How to develop an effective vendor management policy?

Vendor management is one of the most overlooked facets of risk management. Incidentally, these vendors become an entry point for hackers. Organizations need to be aware of how many vendors and their employees have access to the organization’s sensitive data.
Keeping this in mind, organizations are making data secure yet accessible to vendors by creating a vendor management policy (VMP). As the term suggests, the primary goal of vendor management policies is to manage and assess vendors to safeguard the sensitive information in the organization’s network.
That said, many elements go into creating an effective, applicable, and useful vendor management policy. So, sit tight as we walk you through the entire vendor management process, including how to use the vendor management policy and its best practices.
What is a vendor management policy?
Vendor Management Policy (VMP) is a method for organizations to identify and prioritize vendors that pose a risk to an organization’s business.
Through this policy, organizations prescribe controls to identify vendors to minimize risk and ensure compliance with popular information security frameworks like SOC 2. Vendor Management Policies play a vital role in maintaining an organization’s overall compliance risk management strategy. So, it would be wrong to assume that VMPs are a simple addition to your journey toward compliance.
But this apart, why do organizations need a vendor management policy?
Why do organizations need a vendor management policy?

A vendor management policy aims to pinpoint which vendors constitute a risk to your organization and then specify procedures to reduce the identified third-party risk. While that is a huge reason organization should implement a vendor risk management policy, there are more benefits organizations can reap.
1. Ensure legal compliance
Each industry, be it finance, healthcare, retail, energy, and even others, have its legal compliance requirements. If these compliance requirements are not timely and duly satisfied, an organization might face trouble in terms of revenue loss, fines, and/or data breaches.
Regulators will not oversee whether you or your vendor made a mistake; non-compliance could result in lawsuits for both parties involved. With a vendor management policy in place, you will be safe from legal complications by assessing the security posture of vendors beforehand.
2. Secure sensitive data
If your organization stores, uses, or accesses clients’ personal data, you should be concerned about the exposure of said data, especially with vendors. Most organizations outsource part/s of their operations to vendors to save costs or to leverage the expertise that they have after working in the industry.
For this to be done successfully, sharing company data and, often, customer data is inevitable. However, one misstep from either of your vendors can put your customers’ data at risk and expose your organization to hackers and cyber-criminals. A vendor management policy acts as a combat against this while onboarding vendors.
3. Improve visibility into the vendor network
Organizations should be aware of the security vulnerabilities third-party vendors bring into the organization. A proper vendor management policy enables an organization to know, prepare and reduce the related risks.
It also allows organizations to understand whether vendors are enhancing the security posture, thereby solidifying or eliminating their position in the vendor network.
4. Minimize data breach costs
Data breaches are costly, and it is important to prevent them. Vendors are/can be the primary source of data breaches. An optimized vendor management policy can save the day. Not only can IT vendor management policy effectively limit data breach costs, but it can also reduce the likelihood of data breaches.
How to create an effective vendor management policy?
To create an effective vendor management policy, organizations should follow these steps.
1. Putting together a team
It is the first step to developing a successful vendor management policy and controlling your third-party relationships. The main idea is to have a well-established team with members from different departments such as IT and security, finance, legal, and compliance.

2. Vendor evaluations are a must
Moving ahead with vendor management policy is credible only when you have an insight into the current vendors. By including vendor evaluations in your vendor management strategy, your firm can better understand the risks associated with using a vendor’s product or service.
3. Audit your existing vendor relationships
The next step is auditing your existing vendor relationships, which includes identifying all current contractors, suppliers, and other third parties in business with any part of your organization.
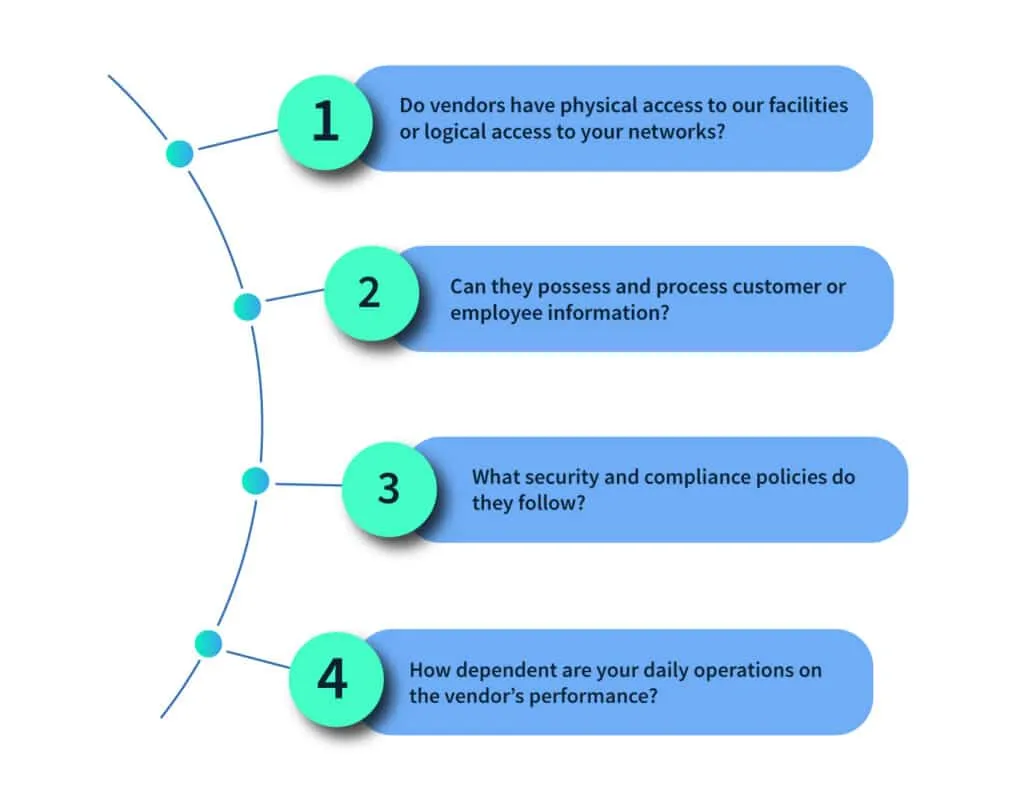
Asking these questions will provide you with the resources to understand the scope and magnitude of risk posed by your vendors. Once that information is attained, you can create a third-party vendor management policy.
What should be included in the vendor management policy?
Vendor management is more than a one-stop finish process. To ensure that you are effectively managing your vendors, here are a few elements you should consider incorporating while creating and implementing a vendor management policy in your organization.
1. Purpose of the policy
This will provide an overview of what the management policy will consist of. You can consider this section as a thesis statement or a description that holds the list of all elements that are to be included in the vendor management policy.
2. The audience and scope of the policy
The second element is that organizations must clearly define who falls under the jurisdiction of the vendor management policy. Create a master list of all your current vendors and potential future acquisitions, using which you can carve out the audience and scope of your vendor management policy.
3. Division of roles and responsibilities
Most organizations divide their employees into two groups; one group enforces the vendor management policy, and the other reviews and updates it. You can assign specific roles and responsibilities within these broad groups for a clear understanding.

4. Add precise terminology
Prepare a formal glossary of terms that your organization uses in the policy. This will benefit your organization in two ways; firstly, the meaning of terms for anyone reviewing the policy in the future will be evident and apparent, and secondly, it will present your understanding of the third party in clear and structured terms.
5. Include the vetting process
This section of the policy specifies the processes used by your organization to assess and study a vendor before dealing with them. It primarily includes information on non-disclosure agreements between the parties, details on the data access provided to the vendors, what will entail if vendor assessment provides high-risk results and how many times vendor assessment will take place.
6. Enlist all vendor management information
All processes involved, from the onboarding of a new vendor to the deboarding of a current vendor, must be specified under this section. You can include statements concerning minimum information requirements, instructions for destroying or disposing of the organization’s data, and incident response criteria.
7. Enforcement of the policy
One of the last elements that you must include to make your vendor risk management policy effective is enforcement. Along with the details of policy execution, this section should also spell out the ramifications of a vendor’s failure to follow the policy. It might entail contract termination, access privileges withdrawal, or other civil or criminal sanctions.
How to use the vendor management policy to assess new vendors?
Many organizations do not have the bandwidth to overlook third parties, which helps them go under the radar and conduct harmful practices. Your networks could be compromised by their security procedures, subjecting your organization to financial, legal, and regulatory repercussions.
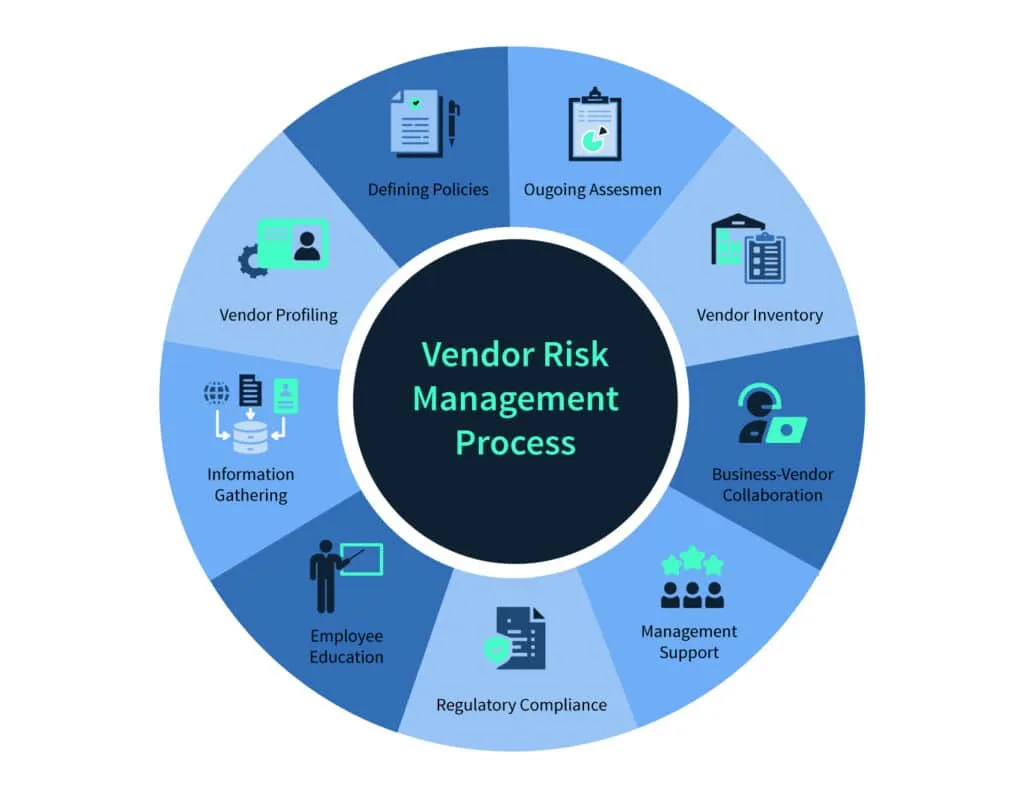
Therefore, each organization must assess whether a potential vendor satisfies an acceptable risk threshold before closing a deal with them. The vendor management team will have to conduct an assessment in accordance with the vendor management policy.
The level of risk connected with the vendor’s participation will determine how in-depth this assessment needs to be. Vendors with restricted access to networks or data may not pose a significant risk and would only need to answer a short questionnaire.
On the other hand, high-risk suppliers who interface their systems with your networks or access personal identifying information (PII) and sensitive information from your firm will require a thorough examination. They may be required to submit to security audits, penetration tests, and other means of verifying their security posture and integrity.
Best practices to follow to improve vendor management
Whether you operate with a single vendor or many, failing to have a vendor management policy puts your company at risk. To avoid putting your organization at the threshold of third-party threats, you must follow some best practices to develop or improve your existing vendor management policy.
- Have a contingency plan in place in case of vendor service failures: Your organization must be ready to act wisely in case a vendor exposes your networks to threats. Assign duties and responsibilities to employees and create an incident response plan beforehand by studying the impact of the vendor’s product in different sectors of your firm.
- Dedicate a full-time manager for vendor relationships: As you expand your management team, you should aim to assign a dedicated manager to each of your vendors. This will be advantageous from a managerial standpoint, especially in the long term.

- Keep your policy simple and straightforward: A vendor management policy should provide a general picture of how you intend to manage vendors.
- Ensure that all vendors are held to the same standards: It’s critical that all of your vendors have the same set of rules when it comes to risk management. Those posing major hazards should receive additional attention from stakeholders.
- Keep your policy up to date: As business processes evolve, ensure that your vendor management policy is updated on a regular basis. If quarterly or semi-annual updates aren’t practicable, strive to update your vendor management policy at least once a year.
Is simply implementing a vendor management policy in my organization enough to tackle third-party risks? This is a question most organizations ask themselves, and rightfully so because vendor management policies help in bringing third-party risk under control, but they are only successful if you have the systems or tools to monitor vendor compliance continuously. This is where Scrut comes in!
Scrut is an innovative and radically simple governance, risk, and compliance automation platform for growing startups and mid-market enterprises. With Scrut, compliance teams can reduce ~70% of their manual effort in continuously maintaining compliance towards SOC 2, ISO 27001, GDPR, PCI DSS, HIPAA, and CCPA. Schedule your demo today to see how it works.
Frequently Asked Questions (FAQs)
1. What are the consequences of not having an effective vendor management policy in place?
In the absence of a vendor management policy, organizations may have to spend a lot of resources to remediate damage caused by cyberattacks, with third parties being some of the most common sources. Aside from monetary penalties, a security breach can have long-term legal and regulatory consequences for your company, not to mention reputational damage and loss of customer trust.
2. What are critical vendors, and how can organizations manage them?
A critical vendor is any vendor who can expose an organization to significant risk if the third party fails to meet expectations or has a significant impact on customers. Organizations must pay close attention to these vendors and manage their security practices constantly. Having an incident response plan is essential when critical vendors are involved.
3. What is a good vendor risk management policy example?
Every organization has its own network of vendors, which they substantially manage and control. A good vendor management policy example will involve a procedure where all the elements mentioned in the article above are included and implemented, such as purpose, scope, division of roles and responsibilities, vetting requirements, and enforcement.


















