How to Automate Your InfoSec Program with Scrut?

GRC software helps you manage your organization’s InfoSec program efficiently. It reduces the effort and time required to manage your governance, risk, and compliance-related tasks. That ultimately helps in building a strong InfoSec posture.
Scrut smartGRC eliminates over 70% of your time required in evidence collection, automatically detects cloud misconfigurations, and enables you to collaborate seamlessly with your internal teams.
InfoSec becomes more and more crucial as your organization grows and becomes more complex.
Scrut offers tools to manage all InfoSec tasks and workflows. Scrut InfoSec platform software provides many benefits to your organization. The tool delivers a robust approach to monitor your organization’s risk and compliance continuously.
This article discusses how the Scrut platform helps you automate your InfoSec program.
smartGRC
Scrut began as a compliance automation platform and has expanded to a ‘smart’ GRC platform built for cloud-native companies. Thus, we created the smartGRC platform, a single-window solution for risk visibility, information security, and compliance.
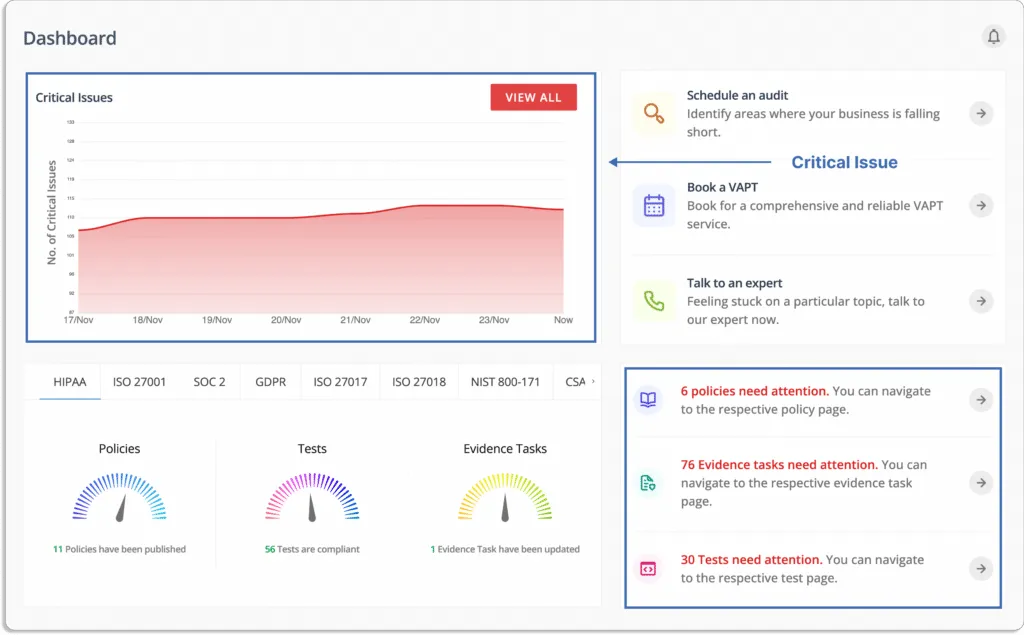
Scrut smartGRC integrates with your cloud service providers within minutes. It performs a gap analysis of compliance status and requirements, monitors over 200 cloud controls across CIS benchmarks, and helps you manage vendor risk, streamline workflows, and build policies—all from a single window for a seamless experience.
Why Scrut takes on a risk-first approach

Given the risk of an actual breach and being fined for violating regulations, many organizations are now prioritizing risks in their information security programs.
Organizations that focus solely on compliance overlook risk factors. Compliance with a standard shows that you are adhering to some of the security best practices applicable universally. However, every company’s risk posture is unique, and a universal guideline is just the bare minimum you can do from a security perspective.
Organizations assume you can automatically combat potential risks if you are compliant. This is not the case.
Let’s see one example of this.
Twilio, which provides programmable communication tools for making and receiving calls and performing different communication functions, complies with all the major security frameworks.
When we checked their website, we found the following certifications and attestations.
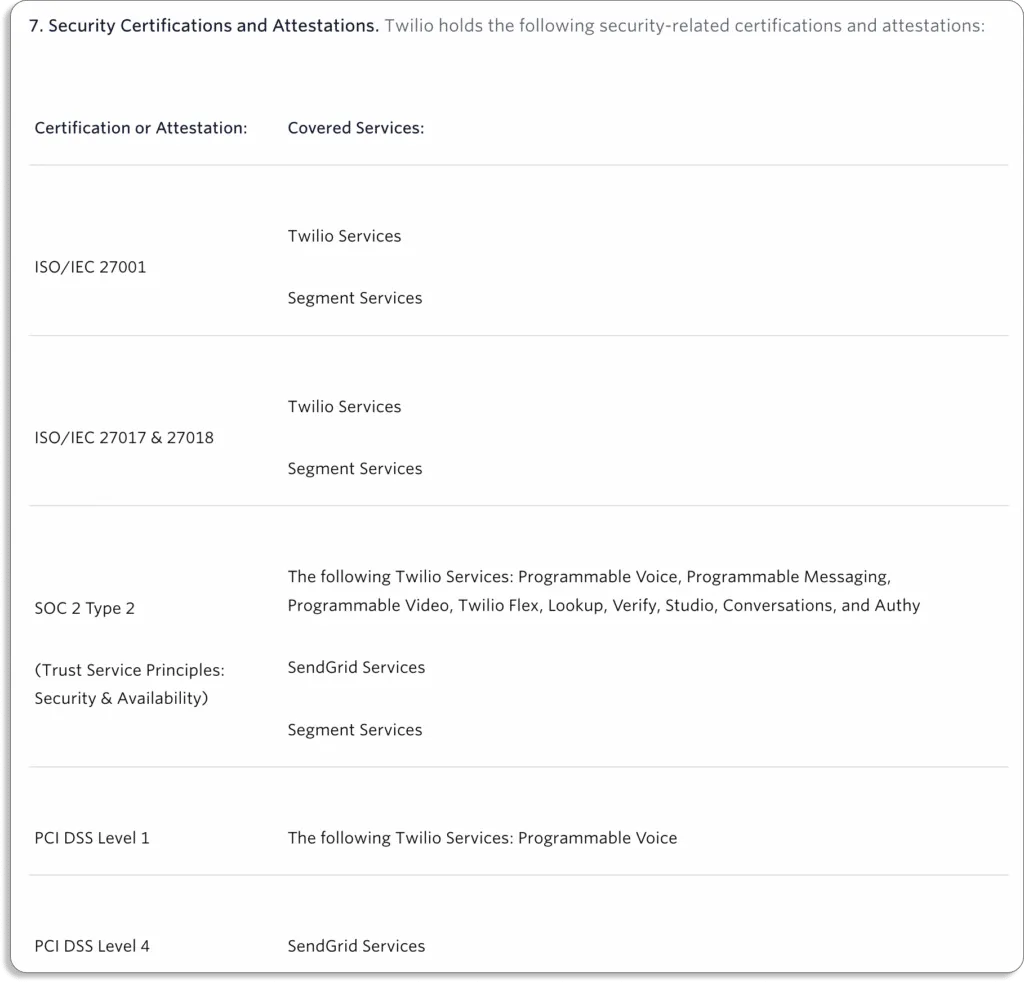
Yet, they suffered a data breach recently. Twilio said this was a “brief security incident” that happened on June 29, 2022. The attackers used social engineering to trick an employee into handing over their credentials in a voice phishing attack.
They further added that the stolen credentials were used “to access customer contact information for a few customers.”

What does this show?
That at the time of the attack, they were compliant but not completely secure. Therefore, we say adapting to risks is a continuous journey, while compliance is just a starting point for security.
Scrut focuses on risk management as it is internal to the organization, whereas compliance is an external requirement and depends on regulatory or other third-party bodies.
The idea behind a risk-first approach is that an organization that prioritizes its risks; finds it easier to meet the compliance requirements, as it is just one part of a larger risk management strategy.
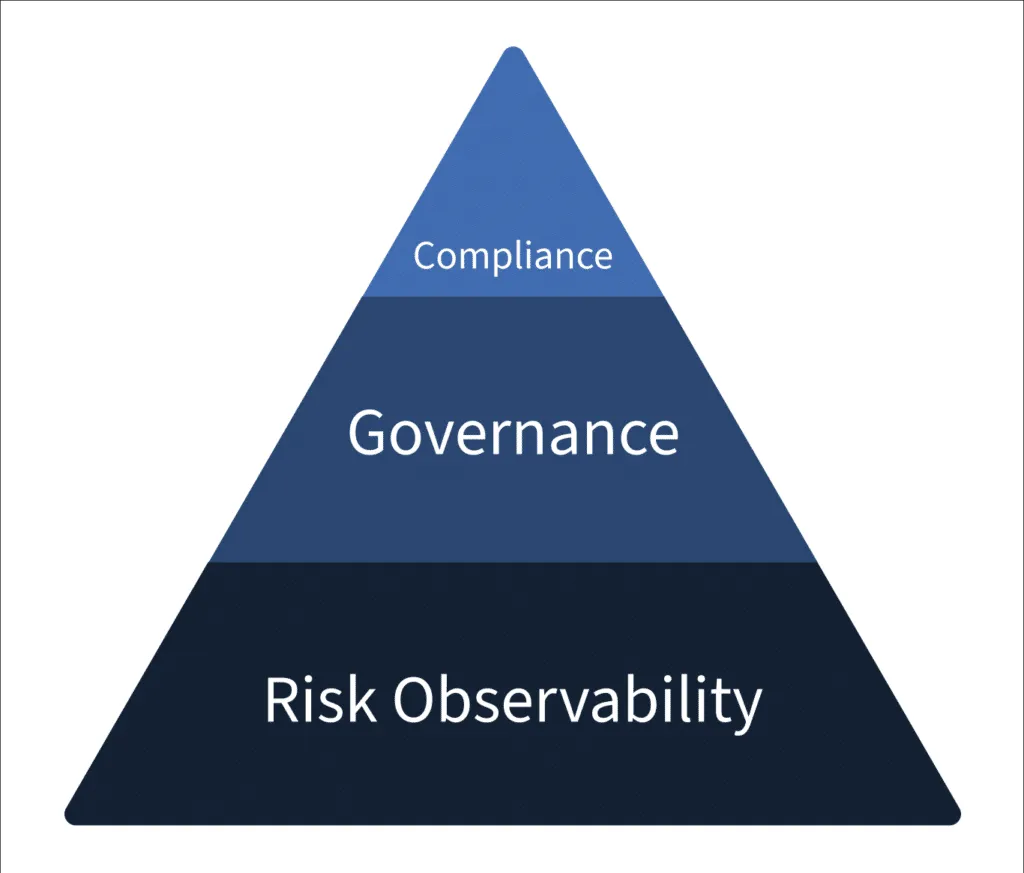
At Scrut, we believe compliance is a byproduct of being secure. Scrut’s SmartGRC is a risk-first GRC platform. This means that instead of a specific point in time, Scrut continuously monitors your organizational risks in real-time.
Risk management
Risk management is the process used by an organization to identify, classify, assess, and reduce risks and enhance business operations.
Scrut Risk Management dashboard gives you an overview of your overall risk posture.
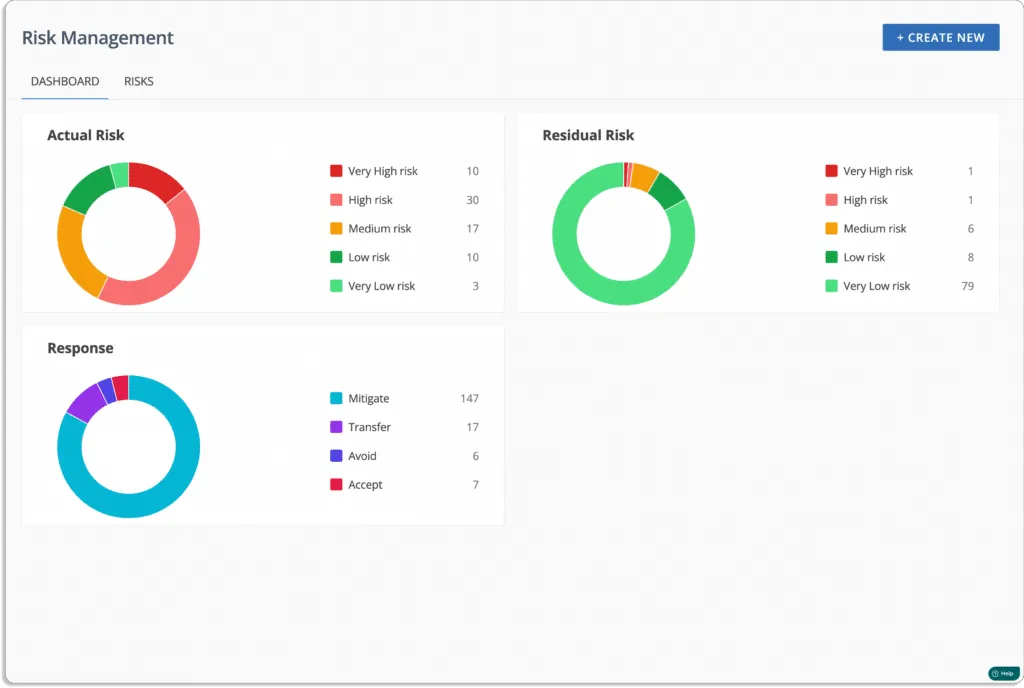
Now let’s see how Scrut helps you with risk management.
- Risk identification: The risk identification process documents all the risks that can disturb the operations or reputation of an organization.
The platform provides a pre-built library of risks to help you identify all risks associated with your business.
Scrut automatically identifies risks in your ecosystem, including code base, infrastructure, applications, vendors, employees, access, and more.
Scrut classifies risks into 7 categories: Governance, People, Customer, Regulatory, Resilience, Technology, and Vendor Management.
To build your risk register, you must first list all the risks. You can do it by following the below steps in Scrut:
To start with,
- First, click on create new
- Once you create, a pop-up like the one shown will appear on your screen:
- After that, you can choose any risks from Scrut’s risk library. In case, if it’s not available then you can create your own custom risks.

- You can select any person responsible for keeping track of and managing the risk. Further, you can select the category of risk from the list we discussed above.
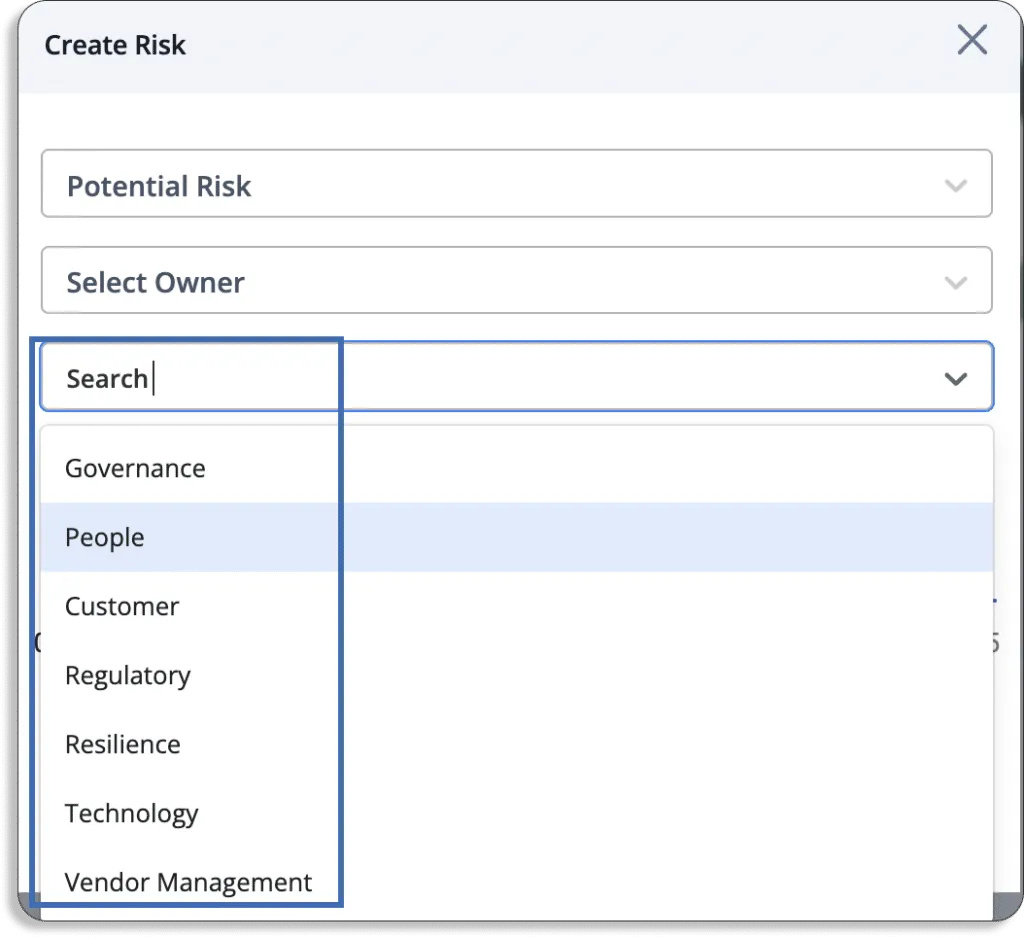
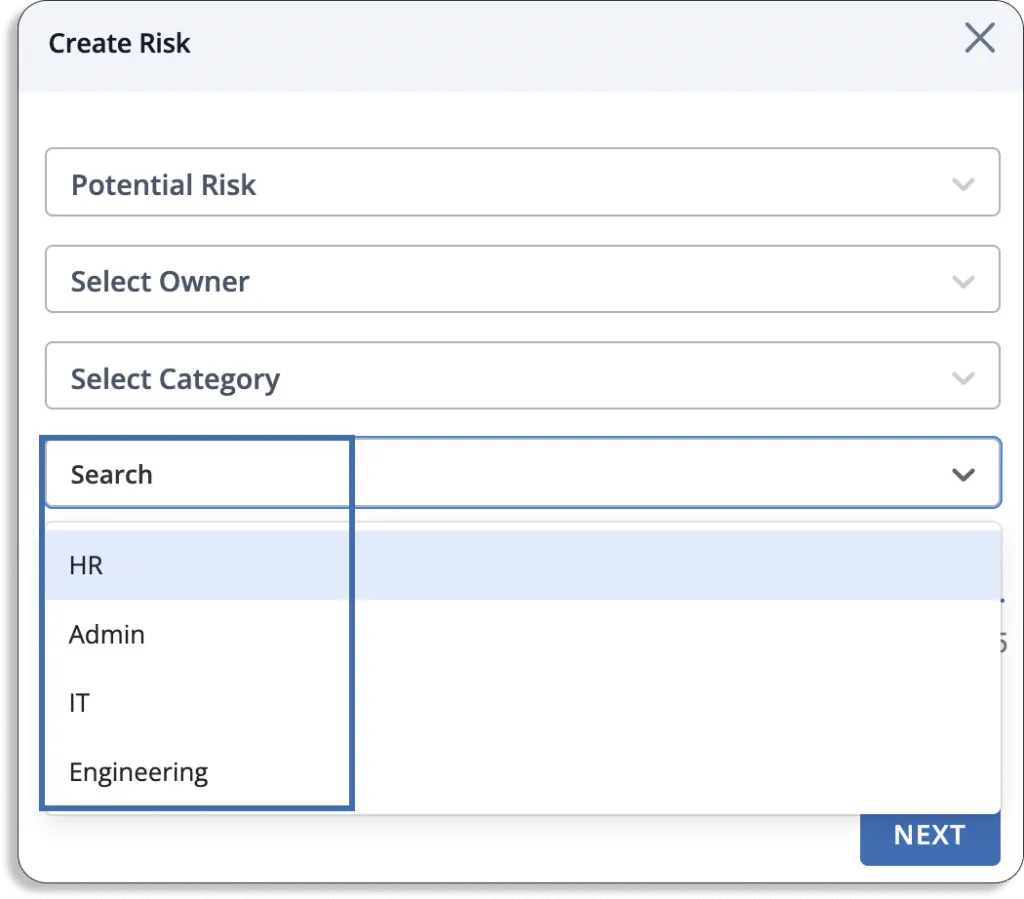
- You can select any department from HR, Admin, IT, and Engineering for the risk.
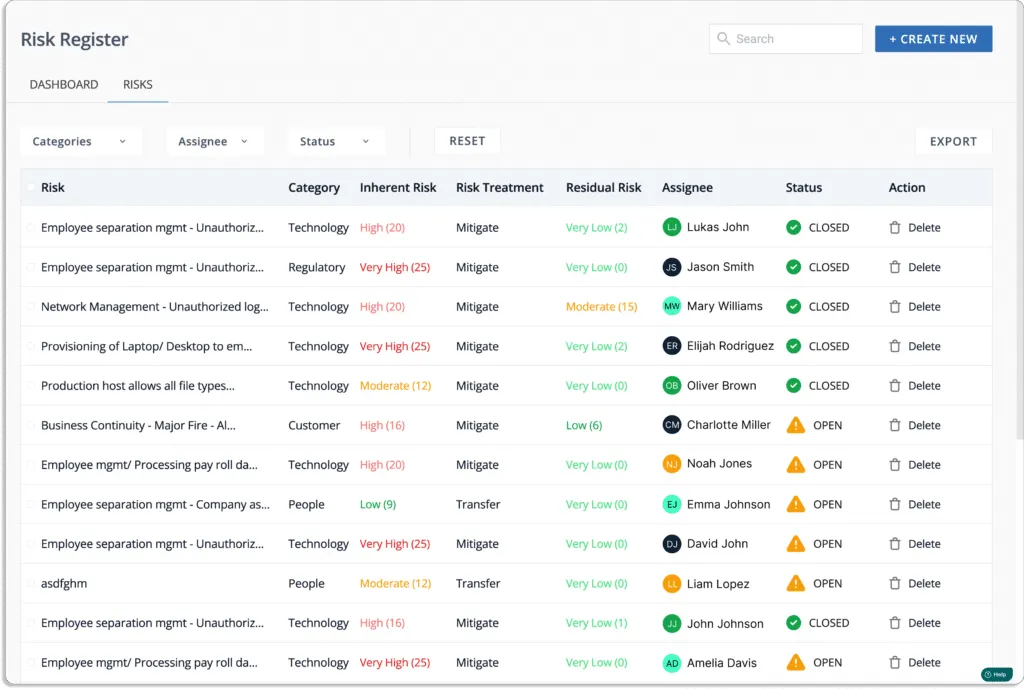
- Finally, you can see a list of all the associated risks known as a Risk register.
- Risk assessment: Once you identify all the risks, you must evaluate them. Risk assessment provides you with insights into how risk can affect your organization.
Scrut platform starts your first risk assessment in minutes by eliminating the time spent creating and mapping risks, threats, and controls and establishing related tasks.
Scrut’s built-in expert-vetted scoring methodologies help you quantify your risk profile. The platform creates your risk scoring based on the likelihood and impact of events.
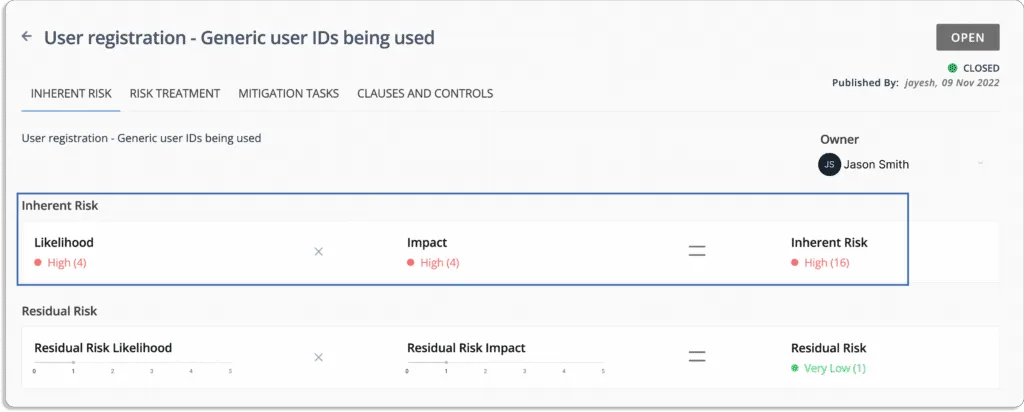
Risk = Likelihood * Impact
The final score lies between 0 – 25.
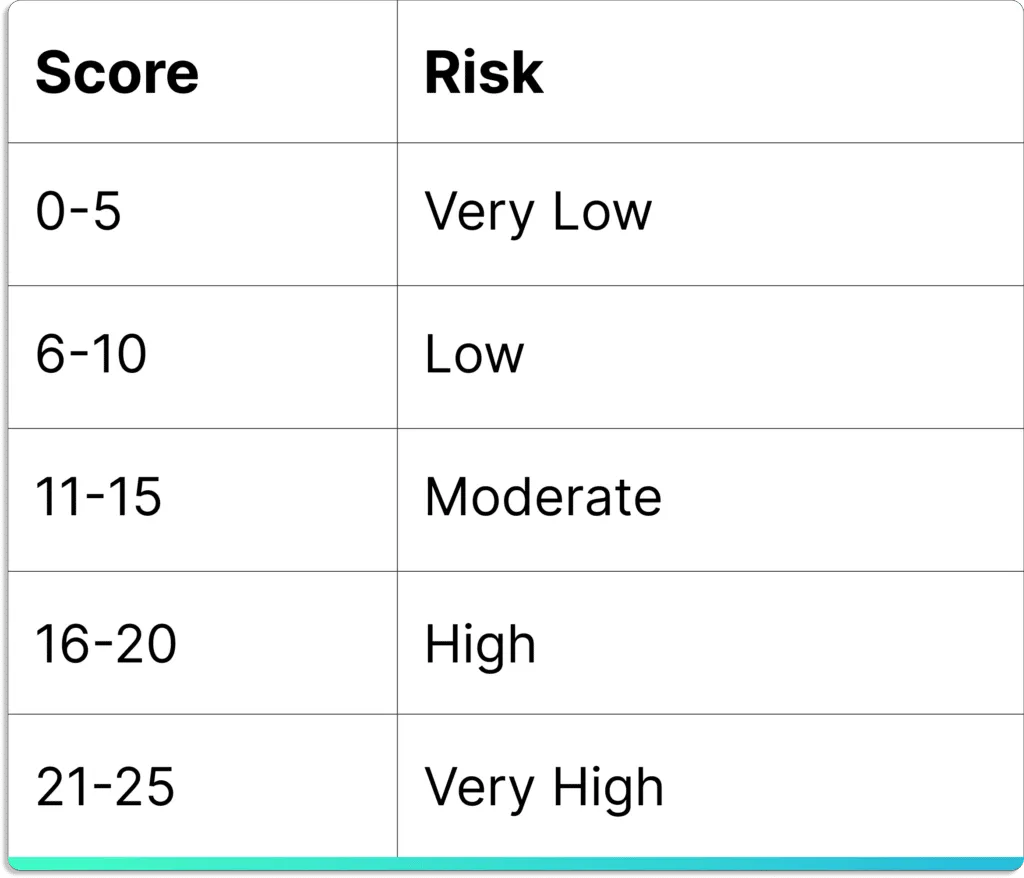
As shown in the screenshot below, you will get a visual overview of your risk profile at this step.
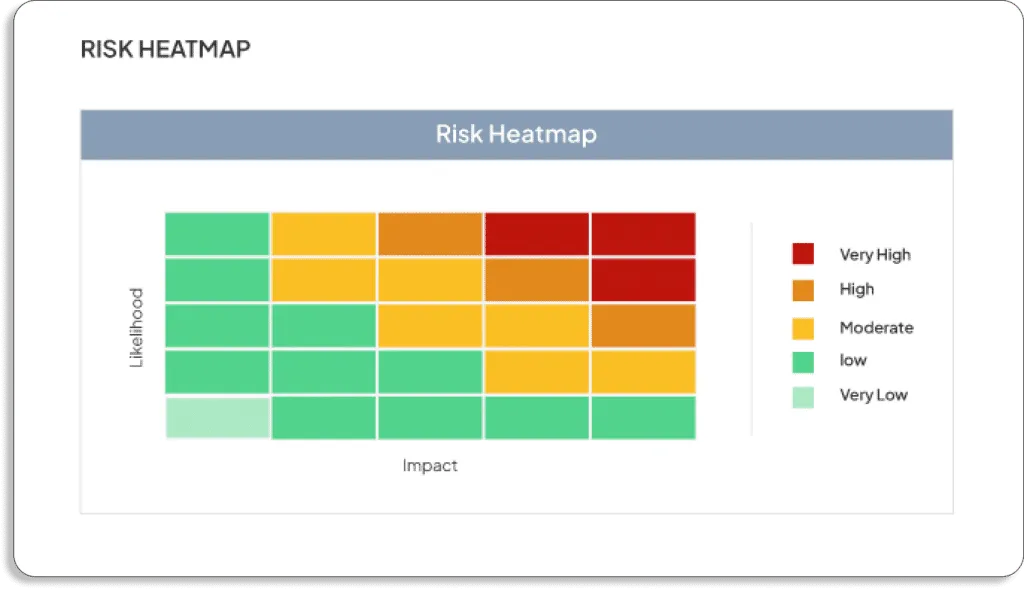
- Risk mitigation: After assessing the risk, organizations should ensure that risk is properly eliminated.
Scrut risk management includes automated procedures for documenting mitigation control use. The platform allows you to create mitigation tasks, define a completion timeline, assign individual owners, and track completion.
Scrut provides four ways of treating the risk.
- Remediation – eliminate the risk
- Mitigation – minimize the impact or likelihood of the risk
- Transference – transfer the risk to another party, e.g. an insurance company
- Acceptance – accept the risk
For risk treatment, you can assign risks to team members, as shown in the screenshot below.
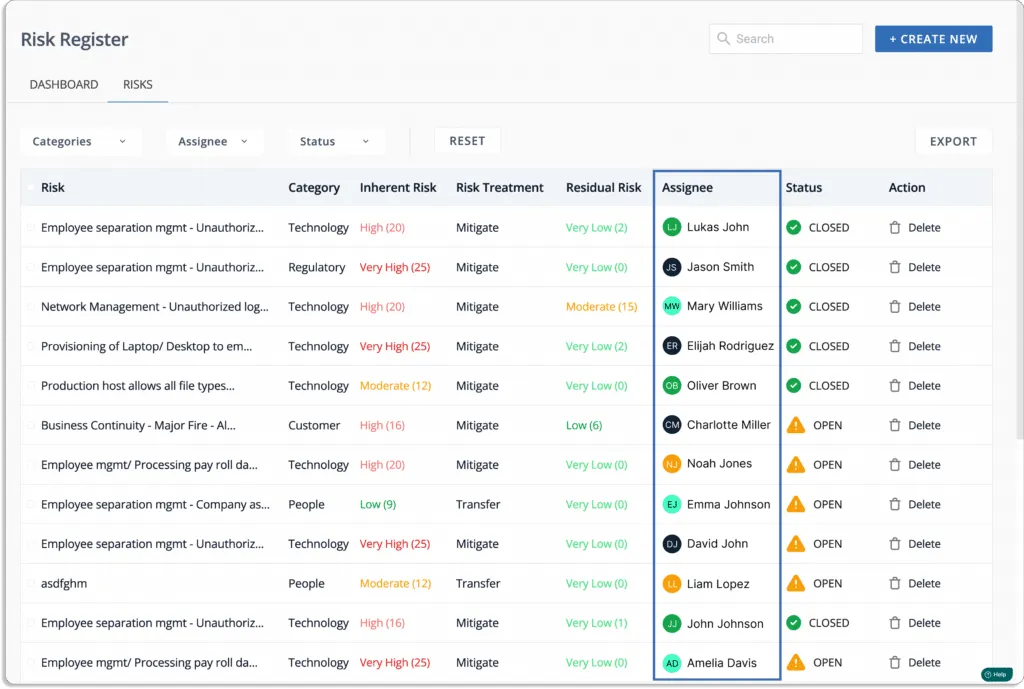
Additionally, add mitigation tasks so that the responsible person can easily do it without any issues.
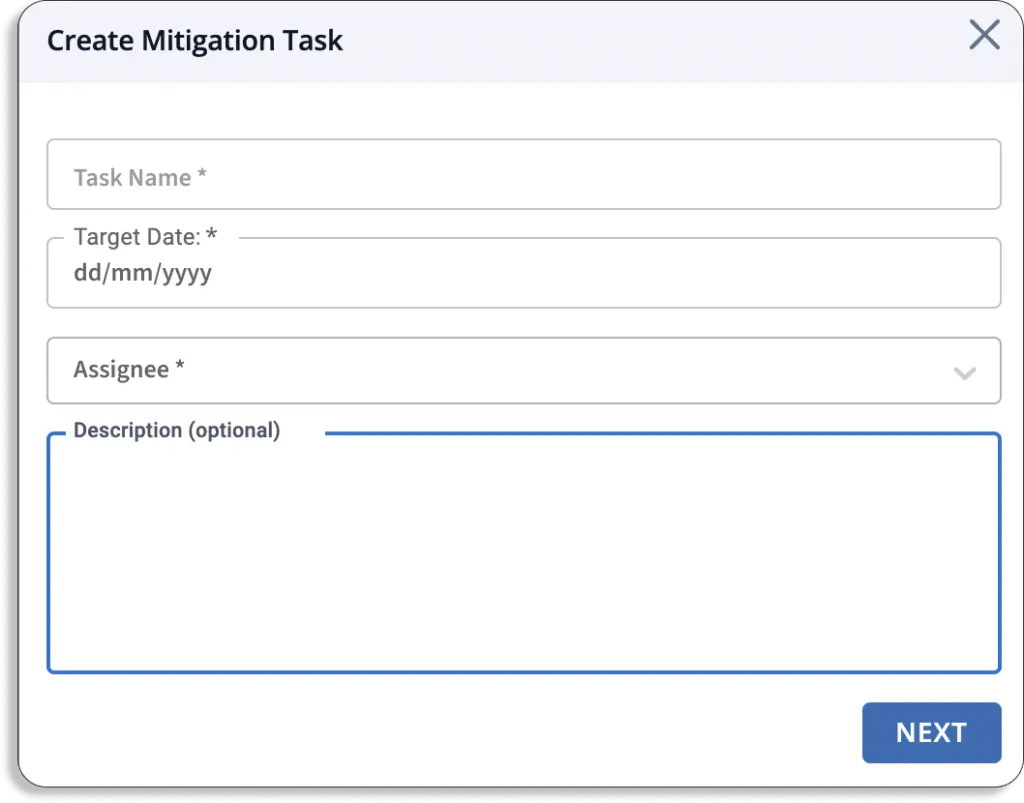
To do this, just go to the mitigation tasks tab and click the new mitigation task button.
A pop-up like this will appear on your screen. Fill in the details.
Moreover, Scrut Risk Management has pre-mapped risks to control across different security and privacy frameworks like SOC 2, ISO 27001, GDPR, HIPAA, PCI DSS, and more.
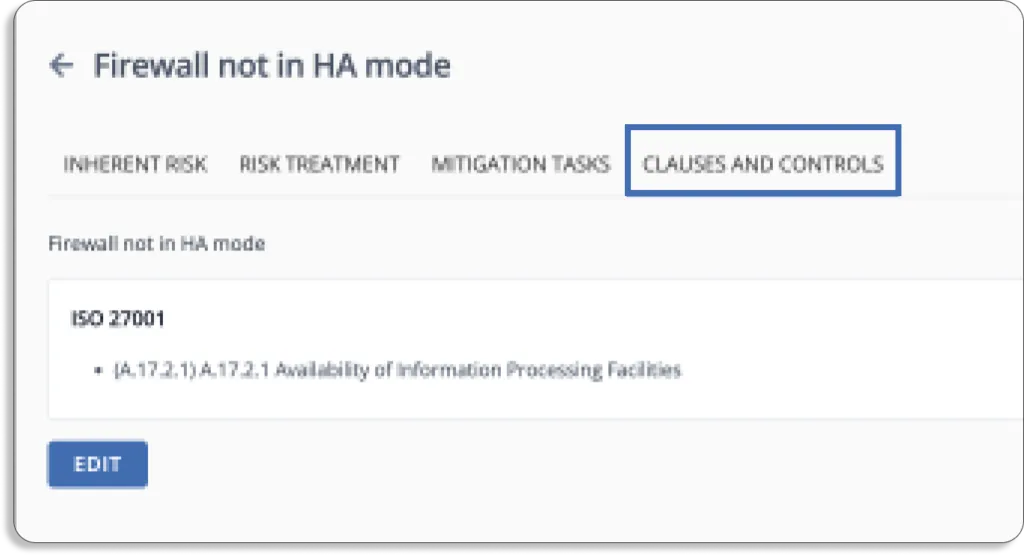
The platform eliminates the need to manage and constantly update a risk register on multiple spreadsheets. It collects all risks, their inherent and residual risk scores, mapped controls, and mitigating tasks in one place, which can then be easily shared with auditors for faster compliance audits.
Governance
smartGRC platform identifies critical issues and provides a single tracker to monitor what needs your attention.

Let’s now see how Scrut helps you set up security governance in your organization.
- 50+ pre-built policy templates for 20+ compliance frameworks: With a library of 50+ pre-built policy templates vetted by our in-house InfoSec experts, you can start your compliance program in minutes.
This eliminates duplication of efforts when going for multiple frameworks, as you can use the same policies for new frameworks.
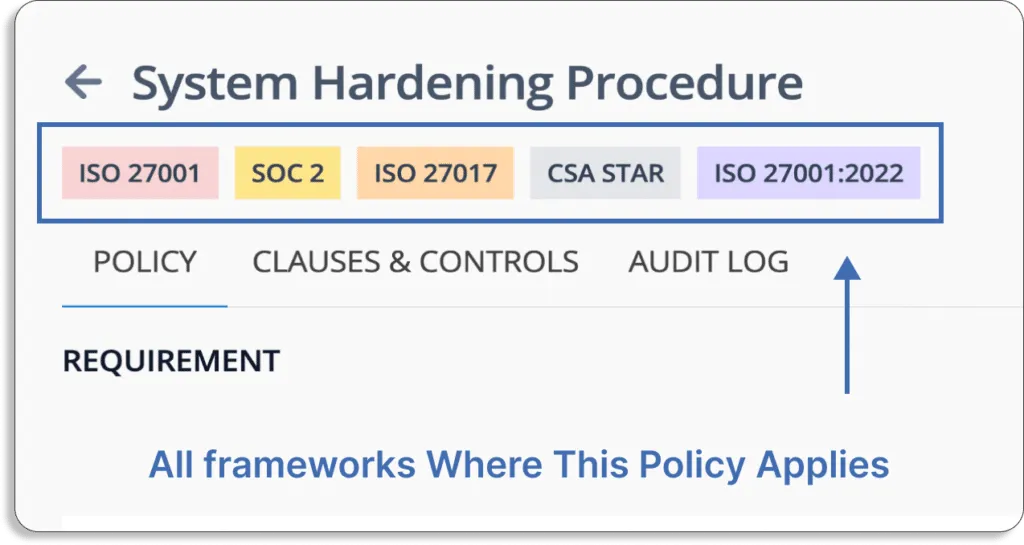
Furthermore, this policy is mapped with all the controls you need for different frameworks. For instance, the control CC6.1 is mapped to SOC 2.
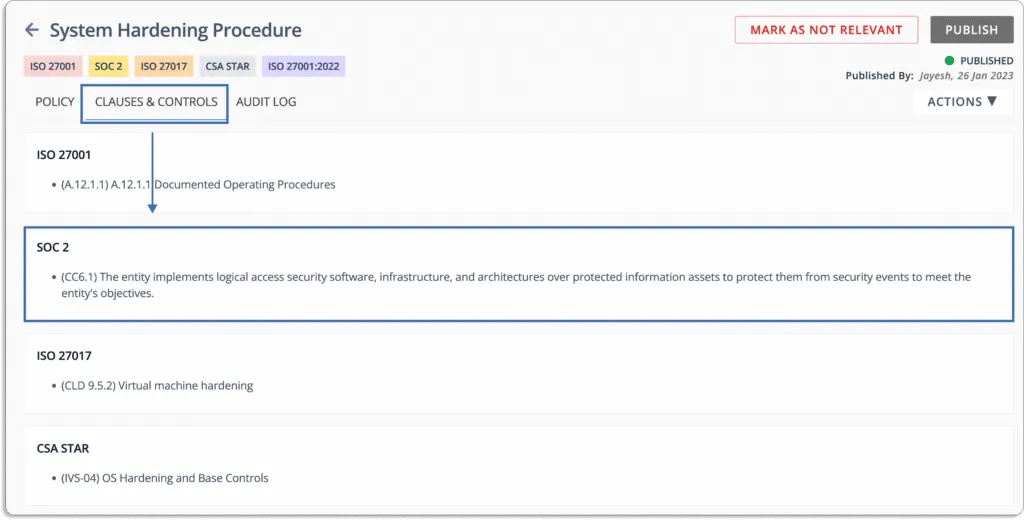
Further, you can edit the policies using the platform’s in-line editor.
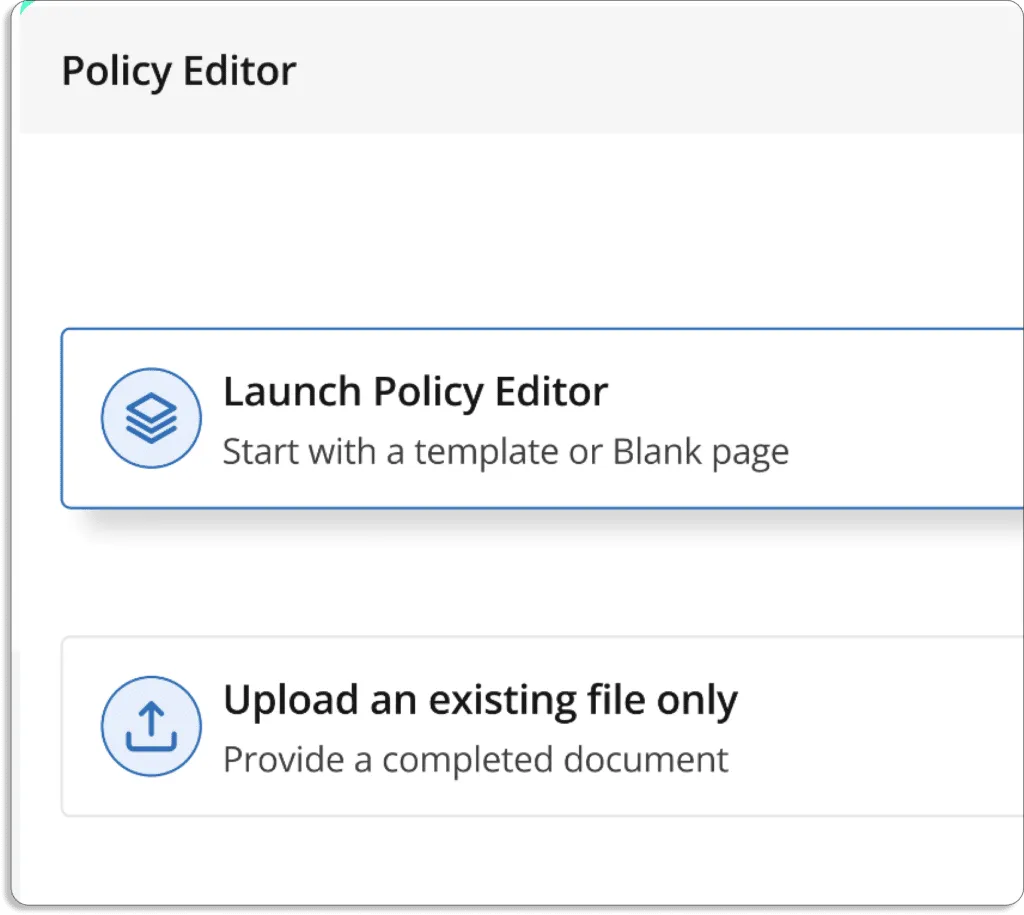
Apart from this, you can also upload your existing policies on the platform.
All the controls required for a framework are pre-populated on the platform, which helps you quickly choose and customize them as per your requirements.
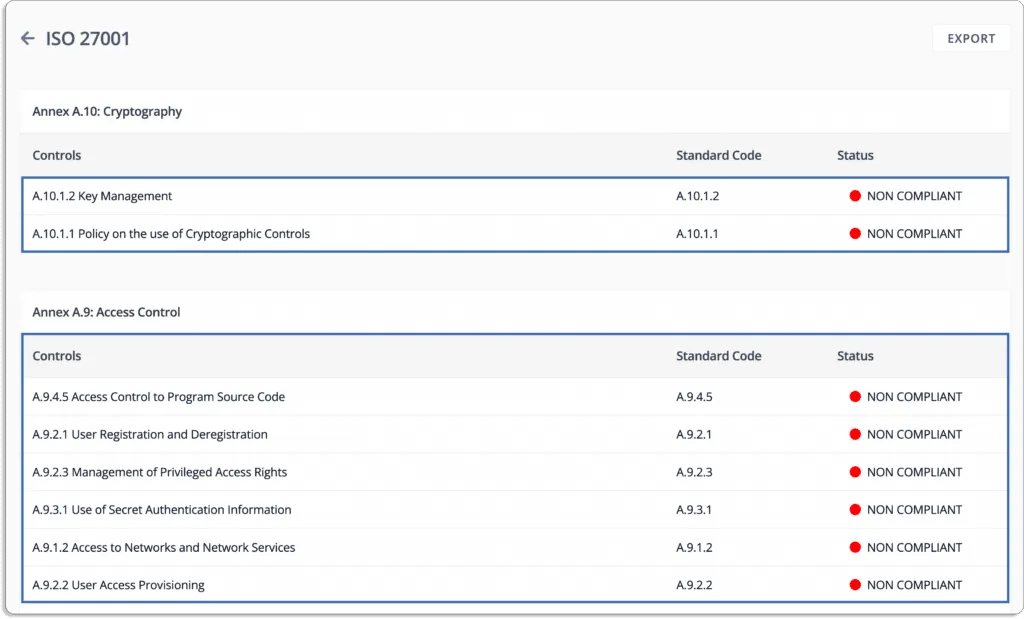
Custom controls can be defined to reflect your company’s specific needs, and pre-built control mapping can be used to map them against your required compliance frameworks.
- Task and workflow management: Scrut helps you easily collaborate with your internal team and assign tasks automatically using workflows. It monitors them and sends reminders for pending tasks to you. It also keeps you on top of risks, and the team feels accountable and in control of their tasks.
You can assign ownership of tasks to members. The tool updates you on the latest status of each task by tracking them on the Scrut platform.
You can assign owners to policies for creating or making any changes to them. This ensures that policies are managed properly, and the policy owner is accountable for all tasks related to the policy. Further, the platform sends reminders to the policy owners (Slack, email) for any pending policy-related tasks.
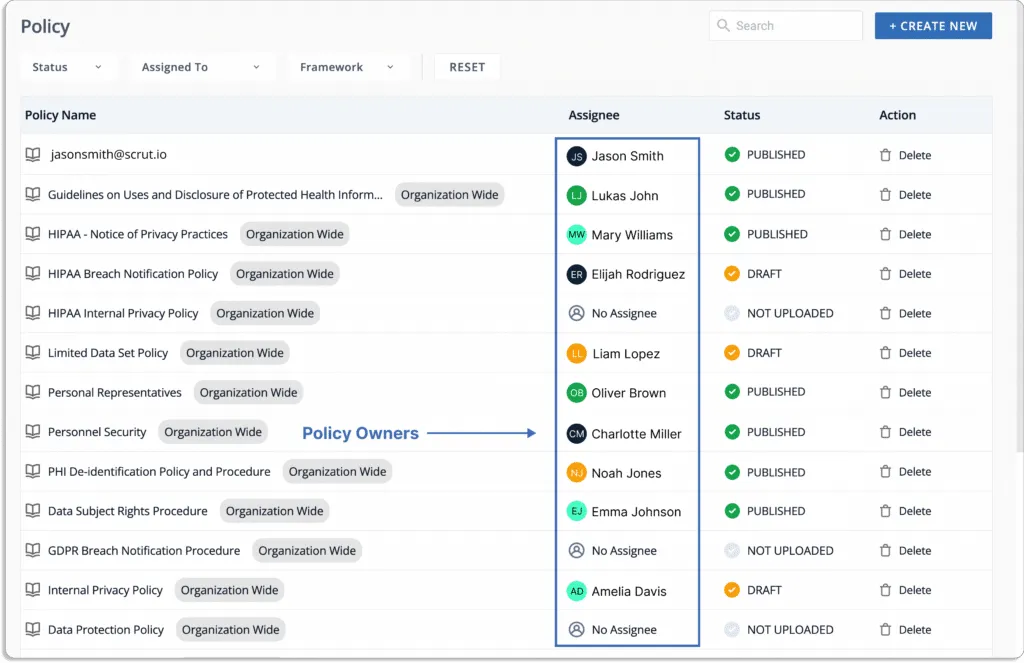
Similarly, you can assign ownership to fix any misconfigurations in your cloud accounts.
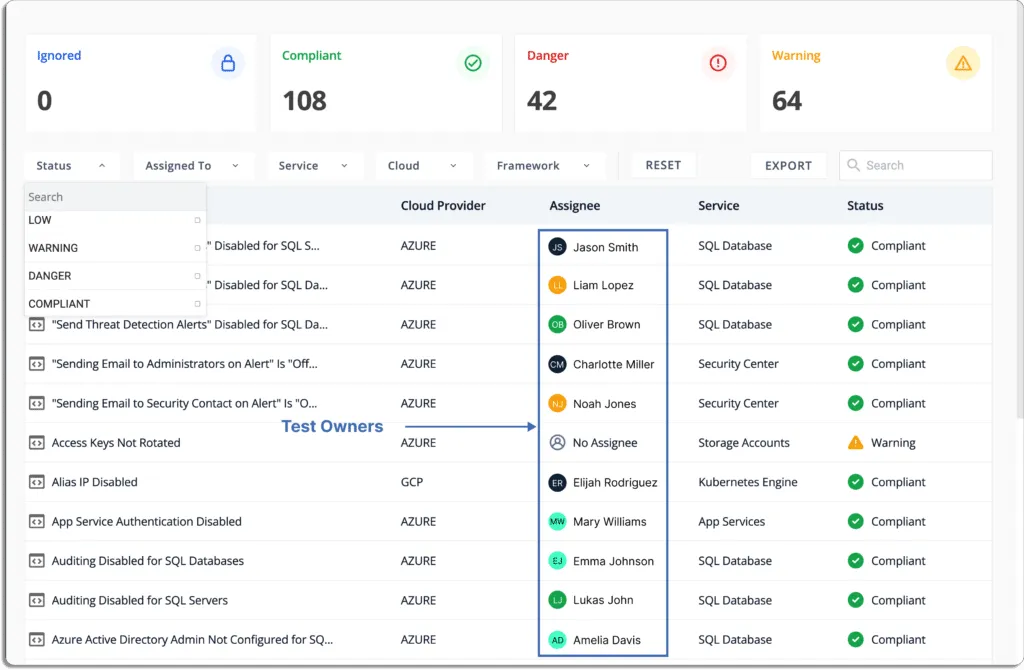
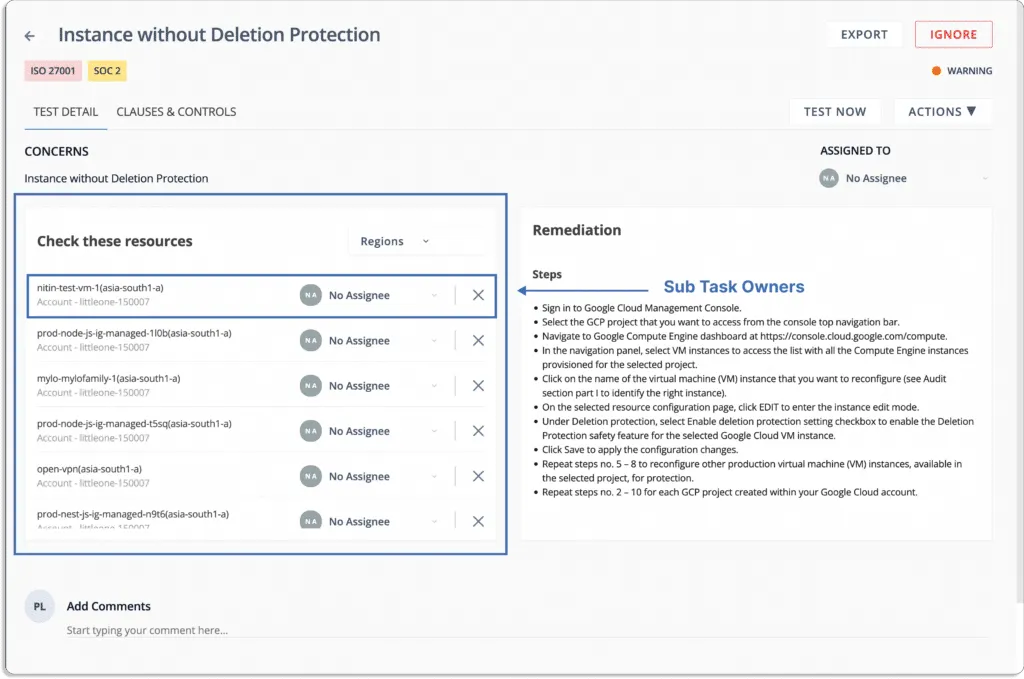
Scrut also gives step-by-step-remediation tasks so that the person responsible can easily resolve the issues.
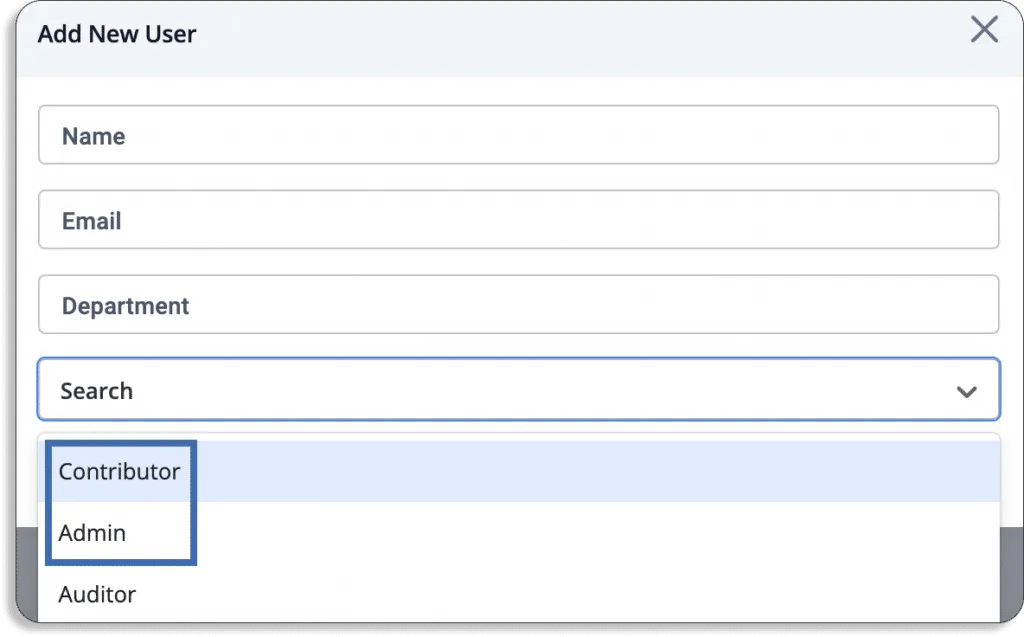
- User role: An important part of good security governance is the separation of roles. Scrut provides 2 types of roles for internal team members: contributor and administrator.
Contributors can be assigned any task, from policy updates, test ownership, risk ownership, etc. But they cannot approve and publish major organization-wide changes. That authority is only with users with admin access.
To add users with different privileges, go to settings and then manage users.
After clicking on add new user, you will get a pop-up like this.
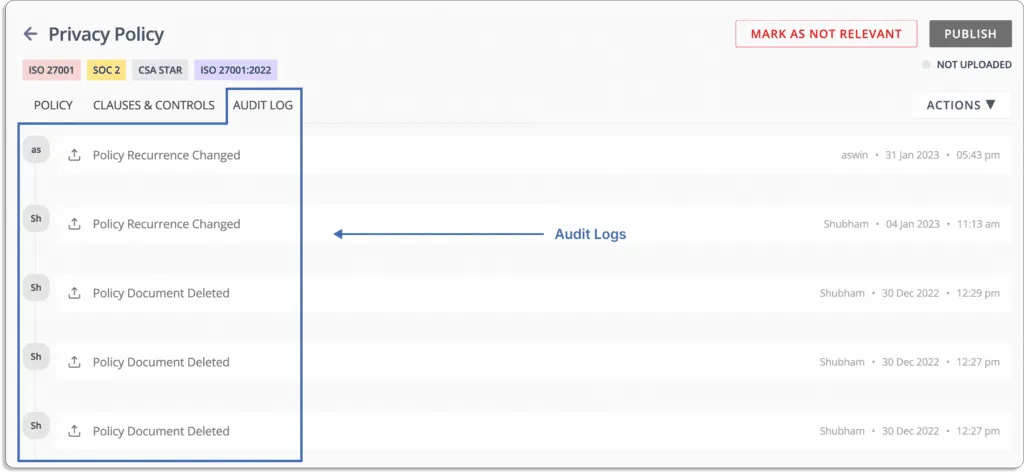
- Audit logs: Scrut logs all actions taken by users, changes made to policy documents, and API calls made through our integration, and monitored as of audit logs.
For example, see this audit log in the privacy policy document.
Compliance
Scrut smartGRC provides a faster, simpler, and smarter path to compliance by eliminating time-consuming manual procedures and keeping you updated on the progress and effectiveness of your programs.
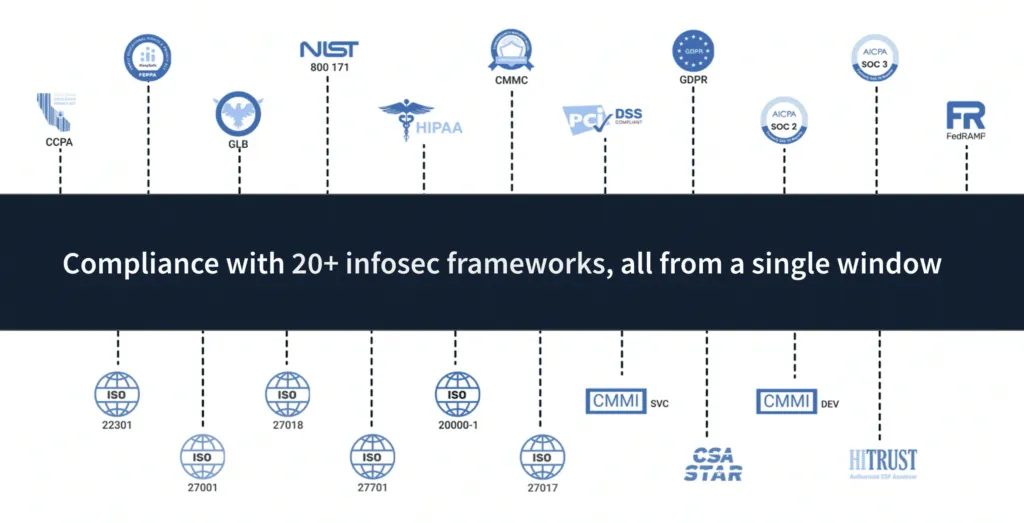
- 20+ compliance frameworks out-of-box: As discussed in the previous section, Scrut comes with a library of over 50 pre-built policy templates that are vetted by our in-house InfoSec experts.
These policies cover 20+ security and privacy frameworks like SOC 2, HIPAA, GDPR, PCI DSS, and ISO 27001.
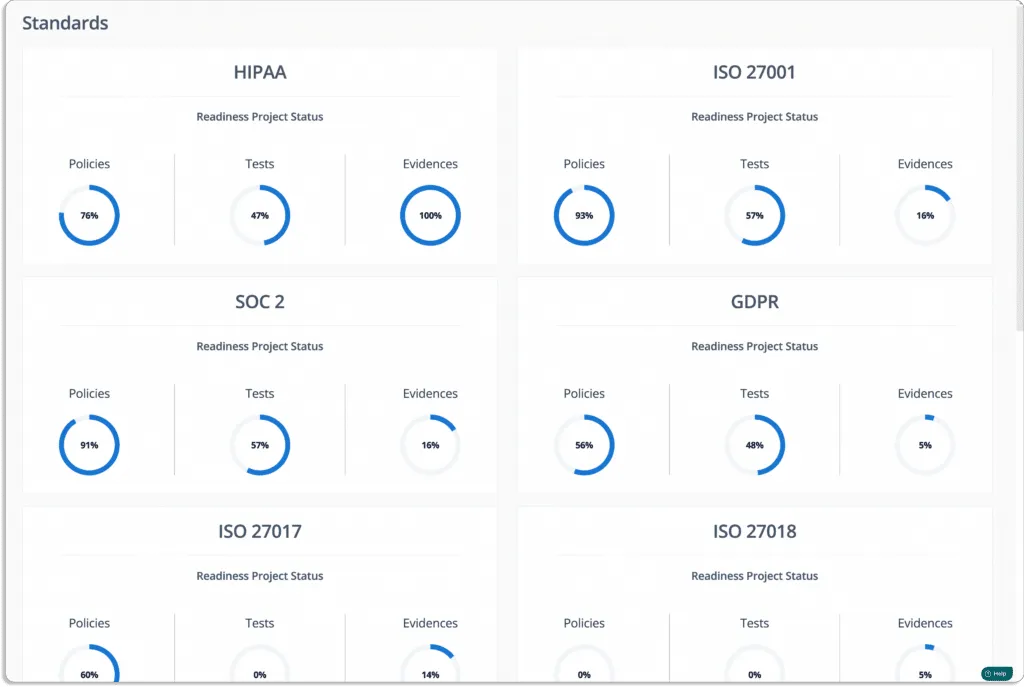
- Visibility into all your InfoSec programs: With Scrut smartGRC platform, you get complete visibility into the status, effectiveness, and impact of your activities on your compliance posture.
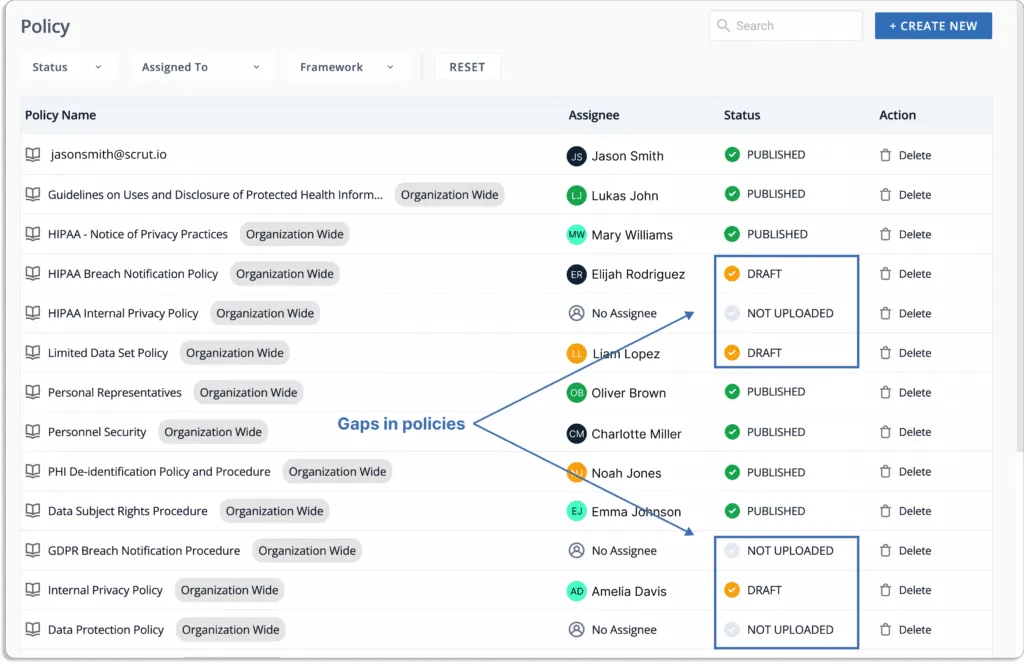
The tools bring all your InfoSec tasks and artifacts into a single place. It enables you to fill compliance gaps in real-time.
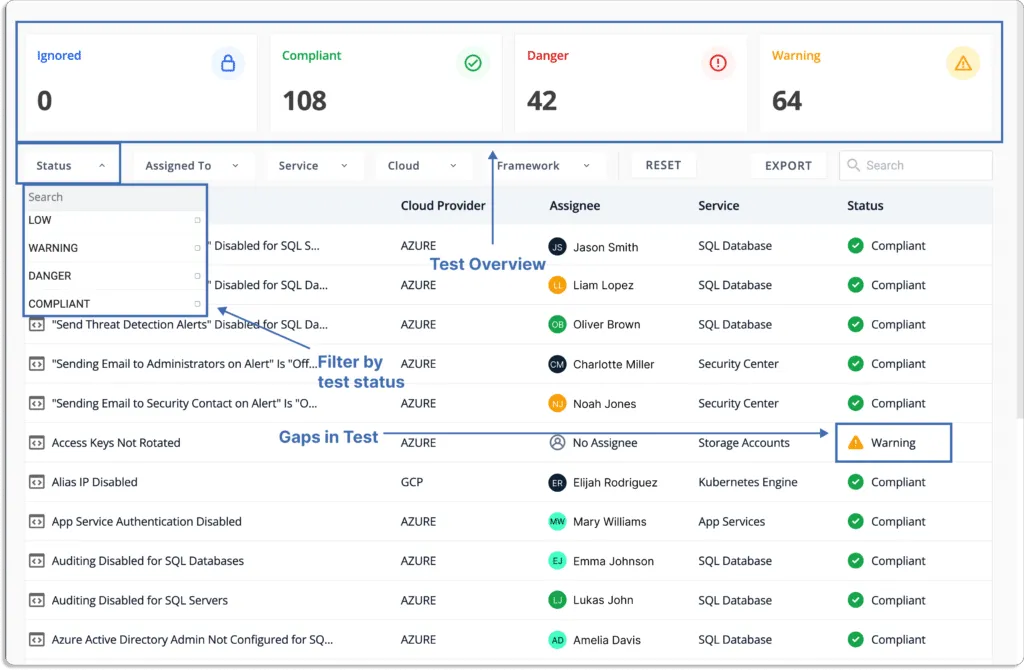
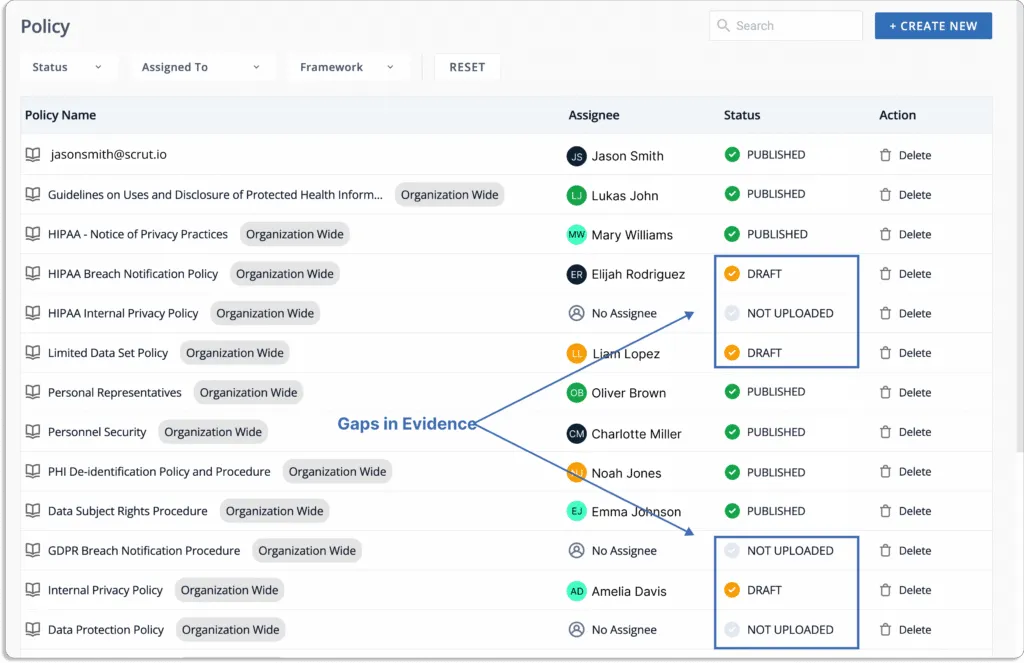
- Automated evidence collection: Evidence collection is one of the important aspects of any compliance program. Without a GRC platform, gathering evidence and maintaining compliance becomes time-consuming and challenging.
With Scrut, you can reduce the effort required for evidence gathering with the help of over 70 integrations.
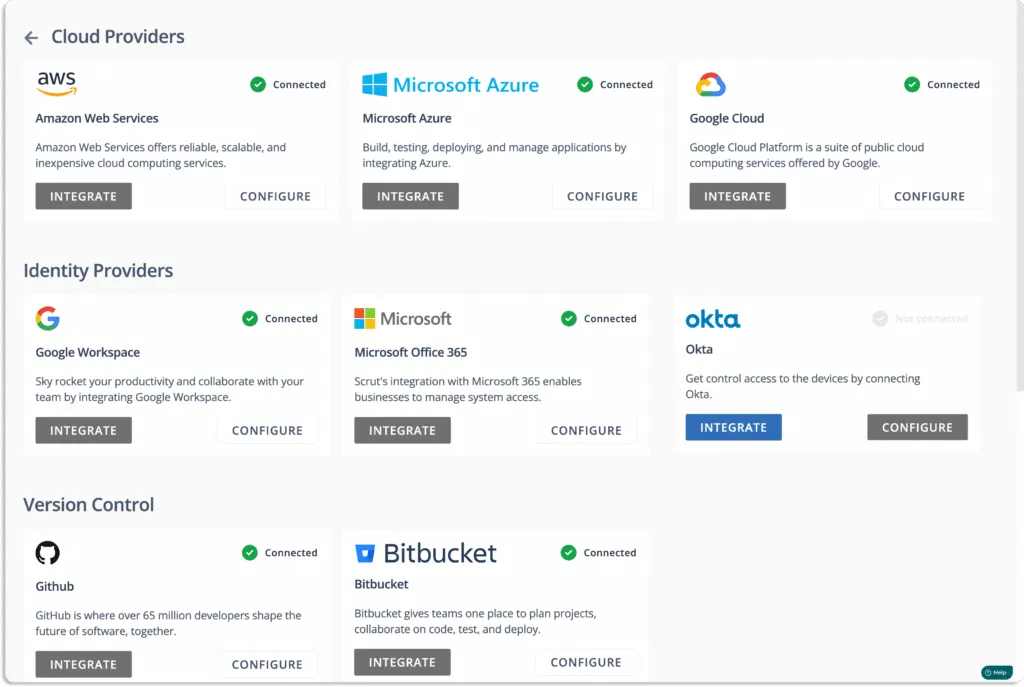
- Scrut cloud security
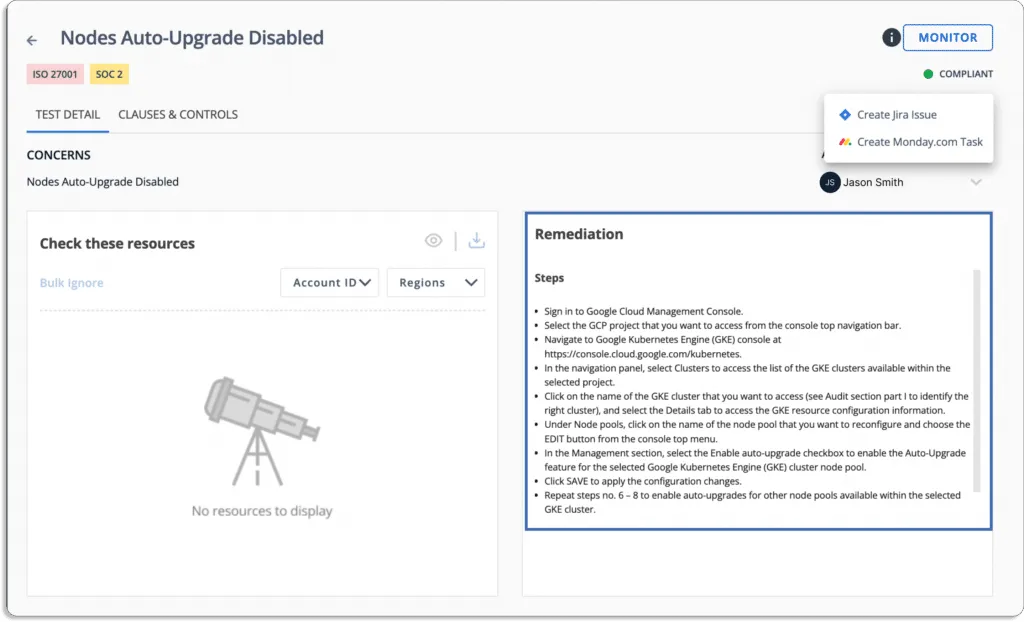
Scrut Cloud Security scans and monitors misconfiguration in public cloud accounts, such as AWS, Azure, and Google Cloud Platform, among others. The tool helps you to maintain a strong InfoSec posture by automatically comparing your cloud configurations against 200+ cloud controls across CIS benchmarks.
When misconfigurations occur, Scrut alerts you with actionable remediation recommendations, as shown in the screenshot below.
- Seamless collaboration with auditors: Auditing is an essential part of any compliance program. You always want a seamless collaboration with the auditors to ensure a smooth and faster audit.
Just create a new audit from the audit center.
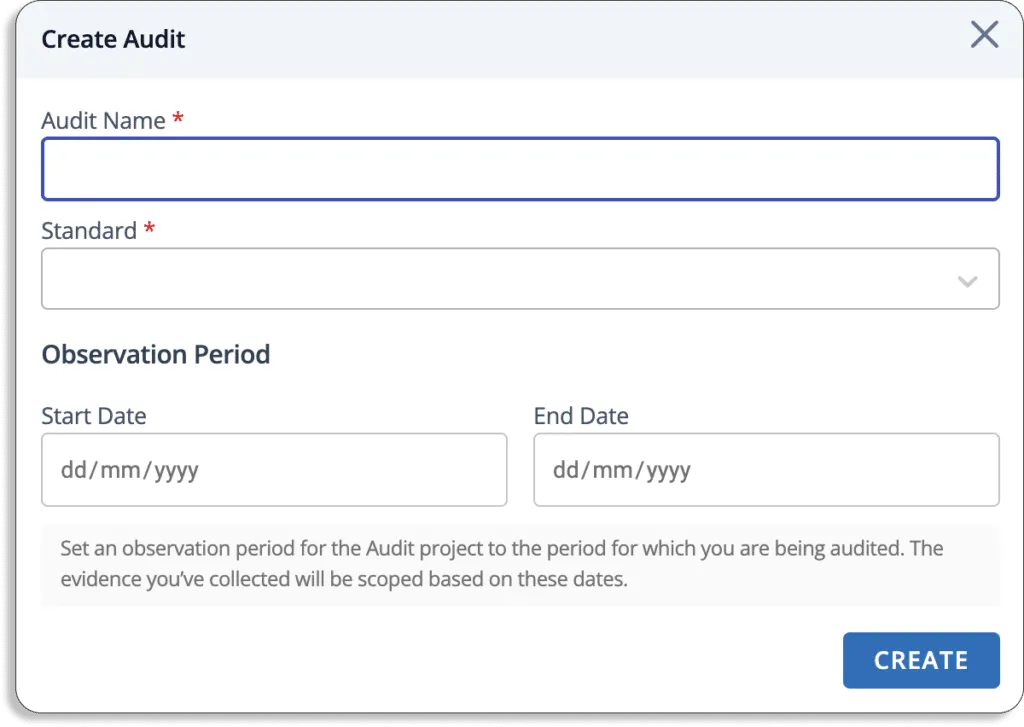
The Scrut smartGRC allows you to invite auditors to the platform.
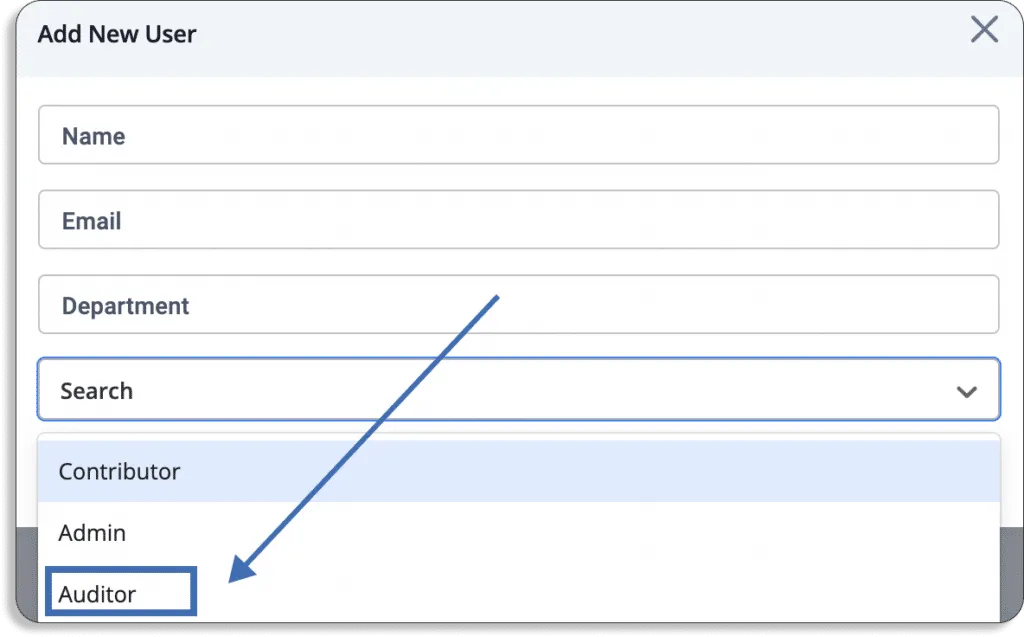
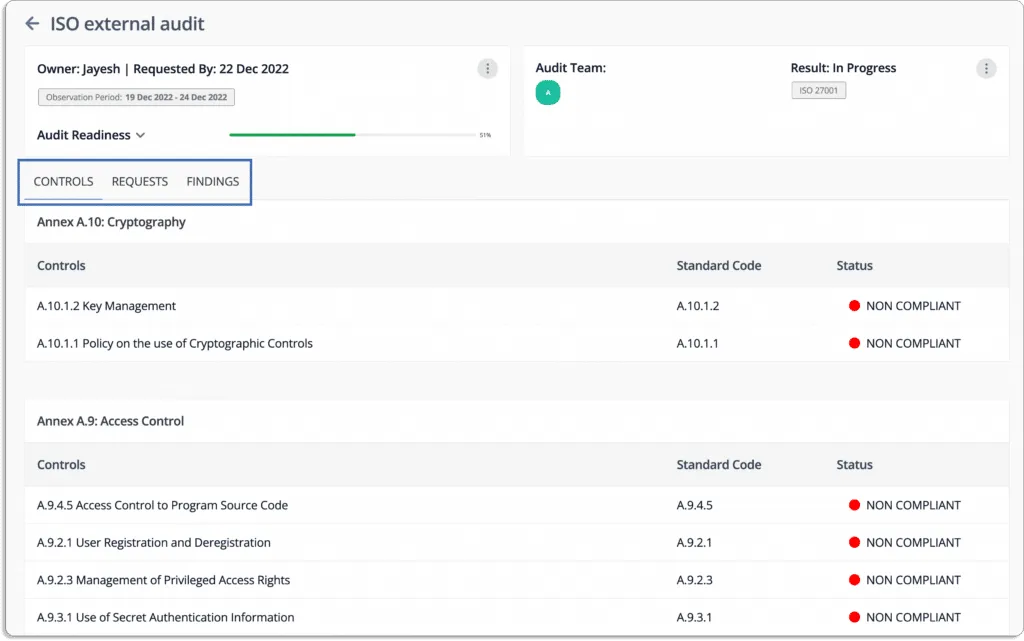
The auditors can go through all policies, controls, evidence, and other artifacts required for the audit on the platform and leave their findings on the platform.
Check one of the user reviews from our customers.

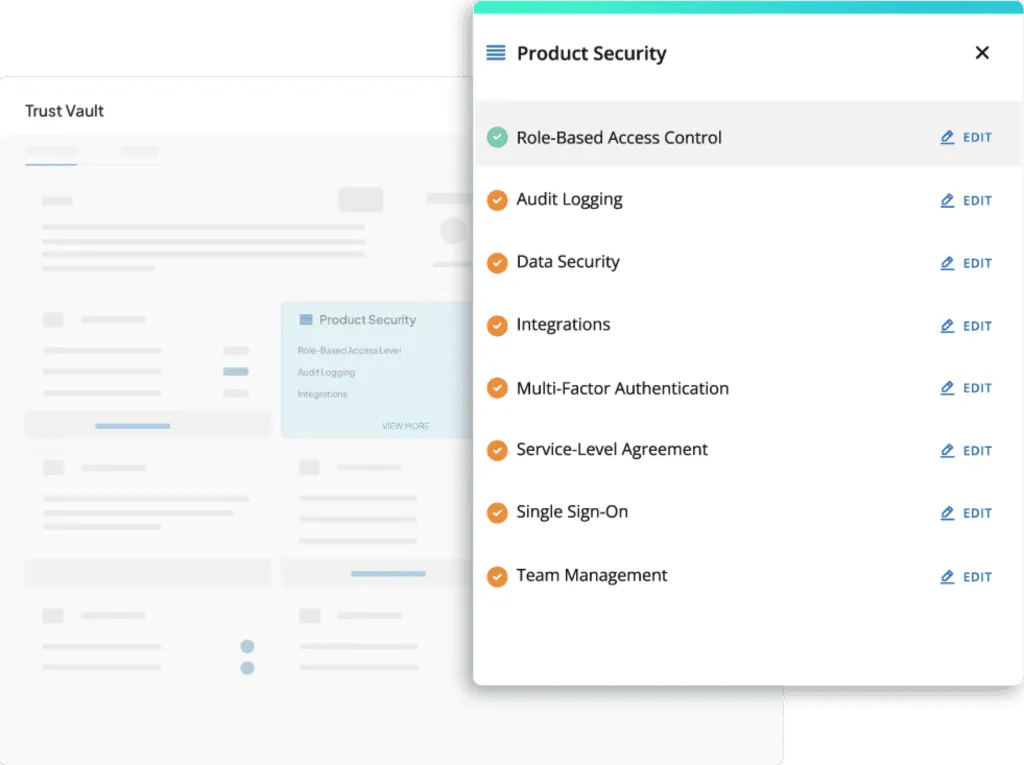
Trust Vault: Establish Trust from Day 1
Scrut Trust Vault empowers you to build trust with customers, partners, investors, and more. It helps in accelerating your sales by eliminating the manual effort and time required to share different InfoSec documents (compliance certifications, attestations, and reports) in the sales process.