FedRAMP decoded: A comprehensive reference guide for CISOs

The Federal Risk and Authorization Management Program (FedRAMP) is an initiative by the United States federal government that promotes the adoption of secure cloud services across the federal government by providing a standardized approach to security and risk assessment.
FedRAMP is crucial in the cybersecurity landscape because it provides standardized security assessments for cloud service providers (CSPs), mitigates risks, promotes cost efficiency, fosters collaboration, builds trust, and enables scalable and flexible cloud adoption within the federal government.
Understanding FedRAMP is essential for chief information security officers (CISOs) as it ensures compliance with federal regulations and enhances the security of federal cloud services. By comprehending the FedRAMP framework, CISOs can effectively navigate the authorization process, implement necessary security controls, and maintain a robust security posture, thereby safeguarding sensitive data and systems from potential cyber threats.
What is FedRAMP?
FedRAMP, short for the Federal Risk and Authorization Management Program, is a United States federal government initiative that aims to promote the adoption of secure cloud services across federal agencies.
It provides a standardized framework for assessing, authorizing, and continuously monitoring CSPs to ensure they meet stringent security requirements. FedRAMP facilitates the evaluation of CSPs’ security posture, streamlines the authorization process, and enhances the overall cybersecurity of federal cloud services.
What are the goals of FedRAMP?
The main objectives of FedRAMP are to increase the use of secure cloud services by government agencies, enhance the framework by which the government secures and authorizes cloud technologies, and build and foster strong partnerships with FedRAMP stakeholders.

It ensures robust security measures, streamlines assessments, reduces costs, fosters collaboration, and instills confidence in the adoption of cloud services by federal agencies.
What is the scope of FedRAMP?
The scope of FedRAMP is centered around the evaluation and authorization of Cloud Service Providers who offer services to federal agencies. The program focuses on assessing the security posture of CSPs and their cloud services to ensure they meet rigorous security standards.
This includes evaluating the confidentiality, integrity, and availability of the data stored and processed in the cloud, as well as assessing the overall risk management practices of the CSP.
FedRAMP covers a wide range of cloud service models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). The program’s scope also extends to continuous monitoring of authorized CSPs to ensure ongoing compliance and the maintenance of security controls.
What are the benefits of FedRAMP for CISOs?
There are several ways in which FedRAMP can benefit CISOs. Let’s look at some of them.

Enhanced security
FedRAMP promotes a standardized and rigorous approach to security assessments for CSPs. By leveraging FedRAMP-compliant CSPs, CISOs can ensure a higher level of security for federal cloud services, protecting sensitive data and systems.
Compliance assurance
FedRAMP compliance is crucial for CISOs in meeting federal regulations and requirements. By understanding and adhering to FedRAMP standards, CISOs can ensure their organizations’ cloud services align with the necessary compliance frameworks, reducing the risk of non-compliance penalties.
Streamlined evaluation
FedRAMP provides a centralized evaluation and authorization process for CSPs. CISOs can leverage this streamlined process to efficiently assess the security posture of potential CSP partners, saving time and effort in evaluating multiple providers individually.
Cost efficiency
FedRAMP eliminates the need for duplicate security assessments by providing a standardized framework. CISOs can leverage the FedRAMP authorization of CSPs, reducing the costs associated with conducting redundant evaluations and accelerating the procurement process.
Collaborative network
FedRAMP fosters collaboration and information sharing among federal agencies, CSPs, and third-party assessment organizations. CISOs can benefit from this network by gaining insights, best practices, and lessons learned from peers, enhancing their organization’s overall security posture.
Continuous monitoring
FedRAMP requires authorized CSPs to undergo continuous monitoring to maintain compliance. CISOs can leverage this aspect to ensure ongoing security and risk management of their organization’s cloud services, staying vigilant against emerging threats and vulnerabilities.
Overall, it offers CISOs enhanced security, compliance assurance, streamlined evaluations, cost efficiency, access to a collaborative network, and the benefits of continuous monitoring. By embracing and understanding FedRAMP, CISOs can effectively navigate the federal cloud landscape and strengthen their organization’s security posture.
The FedRAMP authorization process
There are basically two types of FedRAMP authorization processes – JAB authorization and agency authorization. Let us look at both of them and their respective processes in detail
JAB authorization process
The JAB, or Joint authorization board, is the primary governance and decision-making authority for FedRAMP. The JAB is composed of the Chief Information Officers (CIOs) of the Department of Homeland Security (DHS), the General Services Administration (GSA), and the Department of Defense (DoD).
The JAB defines and establishes the FedRAMP, the basic security control and accreditation criteria for the Third Party Assessment Organizations (3PAOs). It also works in conjunction with FedRAMP program management office (PMO) to ensure that the baseline security controls are incorporated into consistent and repeatable processes for security assessments and authorizations of cloud service offerings (CSOs).
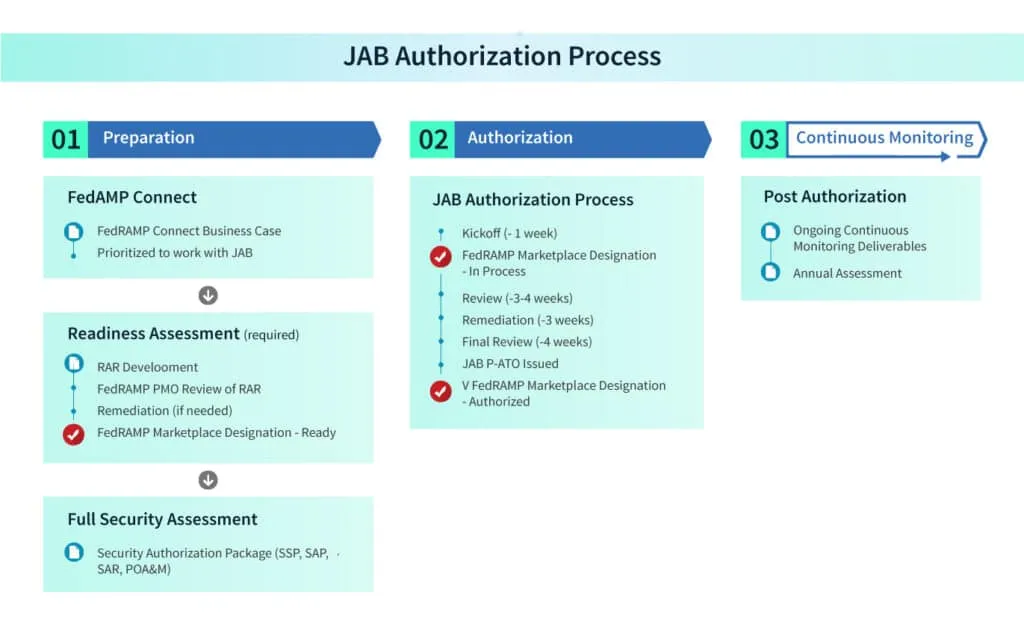
Here is a step-by-step breakdown of the JAB FedRAMP authorization process.
Phase 1: Preparation
There are three parts to the preparation stage of the JAB authorization process.
FedRAMP Connect
The JAB focuses on creating a diverse marketplace of providers but can only authorize a limited number of CSOs annually due to resource and funding constraints. To ensure a clear return on investment, CSOs undergo evaluation and prioritization through FedRAMP Connect. The key criterion for JAB prioritization is demonstrating government-wide demand for the CSO.
CSPs must provide proof of demand from six customers. After achieving a JAB Provisional Authorization To Operate (P-ATO), CSPs need a minimum of six unique federal agency customers to meet Continuous Monitoring requirements. The JAB prioritizes up to 12 CSOs per year, who have 60 days to become FedRAMP Ready, marking the first phase of the JAB Authorization process.
FedRAMP Ready
To pursue a JAB P-ATO or agency ATO, CSPs must obtain a FedRAMP Ready designation. While it doesn’t guarantee authorization, being FedRAMP Ready increases the chances of prioritization. This designation remains valid for one calendar year after approval.
To achieve FedRAMP Ready status, CSPs work with a FedRAMP-recognized 3PAO to conduct a Readiness Assessment. The resulting Readiness Assessment Report (RAR) showcases the CSP’s security capabilities. The RAR is reviewed by the FedRAMP PMO, and if approved, the CSO is listed as FedRAMP Ready on the Marketplace.
This exposure benefits CSPs as they are researched by potential agency customers. CSPs can also use the RAR for self-assessment and to identify any gaps in meeting FedRAMP requirements. Detailed steps can be found in the FedRAMP Marketplace Designations for Cloud Service Providers document.
Full security assessment
Once a CSO is prioritized and deemed FedRAMP Ready, the CSP finalizes the System Security Plan (SSP) and engages a FedRAMP-recognized 3PAO. The 3PAO conducts a comprehensive security assessment and provides a Security Assessment Report (SAR). The CSP participates in the assessment activities and develops a Plan of Action and Milestones (POA&M) to manage security risks.
These documents, prepared using FedRAMP templates, are submitted together as a full security package. The JAB reviews the entire package along with the first Continuous Monitoring submission. The package must be submitted to the PMO at least 2 weeks before the JAB Kickoff Meeting, following a completeness check by the FedRAMP PMO.
Phase 2: Authorization
The JAB Authorization Process follows an agile methodology with multiple stage gates and a “fail fast” principle. The first gate is the JAB Kickoff, where the CSP, 3PAO, and FedRAMP review the system architecture, security capabilities, and risks. Based on the outcome, the JAB decides whether to proceed or not. The JAB then conducts an in-depth review, addressing questions and comments with the CSP and 3PAO. After remediation, the JAB issues a formal authorization decision, including a P-ATO if favorable.
CSPs can be removed from the process for major architectural or unresolved deficiencies. During the process, the CSP and 3PAO must answer detailed questions and submit monthly Continuous Monitoring (ConMon) deliverables. The JAB P-ATO signifies acceptance by three JAB agencies, while individual agencies issue their own authorization for using the product.
Phase 3: Continuous monitoring
After receiving a JAB P-ATO, the CSP must ensure that its security posture remains in accordance with FedRAMP’s requirements established during the initial assessment and authorization process. This is accomplished through the practice of Continuous Monitoring, which involves the ongoing monitoring and assessment of the CSP’s system. As per NIST SP 800-137, the goal of continuous monitoring is to provide (1) operational visibility, (2) managed change control, and (3) attendance to incident response duties over the life or use of a system.
For systems with JAB P-ATOs, the JAB serves as a centralized PMO for Continuous Monitoring activities. It provides agencies with standardized processes and artifacts for assessing and managing JAB P-ATO systems. Here’s a simplified breakdown of the JAB’s responsibilities:
- Reviews and approves Continuous Monitoring and security artifacts regularly.
- Monitors, suspends, and revokes a system’s P-ATO as needed.
- Authorizes or denies requests for Significant Change and deviations.
- Reviews incident information to ensure proper handling and closure.
- Ensures the FedRAMP PMO delivers artifacts to leveraging agencies promptly.
For leveraging agencies, the JAB’s Continuous Monitoring artifacts inform the final approval authority, which lies with each agency’s designated Authorizing Official (AO).
In addition to continuous monitoring, a CSP must engage a 3PAO recognized by FedRAMP to conduct an annual security assessment. This assessment includes updating penetration testing results, a comprehensive assessment of critical controls, and a full evaluation of all system controls over three years.
Agency authorization process
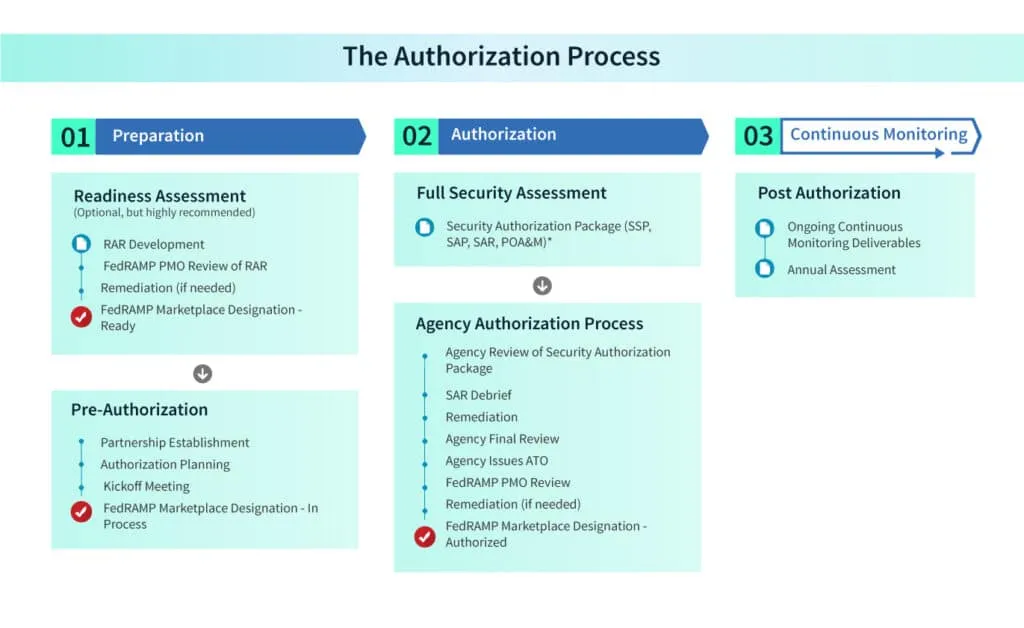
Like the JAB authorization process, the agency authorization process is also done in phases. Let’s look at different phases of the agency authorization process.
Phase 1: Preparation
Phase 1 is further divided into various processes:
1. FedRAMP Ready
A FedRAMP Ready designation is recommended for the Agency Authorization process, although it is optional. To achieve this designation, a CSP must collaborate with a FedRAMP-recognized 3PAO to conduct a Readiness Assessment of its service offering. The assessment, called the RAR, demonstrates the CSP’s ability to meet federal security requirements.
CSPs that successfully achieve the FedRAMP Ready designation are listed on FedRAMP’s Marketplace. The FedRAMP Marketplace is used by agencies to research cloud services that align with their specific organizational needs. If a CSP aims to attract government clients, being FedRAMP Ready provides valuable information about the security of their service offering through the FedRAMP Marketplace.
Moreover, for CSPs contemplating whether to pursue FedRAMP Authorization, the RAR can serve as a self-assessment tool. It helps identify any security gaps in the service offering and provides insight into areas that need improvement. This information enables CSPs to understand the level of effort required to align their system(s) with FedRAMP requirements before pursuing an Authorization to Operate (ATO) with an agency.
2. Pre-authorization – Partnership establishment
During the partnership establishment phase of Pre-Authorization, a CSP formalizes its partnership with an agency by meeting the requirements specified in FedRAMP Marketplace Designations for CSP. This can occur when a vendor is already under contract with an agency or when an agency is going through the acquisition process.
At this stage, the CSP should have a fully operational system and an executive team that is committed to the FedRAMP process. The CSP needs to engage with the FedRAMP PMO by completing a CSP Information Form as part of the intake process. The PMO will generate a FedRAMP ID for the CSP upon form completion.
Before identifying an agency partner, the CSP must determine the security categorization of the data that will be stored in the system. To do this, the CSP should use the FedRAMP FIPS 199 Categorization Template (Attachment 10) in the SSP and refer to the guidance provided in NIST Special Publication 800-60 Volume 2 Revision 1. This analysis will help the CSP appropriately categorize its system based on the types of information processed, stored, and transmitted. It will also determine the impact level that best fits the system.
Once a partnership is established, the CSP needs to confirm the impact level with the agency. The agency will conduct its own assessment based on FIPS 199 to validate the impact level chosen by the CSP.
3. Authorization planning
Once the partnership is established, a CSP should:
- Confirm resources dedicated to the authorization process
- Work with the agency to select a 3PAO for the assessment in Phase 2
- Complete FedRAMP training for CSPs
- Determine the agency’s approach for reviewing the authorization package as a just-in-time linear approach or all deliverables provided simultaneously approach
- Complete a Work Breakdown Structure (WBS) with the assistance of your agency partner and send it to PMO for review
- Work with your agency partner to complete an In-Process Request form indicating the readiness to begin the kickoff meeting
- Begin working on the Kickoff Briefing Deck
4. Kickoff meeting
The final step in this phase is to prepare for and conduct a Kickoff Meeting. The purpose of this meeting is to officially start the Agency Authorization process by introducing key team members, reviewing the Cloud Service Offering (CSO), and ensuring everyone is on the same page regarding the process and milestone timelines. Although the FedRAMP PMO coordinates and facilitates Kickoff Meetings, the primary focus is to support the partnership between the CSP and the agency.
By the end of the Kickoff Meeting, all stakeholders will have a shared understanding of the following:
- The overall authorization process, including milestones, deliverables, roles and responsibilities, and schedule
- The purpose and function of the CSO, authorization boundary, data flows, known security gaps and plans for remediation, agency-specific requirements, customer-responsible controls, and areas that may require agency risk acceptance
- The agency’s process for reviewing the authorization package and making a risk-based authorization decision
- The PMO’s process for reviewing the authorization package from a government-wide reuse perspective
- Best practices and tips for a successful authorization process
After the Kickoff Meeting, CSPs can gain access to FedRAMP’s secure repository (unless the system’s impact level is High). Additionally, CSPs that are not already listed as “In Process” on the FedRAMP Marketplace may be eligible for listing if the agency is comfortable with the briefing and timelines. However, please note that not all systems will be eligible for listing based solely on the Kickoff Meeting. It is important to engage with the PMO regarding the “In Process” status after completing this step.

Phase 2: Authorization
During this phase, the 3PAO conducts system testing while the CSP engages with them to develop a Security Assessment Plan (SAP). If the CSP has followed the Just-In-Time linear approach with an agency, it’s recommended to obtain agency approval for the SAP before testing begins. It’s crucial to freeze the system and avoid any changes during testing. Once testing is complete, the 3PAO prepares a SAR with findings and a recommendation for FedRAMP Authorization.
Based on the SAR findings, the CSP develops a POA&M in collaboration with the 3PAO. The POA&M outlines the plan for addressing the identified issues from testing. Afterward, a SAR Debrief presentation is conducted, which should be shared with the PMO for review before scheduling the meeting. The SAR Debrief aims to inform the agency’s risk review of the CSO.
During the SAR Debrief, the 3PAO presents the security assessment results, the CSP presents the plan and timeline for addressing residual risk, and the FedRAMP PMO provides guidance on remaining milestones and success tips. While the PMO facilitates the SAR Debrief, its purpose is to support the CSP and agency partnership.
By the end of the SAR Debrief, all stakeholders will have a shared understanding of:
- The 3PAO’s assessment approach, methodology, and schedule
- The scope of testing, including the validation of the authorization boundary and data flows
- The assessment results and residual risk
- The CSP’s plan and timeline for remediating residual risk
- Deviation requests requiring agency approval (such as risk adjustments and false positives)
- Operationally required risks necessitating agency risk acceptance (e.g., essential services or components excluded from the tested boundary)
- The agency’s process for reviewing the authorization package and making a risk-based authorization decision
- The PMO’s process for reviewing the authorization package from a government-wide reuse perspective
- Best practices and tips for a successful authorization process
Phase 3: Continuous monitoring
Once a CSP obtains FedRAMP Authorization, they are required to provide monthly ConMon deliverables to the agencies using their service. These deliverables include an updated POA&M, vulnerability scan results/reports, deviation requests, Significant Change requests, incident reports, and the Annual Assessment package. Agencies review these monthly ConMon deliverables.
CSPs with cloud offerings categorized as LI-SaaS, Low, or Moderate use the FedRAMP secure repository to post their monthly ConMon materials. However, CSPs with cloud offerings categorized as High use their own secure repository.
The FedRAMP PMO encourages CSPs with multiple customer agencies to streamline the ConMon process and minimize duplicative efforts through a collaborative approach. The PMO has developed a recommended collaborative ConMon approach outlined in the Guide for Multi-Agency Continuous Monitoring. This approach allows agencies to share responsibility for ConMon oversight and provides a central forum for addressing deviation requests, Significant Change requests, and the Annual Assessment instead of coordinating with each agency individually. CSPs who are FedRAMP Authorized and wish to set up a Multi-Agency ConMon Group can request assistance by contacting info@fedramp.gov.
Additionally, a CSP must employ a FedRAMP-recognized 3PAO to conduct an annual security assessment to maintain an acceptable risk posture throughout the system’s lifecycle. The Annual Assessment, along with updated security authorization package documentation, must be uploaded to the FedRAMP secure repository. CSPs should notify FedRAMP via info@fedramp.gov when this process is complete.
Which businesses need FedRAMP certification?
FedRAMP certification is primarily required for CSPs that wish to offer their cloud services to U.S. federal government agencies. These cloud-based technology providers, which may include companies or organizations, must obtain FedRAMP certification if they want to bid on and provide cloud services for government contracts.
It’s important to note that not all businesses need FedRAMP certification. The requirement is specifically targeted at CSPs that want to offer cloud services to federal agencies. If a business does not intend to provide cloud services to the U.S. government or its agencies, FedRAMP certification is not mandatory.
However, some businesses may choose to pursue FedRAMP certification voluntarily, even if they do not directly work with the government. This certification can serve as a valuable credential and provide assurance to other customers about the security and reliability of their cloud services.
In summary, FedRAMP certification is required for cloud service providers seeking to offer their cloud services to U.S. federal government agencies. Other businesses that do not work with the government may pursue FedRAMP certification voluntarily for its potential benefits in the broader market.
What are the different FedRAMP levels?
The Federal Risk and Authorization Management Program (FedRAMP) classifies CSPs and CSOs into three impact levels: low, moderate, and high. These levels correspond to the sensitivity of the data the cloud provider can handle, store, and transmit.
At the low-impact level, a CSP is authorized to host data intended for public use, and unauthorized access to this data would not pose significant risks to the client’s mission, safety, finances, or reputation.
The moderate-impact level permits a CSP to host non-public data, like personally identifiable information (PII), where a breach could have serious consequences for an agency’s operations.
For the high-impact level, a cloud provider is deemed secure enough to handle sensitive federal information, such as law enforcement, emergency services, and healthcare data. Breaches of such data could be catastrophic, leading to operational shutdowns, financial losses, or even posing risks to intellectual property and human life.
These security levels are established in the National Institute of Standards and Technology’s (NIST) Federal Information Processing Standard 199 (FIPS 199), which defines data security as the protection of information confidentiality, availability, and integrity.
How to determine and implement these risk levels?
To determine the risk level, a CSP or CSO must undergo a security assessment conducted by a certified third-party assessor. This assessment evaluates the cloud service or product’s security controls against those specified in relevant NIST publications, such as NIST 800-53.
CSPs use these risk ratings to ensure that their information systems meet the minimum security requirements necessary to process, store, and transmit data for their federal government customers. Federal agencies select cloud providers, products, and services based on the required level of security. For example, an agency handling non-sensitive government information might use a cloud service with a “low impact” risk level.
Each risk level mandates a minimum number of security controls to ensure that the cloud service or product adequately safeguards the contained information. Under FedRAMP, high-level cloud providers, products, or services must comply with 421 controls, while moderate-level CSPs need to implement 325 controls, and low-level providers only require 125 controls.
Controls refer to the technologies and techniques that CSPs employ to secure federal information stored in the cloud.
In June 2016, FedRAMP released the high-level security baseline, allowing federal agencies to outsource highly sensitive data to any high-level cloud services provider that is FedRAMP compliant. Prior to this, agencies could only outsource low-level and moderate-level information and workloads to CSPs.
FedRAMP’s Joint Authorization Board, consisting of chief information officers from the U.S. Department of Defense (DoD), the U.S. Department of Homeland Security (DHS), and the General Services Administration (GSA), establishes FedRAMP accreditation standards and reviews FedRAMP authorizations.
How much does it cost to get FedRAMP certified?
Complying with FedRAMP, the government program that certifies the security of cloud-based technology providers bidding on government contracts can be quite costly. The certification expenses for CSPs used by federal agencies can vary significantly, ranging from several hundred thousand dollars to over $1 million.
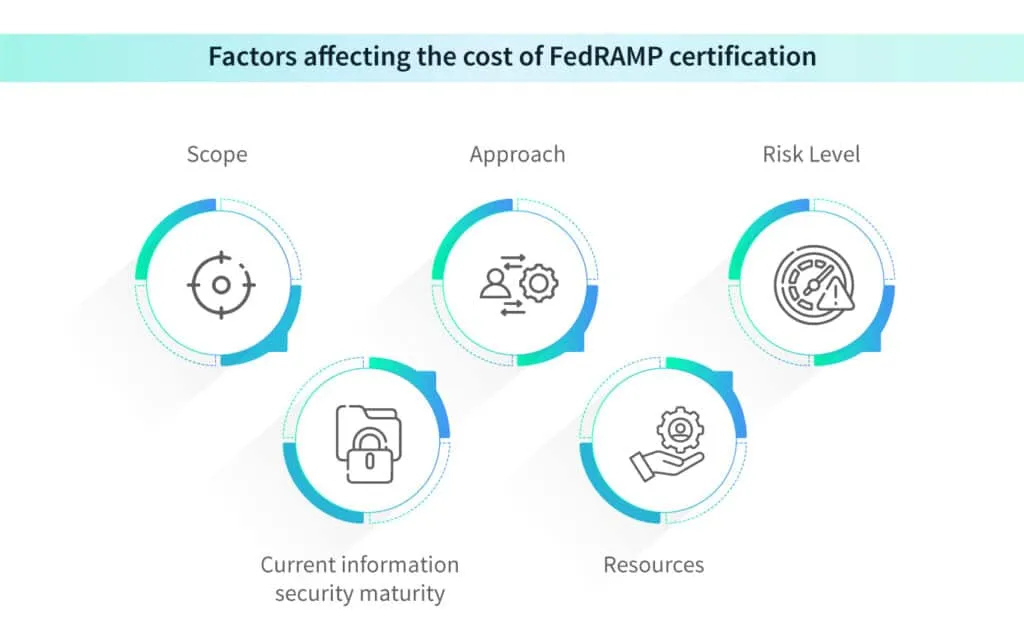
The total cost is influenced by several key factors, which include:
- Scope: The number and complexity of services you intend to authorize for federal government use will impact the certification cost. More services or complex offerings may require additional security measures and assessments, leading to higher expenses.
- Approach: The choice between an agency Authorization to Operate (agency ATO) and the broader Joint Authorization Board Provisional Authorization to Operate (JAB P-ATO) can affect costs. The JAB P-ATO, overseen by multiple agencies, requires a pre-authorization readiness assessment, adding both time and expenses to the process. However, the FedRAMP Accelerated program aims to reduce costs and streamline the JAB P-ATO process, aiming for completion in six months or less.
- Risk Level: FedRAMP categorizes the data being processed into three impact levels based on its security requirements: low, moderate, and high. Higher impact levels demand more stringent controls and more comprehensive security assessments by third-party assessment organizations (3PAOs). These assessments typically cost around $150,000 to $200,000, including the baseline readiness assessment (recommended for JAB P-ATO but not required for ATO).
- Current information security maturity: The security level of your existing cloud solutions and the up-to-dateness of your cybersecurity program play a role in certification costs. If your cloud solutions are already compliant with other frameworks like FISMA or NIST, it may facilitate the process. However, the JAB review of your readiness assessment might require you to address any vulnerabilities and adjust your current cloud security controls, which can constitute around 50 percent of the certification expenses.
- Resources: Having qualified staff to guide your organization through the authorization process can impact the overall cost. If you require external consultants, their fees can range from $20,000 to $40,000 for short-term assistance and possibly more if you need continuous support throughout the FedRAMP compliance process.
Conclusion
In conclusion, the Federal Risk and Authorization Management Program (FedRAMP) is a critical initiative in the cybersecurity landscape, promoting secure cloud services adoption within the US federal government. By providing standardized security assessments, mitigating risks, fostering collaboration, and ensuring compliance, FedRAMP enables CISOs to navigate the authorization process, implement necessary security controls, and safeguard sensitive data and systems.
Embracing FedRAMP empowers CISOs to enhance security, achieve cost efficiency, and maintain a robust security posture, ultimately strengthening the overall cybersecurity of federal cloud services.
If you want to know more about how Scrut can help you with your FedRAMP compliance, book a demo by clicking here.

Frequently asked questions
1. What types of businesses need to be FedRAMP compliant?
FedRAMP certification is required for cloud service providers (CSPs) that want to offer cloud services to U.S. federal government agencies. Other businesses may pursue it voluntarily for market advantages.
2. Is FedRAMP certification perpetual, or does it require regular renewal?
FedRAMP certification is not perpetual and must be renewed periodically to ensure ongoing compliance with evolving security standards.
Can FedRAMP certification be recognized internationally?
While FedRAMP is specific to the U.S. government, its security standards and practices align with many international security frameworks, making it a valuable reference for global best practices. However, it is not a direct substitute for international certifications.


















