A guide to IAM compliance

In the constantly changing field of cybersecurity, organizations face a growing need to fortify their defenses against unauthorized access to sensitive information.
As technology advances, so do the tactics employed by cyber threats. The complexity of modern IT environments, coupled with the dynamic nature of user access, poses a considerable challenge for organizations striving to ensure the confidentiality, availability, and integrity of their data.
Identity and Access Management (IAM) compliance emerges as a critical linchpin in this endeavor, offering a robust framework to safeguard digital assets and maintain the integrity of organizational data.
Join us as we delve into IAM compliance, unraveling its components and showcasing how it acts as a strategic solution to the intricate challenges faced by organizations today.
What is IAM compliance and why is it important?
Compliance ensures that organizations not only protect their sensitive information but also meet the regulatory requirements stipulated by industry standards and laws.
IAM compliance refers to the adherence to a set of regulations, standards, and best practices that govern the secure management of user identities and their access rights.
IAM is the linchpin of cybersecurity, serving as the gatekeeper to an organization's digital assets. It encompasses a set of processes, policies, and technologies designed to manage and secure digital identities and their access to systems and data.
IAM security is foundational to protecting organizational assets and ensuring compliance with regulatory standards.
Understanding the nuances of IAM compliance is vital for organizations aiming to create a robust security posture. This involves implementing measures to authenticate and authorize users effectively, managing user lifecycle changes, and providing visibility into user activities.
By ensuring that only authorized individuals have the right level of access, IAM acts as a crucial layer of defense against unauthorized entry, data breaches, and other cyber threats.
Defining IAM compliance and its components
IAM compliance is a structured approach to managing and securing digital identities, encompassing policies, processes, and technologies to ensure that users have appropriate access to organizational resources.
Compliance goes beyond mere security measures; it involves aligning with industry regulations, standards, and best practices.
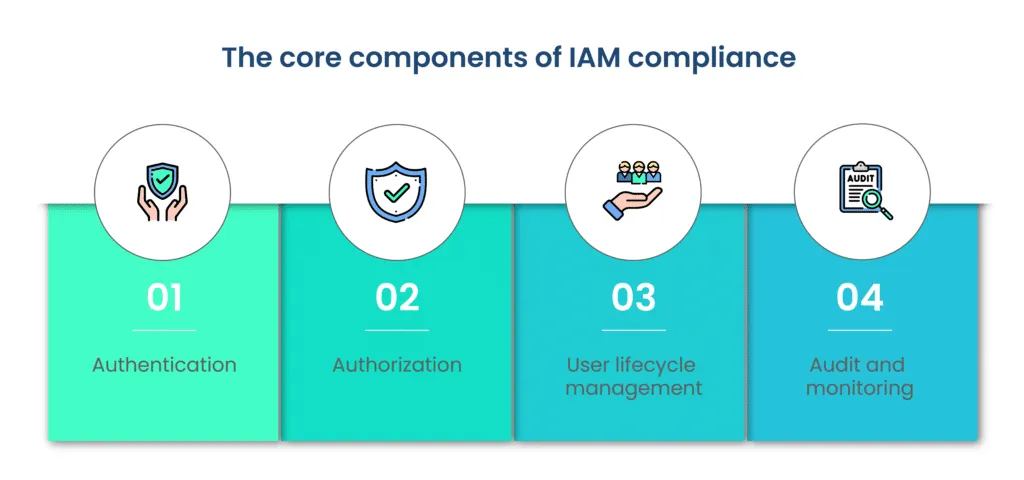
The core components of IAM compliance include:
- Authentication: Verifying the identity of users through credentials such as passwords, biometrics, or multi-factor authentication.
- Authorization: Granting appropriate access rights based on a user's role, responsibilities, and permissions.
- User lifecycle management: Effectively managing user accounts from creation to de-provisioning, ensuring timely updates and revocations.
- Audit and monitoring: Implementing systems for continuous monitoring, logging, and auditing user activities to detect and respond to potential security incidents.
The role of IAM in data security
IAM serves as the gatekeeper to an organization's data kingdom, playing a pivotal role in maintaining the confidentiality, availability, and integrity of sensitive information.
By enforcing access controls, IAM ensures that only authorized users can access specific resources, reducing the risk of unauthorized access and potential data breaches.
IAM also facilitates granular control over user permissions, helping organizations adhere to the principle of least privilege and limiting potential damage in the event of a security incident.
Common challenges in achieving IAM compliance
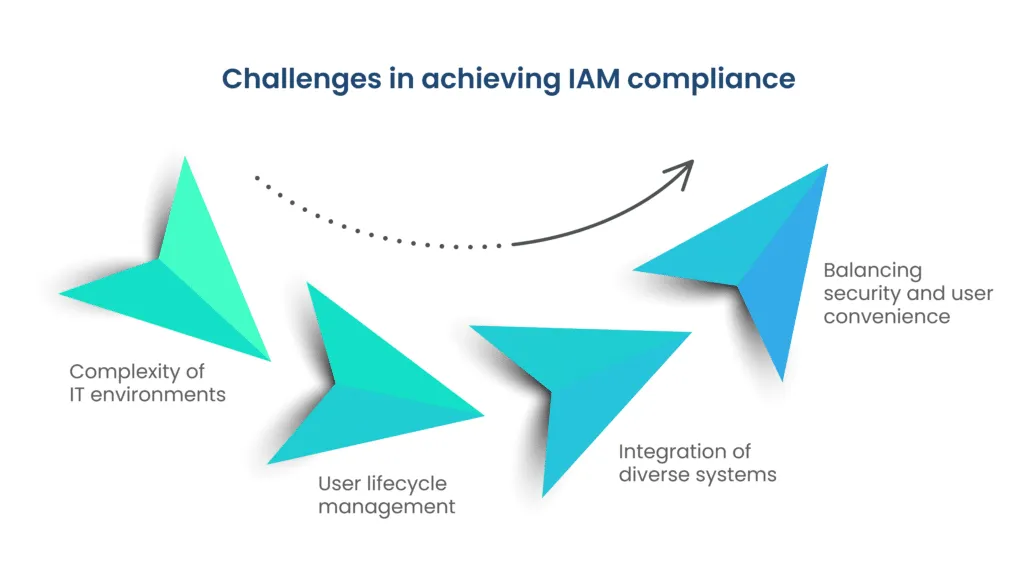
While IAM compliance is indispensable, organizations often face common challenges in its implementation. These challenges include:
- Complexity of IT environments: Integrating IAM across diverse systems and platforms.
- User lifecycle management: Ensuring accurate and timely management of user access throughout their journey within the organization.
- Integration of diverse systems: Coordinating IAM across different applications and platforms seamlessly.
- Balancing security and user convenience: Striking the right balance to ensure security without hindering user productivity.
By understanding these challenges, organizations can better navigate the path to IAM compliance and fortify their defenses against the evolving landscape of cyber threats.
Key components of IAM compliance
Crucial aspects of IAM compliance revolve around enforcing stringent access controls, ensuring visibility into user activities, and navigating the best practices for authentication and authorization.
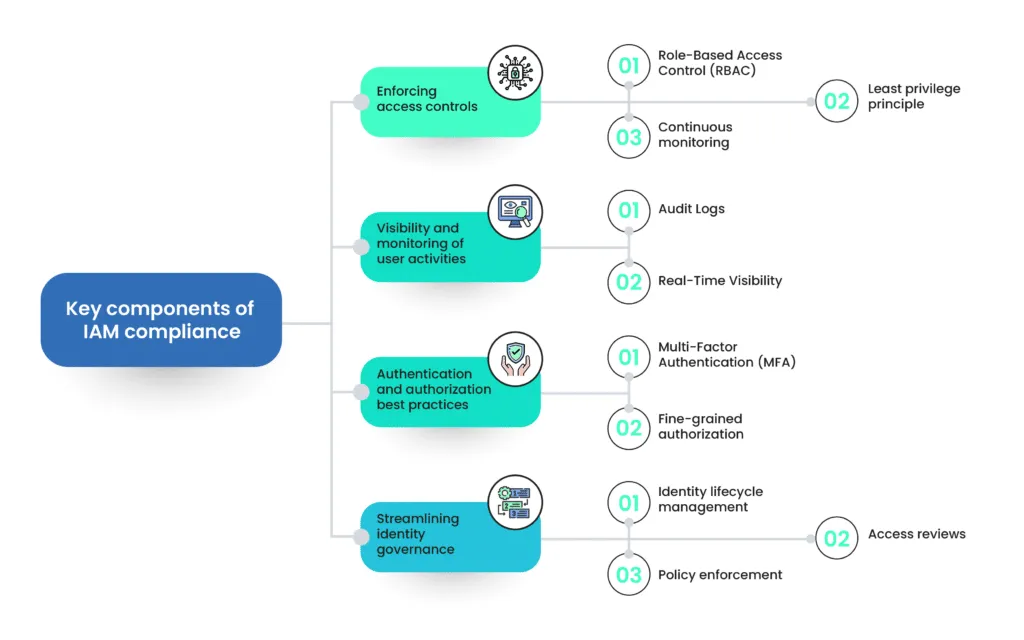
1. Enforcing access controls
IAM's primary objective is to regulate user access to digital resources. The various facets of enforcing access controls include:
- Role-Based Access Control (RBAC): Implementing a granular approach to assigning permissions based on users' roles within the organization.
- Least privilege principle: Limiting user access to the minimum level necessary for their job responsibilities to mitigate potential risks.
- Continuous monitoring: Employing real-time monitoring to swiftly detect and respond to any unauthorized access or suspicious activities.
By establishing stringent access controls, organizations can bolster their defense against unauthorized access, data breaches, and other cyber threats.
2. Visibility and monitoring of user activities:
IAM compliance hinges on the ability to proactively address potential threats through vigilant observation of user activities. It is important to maintain visibility into user actions and continuously monitor user activities.
Through effective monitoring, organizations can detect anomalies, prevent unauthorized access, and enhance their overall security posture. This will allow organizations to take proactive measures to identify and respond to suspicious activities promptly.
- Audit Logs: Creating and analyzing detailed audit logs to track user interactions with systems and data.
- Real-Time Visibility: Implementing tools and processes for real-time monitoring to promptly identify and respond to security incidents.
3. Authentication and authorization best practices
IAM's efficacy is closely tied to authentication and authorization practices. By adhering to best practices in authentication and authorization, organizations can fortify their IAM framework and reduce the risk of unauthorized access. It involves:
- Multi-Factor Authentication (MFA): Implementing robust authentication methods beyond passwords to enhance security.
- Fine-grained authorization: Establishing precise access control policies to regulate user permissions.
4. Streamlining identity governance
IAM compliance is not just about access management; it involves the overarching concept of identity governance.
A well-structured identity governance framework ensures that organizations have a clear understanding of who has access to what and why, fostering compliance and minimizing risks.
The broader concept of identity governance emphasizes:
- Identity lifecycle management: Efficiently managing user identities from creation to de-provisioning.
- Access reviews: Conduct regular reviews to ensure ongoing appropriateness of user access.
- Policy enforcement: Establishing and enforcing policies to govern identity-related processes.
A well-structured identity governance framework ensures clarity in user access, reducing the risk of compliance breaches and unauthorized actions.
Regulations governing IAM
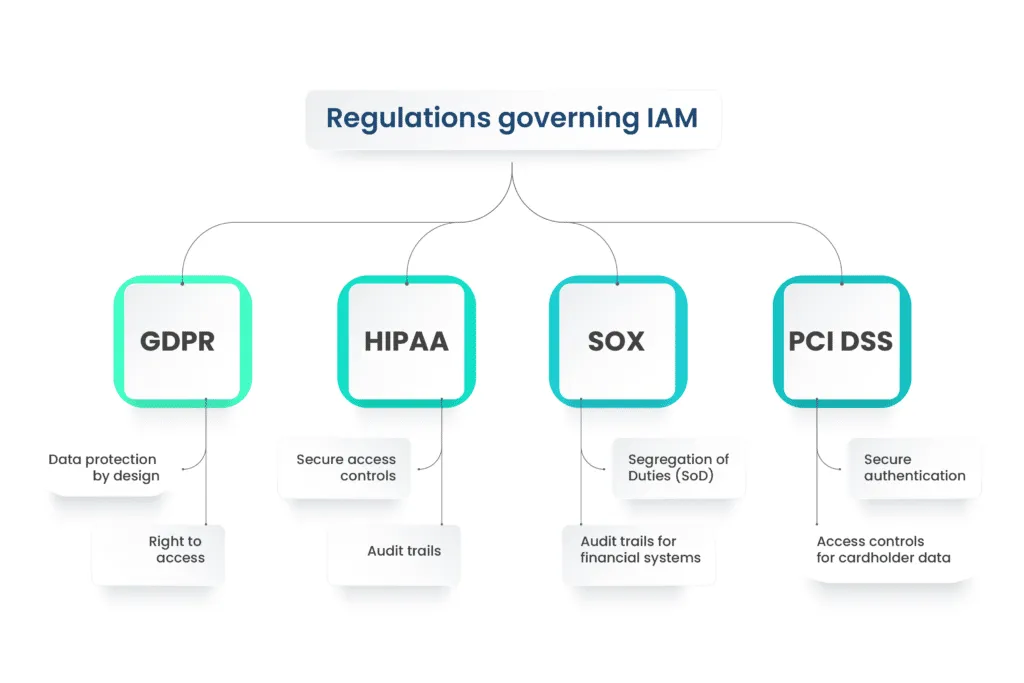
IAM compliance is not only a best practice but is often mandated by various regulations. Key regulations such as GDPR, HIPAA, SOX, and PCI DSS directly impact IAM practices.
Understanding these regulations is vital for organizations to tailor their IAM strategies to meet compliance requirements and avoid legal repercussions.
IAM compliance is not merely a best practice; it often aligns with industry regulations.
GDPR (General Data Protection Regulation)
The General Data Protection Regulation (GDPR) stands as a beacon for safeguarding the privacy and rights of European Union (EU) citizens' personal data. IAM compliance under GDPR is paramount, as it ensures that organizations handle personal data responsibly and transparently. Key aspects include:
- Data protection by design: Integrating data protection measures into IAM processes.
- Right to access: Allowing individuals control over their personal data and access permissions.
IAM practices aligned with GDPR not only fortify data protection but also uphold individual privacy rights.
HIPAA (Health Insurance Portability and Accountability Act):
In the healthcare sector, HIPAA establishes stringent standards for safeguarding patient information. IAM compliance under HIPAA is critical to maintaining the confidentiality and integrity of healthcare data. Key considerations include:
- Secure access controls: Ensuring that only authorized personnel access patient records.
- Audit trails: Maintaining detailed records of who accessed patient data and when.
IAM practices within healthcare organizations must align with HIPAA to prevent unauthorized access to sensitive patient information.
SOX (Sarbanes-Oxley Act)
SOX focuses on financial accountability and transparency within publicly traded companies. IAM compliance under SOX is integral to ensuring the security and accuracy of financial data.
IAM practices aligned with SOX contribute to maintaining the integrity of financial reporting and preventing fraudulent activities. Noteworthy components include:
- Segregation of Duties (SoD): Preventing conflicts of interest by segregating key financial responsibilities.
- Audit trails for financial systems: Providing a clear record of financial transactions and system access.
PCI DSS (Payment Card Industry Data Security Standard):
For organizations handling payment card data, compliance with PCI DSS is non-negotiable. IAM practices under PCI DSS focus on securing access to cardholder data and preventing unauthorized transactions. Key considerations involve:
- Secure authentication: Implementing robust authentication methods for users handling payment card data.
- Access controls for cardholder data: Limiting access to individuals based on job responsibilities.
IAM compliance within payment card environments is crucial for protecting financial transactions and maintaining the trust of customers.
Impact of non-compliance

Failing to adhere to Identity and Access Management (IAM) compliance not only jeopardizes the security of an organization's digital assets but also exposes it to myriad consequences that extend across legal, financial, and reputational domains.
Understanding the gravity of non-compliance is essential for organizations striving to maintain a resilient and secure digital posture.
1. Legal consequences
Non-compliance with IAM regulations often carries significant legal ramifications. Regulatory bodies, such as those overseeing GDPR, HIPAA, SOX, and PCI DSS, impose strict requirements for safeguarding user data.
Failure to meet these standards can lead to legal actions, investigations, and potential litigation. Organizations may find themselves entangled in legal proceedings that not only drain resources but also tarnish their standing in the eyes of regulatory authorities.
2. Financial penalties
Regulatory bodies have the authority to impose substantial fines on organizations found in breach of IAM compliance. These financial penalties are not inconsequential and can result in severe financial setbacks.
The magnitude of fines varies depending on the nature and scale of the non-compliance. For some regulations, fines may accrue on a per-incident or per-day basis, amplifying the financial impact.
3. Reputational damage
The trust of customers, partners, and stakeholders is a fragile commodity. Non-compliance with IAM regulations can erode this trust, leading to severe reputational damage. News of a data breach or regulatory violation spreads swiftly in the age of instant communication, and the resulting negative publicity can have lasting effects.
A tarnished reputation may deter potential customers, partners, and even employees, making it challenging for the organization to rebuild trust.
4. Data breach risks
IAM non-compliance significantly increases the risk of data breaches. Inadequate access controls and authentication mechanisms create vulnerabilities that malicious actors can exploit.
The consequences of a data breach extend beyond regulatory fines and legal actions; organizations may face the loss of sensitive information, intellectual property, and proprietary data. Moreover, the impact on customer trust and loyalty can be irreversible.
Strategies for streamlining IAM compliance processes
Achieving and maintaining Identity and Access Management (IAM) compliance can be a complex undertaking, but organizations can navigate this terrain effectively by implementing streamlined processes and best practices. Here are key strategies to streamline IAM compliance, ensuring efficiency, accuracy, and adherence to regulatory requirements.
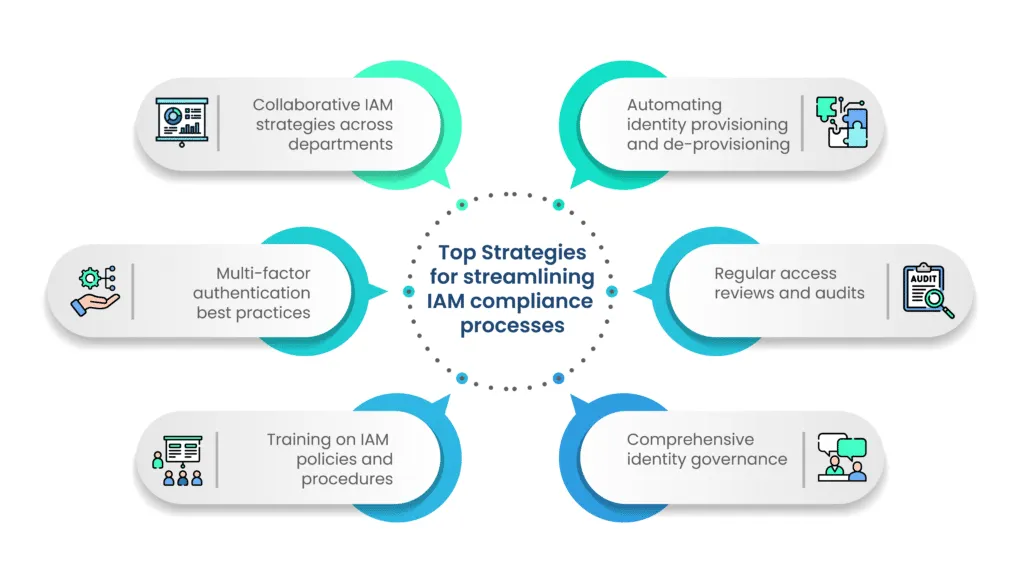
1. Automating identity provisioning and de-provisioning
Automating the process of granting and revoking user access rights is a cornerstone of efficient IAM compliance. Automated identity provisioning ensures that users receive the appropriate access promptly when entering the organization and that access is promptly revoked when they leave or change roles. This not only reduces the risk of human error but also enhances the organization's ability to respond swiftly to personnel changes.
2. Regular access reviews and audits
Regularly reviewing and auditing user access rights is essential for maintaining the principle of least privilege and ensuring ongoing compliance. By conducting periodic access reviews, organizations can identify and rectify discrepancies, unauthorized access, and potential security risks. Automation can play a role in facilitating these reviews, ensuring they are conducted systematically and comprehensively.
3. Comprehensive identity governance
Establishing a comprehensive identity governance framework is critical for effective IAM compliance. This involves creating and enforcing policies related to user identity management, access controls, and data protection. A well-structured identity governance system provides clarity on who has access to what resources and under what conditions, streamlining the overall IAM compliance process.
4. Training on IAM policies and procedures
Human error is a common factor in IAM compliance challenges. Providing regular training on IAM policies and procedures to employees, IT staff, and relevant stakeholders is crucial. Ensuring that individuals understand the importance of compliance, how to follow established procedures, and the consequences of non-compliance contributes significantly to the success of IAM initiatives.
5. Multi-factor authentication best practices
Enhancing authentication practices with Multi-Factor Authentication (MFA) adds an extra layer of security to user access. Best practices in MFA include the use of biometrics, smart cards, or one-time passcodes. By incorporating MFA, organizations significantly strengthen access controls, mitigating the risk of unauthorized access and aligning with IAM compliance requirements.
6. Collaborative IAM strategies across departments
IAM compliance is not solely an IT concern—it requires collaboration across departments. Establishing communication channels between IT, HR, legal, and other relevant departments ensures a holistic approach to IAM. Collaborative strategies help in aligning IAM processes with business needs, regulatory requirements, and the organization's overall security objectives.
Choosing the right IAM solutions
Selecting the appropriate Identity and Access Management (IAM) solution is a pivotal decision for organizations aiming to fortify their cybersecurity posture and achieve compliance.
1. Aligning with industry best practices
Before diving into the plethora of IAM solutions available, organizations should align their selection process with industry best practices.
By aligning with industry best practices, organizations lay a strong foundation for selecting IAM solutions that meet their unique requirements and set the stage for effective implementation. This involves:
- Understanding organizational needs: Identifying specific IAM requirements based on the organization's structure, size, industry, and regulatory environment.
- Scalability: Choosing solutions that can scale with the organization's growth and evolving IAM needs.
- User-friendly interfaces: Prioritizing solutions with intuitive interfaces to enhance user experience and minimize training requirements.
- Interoperability: Ensuring that the chosen IAM solution can seamlessly integrate with existing systems, applications, and third-party tools.
2. Evaluating IAM solutions for compliance
IAM compliance is non-negotiable, and organizations must carefully evaluate potential solutions to ensure they align with regulatory requirements. Key considerations include:
- Regulatory Alignment: Verifying that the IAM solution complies with relevant regulations such as GDPR, HIPAA, SOX, and others applicable to the organization.
- Audit and Reporting Capabilities: Assessing the solution's ability to generate detailed audit logs and reports for compliance audits.
- Access Control Mechanisms: Ensuring the solution provides robust access controls and authorization features to meet regulatory standards.
- Data Encryption: Verifying that the IAM solution employs strong encryption methods to protect sensitive data.
By prioritizing compliance features during the evaluation process, organizations mitigate the risk of non-compliance and lay the groundwork for a secure IAM environment.
3. Implementation tips and considerations
Successful implementation is as crucial as selecting the right IAM solution. Implementation tips and considerations include:
- Phased rollouts: Implementing IAM solutions in phases to manage complexity, minimize disruptions, and ensure smooth user transitions.
- User training: Conducting comprehensive training sessions to educate users on the new IAM processes, policies, and features.
- Continuous monitoring: Implementing tools and processes for continuous monitoring of IAM activities to detect and respond to anomalies promptly.
- Vendor support and updates: Choosing vendors that provide robust support and regular updates to address emerging security threats and vulnerabilities.
Wrapping up
The impact of non-compliance, spanning legal, financial, and reputational risks, highlights the critical importance of prioritizing IAM strategies. Indeed, IAM compliance emerges as a pivotal element in modern cybersecurity, providing a robust framework for safeguarding digital assets and ensuring regulatory adherence.
Through the enforcement of access controls, heightened visibility, and strategic alignment with industry best practices, organizations can fortify their defenses against unauthorized access and potential legal consequences.
The careful selection and implementation of IAM solutions contribute to an organization's security posture, emphasizing regulatory alignment, phased rollouts, and continuous monitoring paving the way for a secure and resilient digital future.
Scrut can help you improve your compliance and security posture. Find out how today!
Frequently Asked Questions
1. What is Identity and Access Management (IAM) compliance, and why is it crucial for organizations?
Identity and Access Management (IAM) compliance refers to adhering to a set of policies, procedures, and regulations that govern the secure management of user identities and their access to organizational resources. It is crucial for organizations because it ensures that only authorized individuals have the right level of access to specific systems, applications, and data. IAM compliance helps protect sensitive information, prevent unauthorized access, and maintain the overall security posture of an organization.
2. What are the common challenges organizations face in achieving and maintaining IAM compliance?
Common challenges in achieving and maintaining IAM compliance include:
- Complexity of IT environments.
- User lifecycle management.
- Integration of diverse systems.
- Balancing security with user convenience.
- Keeping pace with evolving regulations.
- Inadequate resources and expertise.
- Ensuring continuous monitoring and auditing.
3. How does IAM compliance contribute to overall cybersecurity resilience?
IAM compliance contributes to cybersecurity resilience by:
- Enforcing strict access controls, reducing the risk of unauthorized access.
- Providing visibility into user activities for monitoring and early threat detection.
- Ensuring proper authentication and authorization processes.
- Streamlining identity governance to prevent identity-related risks.
- Facilitating timely revocation of access for terminated or changed roles.
4. What key regulations govern Identity and Access Management, and how does non-compliance impact businesses?
Key regulations governing IAM include:
- GDPR (General Data Protection Regulation)
- HIPAA (Health Insurance Portability and Accountability Act)
- SOX (Sarbanes-Oxley Act)
- PCI DSS (Payment Card Industry Data Security Standard)
Non-compliance can lead to legal consequences, financial penalties, damage to reputation, and loss of customer trust. It may also result in data breaches and compromise the confidentiality and integrity of sensitive information.
5. What strategies and best practices can organizations adopt to streamline IAM compliance processes? Organizations can streamline IAM compliance processes by:
- Implementing automated identity provisioning and de-provisioning.
- Conducting regular access reviews and audits.
- Establishing a comprehensive identity governance framework.
- Providing regular training on IAM policies and procedures.
- Implementing multi-factor authentication for enhanced security.
- Collaborating across departments for a unified IAM strategy.
- Staying informed about evolving regulatory requirements.
- Utilizing IAM solutions that align with industry best practices.


















