Bridging the gap: From point-in-time to continuous risk management

Risk assessment is crucial in cybersecurity and compliance because it helps organizations proactively identify, evaluate, and mitigate potential threats to their information technology assets.
By systematically analyzing vulnerabilities and assessing the potential impact of cyber threats, organizations can implement effective security measures, ensuring the protection of sensitive data and maintaining regulatory compliance. This process not only mitigates future risks but also enhances the organization's ability to respond swiftly to emerging threats, thereby safeguarding its operations, reputation, and customer trust.
Not long ago, organizations opted for point-in-time risk assessment, which was simpler and easier to perform; however, today, most have shifted their focus to continuous risk management. Why? This article will answer the question and give you all the information about continuous risk management.
Section 1: Understanding point-in-time risk assessment
What is point-in-time risk assessment?
Point-in-time risk assessment is a method of evaluating risks at a specific moment. This approach provides a snapshot of the current risk landscape, allowing organizations to identify potential vulnerabilities and compliance issues based on the information available at that particular time.
While it helps understand the immediate risk posture and address current threats, its static nature means that it can quickly become outdated as new risks emerge and circumstances change. Therefore, it is often complemented by continuous monitoring and regular updates to maintain an accurate and effective risk management strategy.
Steps involved in point-in-time risk assessment
Point-in-time risk assessment involves a series of systematic steps to identify and evaluate risks at a specific moment. Here are the key steps:
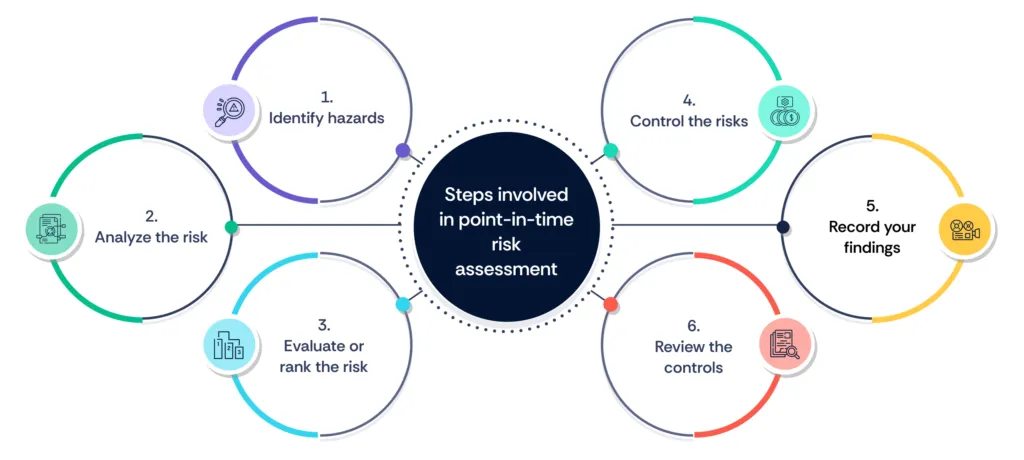
- Identify hazards: Determine what could potentially cause harm. This involves recognizing hazards related to processes, activities, and the environment.
- Analyze the risk: Assess the identified hazards to understand their potential impact and the likelihood of occurrence. This step helps in prioritizing risks based on their severity and probability.
- Evaluate or rank the risk: Evaluate the risks to determine their significance and prioritize them. This step involves comparing the levels of risk against predetermined criteria to decide which risks need to be addressed immediately.
- Control the risks: Implement measures to mitigate the identified risks. This could involve changes to processes, implementing safety measures, or other control strategies to reduce the impact or likelihood of the risks.
- Record your findings: Document the hazards identified, the analysis performed, and the control measures implemented. Keeping detailed records ensures that the assessment process is transparent and can be reviewed or audited later.
- Review the controls: Regularly review and update the risk assessment to ensure that the control measures are effective and up-to-date. This helps in maintaining the relevance of the risk assessment over time.
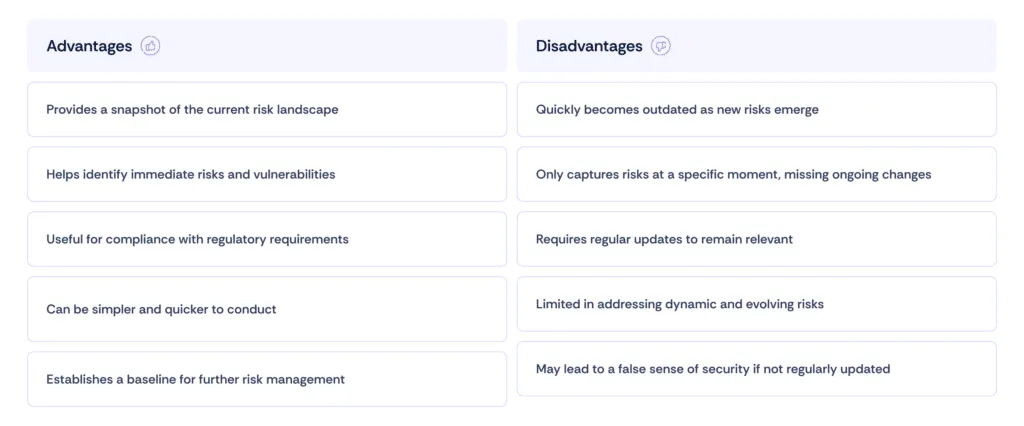
Advantages and disadvantages of point-in-time risk assessment
Section 2: The shift to continuous risk management
Continuous risk management in cybersecurity and compliance involves the ongoing evaluation and monitoring of potential threats and vulnerabilities to an organization's IT systems and data. Unlike point-in-time assessments that provide a static snapshot, continuous assessments leverage live data to offer a dynamic and real-time view of the risk landscape.
This approach allows organizations to detect emerging risks promptly and respond swiftly, thereby enhancing their ability to protect sensitive information and maintain regulatory compliance.
Continuous risk management helps in staying current with evolving threats, improving collaboration within internal audit teams, and ensuring that cybersecurity controls remain effective and up-to-date. It forms a critical component of a robust cybersecurity strategy, ensuring that organizations can adapt to new risks as they arise and maintain a proactive stance in managing cybersecurity threats.
What are the key elements of continuous risk management in cybersecurity and compliance?
What are the benefits of continuous risk management?
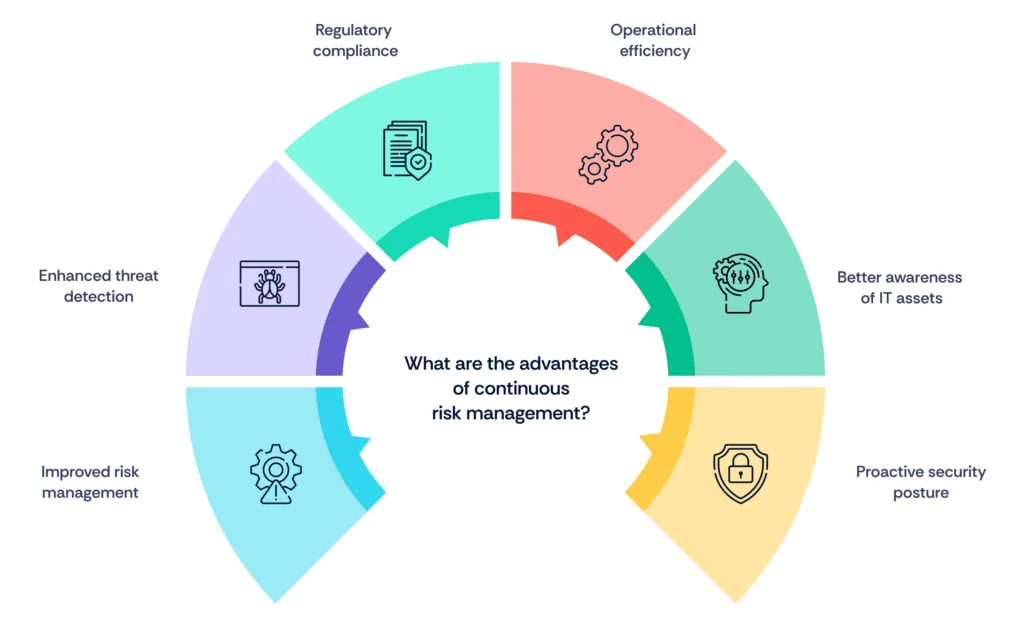
Continuous assessment in cybersecurity and compliance provides numerous advantages by ensuring that organizations are always aware of their security posture and compliance status. Here are the key benefits:
1. Improved risk management
Continuous assessment helps identify and prioritize security risks in real time, allowing organizations to allocate resources effectively to mitigate the most critical threats.
2. Enhanced threat detection
By constantly monitoring for vulnerabilities and threats, continuous assessment ensures that potential issues are detected and addressed before they can cause significant harm.
3. Regulatory compliance
Continuous compliance processes help organizations stay updated with regulatory requirements, reducing the risk of non-compliance penalties and improving audit readiness.
4. Operational efficiency
Automated continuous monitoring reduces the manual workload on security teams, allowing them to focus on strategic tasks and improving overall operational efficiency.
5. Better awareness of IT assets
Continuous assessment provides better visibility into the organization's IT environment, helping to identify and manage vulnerabilities across all assets effectively.
6. Proactive security posture
By continuously assessing the cybersecurity landscape, organizations can maintain a proactive stance, anticipating and preparing for potential threats rather than reacting after an incident has occurred.
Section 3: Key components of continuous risk management
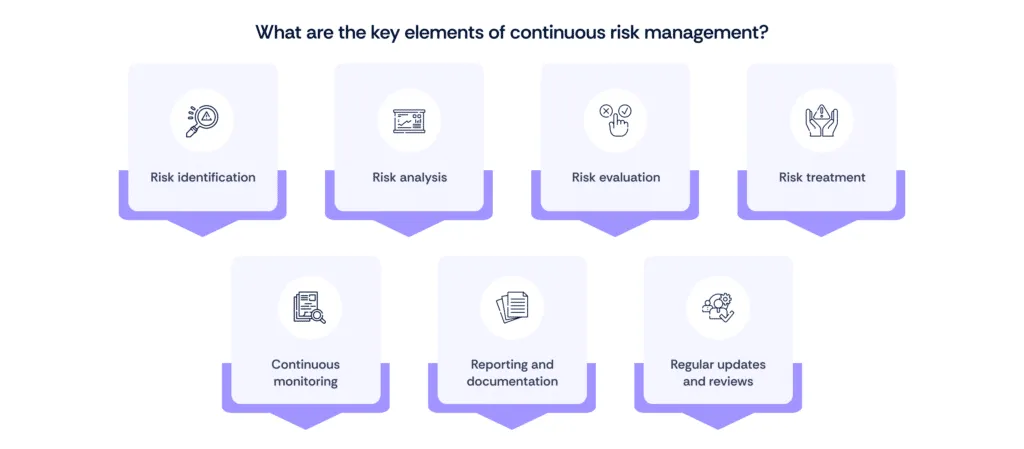
Continuous risk management in cybersecurity and compliance involves several key elements and ongoing processes to ensure the effective identification, evaluation, and mitigation of risks in real time. Here are the main components:
1. Risk identification
Continuously identifying new and emerging risks to the organization's IT systems and data. This involves monitoring for threats such as malware, phishing attacks, and other vulnerabilities.
2. Risk analysis
Analyzing identified risks to determine their potential impact and likelihood. This process helps prioritize risks based on their severity and probability, ensuring that the most critical threats are addressed promptly.
3. Risk evaluation
Evaluating the identified and analyzed risks to decide on the appropriate risk treatment options. This step involves comparing the level of risk against the organization's risk tolerance and compliance requirements.
4. Risk treatment
Implementing measures to mitigate, transfer, accept, or avoid identified risks. This can include deploying new security technologies, updating policies and procedures, or conducting training for employees.
5. Continuous monitoring
Ongoing monitoring of the risk environment to detect changes in the threat landscape. This involves using automated tools and technologies to track and respond to security events in real time, ensuring continuous protection and compliance.
6. Reporting and documentation
Keeping detailed records of risk assessments, treatment measures, and monitoring activities. Regular reporting to stakeholders and regulatory bodies is essential for transparency and demonstrating compliance.
7. Regular updates and reviews
Regularly updating the risk assessment process to incorporate new information and changing circumstances. This includes reviewing and revising risk management strategies to ensure they remain effective and aligned with current threats and compliance requirements.
Section 4: Implementing continuous risk management
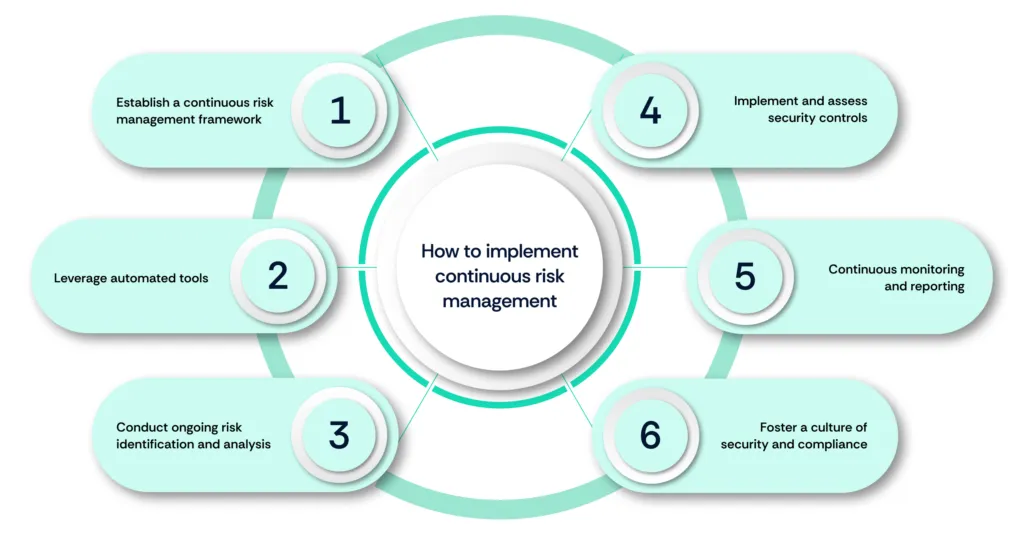
Implementing continuous risk management in cybersecurity and compliance involves several key steps and best practices to ensure ongoing protection and regulatory adherence. Here's a structured approach to implementation:
1. Establish a continuous risk management framework
Develop a comprehensive framework that includes policies, procedures, and tools for continuous risk monitoring and assessment. This framework should align with industry standards and regulatory requirements.
2. Leverage automated tools
Use automated compliance and risk management tools to monitor configurations, track changes, and analyze security impacts in real time. Automation enhances efficiency and accuracy, allowing for timely detection and mitigation of risks.
3. Conduct ongoing risk identification and analysis
Perform continuous, adaptive risk identification and assessment to keep up with evolving cybersecurity threats. This involves regular scanning for vulnerabilities and analyzing potential impacts on information systems.
4. Implement and assess security controls
Continuously implement, monitor, and assess security controls to ensure they remain effective against current threats. This includes periodic testing and updating of controls based on new threat intelligence.
5. Continuous monitoring and reporting
Establish continuous monitoring processes to track the security posture of all IT assets. Regularly report findings to stakeholders and regulatory bodies to demonstrate compliance and proactive risk management.
6. Foster a culture of security and compliance
Encourage a culture of continuous improvement in security and compliance across the organization. This involves training employees, promoting awareness, and ensuring that security practices are integrated into daily operations.
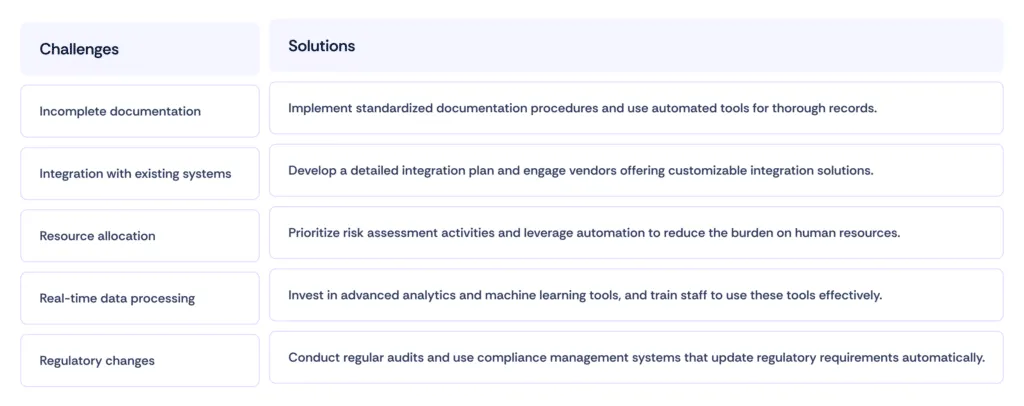
Challenges and solutions in implementing continuous risk management
Section 5: How can Scrut help implement continuous risk management?
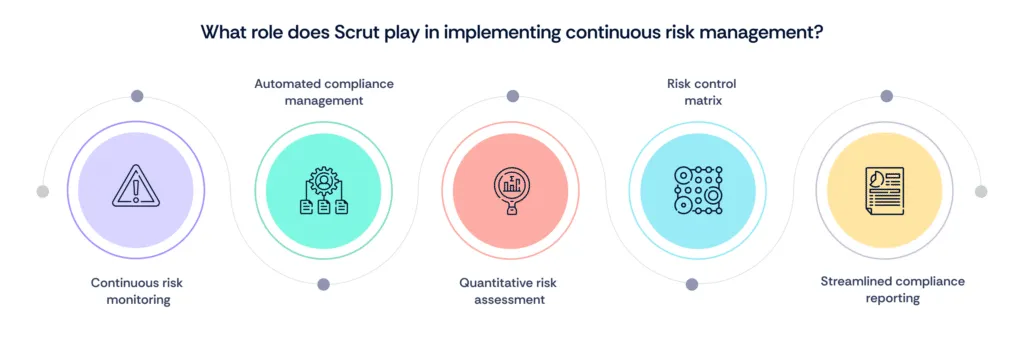
Scrut is a comprehensive compliance automation platform designed to streamline continuous risk management in cybersecurity and compliance. Here's how Scrut can assist:
1. Continuous risk monitoring
Scrut provides continuous risk monitoring, allowing organizations to stay aware of emerging threats and vulnerabilities in real time. This proactive approach helps promptly identify and address risks before they escalate.
2. Automated compliance management
The platform automates various compliance processes, reducing manual efforts and ensuring that all compliance requirements are met consistently. This automation includes regular updates and checks to stay aligned with changing regulatory standards.
3. Quantitative risk assessment
Scrut offers tools for mastering quantitative risk assessment, providing a structured method to evaluate and prioritize risks based on their potential impact and likelihood. This helps in making data-driven decisions to mitigate the most significant risks.
4. Risk control matrix
The platform includes a Risk Control Matrix (RCM) that helps in mapping out controls to specific risks, ensuring that appropriate measures are in place to manage and mitigate identified risks effectively.
5. Streamlined compliance reporting
Scrut simplifies the compliance reporting process by providing clear, domain-specific risk scores and overall compliance statuses. This feature ensures that organizations can maintain a transparent and up-to-date view of their compliance posture.
Final thoughts
In conclusion, the shift from point-in-time to continuous risk management is vital in today's dynamic cybersecurity terrain. Continuous risk management enables organizations to stay ahead of emerging threats, maintain regulatory compliance, and ensure the ongoing protection of sensitive data.
By adopting a proactive and real-time approach, organizations can enhance their risk management strategies, improve operational efficiency, and safeguard their reputation and customer trust. Embracing continuous risk management is not just a good practice but a necessity for robust cybersecurity and compliance in the modern digital age.
Ready to elevate your cybersecurity and compliance strategy? Discover how Scrut's comprehensive risk assessment solutions can help you stay ahead of threats and ensure continuous protection. Start your journey towards seamless compliance and proactive risk management with Scrut today!
FAQs
1. What is risk assessment in cybersecurity and compliance?
Risk assessment in cybersecurity and compliance involves identifying, evaluating, and mitigating potential threats to an organization's IT assets. It ensures the protection of sensitive data and helps maintain regulatory compliance by systematically analyzing vulnerabilities and assessing the potential impact of cyber threats.
2. What are the disadvantages of point-in-time risk assessment?
The main disadvantages include its static nature, which can quickly become outdated, and its limited ability to address dynamic and evolving risks. It only captures risks at a specific moment, missing ongoing changes, and may lead to a false sense of security if not regularly updated.
3. What is continuous risk management?
Continuous risk management involves the ongoing evaluation and monitoring of potential threats and vulnerabilities to an organization's IT systems and data. It provides a dynamic and real-time view of the risk landscape, allowing organizations to detect emerging risks promptly and respond swiftly.


















