IT GRC Best Practices: CISO's Practical Guide

In today’s ever-changing business landscape, the implementation of IT GRC (information technology governance, risk management, and compliance) has become crucial. This blog aims to provide CISOs with a practical guide to mastering IT GRC, enabling them to safeguard their organizations against cyber threats, assess and mitigate risks, and ensure compliance with relevant standards and frameworks. By following these best practices and avoiding common pitfalls, CISOs can achieve success in their IT GRC initiatives.
Importance of implementing an IT GRC program:
An IT GRC program is essential for protecting an organization’s assets, reputation, and bottom line in an increasingly complex and digital business environment. Here are some reasons why it is necessary:
- An effective IT GRC program aligns the organization’s IT systems with its business goals, ensures compliance with standards and frameworks, and fortifies defenses against cyber attacks.
- Numerous regulations and standards apply to organizations, necessitating meticulous adherence. Additionally, partners may require adherence to specific frameworks, such as SOC 2 and ISO 27001.
- The organization itself may need robust vendor management to ensure data integrity.
Implementing a comprehensive IT GRC program helps address these challenges and ensure compliance while reducing manual burdens through automation.
Do’s: IT GRC best practices
An organization should carry out certain tasks in order to form a strong GRC process. Let’s look at some of the IT GRC best practices in detail.
1. Establish a clear GRC strategy:

A clear GRC strategy involves the organization defining its objectives, scope, and priorities.
a. Defining the objectives
The strategy of GRC begins by defining the objectives of the IT GRC program. Typically, organizations aim to strengthen the security and reliability of IT systems, ensure compliance with IT regulations and frameworks, reduce risk exposure, and increase transparency and accountability in their IT operations. IT GRC objectives should align with the organization’s strategic goals and mission.
b. Deciding the scope
The scope of your GRC program has two sections – the scope of people and the scope of systems. Identify the scope of IT systems that will be covered in the GRC program and the employees that will be involved in the process.
c. Setting the priorities
The priorities of the IT GRC program will be different in every organization depending on its functions, size, how much risk it faces, and its risk tolerance. So, set your customized priorities to suit your needs.
Additionally, an organization should allocate all its resources, including human and administrative resources, for the GRC program. If you don’t prepare adequately beforehand, it can lead to chaos during the GRC implementation phase.
2. Involve stakeholders and establish accountability:
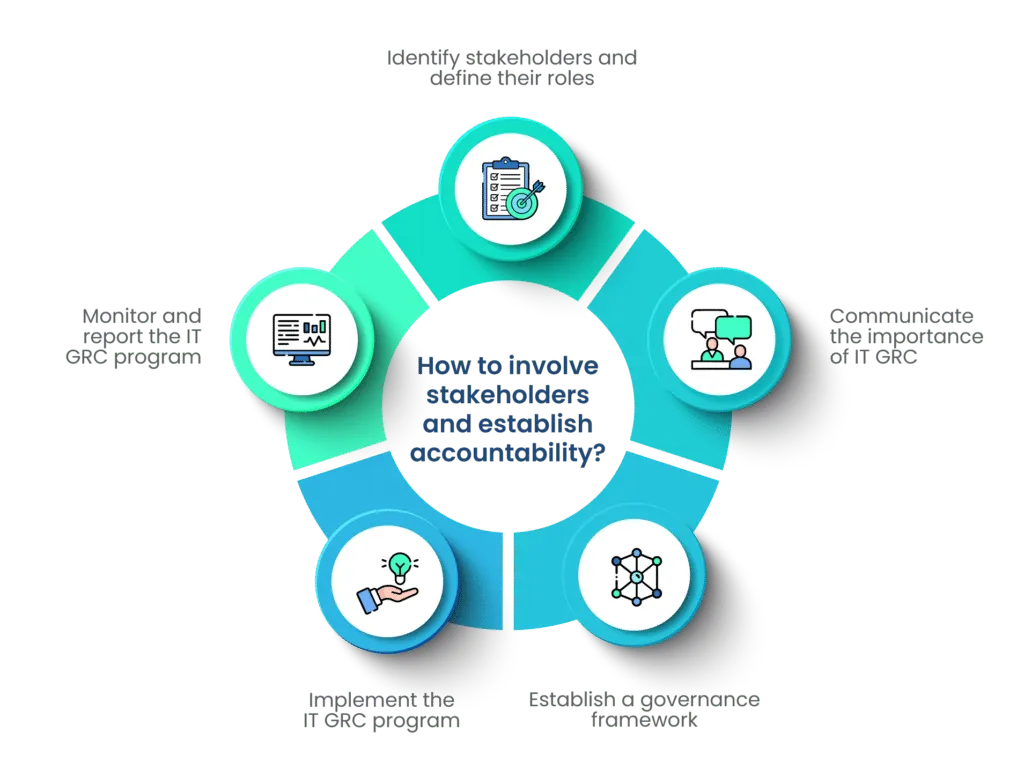
The next crucial step is involving stakeholders and defining their roles clearly to establish accountability.
a. Identify stakeholders and define their roles
The organization must identify stakeholders, such as management personnel, IT employees, compliance officers, audit staff, and legal departments, for the implementation of the GRC program.
Assign the IT GRC roles and responsibilities to each and every stakeholder in clear terms. They should be aware of the expectations of the organization. Also, the higher management should assess whether the tasks are completed on time.
b. Communicate the importance of IT GRC best practices
It is crucial that every person on the team is aware of the importance of IT GRC. Educate the stakeholders about the legal and financial repercussions of non-compliance for the organization’s overall success.
c. Establish a governance framework
A governance framework involves the creation of policies, procedures, and controls required for an effective IT GRC program. This framework should be reviewed regularly and communicated to all stakeholders.
d. Implement the IT GRC program
The next step is to implement the IT GRC program. Focus on technologies, including risk management, policy management, and compliance monitoring. Training the stakeholders is one of the significant sections of the IT GRC program.
e. Monitor and report the IT GRC program
Monitoring and reporting all the facets of the IT GRC program, including governance, risk management, and compliance, can help the organization pinpoint flaws as soon as they appear. An outdated program can do more harm than good to the organization, while regular updation of the GRC program ensures its relevance.
3. Conduct regular risk assessments:
Conducting regular risk assessments can aid organizations in identifying vulnerabilities before they have had a chance to take effect. Begin by identifying the IT assets that require regular assessments, including hardware, software, applications, and IoT devices.
Identify both internal and external threats and assess the vulnerabilities existing in the assets. This will help you determine the likelihood and impact of risks and implement the corrective actions required to mitigate them.
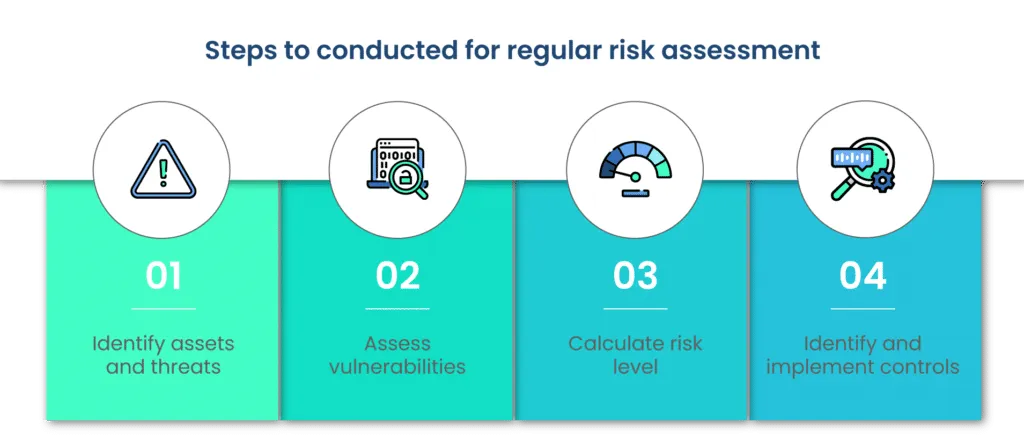
Here’s a step-by-step description of how to conduct regular risk assessments:
a. Identify assets and threats
Begin by identifying the IT assets, including hardware, software, applications, and Internet of Things (IoT) devices, that should be assessed for risk management. While conducting the risk assessment, the organization must focus on both types of threats – internal and external.
b. Assess vulnerabilities
Asset vulnerability refers to the flaw in software or hardware that can be responsible for letting cybercriminals into the organization’s systems. Assess all the assets for possible vulnerabilities and patch them as soon as possible.
c. Calculate risk level
Considering the likelihood and impact of the risks, calculate the risk that is imminent for the organization. Now, address the risks in accordance with your priorities.
d. Identify and implement controls
Create a list of controls you already have in place in the organization’s systems. Controls are the way in which the organization addresses and mitigates the risks. These controls may include but are not limited to updating software and hardware, training employees, and implementing security measures. Review the implementation frequently to ensure its effectiveness.
4. Regularly review and update policies and procedures:
An organization should regularly review and update IT GRC policies, procedures, and guidelines to ensure they remain current and relevant. They should be up to date with the latest industrial frameworks and regulations.
The policies and procedures should consider the ongoing threats in the industry to maintain the cybersecurity posture of the organization.

The following steps can be a guide to reviewing your policies and procedures:
a. Establish a review cycle
Experts recommend term reviews in addition to reviewing after every significant event. These events can be changes in organizational structure or legal policies or a cybersecurity incident.
b. Identify stakeholders
Identify the people who will be managing the policy reviews. The roles of these people must be clearly defined with an authoritative structure.
c. Evaluate effectiveness
Review the effectiveness of the current policies and procedures. Gather evidence, artifacts, feedback, and reports from various sections of the organization. Assess this evidence to form a comprehensive report of the effectiveness.
d. Identify gaps
The comprehensive report on the effectiveness of the policies and procedures will help you identify the gaps in the systems. These gaps can become vulnerabilities hindering the progress of the organization.
e. Develop updates and communicate changes
Patch the gaps with necessary updates. A single error in patching the software, hardware, or firmware can be the initial vector of a major cyber incident.
Once you have developed the updates, ensure that all the stakeholders are aware of the changes made in the policies. Train the employees if you see a knowledge gap.
f. Monitor effectiveness
An organization can’t ever stop reviewing the policies and procedures if it wants effective IT GRC.
Now that we’ve discussed the IT GRC best practices, let’s take a look at some of the actions organizations must refrain from doing when it comes to effectively implementing a GRC program.
Don’ts: Common pitfalls to avoid in IT GRC best practices
Sometimes in an organization’s management, the ‘don’ts’ take precedence over the ‘dos,’ as they are more impactful. Let us list out what an organization should not do in order to have an effective IT GRC program.
1. Don’t treat IT GRC as a one-time project:
IT GRC should be an ongoing process integrated into the core activities of the organization rather than a one-time initiative. Continuously update policies and procedures to align with evolving regulations and technologies. Allocate the necessary resources and ensure ongoing attention from top management.
2. Don’t overlook the importance of training and awareness:
Training and awareness are vital components of an effective IT GRC program. Educate all stakeholders on the importance of cybersecurity, compliance, and policies. Regularly assess their knowledge through quizzes and tests.
Scrut has an excellent employee training module that can help you train, assess, and encourage your employees to use secure cyber practices.
3. Don’t neglect regular audits and assessments:
Conducting internal audits is a critical part of evaluating the effectiveness of IT GRC; it ensures compliance with policies, procedures, and regulatory requirements. Additionally, organizations should also engage external auditors to gain an independent assessment of their program, which will help identify areas for improvement.
4. Don’t underestimate the importance of incident response planning:
Developing a robust incident response plan is essential for effective IT GRC. Establish a formal process for detecting, responding to, and recovering from security incidents. Define roles and responsibilities, establish communication channels, and conduct regular tabletop exercises to test the plan’s effectiveness. Learning from past incidents will help improve your response capabilities and strengthen your overall IT GRC program.
5. Don’t rely solely on technology:
Technology is a crucial role part of IT GRC best practices, it should not be the sole focus. One should remember that IT GRC is a combination of people, processes, and technology. Invest in training your staff, develop clear policies and procedures, and ensure effective communication and collaboration among different teams. Technology should support these efforts but not be considered a complete solution on its own.
Conclusion
Mastering IT GRC is essential for CISOs to protect their organizations from cyber threats, manage risks, and ensure compliance. By following the IT GRC best practices outlined in this guide and avoiding common pitfalls, CISOs can establish a strong and effective IT GRC program.
Remember to involve stakeholders, conduct regular risk assessments, update policies and procedures, provide training and awareness, perform audits and assessments, prioritize incident response planning, and balance technology with people and processes.
With a proactive and holistic approach to IT GRC, CISOs can achieve success in safeguarding their organizations’ critical assets and maintaining a secure and compliant environment.
To learn more about how smartGRC software can help your organization effectively implement a GRC program, schedule a demo with us today.

FAQs
1. What are the benefits of implementing an IT GRC program?
Some of the benefits of implementing an IT GRC program are
– Mitigation of cyber risks
– Improved security posture
– Optimized policies and procedures
– Reduced costs
– Slashed fines and penalties
2. What are some common mistakes organizations make when implementing IT GRC?
Organizations often treat IT GRC as a siloed practice and fail to integrate it with the main objectives of the organization. They treat IT GRC as a one-time project rather than an ongoing exercise resulting in the failure of the program.
Additionally, the organizations overlook the importance of the human factor in IT GRC. They fail to train their employees adequately to use the IT GRC software and to notify the management in case of a breach. This leads to a chaotic IT GRC environment.
3. Can small businesses benefit from implementing an IT GRC program?
Any business, whether small or large, can benefit from implementing an IT GRC program. In a small business, the roles and responsibilities often overlap, as there are fewer employees to carry out multiple tasks. In such cases, the responsibility of IT GRC falls on the shoulders of the IT department or the top management, all of whom have other responsibilities as well. This increases the chances of failure of the program as enough time is not spent on it. An automated IT GRC program can help small businesses carry out their tasks with ease and simplicity without losing productivity.


















