NYDFS cybersecurity regulation: Requirements, penalties, and compliance tips

When it comes to cybersecurity in the financial sector, New York is not just reacting to threats. It is setting the rules of the game. The NYDFS Cybersecurity Regulation (23 NYCRR Part 500) is a comprehensive framework designed to protect customer data and strengthen operational resilience across banks, insurers, and other financial services companies under New York’s jurisdiction.
This is far from optional. Enforcement actions have made it clear that the stakes are high. Recently, PayPal faced a $2 million civil fine after credentials were exposed due to weak training and a lack of multi‑factor authentication (MFA) on Forms 1099‑K, while two insurers (Geico & Travelers) settled for a total of $11.3 million in penalties after attackers stole data from auto insurance portals that did not use MFA.
In this blog, we will break down what the NYDFS Cybersecurity Regulation means, who it applies to, the critical requirements organizations must meet, and a step-by-step guide to achieve compliance.
What is NYDFS cybersecurity?
The NYDFS Cybersecurity Regulation, officially 23 NYCRR 500, is New York State’s rulebook for keeping financial institutions safe from cyber threats. It took effect on March 1, 2017, and starting February 15, 2018, institutions had to submit an annual compliance certificate.
At its heart, the regulation demands that covered entities build and sustain a cybersecurity program that:
- Fits their unique risk profile, including data they hold and systems they use
- Maintains policies on everything from data protection to incident response
- Appoints a Chief Information Security Officer (CISO) to oversee cybersecurity
- Implements technical controls like access management, vulnerability scanning, MFA, and encryption
- Conducts risk assessments, testing, and staff training
- Reports breaches, within 72 hours if they threaten operations or sensitive data, and annually certifies its compliance.
Who must comply with NYDFS cybersecurity?
The NYDFS Cybersecurity Regulation applies broadly to organizations supervised by the New York Department of Financial Services. If your business operates under a license, registration, charter, certificate, permit, or similar authorization from NYDFS, you are considered a covered entity and must comply with Part 500.
Covered entities include:
- State-chartered banks and credit unions
- Foreign banks licensed to operate in New York
- Mortgage companies, licensed lenders, and money transmitters
- Trust companies, private bankers, and service contract providers
- Insurance companies and agents or brokers conducting business in New York
- Health maintenance organizations (HMOs) and continuing care retirement communities (CCRCs)
Class A companies: heightened requirements for large organizations
Under the 2025 amendments, NYDFS introduced a new Class A designation for larger institutions. Covered entities are classified as Class A companies if they meet either of these thresholds:
- More than 2,000 employees (including affiliates and contractors) averaged over the past 12 months.
- Over $1 billion in gross annual revenue averaged over the past three fiscal years (including affiliates, globally).
While all covered entities must meet the core requirements of Part 500, Class A companies face enhanced obligations. This category reflects NYDFS’s recognition that large organizations carry greater responsibility for safeguarding the financial system.
Who is exempt from NYDFS cybersecurity?
While NYDFS Part 500 applies broadly, Section 500.19 of the regulation outlines specific exemptions for certain entities. These exemptions are designed to account for variations in organizational size, structure, and risk exposure.
1. Full exemptions
Some organizations do not need their own cybersecurity program under Part 500 if they are already covered by another entity’s program. This applies to:
- Employees, agents, representatives, designees, or wholly owned subsidiaries of a covered entity, provided they are fully protected by the parent entity’s cybersecurity measures
- Inactive individual insurance brokers or agents who have no access to nonpublic information, systems, or policy activity for at least a year
- Certain niche insurers, such as charitable annuity societies, risk retention groups not chartered in New York, and accredited reinsurers
These entities must still file a Notice of Exemption within 30 days of qualifying.
2. Limited exemptions (small entity carve-out)
Smaller firms may qualify for limited exemptions if they meet all of the following criteria:
- Fewer than 20 employees, including contractors
- Less than $7.5 million in annual revenue globally (including affiliates)
- Less than $15 million in total year-end assets (including affiliates)
Entities that meet these thresholds are exempt from some specific requirements, such as testing, logging, multi-factor authentication, and incident response. However, they must still:
- File a Notice of Exemption within 30 days of qualifying
- Maintain a basic cybersecurity program and policy, conduct risk assessments, apply access controls, manage third-party risks, retain data appropriately, and report incidents
- Submit an annual certification or acknowledgment of compliance for the applicable sections
What if the exemption status changes?
If a company no longer qualifies for an exemption, perhaps due to growth in size or revenue, it has 180 days to fully comply with all NYDFS Part 500 requirements.
What are the NYDFS cybersecurity requirements?
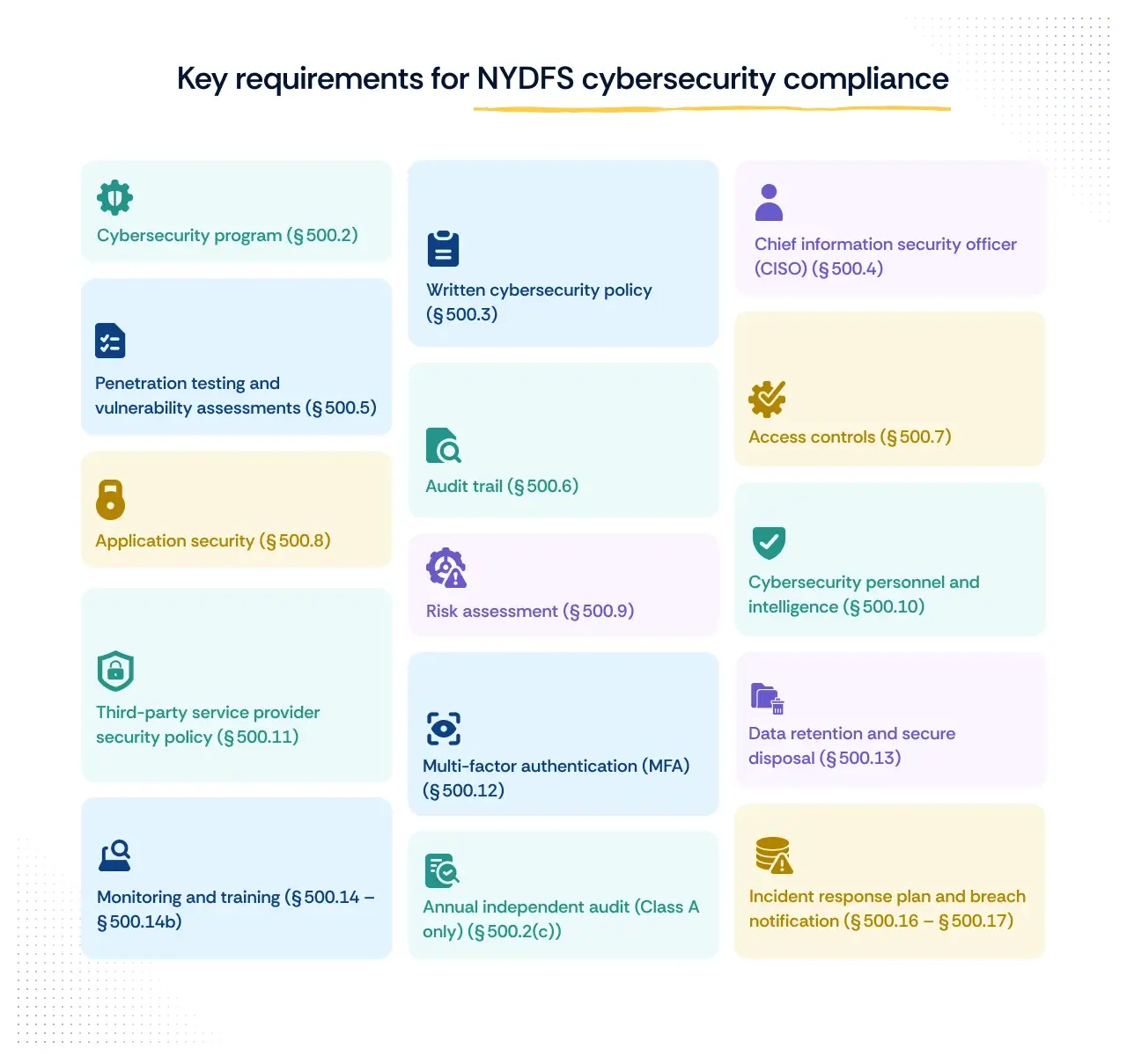
The NYDFS Cybersecurity Regulation establishes 14 core requirements that form a robust framework for protecting sensitive data and systems. With the 2025 amendments now in effect, these requirements reflect a stronger focus on continuous monitoring and advanced technical controls.
Here’s what organizations must implement:
1. Cybersecurity program (§ 500.2)
Develop and maintain a cybersecurity program to protect the confidentiality, integrity, and availability of information systems. Regular risk assessments should inform the program and include measures for detecting, responding to, and recovering from cybersecurity events.
2. Written cybersecurity policy (§ 500.3)
Establish a board-approved cybersecurity policy covering areas such as data governance, access controls, business continuity, and third-party vendor management.
3. Chief information security officer (CISO) (§ 500.4)
Designate a qualified CISO to oversee and enforce the cybersecurity program. This role may be filled internally or by an approved third-party provider.
4. Penetration testing and vulnerability assessments (§ 500.5)
Implement automated vulnerability scanning across information systems and manually review unscanned areas. Class A companies must also deploy endpoint detection and response (EDR) solutions and centralized logging to strengthen monitoring.
5. Audit trail (§ 500.6)
Maintain systems capable of reconstructing material financial transactions and detecting cybersecurity events. Retain these records for at least five years.
6. Access controls (§ 500.7)
Enforce the principle of least privilege. Perform regular privilege audits, promptly disable inactive accounts, and secure remote control protocols.
7. Application security (§ 500.8)
Establish secure development practices for in-house applications and evaluate externally sourced software for vulnerabilities.
8. Risk assessment (§ 500.9)
Conduct regular risk assessments to identify threats, evaluate controls, and ensure the cybersecurity program evolves with the business and threat landscape.
9. Cybersecurity personnel and intelligence (§ 500.10)
Employ qualified personnel or engage third-party experts to manage cybersecurity. Provide regular training to employees on identifying and responding to threats such as phishing and social engineering.
10. Third-party service provider security policy (§ 500.11)
Develop and enforce policies to ensure vendors meet your cybersecurity standards. Conduct periodic reviews of their security posture.
11. Multi-factor authentication (MFA) (§ 500.12)
Require MFA for all users accessing information systems, not just remote and privileged accounts. Class A companies must also implement password filtering to block weak or commonly used passwords.
12. Data retention and secure disposal (§ 500.13)
Limit retention of nonpublic information to what is necessary for business or legal purposes and securely dispose of data that is no longer needed.
13. Monitoring and training (§ 500.14 – § 500.14b)
Maintain a detailed inventory of all information assets, including their owners, locations, classifications, support end dates, and recovery time objectives.
14. Incident response plan and breach notification (§ 500.16 – § 500.17)
Create and maintain a written incident response plan that covers detection, response, recovery, and communication workflows. Report cybersecurity events that materially affect operations or expose nonpublic information to NYDFS within 72 hours of determining an incident has occurred.
For Class A companies: In addition to incident reporting, notify NYDFS within 72 hours if a ransom payment is made. Submit a detailed report within 30 days explaining the decision, alternatives considered, and compliance with applicable laws.
15. Annual independent audit (Class A only) (§ 500.2(c))
Class A companies must engage qualified independent auditors to review the design and effectiveness of their cybersecurity program annually. The audit findings must be reported to senior management and the board, and remediation plans must be developed for any gaps identified.
New in 2025: What’s changed?
The Second Amendment to the NYDFS Cybersecurity Regulation introduced new requirements and strengthened existing ones. Key updates include:
- Expanded MFA (§ 500.12): Now mandatory for all users accessing information systems, not just for remote access or privileged accounts.
- Continuous vulnerability management (§ 500.5): Requires automated scans and manual reviews of unscanned systems.
- Privileged access management (Class A): Large organizations must deploy privileged access solutions and enforce password filtering to block weak passwords.
- Endpoint detection and response (Class A): Mandatory deployment of EDR solutions and centralized logging for Class A companies.
- Asset inventory (§ 500.13): Covered entities must maintain a complete and updated inventory of all information assets.
- Ransom payment reporting (Class A): Class A companies must notify NYDFS within 72 hours of making a ransom payment and provide a detailed explanation within 30 days.
- Annual independent audit (Class A): Class A companies must have their entire cybersecurity program independently audited each year and report findings to senior management and the board.
These changes reflect NYDFS’s push toward proactive, continuous cybersecurity rather than periodic, checklist-driven compliance.
How to become NYDFS compliant?
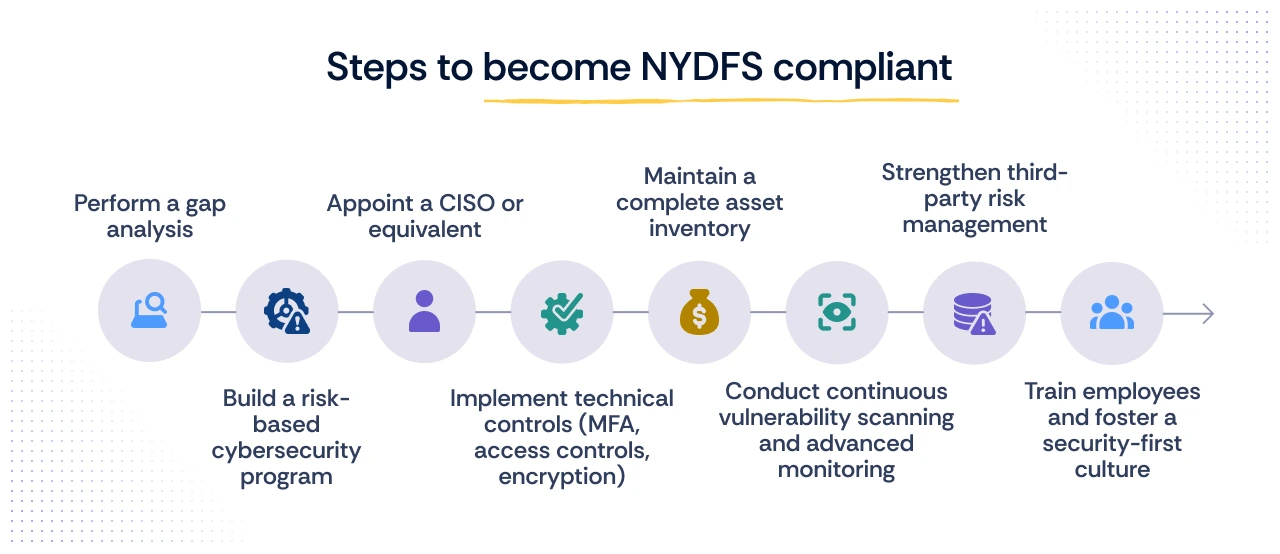
Complying with NYDFS Cybersecurity Regulation is not a one-time sprint—it’s a strategic roadmap that demands continuous attention. The 2025 amendments have raised the bar, making proactive measures and advanced technical controls non-negotiable. Here’s how to get there:
Step 1: Perform a gap analysis
Begin by evaluating your current cybersecurity posture against the full scope of Part 500, including the 2025 amendments. Identify gaps in areas like MFA for all users, continuous vulnerability scanning, and asset inventory management. Prioritize risks that could trigger regulatory scrutiny.
Lesson from First American Title: They knew of a critical vulnerability in their title-document portal but failed to act. This oversight led to sensitive data exposure and a $1 million fine. A thorough gap analysis could have surfaced and addressed the issue early.
Step 2: Build a risk-based cybersecurity program
Design a program tailored to your organization’s size, operations, and risk profile. Include controls for data protection, incident response, and governance. For Class A companies, this means planning for advanced requirements like endpoint detection and response (EDR) and centralized logging.
Lesson from OneMain Financial: Despite internal audits highlighting risks, the company did not update its policies or controls adequately. This failure to align their program with known risks contributed to their $4.25 million penalty.
Step 3: Appoint a CISO or equivalent
Designate a Chief Information Security Officer (CISO) or outsource to a qualified third party. Ensure they have the authority and resources to enforce the program effectively.
Step 4: Implement technical controls (MFA, access controls, encryption)
Expand MFA beyond remote and privileged accounts; it is now required for all users accessing information systems. Enforce least privilege principles, conduct regular privilege audits, disable unused accounts promptly, and secure remote access protocols. Class A companies must also deploy privileged access management solutions and enforce password filtering to block weak or commonly used passwords.
Lesson from OneMain Financial: Shared credentials stored in a folder literally named “PASSWORDS” left systems wide open. Robust access controls and MFA could have mitigated this glaring vulnerability.
Step 5: Maintain a complete asset inventory
Create and update a detailed inventory of all information assets, including ownership, location, classification, support end dates, and recovery time objectives. This inventory serves as the foundation for risk assessments and incident response planning.
Step 6: Conduct continuous vulnerability scanning and advanced monitoring
Move beyond periodic testing. Deploy automated vulnerability scans and perform manual reviews of unscanned areas. Class A companies must also implement EDR solutions and centralized logging to enhance visibility and response capabilities.
Lesson from First American Title: Lack of regular testing allowed a known vulnerability to persist unaddressed. Periodic testing would have revealed the flaw before it became a headline breach.
Step 7: Strengthen third-party risk management
Audit your vendors’ cybersecurity practices and ensure they align with your standards. Include security requirements in contracts and establish a schedule for periodic reviews.
Step 8: Train employees and foster a security-first culture
Regularly educate staff on cybersecurity threats, including phishing, social engineering, and safe data handling practices. A vigilant workforce is a key line of defense against breaches.
Lesson from OneMain Financial: Weak governance and poor staff awareness contributed to their enforcement action. Training can help turn employees from a vulnerability into a line of defense.
Step 9: Develop and test an incident response plan
Document roles, workflows, and communication protocols for responding to cybersecurity events. Test the plan regularly to ensure your team can act swiftly and comply with NYDFS’s 72-hour breach notification requirement.
For Class A companies: Expand your plan to include:
- Ransom payment notifications – Notify NYDFS within 72 hours if a ransom payment is made in response to an incident.
- 30-day detailed report – Provide NYDFS with a written explanation within 30 days, describing why the payment was necessary, what alternatives were considered, and how compliance with applicable laws was ensured.
Step 10: File annual certifications and monitor exemption status
By April 15 each year, file your Certification of Compliance or Acknowledgment of Non-Compliance with NYDFS. If your organization’s size or operations change, reassess whether you still qualify for any exemptions. Maintain detailed records to support your certification and prepare for potential audits.
For Class A companies: Conduct an annual independent audit of your cybersecurity program to evaluate both design and operational effectiveness. Share the results and remediation plans with senior leadership and the board.
Don’t wait for NYDFS to issue a fine; get ahead of the curve with these real-world lessons.
How do you renew NYDFS cybersecurity compliance?
Renewing compliance with NYDFS Cybersecurity Regulation requires covered entities to submit an annual Certification of Compliance by April 15, confirming they have met all applicable requirements over the previous calendar year.
Organizations must also review any changes to their exemption status and update their cybersecurity program to reflect evolving risks, technologies, or business operations. Renewal isn’t automatic; NYDFS expects evidence-backed confirmation that your program continues to meet the standards year after year.
What are the consequences of non-compliance?
Non-compliance with NYDFS Cybersecurity Regulation can have significant legal, financial, and reputational repercussions. The regulator’s authority under New York Banking Law § 44 gives it wide latitude to act against covered entities that fail to meet their obligations.
1. Financial penalties
NYDFS can impose daily fines for each violation:
- Up to $2,500 per day for general violations.
- Up to $15,000 per day if the violations form part of a pattern or pose a higher level of risk.
- Up to $75,000 per day for knowing or willful violations, or when failures threaten the institution’s safety and soundness or undermine public confidence.
These amounts are applied per violation, per day, meaning even short-lived non-compliance can escalate into millions of dollars in penalties.
2. Mandatory remediation and enhanced oversight
In addition to financial penalties, NYDFS may require non-compliant organizations to:
- Engage independent consultants to remediate deficiencies.
- Strengthen policies, procedures, and technical controls.
- Undergo heightened regulatory monitoring or periodic reporting until issues are resolved.
3. Reputational damage
Enforcement actions are publicized on NYDFS’s website and in press releases, often naming the company and outlining its failings. This public exposure can erode trust among customers, partners, and investors.
4. Operational disruptions
Regulatory remediation often demands urgent resource allocation, forcing organizations to divert attention from core business activities.
5. License risk
For severe or repeated violations, NYDFS has the authority to suspend or revoke a company’s license to operate in New York. While rare, this remains the regulator’s ultimate enforcement tool.
Enforcement patterns: lessons to learn
- Enforcement is escalating: NYDFS is taking action even for failures in basic controls (like MFA or access logging).
- Daily fines multiply fast: Non-compliance with multiple provisions results in large cumulative penalties.
- Industry-wide impact: These cases aren’t isolated; they send a clear signal that NYDFS expects effective cybersecurity every day of the year.
How Scrut helps you stay NYDFS-ready year after year
Scrut gives you the tools to not just achieve compliance but maintain it effortlessly. With the NYDFS Cybersecurity Regulation evolving in 2025 and enforcement becoming sharper, you need more than manual checklists; you need a system that works as hard as you do.
Here’s how Scrut helps:
- Automated gap analysis: Instantly map your current policies and controls against NYDFS Part 500 (including 2025 updates) to identify non-conformities.
- Continuous monitoring: Run daily automated checks for vulnerabilities, access issues, and third-party risks, keeping you ahead of breaches and fines.
- Pre-mapped controls and policy templates: Access 75+ expert-vetted templates to build a robust cybersecurity program faster.
- Vendor risk workflows: Assess and monitor third-party providers in line with § 500.11 requirements.
- Employee training modules: Turn your team into your first line of defense with ongoing, role-based awareness programs.
- Audit-ready reports: Maintain evidence trails and certifications to support your April 15 NYDFS filings and stay prepared for regulator reviews.
With Scrut, you don’t just tick boxes, you embed cybersecurity into the fabric of your operations, protecting your business and customers while avoiding costly enforcement actions.

FAQs
Is the NYDFS cybersecurity regulation applicable to banks?
Yes, the NYDFS Cybersecurity Regulation applies to all banks chartered or licensed by the New York Department of Financial Services. This includes state-chartered banks, foreign banks licensed to operate in New York, private bankers, and trust companies. Even if a bank is headquartered outside New York, it must comply if it operates under NYDFS supervision.
Is NYDFS part of New York’s cybersecurity law?
Yes, the NYDFS Cybersecurity Regulation is a key part of New York’s cybersecurity laws. It sets mandatory standards for financial institutions and other entities regulated by the New York Department of Financial Services to protect sensitive data and systems.
What is the eligibility for the NYDFS Cybersecurity Certificate of Compliance?
To be eligible (and required) to submit the NYDFS Certificate of Compliance, your organization must:
- Be a covered entity under NYDFS regulation (banks, insurers, lenders, money transmitters, trust companies, HMOs, etc.)
- Not qualify for a full exemption (e.g., fully covered affiliate or inactive agent)
- Not qualify for a limited exemption (small entities must instead file a Notice of Exemption and can submit an acknowledgment instead of full certification)
If you meet all the above, you must file the full certification by April 15 each year, affirming that your organization meets all applicable 23 NYCRR Part 500 requirements from the prior calendar year.
What is the 72-hour rule for NYDFS?
Under 23 NYCRR § 500.17, covered entities must notify the NYDFS within 72 hours after determining that a cybersecurity incident has occurred. This applies if:
- The incident requires notification to another regulatory or supervisory body, or
- The incident has a reasonable likelihood of causing material harm to any part of the organization’s normal operations.
This timeline begins once the organization becomes aware of the incident, not when the incident actually occurred. You must also provide updates as new or material information emerges.
Additional obligations for Class A companies
For Class A companies, the 2025 amendments added two more reporting requirements:
- 72-hour notification for ransom payments – Class A companies must notify NYDFS within 72 hours of making any ransom payment in response to a cybersecurity event.
30-day written explanation – Within 30 days of the ransom payment, they must submit a detailed explanation outlining why the payment was made, what alternatives were considered, and how legal compliance (e.g., with OFAC sanctions) was ensured.


















