Introducing the new NIST CSF 2.0

In 2024, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) underwent a major upgrade after a significant ten-year gap. The NIST CSF 2.0 was finally released on February 26, 2024, after taking into consideration numerous comments received on the proposed changes for the same.
In this article, we will talk about the new factors of NIST CSF 2.0.
1. NIST CSF 2.0 has widened its scope
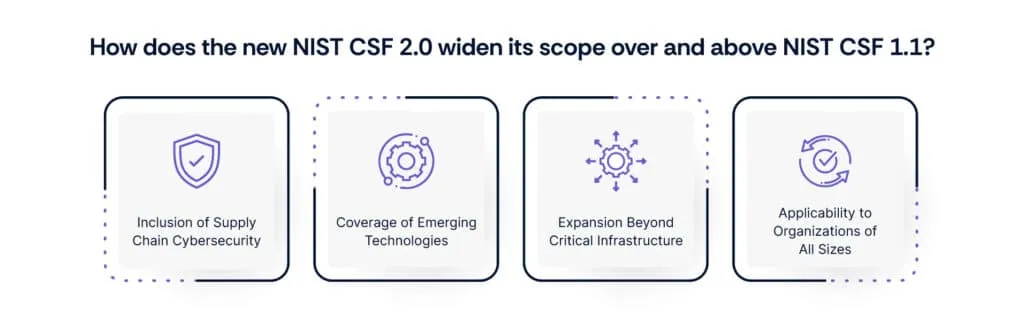
The NIST CSF 2.0 has significantly broadened its scope to address a wider array of cybersecurity challenges and risks. By doing so, it ensures that organizations are better equipped to address modern cyber threats and challenges.
Here are key aspects of its expanded scope:
- Inclusion of Supply Chain Cybersecurity: NIST CSF 2.0 now incorporates supply chain cybersecurity, recognizing the interconnectedness of organizations and the importance of securing the entire supply chain. This addition aims to mitigate risks associated with third-party vendors and partners.
- Coverage of Emerging Technologies: The updated framework acknowledges the emergence of new technologies such as artificial intelligence, IoT, and cloud computing. It offers guidance on securing these technologies effectively, ensuring organizations stay resilient amidst technological advancements.
- Expansion Beyond Critical Infrastructure: NIST CSF 2.0 goes beyond protecting critical infrastructure like hospitals and power plants. It now encompasses a broader range of industries, including healthcare, finance, government, and academia, reflecting the evolving cybersecurity landscape.
- Applicability to Organizations of All Sizes: The framework is designed to assist organizations of varying sizes and sectors in promoting cybersecurity best practices across industries. Whether a small business or a large enterprise, organizations can leverage NIST CSF 2.0 to manage and reduce their cybersecurity risks effectively.
2. NIST CSF 2.0 has introduced the new “Govern” function
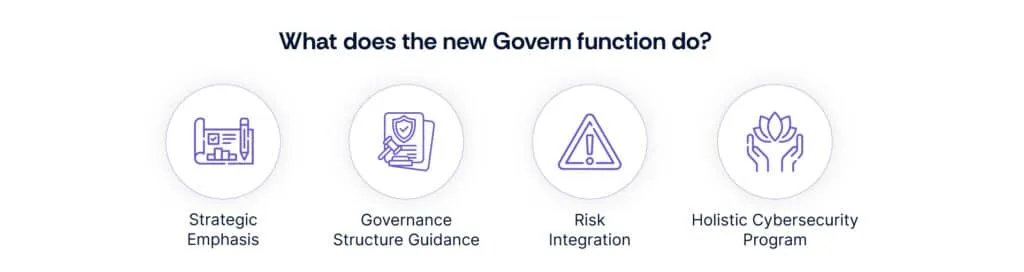
The new "Govern" function introduced in NIST CSF 2.0 signifies a paradigm shift towards a more comprehensive and strategic approach to cybersecurity governance. Here's a deeper dive into its key aspects:
- Strategic Emphasis: The Govern function is not merely operational but focuses on strategic elements such as organizational context, aligning cybersecurity efforts with business goals, and integrating cybersecurity risk management into broader enterprise risk management strategies.
- Governance Structure Guidance: It offers detailed guidance on establishing and maintaining an effective governance structure tailored to support an organization's unique cybersecurity objectives.
- Risk Integration: The Govern function ensures the integration of cybersecurity risk management into the organization's overall risk management strategy, fostering a more cohesive and coordinated approach.
- Holistic Cybersecurity Program: By adding a governance focus, NIST CSF 2.0 aims to bolster the pillars of a successful cybersecurity program, recognizing governance as a foundational element alongside other core functions like Identify, Protect, Detect, Respond, and Recover.
3. NIST CSF 2.0 has a bank of resources to facilitate the implementation

NIST CSF 2.0 introduces several new resources to facilitate its implementation and adoption by organizations:
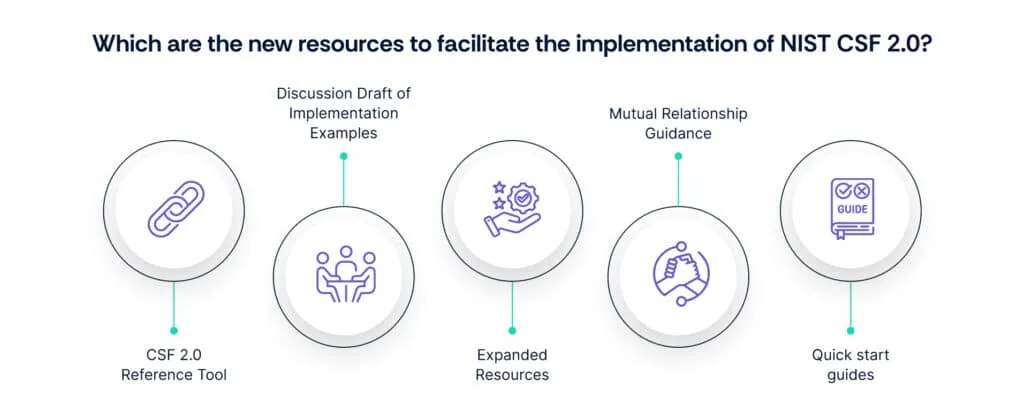
- CSF 2.0 Reference Tool: This tool simplifies implementation by providing users with access to core guidance data in a user-friendly format. It allows users to search, access, and export essential information to aid in the implementation process.
- Discussion Draft of Implementation Examples: NIST has released a discussion draft of implementation examples for CSF 2.0. This document complements the framework by providing practical examples that organizations can refer to while implementing cybersecurity measures.
- Expanded Resources: NIST continues to build and host additional resources to aid organizations in implementing the CSF. These resources are publicly available and aim to provide comprehensive support for organizations looking to adopt the framework.
- Mutual Relationship Guidance: NIST resources describe the mutual relationship between cybersecurity risk management and Enterprise Risk Management (ERM). Understanding this relationship is crucial for organizations to effectively integrate cybersecurity into their overall risk management strategies.
- Quick start guides: NIST CSF 2.0 offers Quick Start Guides tailored to various entities, including small businesses, to aid in implementing cybersecurity measures effectively. These guides provide practical direction and guidance for organizations seeking to improve their cybersecurity posture.
Particularly, the Small Business Quick Start Guide is designed for small-to-medium-sized businesses (SMBs) that lack or have modest cybersecurity plans. It aims to facilitate the adoption of cybersecurity best practices outlined in the CSF 2.0, ensuring that SMBs can enhance their cybersecurity resilience.
Additionally, there are resources available such as videos and transcriptions, to further assist in understanding and implementing these Quick Start Guides.
4. NIST CSF 2.0 aligns with other security standards
The NIST Cybersecurity Framework (CSF) 2.0 exhibits alignment with various security standards and frameworks, enhancing its interoperability and relevance:
- ISO Standards: NIST CSF 2.0 aligns with International Organization for Standardization (ISO) standards, providing organizations with a flexible approach to adopting internationally recognized cybersecurity best practices.
- NIST Privacy Framework: The CSF harmonizes with the NIST Privacy Framework, offering a cohesive approach to managing both cybersecurity and privacy risks, ensuring comprehensive protection.
- NIST Risk Management Framework (RMF): CSF 2.0 complements RMF, enabling organizations to seamlessly integrate cybersecurity risk management practices into their broader risk management strategies, fostering a holistic approach to risk management.
- PCI DSS and Sarbanes-Oxley (SOX): Adhering to NIST CSF facilitates compliance with other security standards like the Payment Card Industry Data Security Standard (PCI DSS) and Sarbanes-Oxley Act (SOX), streamlining regulatory compliance efforts.

Additionally, tools like the NIST CSF 2.0 Reference Tool simplify the integration of related resources, enabling users to move quickly from CSF outcome statements to relevant guidance and best practices. These mappings enhance the usability and applicability of the NIST CSF 2.0 across various industries and cybersecurity contexts.
Challenges in implementing NIST CSF 2.0
1. Resource constraints
Implementing the updated framework may require additional resources in terms of both budget and personnel. Organizations might need to invest in training and technology to align with NIST CSF 2.0, which could strain their existing resources.
2. Technical complexity
Adapting to the updated framework can be technically complex. Integrating new cybersecurity measures, aligning with evolving guidelines, and managing the technical aspects of implementation can be challenging for organizations, especially those with limited technical expertise.
3. Resistance to change
Organizations often face resistance to change when implementing new cybersecurity practices. Employees and stakeholders may resist adopting new procedures and technologies, making it essential to manage change effectively and ensure buy-in from all parties involved.
4. Knowledge and understanding
Understanding the intricacies of CSF 2.0 and its implications can be a challenge for organizations. Adequate training and education are required to ensure that all stakeholders grasp the framework's principles and can effectively implement them.
5. Keeping up with evolving threats
Cyber threats are constantly evolving. Staying aligned with the updated framework and adapting to new threats and vulnerabilities requires ongoing vigilance and the ability to keep security measures up to date.
How can Scrut help in the implementation of NIST CSF 2.0?
Scrut helps in implementing NIST CSF in multifaceted ways:
- Framework Controls Assistance: Scrut provides support for NIST Special Publication 800-171 and NIST 800-53 framework controls, assisting organizations in implementing the controls required by NIST CSF 2.0.
- Continuous Compliance Monitoring: With Scrut's automation tools, organizations can continuously monitor their compliance with NIST CSF 2.0, ensuring that security controls are consistently applied and maintained.
- Risk Management: Scrut offers a risk-first approach, helping organizations prioritize their efforts based on risk assessment results, which aligns with the risk management focus of NIST CSF 2.0.
- Streamlined Implementation: By providing guidance and automation tools, Scrut simplifies the implementation process of NIST CSF 2.0, enabling organizations to efficiently adopt the framework and enhance their cybersecurity posture.
- Comprehensive Governance: Scrut Automation offers a governance, risk, and compliance (GRC) automation platform, allowing organizations to manage their cybersecurity initiatives comprehensively, including NIST CSF 2.0 implementation.
Final thoughts
The release of NIST CSF 2.0 signifies a crucial advancement in cybersecurity resilience. With expanded scope, a new governance function, and ample resources, it offers a comprehensive guide for organizations facing modern threats. Despite challenges, solutions like Scrut streamline implementation and enhance cybersecurity posture. By embracing NIST CSF 2.0 and leveraging tools like Scrut, organizations can fortify their defenses and navigate the evolving cybersecurity landscape with confidence.
FAQs
1. How does NIST CSF 2.0 align with other security standards and frameworks? NIST CSF 2.0 aligns with various security standards and frameworks, including ISO standards, the NIST Privacy Framework, and the NIST Risk Management Framework. This alignment enhances interoperability and streamlines compliance efforts.
2. What challenges might organizations face in implementing NIST CSF 2.0? Implementing NIST CSF 2.0 may pose challenges such as resource constraints, technical complexity, resistance to change, and the need for adequate knowledge and understanding of the framework and its implications.
3. What are the benefits of implementing NIST CSF 2.0 for organizations? Implementing NIST CSF 2.0 enables organizations to adopt a risk-based approach to cybersecurity, prioritize continuous improvement, ensure versatility across sectors and sizes, and gain clarity on governance structures, ultimately enhancing their cybersecurity resilience.


















