Defining cyber and compliance risk for mid-market businesses

Ransomware attacks. Fines from data protection regulators. Lawsuits from customers after a breach.
In 2023, mid-market businesses face all of these cyber and compliance risks, and more.
While enterprises might be the most frequent targets, they also have the resources – people and tools – to address them more effectively. And data suggests smaller businesses suffer disproportionately more after a cyber attack than bigger ones.
The good news, though, is that while this all might seem scary, there is something you can do about it.
In this post, we’ll take a look at defining cyber and compliance risk. By breaking both of these terms down into their core parts, businesses can begin to develop a comprehensive risk management program to address them.
What is cyber risk?
While cyber risk might be top of mind for many people, they might have different ideas of what it means. Thus, it’s important to define.
Simply put, risk is the probable frequency and magnitude of future loss.
And cyber risk is that which results from losses to data confidentiality, integrity, or availability.
The CIA triad: confidentiality, integrity, and availability
Data confidentiality, integrity, and availability, known together as the CIA triad, are key requirements for any modern business, regardless of sector. And potential losses to any of these components represents cyber risk.
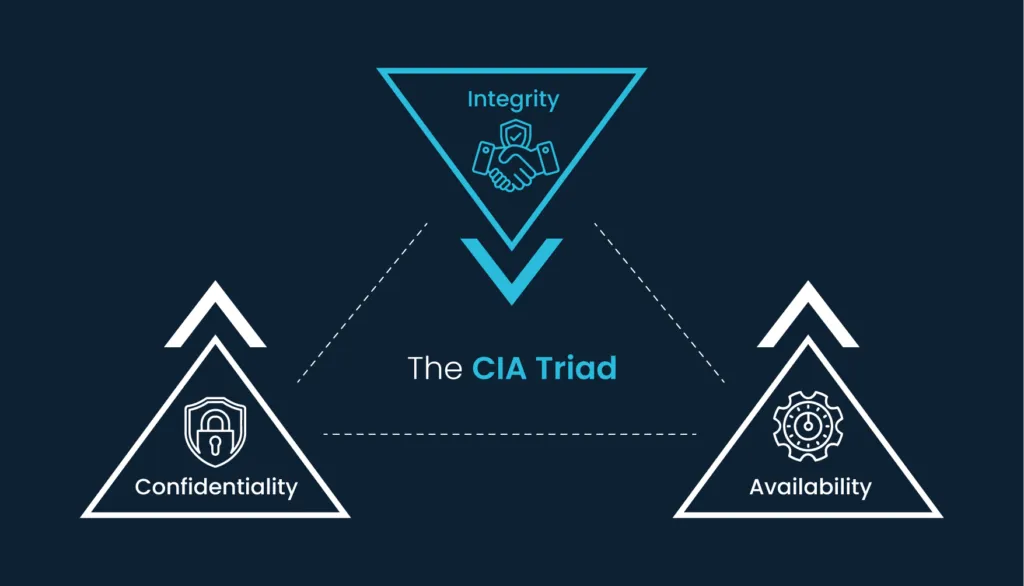
- Confidentiality refers to the protection of sensitive information from unauthorized access or disclosure. Even the most transparent business needs to keep information private, such as:
- Customer, partner, and employee personally identifiable information (PII).
- Financial statements and projections.
- Intellectual property like product specifications, strategic plans, and competitive analyses
- Integrity involves preserving the accuracy and consistency of data over its entire lifecycle, ensuring that it remains unaltered and uncorrupted from creation to disposal. Maintaining data integrity is vital for businesses to:
- Ensure reliable decision-making.
- Support daily operations.
- Availability ensures that systems are accessible and usable when needed by authorized users. Maintaining it is crucial for:
- Employee productivity.
- Continued revenue generation.
- Physical safety, in use cases like manufacturing and healthcare.
Cyber risk versus compliance risk
Cyber risk and compliance risk are two distinct yet interconnected aspects of an organization’s overall risk picture.
Cyber risk refers to the immediate consequences of potential loss to data CIA. These situations can lead directly to decreased productivity and competitive advantage, response and replacement costs, fines and judgements, as well as reputation damage.
Some real-world scenarios include a:
- Ransomware attack preventing employees from doing their job or collecting revenue. After the NotPetya virus outbreak in 2017, for example, FedEx estimated it lost $300 million of potential earnings in the relevant quarter, in part due to forgone revenue.
- Data breach causing a company’s intellectual property property being posted on the public internet. This happened to the video game maker Capcom in 2020 after it refused to pay an extortion demand.
- Loss of customer trust after a data leak leading to reduced sales. Target, which suffered a major data breach in 2013, saw sales decline 3.8% in the relevant quarter.
In contrast, compliance risk arises when an organization doesn’t follow applicable laws, regulations, or industry standards. Compliance risks can also lead to additional losses.
In the above examples, the victims suffered directly from the loss of data CIA. In contrast, compliance risk might materialize when:
- A customer terminates a contract with a vendor who fails to achieve re-certification under ISO 27001.
- Consumers file a lawsuit against a company after it leaks their PII, alleging that it failed to protect the data sufficiently in accordance with the California Consumer Privacy Act (CCPA). There have been almost 200 cases of this happening already.
- Payment Card Industry (PCI) organizations auditors find your business is not handling credit card information according to the Data Security Standard (DSS), and you are fined until you are back into compliance.
While both types of risk can have significant consequences for an organization, they are intrinsically linked in the sense that effectively managing cyber risk often goes hand-in-hand with maintaining regulatory compliance.
Cybersecurity as one of many business risks
All businesses are, at their core, about delivering value. And executives need to deal with a lot of risks while they are doing this.
While leaders will understandably seek to minimize each of the following, it is simply a fact of life that businesses must contend with risks related to the following components.
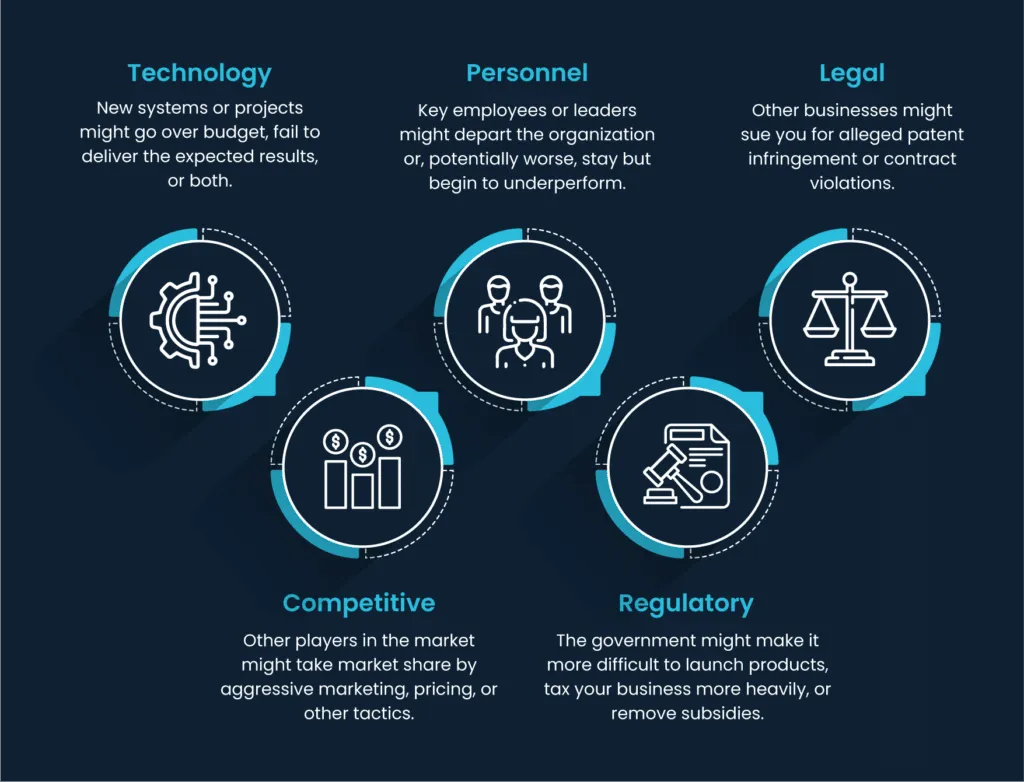
If you add cyber and compliance risk to this list, dealing with all of these effectively while still delivering value can seem overwhelming.
And you will never eliminate risk entirely.
The key is understanding exactly where you are exposed and managing all of these risks effectively. And next month, we’ll dive deeper, identifying the sources of cyber and compliance risks.
Conclusion
Cyber and compliance risk are simply another set of challenges – among many others – that business leaders face. Understanding what they are is the first step toward addressing them systematically.
While, in general, cyber risk should be the primary focus, a strong security posture can help you meet compliance obligations as a consequence. And for resource-strapped businesses operating in the mid-market, there are tools and techniques that can help you address both simultaneously.
“Must haves” are a program or process that lets you:
- Identify the relevant risks
- Measure, track, and monitor them
- Map cyber risks and controls to relevant compliance frameworks.
- Understand your risk landscape through an intuitive and actionable interface
And if you are ready to start doing just this, then schedule a demo of the Scrut Automation platform now!



















