SOC 2 Compliance : Meaning, Importance, Certification, Report, Audit

Businesses today face increasing pressure to safeguard sensitive customer data and preserve trust. IBM reported that 70% of the organizations faced significant disruption to business due to data breaches in 2024. Also, compared to 2023, the costs from lost business and post-breach response rose nearly 11%, underscoring the need for robust cybersecurity.
SOC 2 certification is a comprehensive framework designed to ensure organizations have the controls in place to safeguard customer data and meet industry standards.
Companies, especially those in regulated sectors like healthcare (HIPAA) and finance (FINRA, PCI-DSS), may face legal repercussions related to non-compliance with mandatory compliance standards/frameworks. On the contrary, SOC 2 is a voluntary framework designed to demonstrate the organization’s commitment to data security and to build trust with stakeholders.
In this blog, we’ll explain SOC 2, why it matters, how to get certified, and how SOC 2 audits can enhance your company’s trust and security.
What is SOC 2?
SOC 2 is a voluntary cybersecurity certification that evaluates a service organization’s controls related to security, availability, processing integrity, confidentiality, and privacy. It is part of the broader SOC (System and Organization Controls) framework, which also includes SOC 1 and SOC 3 reports. Service providers in industries such as healthcare, finance, and SaaS who store, process, or transmit customer data or handle sensitive information use it.
To achieve SOC 2 certification, organizations must enforce security controls, follow the Trust Service Criteria, and carry out an independent audit.
SOC 2 compliance helps organizations implement controls that can protect data, help identify and mitigate risks related to data security and vulnerability, and ensure the secure handling of sensitive information.
Why is SOC 2 important?

SOC 2 certification shows that a business follows best practices in securing customer data. It helps build trust with customers and meet industry rules.
These are some of the key benefits of SOC 2:
- Builds customer trust: SOC 2 certification shows that your organization follows strict security and privacy standards. This assures customers that you handle their data securely and responsibly.
- Enhances business reputation: Being SOC 2 certified can set your organization apart in a competitive market. It shows that you are committed to security and regulatory compliance.
- Attracts larger clients: Large enterprises and industries with strict security standards often require SOC 2 certification before forming partnerships or conducting business, which broadens your market opportunities.
- Improves internal security practices: The SOC 2 audit process helps identify and address potential security gaps, leading to stronger internal security protocols and better risk management.
What are the different SOC 2 trust principles?
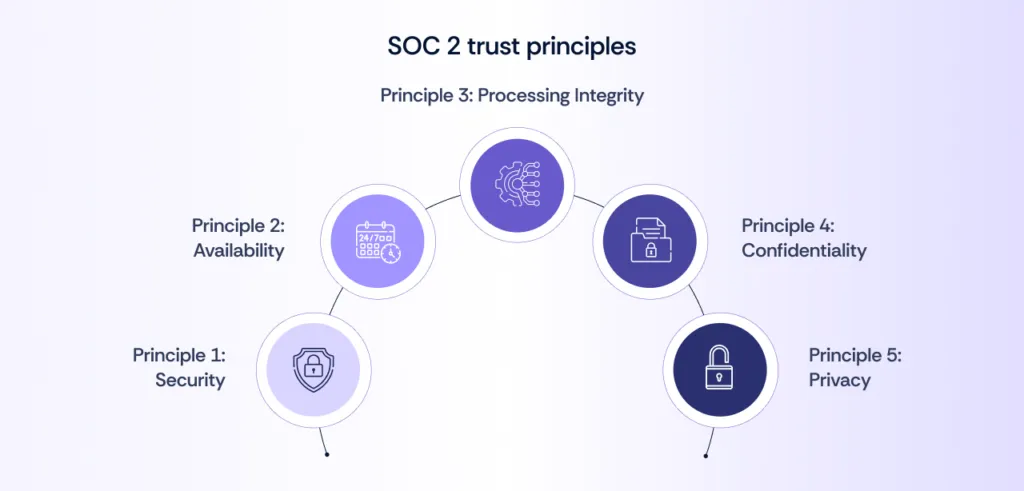
SOC 2 is based on five trust service criteria. These trust principles, also known as pillars of SOC 2, help organizations ensure they meet fundamental security, privacy, and data protection standards.
Each SOC 2 trust principle focuses on a different aspect of organizational processes. This ensures that the organization has addressed all areas of security and risk management.
Principle 1: Security
This principle, also called “common criteria,” is the only mandatory TSC in SOC 2. It serves to protect an organization’s systems against unauthorized access, use, or tampering. It implements safeguards like access control, monitoring, and risk management to maintain system security and protect customer data and internal systems.
Principle 2: Availability
The availability principle confirms that an organization’s systems and services are available for operation and use as agreed upon. This comprises having reliable systems, disaster recovery plans, and effective response strategies that help maintain uptime and meet service-level agreements (SLAs).
Principle 3: Processing integrity
This principle ensures that system processing is accurate, complete, and timely. It ensures that data is processed correctly per business requirements to prevent errors that could affect the integrity of the information.
Principle 4: Confidentiality
The confidentiality principle safeguards sensitive data from unauthorized access or disclosure. Organizations must take steps to protect customer data, intellectual property, and other confidential information. This includes secure handling, storage, transmission, and disposal of the data.
Principle 5: Privacy
The privacy principle ensures that organizations collect, store, and manage personal information in ways that comply with privacy laws. It ensures they follow practices to protect the privacy of individuals’ data. This includes securing personally identifiable information (PII) and obtaining proper consent.
To ensure proper handling of personal data, follow these steps:
- Obtain consent from the individual whose information you are collecting.
- Collect only the necessary data relevant to the stated purpose.
- Gather the information lawfully and in compliance with applicable regulations.
- Ensure the data is accurate, complete, and relevant to the intended use.
- Use the information only for the intended purpose communicated to the individual.
- Secure the data to prevent unauthorized access, disclosure, or alteration.
- Allow individuals access to review, update, or correct their personal data.
- Manage third-party disclosures to ensure consistent data protection.
- Dispose of the information securely once it is no longer needed.
- Monitor and enforce compliance with privacy policies and address privacy complaints.
What are SOC 2 compliance controls?
The SOC 2 controls consist of requirements derived from the five Trust Service Criteria. These controls cover processes, procedures, and systems that aim to protect customer data and ensure compliance with SOC 2 standards.
They manage operational aspects related to data backup, recovery protocols, and regular software updates. They also address safeguards such as encryption, secure data storage, and firewalls. Each control addresses specific risks to protect sensitive information from internal and external threats.
How to choose SOC 2 controls?
- Choose controls based on a thorough risk assessment and your customers’ security needs.
- Prioritize controls that address your most critical risks, ensuring efficient use of resources and enhancing security.
- This approach builds a strong, adaptable security posture that evolves with your business.

Key elements of SOC 2 control list
A SOC 2 control list outlines the processes, procedures, and systems that an organization upholds to safeguard customers’ data and comply with the SOC 2 standards.
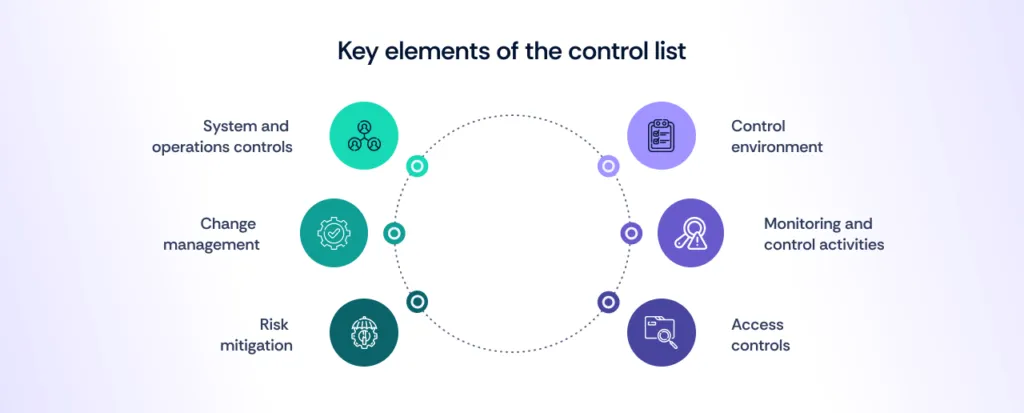
Some of the key elements of the control list include:
- Control environment: Focus on integrity and ethics, with senior management’s involvement to hold the organization accountable for reaching its goals.
- Monitoring and control activities: Focus is on continued assessments that help identify and address weaknesses so that security standards are followed.
- Access controls: Focuses on protecting information through hardy logical and physical access controls—this includes managing credentials and preventing unauthorized facility access.
- System and operations controls: Focuses on monitoring system changes and setting up incident response plans in case of security breaches.
- Change management: Focuses on approving and enforcing changes to ensure they align with security and organizational goals.
- Risk mitigation: Focuses on identifying risks and developing strategies to reduce impact—includes carrying out incident response plans.
What is a SOC 2 audit?
Preparing for a SOC 2 audit requires planning to meet AICPA’s (American Institute of Certified Public Accountants) criteria. Typically performed by an independent auditor, the audit is usually done annually, with additional audits for significant changes in systems or processes.
First, define the audit scope based on relevant Trust Service Criteria, such as security or availability.
Next, review your controls, policies, and procedures, identifying and addressing any gaps before the audit.
Finally, undergo the audit, where the auditor will assess your systems and controls. Tools like Scrut can help automate compliance tracking and evidence gathering throughout the process.
The SOC 2 audit process includes testing controls, collecting documentation, and verifying that your organization meets SOC 2’s security and privacy requirements.
How does a SOC 2 audit process look like?
A. Planning and scoping
- Define audit scope: Identify the systems, processes, and services to be audited and align with relevant Trust Services Criteria (TSC).
- Set timeline: Work with the auditor to establish a realistic timeline, including milestones and deadlines.
B. Risk assessment
- Identify risks: Conduct a risk assessment to spot potential threats to data security, availability, integrity, confidentiality, and privacy.
- Document mitigation controls: Record controls in place to reduce identified risks, including policies and technical safeguards.
C. Control testing
- Evaluate controls: Assess the design and effectiveness of controls to ensure they meet objectives.
- Test controls: Select a sample of controls for testing, including reviewing documents, observing processes, and checking system logs.
D. Gathering evidence
- Collect documentation: Gather policies, procedures, logs, and incident reports to support control existence and operation.
- Employee interviews: Interview key staff to verify control understanding and adherence to security measures.
E. Reporting
- Prepare SOC 2 report: Work with the auditor to draft the report, including an opinion letter and details of controls, deficiencies, and their severity.
- Report content: The report includes the auditor’s opinion, control testing results, and any improvement recommendations.
F. Remediation and follow-up
- Address issues: Develop remediation plans for any identified control weaknesses and document resolutions.
- Drive improvement: Use audit insights to improve controls and regularly update policies to address evolving risks.
What is a SOC 2 report?
SOC 2 is an audit report that evaluates how well a service organization follows the Trust Service Criteria for data security, availability, processing integrity, confidentiality, and privacy.
The report includes an assessment of the organization’s controls, their effectiveness, and how they align with SOC 2 standards. Organizations may share this information with third parties to demonstrate a strong control environment.
What are the different types of SOC 2 reports?
An independent third-party auditor typically creates SOC 2 reports after an audit. They are valid for one year. There are two types of SOC2 reports:
- Type I: Assesses the design and implementation of controls at a specific point in time.
- Type II: Evaluates both the design and operational effectiveness of controls over a specified period (usually 6 to 12 months).
Each SOC 2 report type helps organizations demonstrate their commitment to data security and compliance, with Type II providing a more comprehensive view of ongoing control effectiveness.
SOC 2 Type 1 evaluates control design at a specific point in time, while Type 2 assesses control effectiveness over 6-12 months. Type 1 shows controls are properly designed, and Type 2 ensures they work effectively over time. Both protect sensitive data and are shared privately with relevant parties.
Is SOC 2 Type 1 the same as SOC 2 Type 2?
No, SOC 2 Type 1 and SOC 2 Type 2 are not the same. The major difference lies in the scope of evaluation.
SOC 2 Type 1 assesses the design and implementation of controls at a specific point in time, while SOC 2 Type 2 evaluates both the design and the operational effectiveness of controls over a specified period (usually 6 to 12 months).
Type 2 provides a more comprehensive view of how controls function over time, offering greater assurance to customers about ongoing compliance.
How soon can you get SOC 2 certified?
The timeline for SOC 2 certification varies depending on the organization’s readiness and the complexity of its systems. On average, it can take 3 to 6 months to get SOC 2 Type I certified. On the other hand, SOC 2 Type 2 certification takes longer, typically around 6-15 months.
This includes the time needed for gap analysis, implementing necessary controls, documenting processes, and preparing for the audit.
How much does a SOC 2 audit cost?
The cost of a SOC 2 audit varies depending on factors such as the size of the organization, the complexity of its systems, and the service provider chosen for the audit.
On average, it can range from $10,000 to $50,000. This includes preparation costs, audit fees, and any necessary system improvements.
Smaller organizations may fall on the lower end of the spectrum, while larger enterprises with more complex systems may incur higher costs.
Can SOC 2 compliance software help you become SOC 2 certified?
Yes, SOC 2 compliance software helps you obtain SOC 2 certification seamlessly with features like continuous monitoring, real-time risk assessments, automated evidence gathering, and integration with existing systems so that your organization stays on track with SOC 2 requirements. These tools reduce manual effort and human error while speeding up audit preparation, making it easy to show compliance at all times.
What are the popular SOC 2 compliance software?
Many SOC 2 compliance software options are available, with the most popular ones being those with high ratings or strong customer reviews. Some popular SOC 2 compliance software solutions include:
- Scrut Automation
- Drata
- Vanta
These platforms offer automation, continuous monitoring, and integration features to simplify the SOC 2 compliance process.
How can Scrut help your SOC 2 certification journey?
Getting SOC 2 compliant using Scrut’s platform is a seamless and error-free experience. From identifying controls and control gaps to mapping them to the required trust services criteria, your SOC 2 journey with Scrut is streamlined from the start.
Here’s how Scrut helps:
1. Streamlined compliance journey
Scrut’s all-in-one platform streamlines SOC 2 implementation and management. Automated evidence collection and workflows minimize the manual workload and ensure error-free documentation.
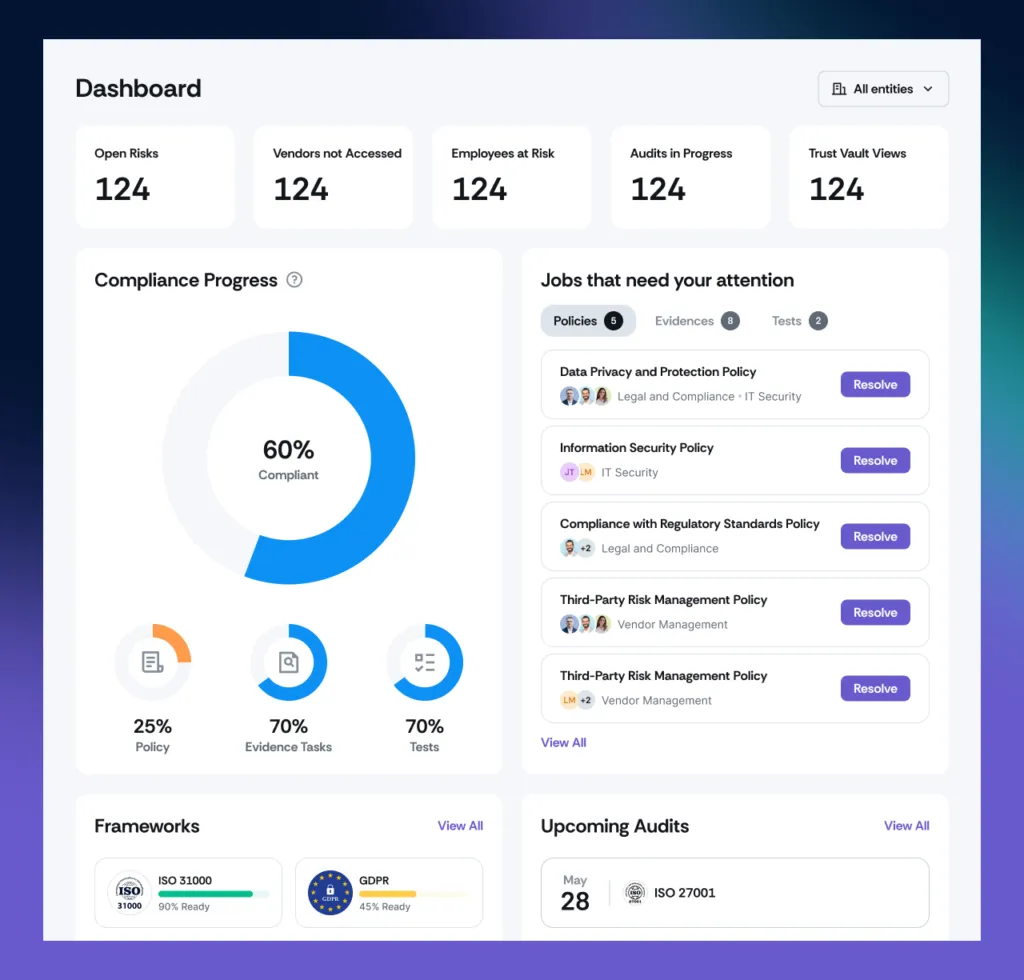
2. Continuous monitoring
Scrut dashboards help you monitor compliance non-stop, quickly identifying compliance control gaps. You will receive real-time alerts and always stay ahead of possible security risks.
3. Expert consultation
Scrut offers expert advice to help you navigate SOC 2 requirements for your organization. Industry best practices will also help strengthen your compliance posture.
4. Improved data security
Two-factor authorization on Scrut’s platform helps ensure your data is stored safely and access is controlled. Scrut’s integrated risk management tools help secure sensitive information.
5. Seamless integration
Scrut seamlessly integrates with your existing systems, enabling seamless data flow with minimum interruption during the entire compliance process.
6. Market differentiation
Scrut gives its market segment and competitors a complete platform that provides vulnerability scanning, third-party risk management, continuous control monitoring, and modules for employee security training. This saves the cost of investing in separate tools for each.
Schedule a demo to explore how Scrut’s unique features can accelerate your SOC 2 compliance journey and enhance your overall governance framework.

Frequently Asked Questions
1. What kind of SOC 2 compliance documentation should be created?
SOC 2 compliance documentation should include various key documents that outline your organization’s policies, procedures, and controls related to security, availability, confidentiality, and other Trust Service Criteria. Essential documentation includes a system description, policies and procedures, risk assessment and mitigation plans, and evidence of compliance, such as logs and audit trails.
2. Is it necessary to write a SOC 2 system description?
Yes, it is necessary to write a SOC 2 system description. It details the scope of services that are under review. It also states how the organization’s systems meet SOC 2 criteria in terms of infrastructure, software, policies, and processes. This document is foundational for both Type 1 and Type 2 audits, helping auditors understand the operational context and ensuring alignment on security and compliance standards.
3. What kind of business can be SOC 2 certified?
Any business that handles sensitive customer data or provides services involving data security can pursue SOC 2 certification. This includes but is not limited to, SaaS (Software-as-a-Service) providers, Tech and IT companies, healthcare providers, financial services, and e-commerce platforms.
SOC 2 certification is vital for businesses that wish to build trust with customers, demonstrate commitment to security best practices, and comply with industry standards. Any organization that interacts with or stores sensitive data is a candidate for SOC 2 certification.
4. Who are SOC 2 auditors?
SOC 2 auditors are independent third-party professionals or firms that evaluate an organization’s adherence to the SOC 2 Trust Service Criteria. They should have relevant qualifications, such as certifications in auditing and information security, including CPA (Certified Public Accountant) or CISA (Certified Information Systems Auditor).
These auditors must be external to the organization to ensure impartiality and objectivity in the audit process. SOC 2 auditors assess the effectiveness of the organization’s controls over security, availability, confidentiality, and privacy, providing a detailed report based on their findings.
5. Is it necessary to get SOC 2 attestation?
No, while it is not mandatory, obtaining SOC 2 attestation from an independent auditor provides verification that an organization has implemented necessary controls to meet the SOC 2 Trust Service Criteria, helping to build customer trust and reduce security risks. Getting SOC 2 attestation is highly beneficial for businesses that need to demonstrate their commitment to security, availability, confidentiality, and privacy standards.
6. How different is SOC 2 from SOC 1 standards?
The main difference between SOC 2 and SOC 1 is their focus: SOC 1 evaluates controls over financial reporting, specifically for service organizations impacting financial operations, while SOC 2 focuses on data security, privacy, availability, and confidentiality for technology and cloud-based organizations, making it ideal for service organizations handling sensitive customer data.
7. Does SOC 2 require penetration testing?
No, SOC 2 does not explicitly require penetration testing, but it is often a recommended practice to evaluate the effectiveness of security controls by simulating cyberattacks and identifying vulnerabilities, helping to ensure alignment with the Trust Service Criteria CC4 for security.
8. Why is being SOC 2 compliant important?
Being SOC 2 compliant is important as it helps you to build trust and reputation with clients and stakeholders. It shows that your organization places emphasis on data security and privacy. It helps protect sensitive customer information, aligns with industry standards, and reduces risks of data breaches. This helps your business run without disruptions. Compliance generally makes audits easier and offers some buffer against legal and reputational risks.