Why Organizations Need Multiple Authentication Protocols

In an increasingly interconnected world, where digital interactions have become the norm, ensuring secure access to information and services is paramount.
Authentication protocols serve as the gatekeepers of digital access, verifying the identity of users and granting them appropriate permissions. Traditionally, password-based authentication has been the cornerstone of online security, requiring users to prove their identity through a combination of usernames and passwords.
However, the rise of cyber threats and the vulnerabilities inherent in password-based systems have highlighted the need for more robust authentication methods. Enter multi-factor authentication (MFA), which adds additional layers of security by requiring users to provide multiple forms of identification, such as passwords, biometric data, or security tokens.
In this blog, we will delve into the significance of multi-factor authentication in bolstering security measures.
Commonly used authentication methods
The traditional methods of authentication, such as simple passwords, mobile apps, and two-step verification (SMS OTP), fall short in providing robust security.
However, relying solely on these methods is no longer sufficient.
While these methods offer some level of security, they pale in comparison to the comprehensive protection provided by Multi-Factor Authentication (MFA).
What is MFA?
Multi-factor authentication (MFA) is a security method that requires users to provide two or more forms of verification before granting access to a system or application. These verification factors typically include:
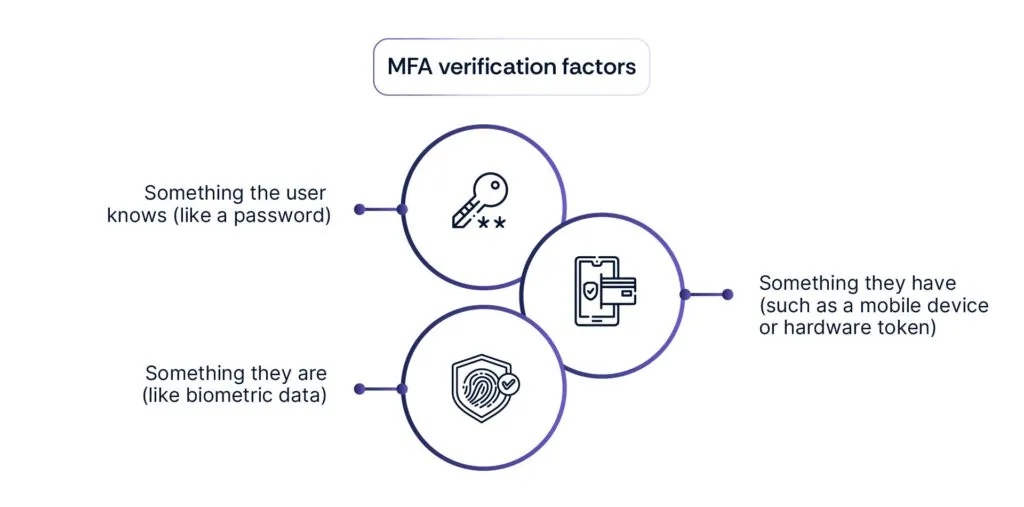
MFA adds an extra layer of security beyond traditional password-based authentication, making it significantly more difficult for unauthorized users to gain access to sensitive information or accounts. It’s an essential tool in combating cyber threats and protecting digital assets.
Indeed, MFA emerges as the superior choice for organizations striving to fortify their defenses against evolving cyber threats.
Benefits of Multi-Factor Authentication (MFA) in mitigating security risks
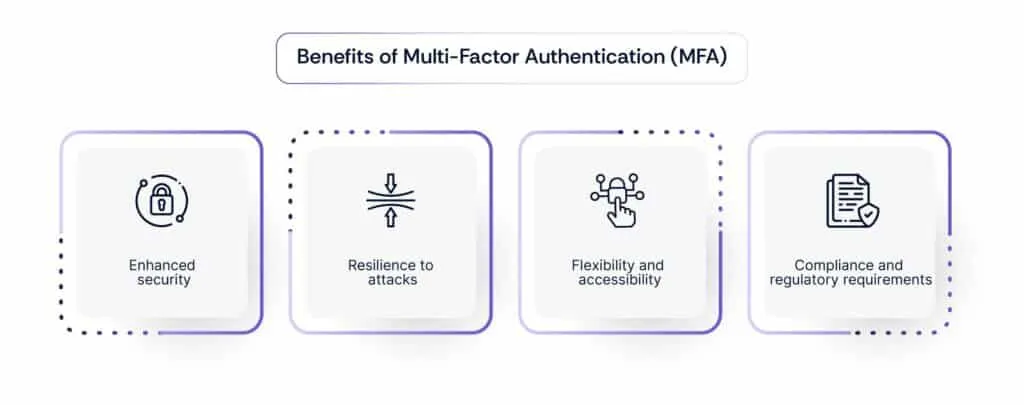
- Enhanced security: MFA adds an extra layer of protection beyond simple passwords, mitigating the risks associated with password breaches and unauthorized access.
- Resilience to attacks: Unlike single-factor authentication methods like SMS OTP, MFA reduces the likelihood of successful phishing attacks or credential theft, as attackers would need to compromise multiple authentication factors.
- Flexibility and accessibility: MFA accommodates a diverse range of authentication factors, allowing organizations to tailor security measures to suit their users’ preferences and operational needs.
- Compliance and regulatory requirements: Many regulatory standards, such as GDPR and PCI DSS, mandate the implementation of MFA as part of robust cybersecurity practices, ensuring compliance with legal and industry requirements.
Leveraging mobile devices for MFA
Leveraging mobile devices for MFA presents a pragmatic compromise that addresses the security, cost, and convenience concerns. Most users already own smartphones or tablets, making them readily available for authentication purposes.
Mobile devices offer built-in biometric authentication features such as fingerprint scanners and facial recognition, enhancing security without the need for additional hardware tokens.
Utilizing existing mobile devices for authentication can significantly reduce the implementation costs associated with deploying specialized hardware tokens or biometric scanners.
Mobile-based MFA solutions provide users with a seamless and convenient authentication experience, leveraging familiar devices and interfaces.
In conclusion
Deploying multiple authentication protocols is vital for robust cybersecurity. Biometrics, tokens, and multi-factor authentication (MFA) offer layers of protection against unauthorized access and data breaches.
Organizations must prioritize comprehensive security measures while maintaining flexibility and independence in decision-making.
Scrut provides the tools to evaluate security solutions objectively, ensuring that choices align with risk profiles, resources, and goals. Schedule a demo today to learn more.
Frequently Asked Questions
1. What are authentication protocols, and why are they crucial for organizational security?
Authentication protocols are sets of rules and procedures used to verify the identity of users accessing systems or networks. They are critical for organizational security because they ensure that only authorized individuals can access sensitive information or resources, thus preventing unauthorized access and potential security breaches.
2. How do diverse authentication methods, such as biometrics and tokens, contribute to stronger security defenses?
Diverse authentication methods add layers of security by requiring multiple forms of verification beyond just passwords. Biometrics, such as fingerprints or facial recognition, provide unique physical identifiers, while tokens generate one-time passcodes, making it harder for attackers to gain unauthorized access.
3. What risks do organizations face if they rely solely on traditional password-based authentication methods?
Organizations relying solely on traditional password-based authentication methods face significant security risks. Passwords can be easily compromised through techniques like phishing, brute force attacks, or password reuse. Additionally, users often choose weak or easily guessable passwords, further increasing the risk of unauthorized access.
4. How can implementing multiple authentication protocols help mitigate the risks of data breaches and unauthorized access?
Implementing multiple authentication protocols creates a more robust security posture by adding layers of defense. Even if one authentication method is compromised, attackers would still need to bypass additional authentication factors, such as biometrics or tokens, to gain access. This multi-factor approach significantly reduces the likelihood of successful unauthorized access.
5. What factors should organizations consider when determining which authentication protocols to deploy across their systems and networks?
When determining which authentication protocols to deploy, organizations should consider factors such as the sensitivity of the data or resources being protected, the usability and convenience for end-users, regulatory compliance requirements, and the organization’s risk tolerance. It’s essential to strike a balance between security and usability to ensure that authentication measures are effective without overly burdening users.


















