How to establish a company-wide infosec policy?

According to the 2022: Hackers Powered Security Report, 92% of hackers say they can find vulnerabilities that scanners cannot. In 2022 alone, hackers found 65,000 vulnerabilities that might be used to steal information from organizations worldwide. This only reiterates how organizations need to work on their information security posture. Every organization requires a company-wide security policy that will protect its data and other information assets.
Establishing an infosec policy throughout the organization is not an easy ask, but it is certainly the need of the hour. If you want to form your infosec policy or review what you have missed to include in your policy, you are in the right place. In this article, we will discuss the components as well as the purpose of establishing a company-wide information security policy, along with a step-by-step guide on how to implement it.
What is information security policy?
Information security, also called infosec for convenience, is a sum-total of the actions taken to protect digital or physical information as well as prevent unauthorized disclosure, disruption, access, use, and modification of an organization’s data. It also contains detail on how to mitigate information risks.
This information includes, but is not limited to, the following:
- Personally identifiable information (PII) of stakeholders, including customers, suppliers, and investors
- Intellectual property (IP)
- Internal or external communication
- Financial information

However, let us first clarify the difference between infosec policy and infosec procedure. Infosec policy is the policy designed to protect the organization’s data assets, while procedures are the actions recommended to follow the policy. On the other hand, infosec tools are the software, hardware, and applications used to protect information.
What is the purpose of infosec policy?
Every organization has its own infosec policy, created after keeping in mind the data the organization stores, the size of the organization, etc.
But the important question is why an organization requires an infosec policy. Let’s discuss some of the purposes a robust infosec policy fulfills:
Information security
Infosec policy provides a framework for the organization to protect its information from unauthorized access and security threats. It describes all the aspects of security controls, including access control, encryption requirements, and data handling processes to ensure the security of information.
Risk management
Information security policy helps the organization minimize the risk associated with data processing. It describes the policies and procedures to deal with risk assessment, detection, mitigation, and incident response. Therefore, the employees are aware of what is expected of them in every situation. Documentation of the policy helps in the detection of vulnerabilities and mitigation of risk rather quickly. It also helps in minimizing the effects of a security incident.
Compliance
With the help of an infosec policy, the organization can ensure compliance procedures throughout the organization. Compliance regulations and frameworks like HIPAA, GDPR, SOX, and FISMA have specific expectations regarding data security, access control, and data breach. A well-formed infosec policy helps you meet compliance requirements.
Employee awareness
An infosec policy can help employees know what is expected from them on a day-to-day basis with regard to data protection. Access control helps the organization in limiting data sharing on a need-to-know basis. The employees are also aware that only the information they need to perform their duties will be shared with them. Moreover, the infosec policy also mentions the actions to be taken against the employees if the policy is not followed. Thus, they will behave accordingly.
Organization’s reputation
Infosec policy provides the stakeholders the assurance that the organization takes the security of their data seriously and is doing everything possible to protect it. The policy has guidelines for every type of situation, including security incidents, data backup, and recovery. Therefore, if the organization is breached, the organization doesn’t waste time deciding what to do but follows the policy instantly.
What are the components of infosec policy?
There are nine components of infosec policy:
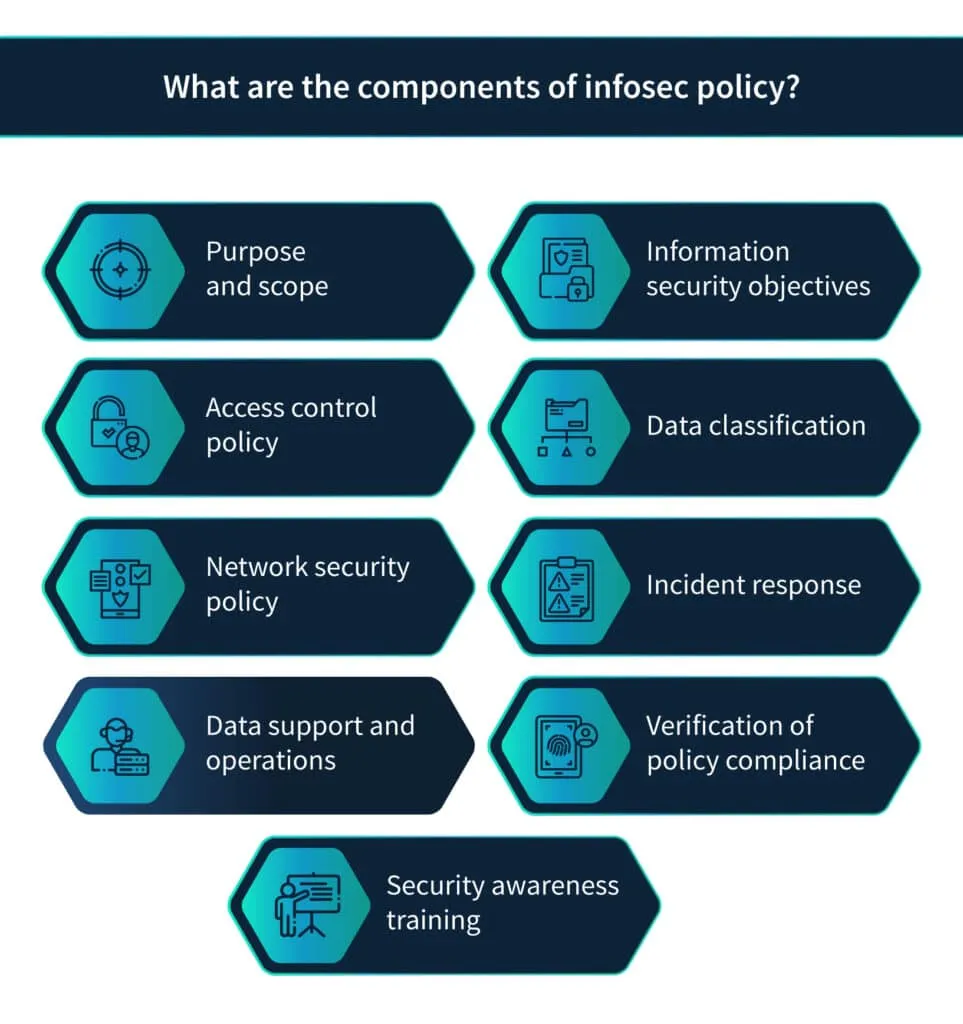
Purpose and scope
As we discussed in the previous section, the purpose of infosec policy is different for every organization. However, the organization should mention its goals at the very beginning of the policy.
Following this purpose, the scope of the document must be shared as well. Scope refers to the parties it applies to as well as the department it doesn’t cover.
For example, if an organization has two divisions – manufacturing and research & development (R&D), the infosec policies for both departments might be different. Hence, the policy of the manufacturing department should mention that the employees of the R&D division are not included in the scope and vice versa.
Information security objectives
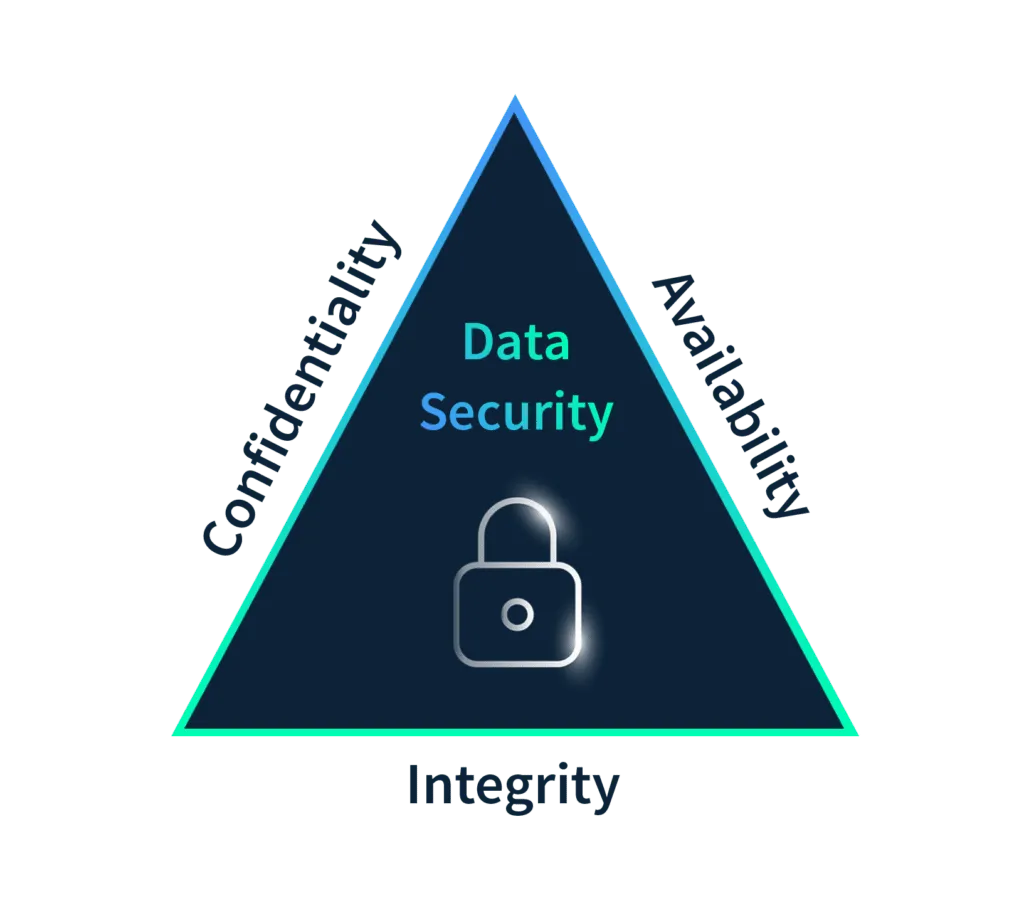
Information security policy must state its objectives clearly. Information security focuses on the well-known CIA triad as described below
- Confidentiality: The information should remain confidential unless an individual needs it to perform their duties. For example, a product manager does not need to disclose their data to a security guard.
This principle applies even if we are talking about loyal employees who have been in service for years. The reason is humans are susceptible to errors and might give out the information inappropriately to others. Did you know Verizon found that 82% of the breaches involved the human element? Hence, maintaining confidentiality is paramount in the infosec policy.
- Integrity: Integrity means that the data should not have been tampered with in any manner. It should be complete, intact, and accurate. A person accessing the data should be able to rely on it.
For example, if a doctor has recommended some tests and the laboratory gives back only a part of those tests or changes the data on the test results, the patient’s life might be at risk. The same applies to all kinds of data.
- Availability: The data should be available when an authorized person needs it. If the data is not available on time, it loses its validity.
For instance, if a CEO makes a strategic decision without real-time data, the decision might ricochet.
Access control policy
Access control policy restricts data access to unauthorized users. But who will decide who is authorized and who is not? The organization’s management can decide on someone with authority to decide the access.
However, organizations often must follow the rules and regulations set up by the government and other authorities, like GDPR, CRPA, or HIPAA. The organizations can only share information that they are allowed to share; otherwise, they might face penalties and fines.
In addition to this, some organizations, such as suppliers or customers, are contractually obligated to keep the information private.
Network security policy
The network security policy is the policy to access the networks and servers of the company. It also includes a password policy, authentication policy, multi-factor authentication, biometrics, or ID cards.
For instance, the company can direct the employees to reset their passwords quarterly or allows a limited number of employees to access the servers.
Data classification
Every organization must have specific guidelines to classify the data, called data stewardship. Access must be given on a need-to-know basis. Meaning if you do not need it, you do not get access to information. Generally, data is classified into four categories for granting access.
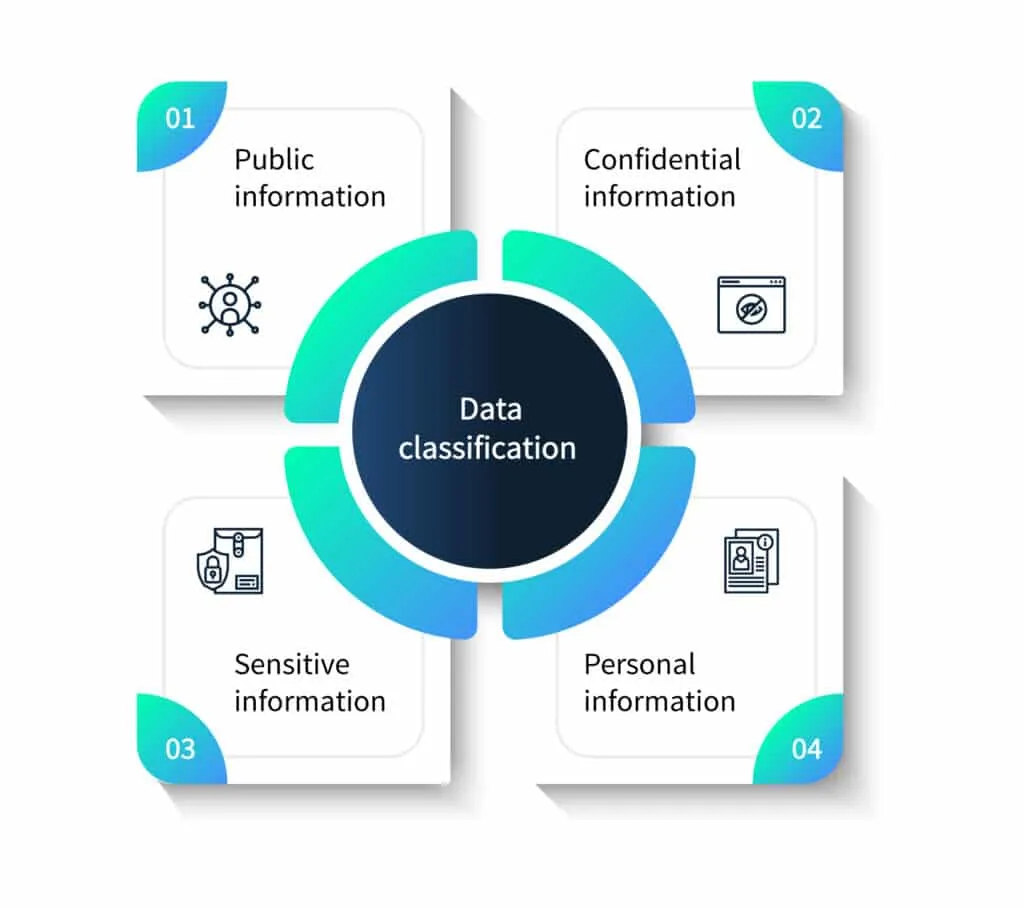
- Public information: This type of information is accessible to the general public. Sometimes such information is recommended by the government to be disclosed to the public. For example, public companies must disclose their financial information to the general public.
- Confidential information: Access to confidential data is restricted to a very limited number of people. There might be legal restrictions about sharing confidential information too. For instance, HIPAA in the US bans sharing patients’ health information.
- Sensitive information: Sensitive information is highly sensitive information that might prove harmful to the organization or its stakeholders if it were leaked. This information might even prove harmful to the state or country.
- Personal information: Personally identifiable information (PII) is information that can reveal the identity of the person it belongs to. This is why PII cannot be shared with anyone not legally authorized.
Data support and operations
This component of data security describes how the data should be stored and transferred.
- Data protection: Inherently, all data should be treated as confidential and protected. However, PII and other sensitive data must be protected by implementing stricter policies. Data-at-rest refers to the data that is stored – temporarily or permanently – on a drive or a cloud. This data should be encrypted to protect it from unauthorized access.
- Data movement: When data is transferred from one node to another, it is called data in motion. Data in motion must be secured using SSL/TLS certificates to protect it from cyber attacks, including man-in-the-middle attacks. An organization must restrict the use of open, public networks for accessing data.
- Data backup: Infosec policy must include the process of taking backups of all the data. The backup should be stored in a different location from the main data to secure it from physical damage such as fire or flooding. Backups must not be stored on the same device and network. As a result, if there is a ransomware attack and the organization is unable to access its data, it can use the backup.
Security awareness training
If your employees do not follow the infosec policies, your information is not safe at all. The infosec policy must be communicated to all employees regardless of their posts. Secondly, they must be trained to follow hygienic practices to access data.
They should be made aware of social engineering techniques frequently used by the actors in order to protect the organization’s data. They must also be educated on what a cyber attack looks like.
The employees who handle sensitive information must be trained over and above the regular employees.
All employees must follow the clean desk policy. Meaning no papers should be left on the desk at the end of the working day. Laptops must be locked in, and computers shut properly.
An organization can blocklist websites that are known for phishing, including porn and gambling sites. No employee should be able to access these websites.
Also, the employees must be held accountable for their actions. They must be penalized if they do not follow the infosec policy set up by the organization.

Incident response
The infosec policy of the organization should clearly mention the steps to be taken in case of a breach. The initial response plan should be in place and communicated to all employees. They should know who to contact if they find an intruder in their system.

Verification of policy compliance
In this section, an organization should mention the tests and procedures to verify whether the policy is followed throughout the organization. Some examples of verification are penetration testing, assessments, and exercises.
A step-by-step guide to preparing an infosec policy

To sum up
A policy formed by an organization to protect the information it generates, collects, and transfers are called the information security policy, also called the infosec policy. We saw the benefits of the infosec policy and how to form a robust policy. However, every organization’s requirement is different; therefore, you are the best judge of what you should include in your infosec policy.
Employee awareness training is one of the most important aspects of the infosec policy of an organization. Scrut can help you in training your employees through different programs. You can also keep an eye on how they are performing via an automated dashboard.
FAQs
What is information security or infosec?
Information security or infosec refers to the protection of information generated, collected, processed, or transmitted by an organization from unauthorized access. Every organization has a tailor-made information security policy to protect its physical and digital information.
Which type of information is included in the infosec policy?
The infosec policy refers to the protection of both – physical and digital – information from unauthorized access. The information that is stored on papers and diaries is called physical information, while the information stored on a cloud or the internet is called digital information.
What are the different types of data?
Data can be divided into four categories depending on its relevance:
1. Public data
2. Confidential data
3. Sensitive data
4. Personal data


















