compliance for non-EU entities providing services within the EU, thus ensuring a consistent level of security throughout the bloc. Additionally, the directive grants member states the flexibility to tailor specific measures and include further sectors or entities as necessary.
If you want to learn about the process of implementing the NIS 2 Directive in your organization, you have clicked on the right blog.
Understanding NIS 2 directive scope applicability
1. Essential vs. Important entities:
- Essential entities: These include operators of essential services in key sectors like energy, transport, banking, health, and digital infrastructure. These entities are considered vital for societal and economic activities; thus, their disruption could have significant impacts.
- Important entities: Although the specific definition isn’t detailed in the provided results, it’s generally understood that these entities, while still crucial, do not have the same critical impact on societal stability as essential entities.
2. Sectors affected:
- The directive covers a wide range of sectors, explicitly mentioning energy, transport, banking, financial market infrastructures, health, drinking water, and digital infrastructure as areas where essential entities operate. Public electronic communications networks are also included under this umbrella.
3. Implications for organizations:
- All organizations classified under these categories, regardless of size, need to meet the new stringent cybersecurity measures, ensuring they can manage and report cyber incidents effectively.
Timeline for compliance for NIS 2 Directive
The NIS 2 Directive outlines a timeline for compliance to ensure that OES and DSPs adhere to its provisions in a timely manner. The key aspects of the compliance timeline include:

Penalties for non-compliance
- The consequences of failing to comply with NIS 2 can be severe, encompassing financial fines, as mentioned above, limitations on business activities, and additional barriers to future approvals. In more serious cases, non-compliance could also lead to criminal charges, including prison sentences for responsible parties.
- Ethical repercussions include loss of public trust and damaged reputation, which can indirectly affect business operations and long-term viability.
Steps to compliance with the NIS 2 checklist
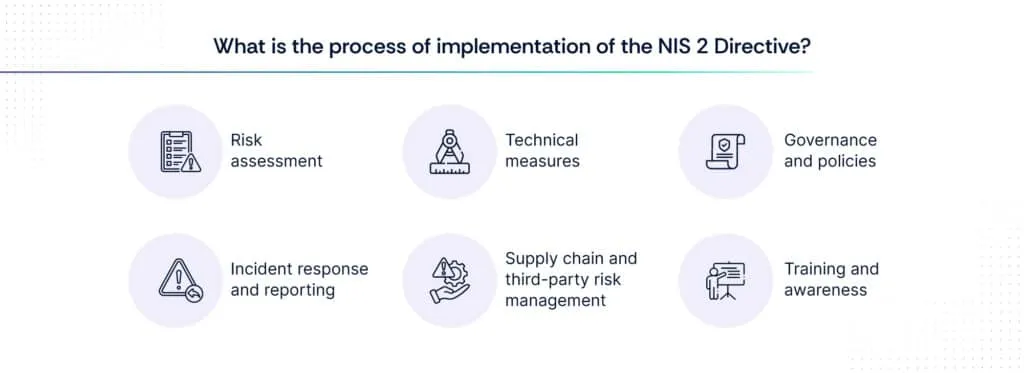
Achieving compliance in cybersecurity involves a detailed and structured approach to managing the integrity, confidentiality, and availability of data. This comprehensive guide elaborates on the key steps organizations must take, from initial risk assessments through to technical measures, governance, and incident management, all aligned with the NIS 2 checklist.
1. Risk assessment
- Conducting thorough cybersecurity risk assessments
Start by clearly defining the scope of the assessment to include all potentially vulnerable assets. This step involves identifying the organization’s critical information assets, which could range from customer databases to internal communications. Then, assess the risks associated with each asset, including potential threats and vulnerabilities, and evaluate the impact and likelihood of these risks. This systematic approach helps prioritize mitigation efforts based on the severity of the risk.
- Identifying vulnerabilities in information systems
Implement vulnerability scanning and penetration testing to uncover weak points in the network and systems. These activities should be performed regularly to discover new vulnerabilities that could be exploited by attackers. This ongoing process is essential for maintaining a robust defense against evolving cybersecurity threats.
2. Technical measures
- Implementing state-of-the-art cybersecurity technologies
Equip your IT infrastructure with advanced cybersecurity solutions, such as next-generation firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and robust encryption methods. These technologies help to detect, prevent, and respond to cyber threats in real-time.
- Enhancing the security of network and information systems
Consistently update and patch systems and software to defend against vulnerabilities. Implement strong network security measures, including secure configurations, network segmentation, and strict access controls. These practices reduce the attack surface and limit the potential damage from security breaches
3. Governance and policies
- Establishing robust cybersecurity governance structures
Develop a cybersecurity governance framework that assigns clear roles and responsibilities across the organization. This framework should also include regular reviews and updates to security policies and procedures to adapt to new cybersecurity trends and regulatory changes.
- Developing and updating cybersecurity policies in alignment with the NIS 2 checklist
Create comprehensive policies that address all aspects of information security, from employee conduct to response strategies for different types of cyber incidents. These policies should be regularly reviewed and updated to incorporate new security technologies, threat information, and compliance requirements.
4. Incident response and reporting
- Setting up an incident response plan
Develop a detailed incident response plan that outlines specific procedures for handling different types of cyber incidents. This plan should include roles and responsibilities, steps for containment and eradication, and communication strategies for internal and external stakeholders.
- Obligations for reporting cybersecurity incidents to national authorities
Ensure there are protocols for promptly reporting cybersecurity incidents to relevant authorities, as required by law. This not only complies with regulatory frameworks like NIS 2 but also helps the broader community by sharing information on emerging threats.
5. Supply chain and third-party risk management
- Assessing and managing risks posed by third parties and supply chains
Evaluate the security posture of all third-party vendors and supply chain partners. Implement stringent security requirements and regular audits for these partners to mitigate the risk of a security breach originating from less secure systems.
6. Training and awareness
- Regular training programs for staff on cybersecurity best practices
Conduct regular training sessions and simulations to educate employees about the latest cybersecurity threats and safe practices. This training helps to build a culture of security awareness throughout the organization.
- Raising awareness about cyber threats and safe practices
Initiate ongoing awareness campaigns that keep cybersecurity at the forefront of employees’ minds, helping to prevent inadvertent breaches and ensuring staff know how to react in the event of an incident.
Role of National Authorities in the Enforcement of the NIS 2 Directive
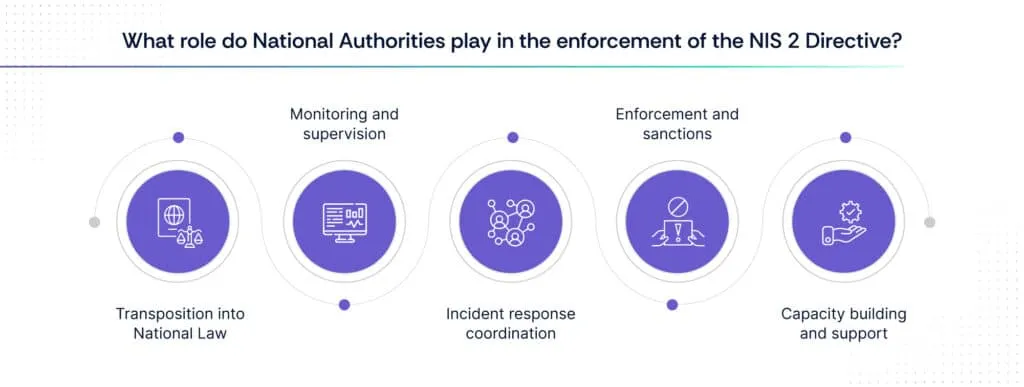
The role of national authorities in enforcing the NIS 2 Directive is critical for ensuring compliance and cybersecurity resilience across Member States. The key aspects of their role include:
1. Transposition into National Law
National authorities are responsible for transposing the provisions of the NIS 2 Directive into national law within the specified timeframe. This involves incorporating the NIS 2 requirements into the legal frameworks of Member States to enable enforcement and compliance monitoring.
2. Monitoring and supervision
National authorities are tasked with monitoring and supervising compliance with the NIS 2 Directive within their respective jurisdictions. This includes conducting audits, inspections, and assessments to evaluate organizations’ adherence to cybersecurity requirements and identify any non-compliance issues.
3. Incident response coordination
National authorities play a crucial role in coordinating responses to cybersecurity incidents, including facilitating information sharing and collaboration between relevant stakeholders. They serve as central points of contact for receiving incident reports from OES and DSPs and coordinating response efforts to mitigate the impact of cyber threats.
4. Enforcement and sanctions
National authorities have the authority to enforce compliance with the NIS 2 Directive and impose sanctions on organizations that fail to meet their obligations. This may include issuing warnings, imposing fines, or taking other corrective measures to address non-compliance and mitigate cybersecurity risks.
5. Capacity building and support
National authorities are responsible for building capacity and providing support to organizations, particularly small and medium-sized enterprises (SMEs), to help them meet their cybersecurity obligations effectively. This may involve offering guidance, training, and technical assistance to enhance cybersecurity resilience and compliance capabilities.
Challenges and concerns for businesses in the implementation of the NIS Directive
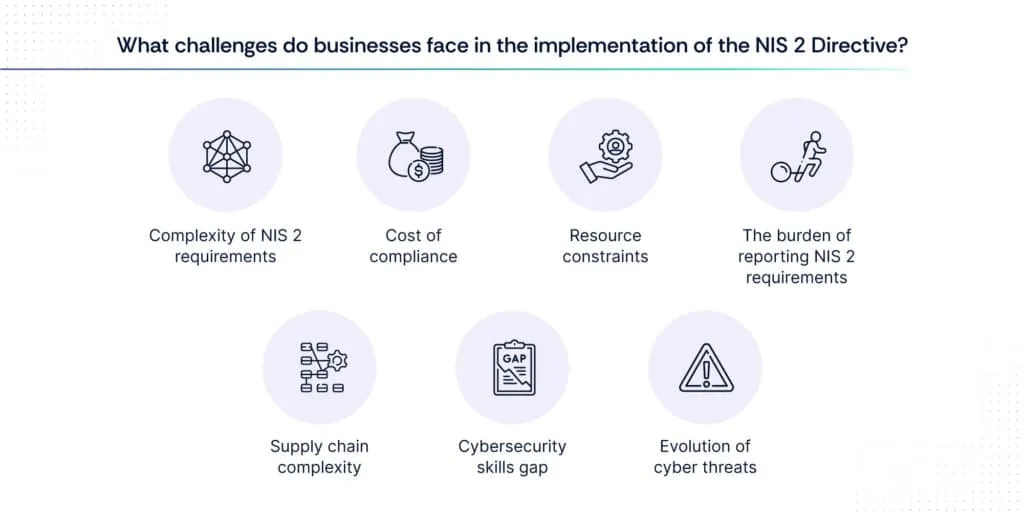
While compliance with the NIS 2 Directive offers significant benefits, businesses may also face several challenges and concerns:
1. Complexity of NIS 2 requirements
The NIS 2 Directive’s provisions can be complex and comprehensive, requiring businesses to dedicate substantial time and resources to understand and implement them effectively. This complexity may pose challenges, particularly for SMEs with limited cybersecurity expertise and resources.
2. Cost of compliance
Achieving compliance with the NIS 2 Directive may involve significant financial investments in cybersecurity measures, technologies, and personnel training. Businesses may face challenges in allocating sufficient budget and resources to meet the NIS 2 requirements while balancing other operational priorities.
3. Resource constraints
SMEs, in particular, may struggle to allocate sufficient resources, including skilled cybersecurity professionals, to comply with the directive. Limited budgets and manpower can hinder their ability to implement robust cybersecurity measures and maintain effective incident response capabilities.
4. The burden of reporting NIS 2 requirements
The directive’s incident reporting obligations impose additional administrative burdens on businesses, requiring them to promptly report significant cybersecurity incidents to national authorities. Ensuring compliance with reporting timeframes and providing detailed incident information may strain organizational resources and capabilities.
5. Supply chain complexity
Businesses operating within complex supply chains may face challenges in ensuring compliance across their network of suppliers, partners, and subcontractors. Ensuring consistent cybersecurity standards and practices throughout the supply chain can be difficult, increasing the risk of vulnerabilities and exposures.
6. Cybersecurity skills gap
The shortage of skilled cybersecurity professionals poses a challenge for businesses seeking to enhance their cybersecurity resilience and comply with the NIS 2 Directive. Recruiting and retaining qualified cybersecurity talent can be challenging, particularly in competitive labor markets.
7. Evolution of cyber threats
The rapidly evolving nature of cyber threats presents an ongoing challenge for businesses in maintaining effective cybersecurity defenses. Adapting to emerging threats, vulnerabilities, and attack techniques requires continuous monitoring, assessment, and adjustment of cybersecurity strategies and measures.
How can Scrut help you in the implementation of the NIS 2 Directive?
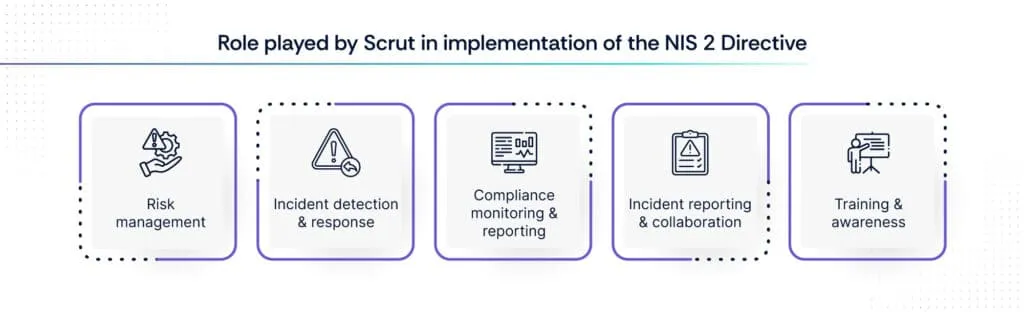
Scrut can play a crucial role in the implementation of the NIS 2 Directive by providing technical solutions and support in several key areas:
1. Risk management
Scrut can assist organizations in conducting comprehensive risk assessments to identify, assess, and prioritize cybersecurity risks to their networks and information systems. By leveraging advanced threat intelligence and risk analysis tools, Scrut can help organizations develop risk mitigation strategies aligned with the NIS 2 requirements.
2. Incident detection and response
Scrut can enhance organizations’ incident detection and response capabilities by providing real-time monitoring, threat detection, and automated incident response capabilities. By continuously monitoring network traffic and system logs, Scrut can quickly identify and respond to cybersecurity incidents, minimizing their impact on essential services and digital infrastructure.
3. Compliance monitoring and reporting
Scrut can support organizations in monitoring their compliance with the requirements of the NIS 2 Directive by providing automated compliance checks, audit trails, and reporting capabilities. By generating comprehensive compliance reports and evidence, Scrut can help organizations demonstrate their adherence to regulatory obligations and facilitate regulatory audits and assessments.
4. Incident reporting and collaboration
Scrut can streamline the incident reporting process by providing automated incident reporting templates, workflows, and collaboration tools. By facilitating timely and accurate incident reporting to national authorities and other stakeholders, Scrut can ensure compliance with the incident reporting requirements of the NIS 2 Directive and promote effective collaboration in incident response efforts.
5. Training and awareness
Scrut can support organizations in raising awareness and building cybersecurity skills among their employees through interactive training modules, simulations, and educational resources. By empowering employees to recognize and respond to cybersecurity threats effectively, Scrut can enhance the overall cybersecurity posture of organizations and support compliance with the NIS 2 Directive.
Final words
As the NIS 2 Directive reshapes cybersecurity standards across the European Union, organizations are tasked with not only meeting stringent compliance requirements but also proactively enhancing their security measures. This directive broadens the scope of affected sectors and mandates robust incident response and risk management practices.
Businesses must integrate NIS 2 requirements into their operations, emphasizing advanced cybersecurity technologies and comprehensive risk assessments. The directive’s reach, including non-EU entities, highlights the global significance of strong cybersecurity protocols. Leveraging resources like Scrut can facilitate compliance and strengthen defenses against evolving cyber threats.
Streamline Your NIS 2 Compliance with Scrut: Enhance your cybersecurity resilience and meet EU regulations effortlessly. Discover how Scrut can safeguard your operations. Get started today and secure your future!
FAQs
1. What are the main requirements of the NIS 2 Directive?
Organizations must implement stringent cybersecurity measures, manage and report cyber incidents effectively, and comply with enhanced standards for network and information system security.
2. What is the deadline for compliance with the NIS 2 Directive?
EU Member States must transpose the NIS 2 Directive into national law by October 17, 2024. Specific compliance timeframes for organizations will be established by national authorities.
3. How can organizations prepare for compliance with the NIS 2 Directive?
Organizations should start with a thorough risk assessment, implement state-of-the-art cybersecurity technologies, establish robust governance frameworks, and develop incident response plans.


















