Mastering data spill management in the digital age

In an era where data serves as the lifeblood of organizations, ensuring its security is paramount. Unfortunately, the increasing interconnectedness and reliance on digital platforms expose businesses to the risk of data spills.
A data spill is a security violation or infraction that underscores the critical importance of implementing stringent measures to protect sensitive information from unauthorized access or exposure. Data spills can tarnish an organization’s reputation and result in legal liabilities, leading to a loss of trust among stakeholders and potential financial penalties.
Therefore, effective data spill management is a necessity. Establishing robust data spill management protocols, including proactive monitoring, swift incident response, and transparent communication, is key. Regularly updating and testing response plans to minimize reputational damage and legal repercussions is also essential.
This blog will delve into the intricacies of managing data spills, exploring preventive measures, response strategies, legal considerations, and the importance of building a resilient response plan.
What are data spills?
A data spill is a serious security violation or infraction that occurs when sensitive or confidential information is unintentionally exposed, compromised, or accessed by unauthorized parties. This can happen through various means, including cyberattacks, accidental data disclosures, or insider threats.
Causes of data spills
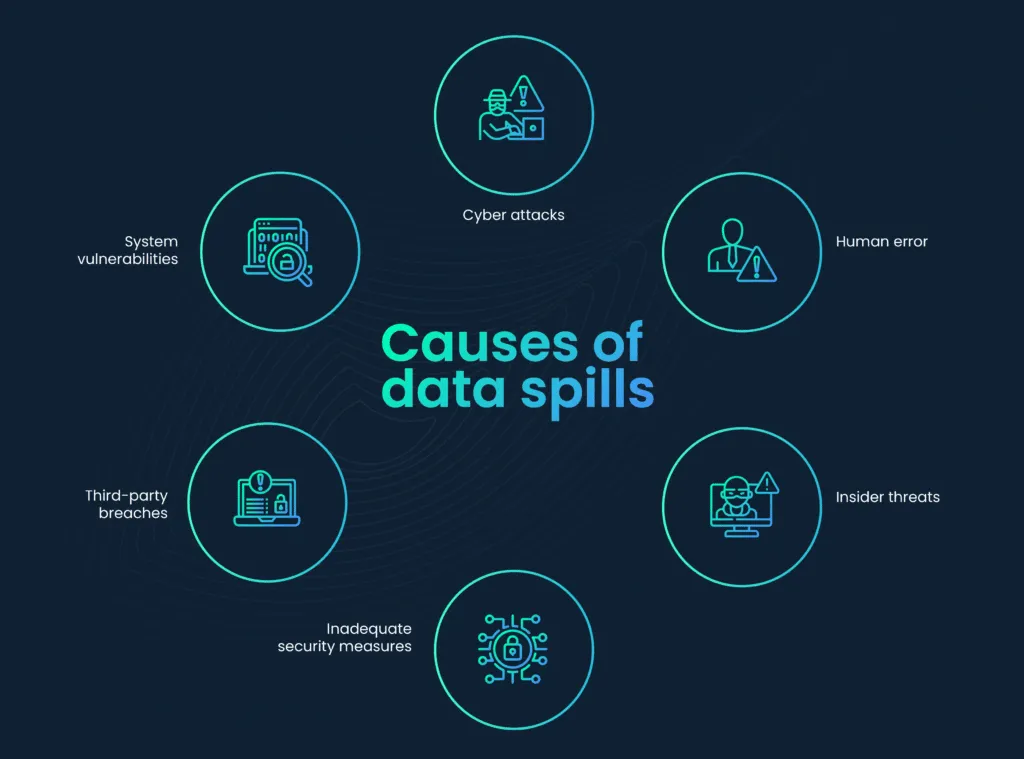
Data spills can result from a range of factors, including inadequate cybersecurity measures, human error, malicious activities, or vulnerabilities in software and systems.
Understanding the root causes is essential for developing effective strategies to prevent and manage such incidents.
- Cyber attacks: Malicious activities, including hacking and ransomware attacks, can breach security and lead to data spills.
- Human error: Accidental actions, such as misconfigurations, data mishandling, or unintended disclosures, contribute to data spills.
- Insider threats: Deliberate or unintentional actions by employees or trusted individuals can compromise sensitive data.
- Inadequate security measures: Weak cybersecurity practices, insufficient safeguards, and outdated security systems create vulnerabilities.
- Third-party breaches: Security lapses in external vendors or partners may result in unauthorized access to shared data.
- System vulnerabilities: Exploitation of software or hardware vulnerabilities can lead to unauthorized access and data spills.
Key components of data spill management
Effective data spill management involves a multifaceted approach, covering various stages from prevention to recovery. Understanding the key components of data spill management is crucial for organizations to build resilience against potential breaches.
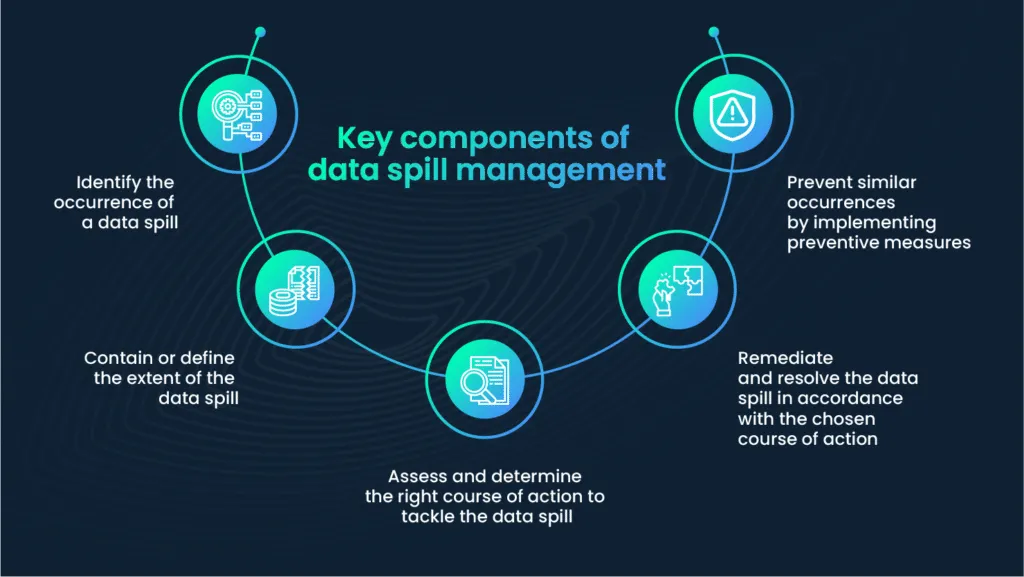
According to the ACSC’s Data Spill Management Guide, five steps are to be followed when tackling a data spill.
1. Identify the data spill
Effective identification of data spills involves both user reporting and proactive monitoring strategies.
Proactive monitoring strategies for data spill identification:
- Organizations should establish standard procedures, instructing all users to promptly notify an appropriate security contact if they suspect a data spill or unauthorized data access.
- Proactive measures include monitoring, auditing, and logging practices.
- Data loss prevention tools can help deliver user warnings and alert administrators of possible spills.
- In the event of a suspected data spill, an immediate assessment should be conducted. This assessment should involve tracking the data’s flow, movement, and storage locations, identifying affected system users (both internal and external), and determining the timeframe between the data spill occurrence and its identification.
- Implementing advanced threat detection tools and technologies aids in the early identification of unusual activities or patterns that may indicate a potential data spill. This allows for a rapid response before the incident escalates.
- Having well-defined protocols for notifying relevant stakeholders in the event of a data spill is crucial. Timely and transparent communication during and after a data spill can minimize the impact on both internal and external parties, fostering trust and accountability. Organizations should have well-thought-out communication plans for internal teams, affected customers, and the public. Transparent communication builds trust and demonstrates a commitment to addressing the incident.
- Acknowledging the incident openly, providing details about the breach without compromising security, and outlining steps taken for resolution contribute to an organization’s credibility. Transparency is key to maintaining customer and stakeholder trust.
These measures collectively enhance an organization’s ability to swiftly respond to and mitigate the impact of data spills.
2. Contain the spill
Containing a data spill is a critical and time-sensitive process that involves isolating and mitigating the impact of the incident.
The containment phase acts as a crucial barrier, aiming to restrict the spill’s reach and mitigate potential damage before moving on to the assessment and remediation stages.
- Swift identification of the spill’s source and affected areas.
- Upon detection, organizations should have predefined rapid response strategies to contain the spill and prevent further unauthorized access. Swift action helps minimize the extent of the breach and limits potential damage. For instance, around October 25, 2023, Redcliffe Labs faced a breach exposing 12.3 million medical records stored in a non-password-protected database. The company responded promptly by restricting public access, though the extent of potential data exfiltration remains uncertain.
- Physically isolate affected systems or logically separate them from the network.
- Restrict user access to certain directories, restrict user permissions.
- Implementing mitigation measures involves addressing the root causes of the data spill and taking steps to rectify vulnerabilities. This may include patching system weaknesses, updating security protocols, and fortifying access controls.
In cases of data spills involving electronic communication, such as internal emails, containment actions may extend to identifying the sender and recipients and instructing them not to forward or access the compromised data.
Additionally, organizations may evaluate the necessity of retaining a copy for damage assessment and verification by data owners while promptly deleting the compromised content from affected users’ inboxes to prevent further dissemination.
3. Assess and determine a course of action
After successfully containing a data spill, a comprehensive assessment becomes imperative to prevent further access and exposure of compromised information.
Components of assessment of a data spill
- Identification of affected system users, systems, and devices.
- A thorough examination of devices such as workstations, backup storage, printers, print servers, network shares, email inboxes and servers, content filtering appliances, webmail, and external systems.
- Collaboration with system and network administrators to ensure a meticulous evaluation.
- Prompt notification of the data spill to contact data owners and relevant authorities. Data owners play a pivotal role in providing guidance on specific handling requirements for the compromised data, contributing to the minimization of its exposure.
- Performing a damage assessment. Organizations need to assume that the spilled data is compromised and conduct a comprehensive evaluation of the harm caused by the data spill. This assessment serves as the foundation for developing remediation procedures and implementing risk management strategies, with organizations basing their responses on a worst-case scenario to effectively address the aftermath of the data spill.
4. Remediate
Organizations must work with data owners to determine satisfactory remediation for a data spill. They can achieve remediation through a balance of technical controls and risk management activities.
For each system identified in the assessment stage, develop a comprehensive remediation strategy.
Developing remediation strategy for data spills
- Assess and adjust access controls for data and system security.
- Monitor memory storage utilization, ensuring natural overwriting capability.
- Determine the system’s criticality to business operations.
- Evaluate the exposure duration of compromised data.
- Choose appropriate sanitization methods for the media.
- Consider disposal options for the asset, including resale or physical destruction.
- Balance the risk of data attention versus accepting damage.
- Assess resources, impacts, and financial costs for system replacement or sanitization.
5. Prevent data spillage
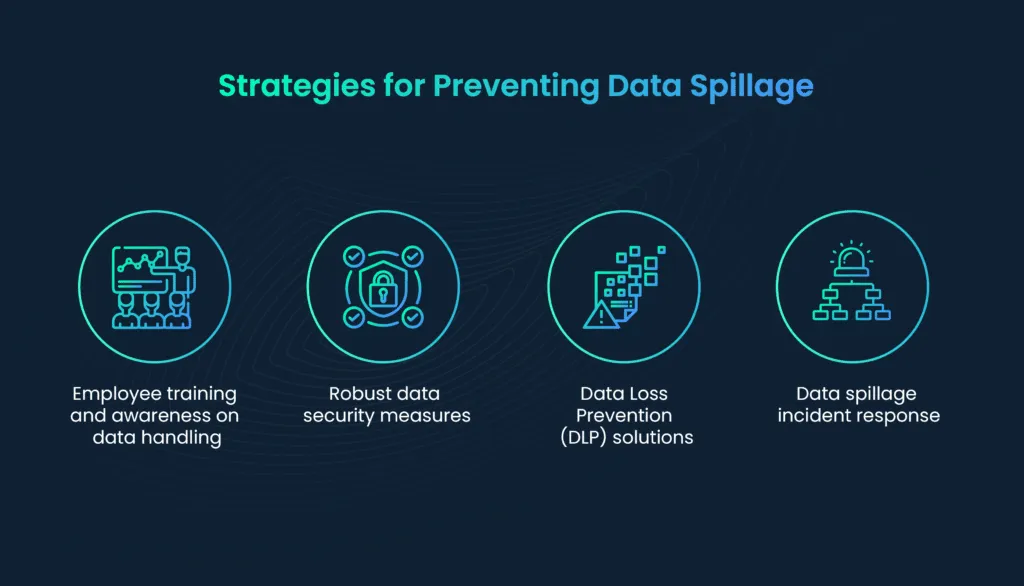
Data spillage is closely connected to cybersecurity, as it often results from vulnerabilities in an organization’s security infrastructure.
Cybersecurity measures, such as firewalls, intrusion detection systems, and endpoint security solutions, play a critical role in preventing unauthorized access and data spillage.
Regular security assessments and threat intelligence monitoring can help organizations stay ahead of evolving cyber threats.
a. Employee training and awareness on data handling
Human error is a common factor in data spills. One of the most effective ways to prevent data spillage is through employee training and awareness programs.
Educating your workforce about the importance of data security, the risks associated with data spillage, and best practices for handling sensitive information is paramount. This includes comprehensive training on recognizing phishing attempts, verifying the identity of email recipients, and understanding the proper procedures for handling confidential data.
By fostering a culture of security awareness, organizations can empower their employees with employee awareness programs, like those offered by Scrut, to be proactive in preventing data spillage incidents.
b. Robust data security measures
Implementing robust data security measures is essential for safeguarding sensitive information.
Enforcing stringent access controls, and enabling authentication mechanisms help safeguard information from unauthorized access. This ensures that even if a data spill occurs, the exposed information remains indecipherable to malicious actors.
Organizations should classify their data based on its sensitivity and restrict access to authorized personnel only.
Proactive measures, such as conducting regular security audits and vulnerability assessments, enable organizations to identify and address potential weaknesses in their systems. This ongoing evaluation helps preemptively close security gaps before they can be exploited.
c. Data Loss Prevention (DLP) solutions
Data Loss Prevention (DLP) solutions are powerful tools in the fight against data spillage. DLP software can monitor and protect sensitive data by scanning for keywords, patterns, and file types that match predefined criteria.
When it detects an attempt to move, copy, or transmit sensitive data, it can take actions such as blocking the transfer, alerting administrators, or applying encryption. DLP solutions offer an additional layer of protection to prevent data spillage incidents.
d. Data spillage incident response
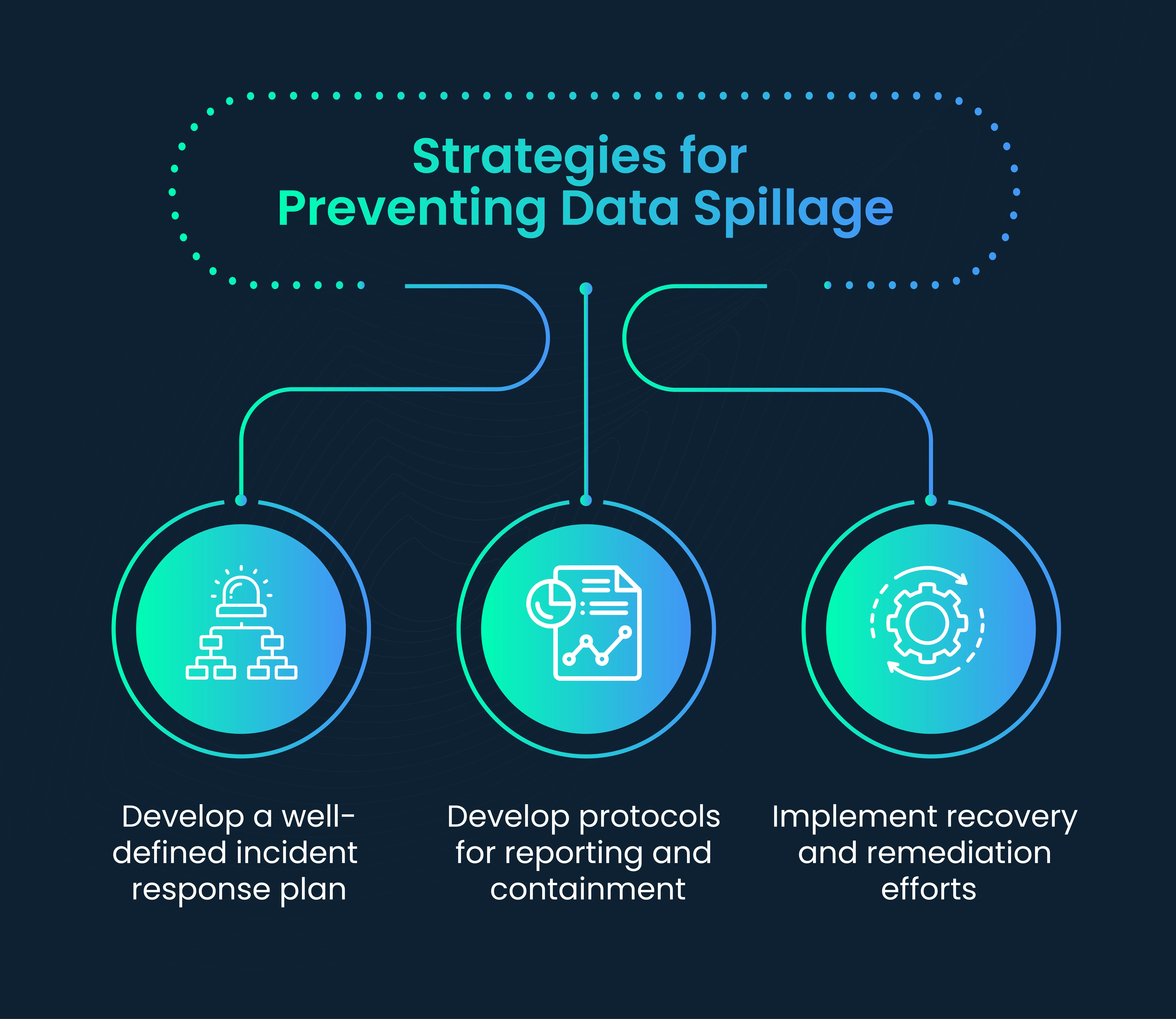
Incident response is essential even with a prevention plan in place, as no prevention strategy is foolproof. New threats and vulnerabilities can emerge, and human errors can still occur.
Incident response ensures quick detection and effective mitigation, reducing potential damage and minimizing downtime while allowing organizations to adapt to evolving security challenges.
1. Develop a well-defined incident response plan
Preparation is key to effectively responding to data spillage incidents. Organizations should have a well-defined incident response plan in place. This plan outlines the steps to be taken when a data spillage incident occurs.
It should identify key personnel responsible for incident response, the processes for containment and recovery, and communication strategies for notifying affected parties.
2. Develop protocols for reporting and containment
When a data spillage incident is identified, it’s critical to report it promptly. Quick action can help limit the damage and potential consequences.
Organizations should have protocols in place for containing the incident, isolating affected systems, and preserving evidence for investigation. Effective containment can prevent the further spread of sensitive data.
3. Implement recovery and remediation efforts
Recovery efforts following a data spillage incident involve restoring affected systems and data to their pre-incident state. This may include restoring data from backups, implementing security patches to address vulnerabilities, and improving security measures to prevent similar incidents in the future.
Post-incident remediation efforts should also focus on addressing the root causes of the incident and implementing safeguards to reduce the risk of recurrence.
High-profile data spill incidents in 2023
Several organizations have faced the brunt of data spills, leading to significant consequences. Learning from these examples can provide insights into potential vulnerabilities and the impact of insufficient data spill response strategies.
- Kid Security: The Kid Security parental control app, designed to monitor children’s online safety, inadvertently exposed over 300 million records through misconfigured Elasticsearch and Logstash instances for over a month. Discovered by security researcher Bob Diachenko, the compromised data included 21,000 phone numbers, 31,000 email addresses, and some exposed payment card information. The breach led to unauthorized access, with the Readme bot injecting a ransom note into the open instance.
- TmaxSoft: South Korean IT company TmaxSoft exposed over 56 million records via a Kibana dashboard for more than two years. The leaked data included company information, emails, employee details, and attachments, posing a risk for potential supply chain attacks.
- DarkBeam: DarkBeam, a digital risk protection firm, left Elasticsearch and Kibana interfaces unprotected, revealing 3.8 billion records with user emails and passwords. While most data originated from previous breaches, the organized information raises concerns about potential phishing campaigns.
- MOVEit Breach: The MOVEit breach, initiated by the Cl0p gang exploiting a zero-day SQL injection in MOVEit Transfer, persists with over 1,000 affected organizations and 60 million individuals. Notable victims include Maximus, TIAA, Pôle emploi, Oregon and Louisiana DMVs, Genworth Financial, Wilton Reassurance, and the University of Minnesota, underscoring the widespread repercussions.
- UK Electoral Commission: A “complex cyber-attack” on the UK Electoral Commission compromised personal information of around 40 million people. While the attack was initially labeled complex, a whistleblower suggested a Cyber Essentials audit failure, raising questions about the Commission’s cybersecurity.
- Indonesian Immigration: Hacktivist “Bjorka” accessed Indonesia’s Immigration Directorate General, leaking passport data of 34 million citizens on the dark web for $10,000.
Legal and regulatory considerations of data spills
Navigating the aftermath of a data spill involves not only technical measures but also a keen understanding of the legal and regulatory landscape.
Organizations must be aware of the implications and responsibilities associated with data breaches to ensure compliance and minimize legal consequences.
Legal implications: Data spills often trigger legal ramifications, with potential consequences ranging from fines and legal action to damage to an organization’s reputation. Understanding the legal implications specific to the jurisdiction in which the organization operates is critical.
Regulatory requirements: Various regulatory bodies enforce data protection laws and standards. Compliance with regulations such as GDPR, HIPAA, or other industry-specific standards is not only mandatory but also essential for maintaining trust among customers and stakeholders.
Importance of compliance and cooperation: Organizations should prioritize compliance with data protection laws and cooperate with regulatory bodies during investigations. Proactive measures to adhere to legal requirements demonstrate a commitment to data security and can mitigate potential penalties.
Data spills can have longstanding consequences. For example, the personal information of 2.2 million Pakistani citizens, including credit card details, was offered for sale on the dark web in 2023. The data breach resulted from hackers accessing a database used by over 250 restaurants, with conflicting analyses suggesting a 2022 leak.
Data recovery and restoration after a data spill
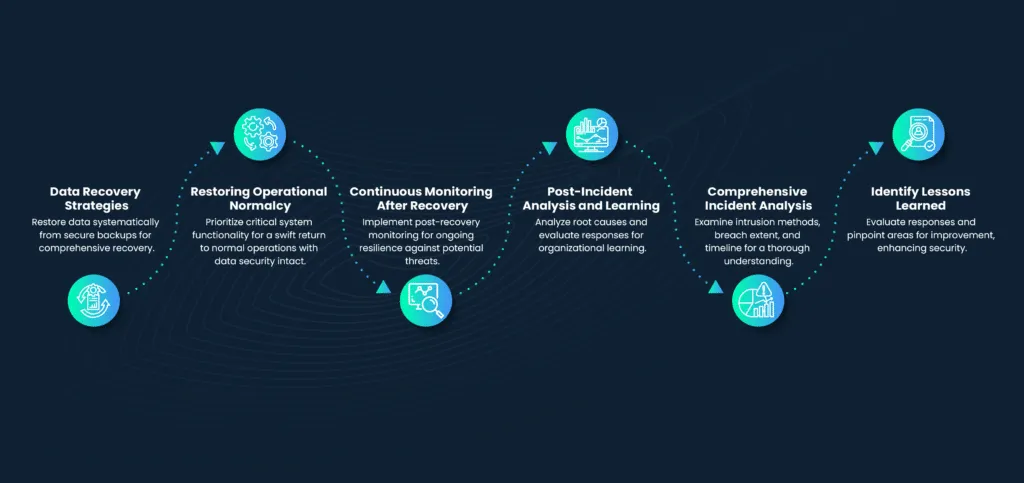
Recovering from a data spill involves not only addressing the immediate incident but also implementing measures to restore normalcy and prevent future occurrences.
- Strategies for data recovery: Recovering lost or compromised data requires a systematic approach. Organizations should have backup and recovery strategies in place to restore data to its pre-incident state. This involves deploying backups from secure and unaffected sources.
- Restoring normal operations: After the immediate impact is addressed, organizations need to focus on restoring normal operations. This includes ensuring that critical systems are functioning, and employees can resume their regular activities without compromising data security.
- Continuous monitoring post-recovery: Post-recovery, it is crucial to implement continuous monitoring to detect any residual threats or potential weaknesses in the systems. This ongoing vigilance helps organizations stay resilient against future incidents.
- Post-incident analysis and learning: Following a data spill incident, conducting a thorough analysis is crucial for organizations to understand the root causes, evaluate the effectiveness of their response, and derive valuable insights for future improvements.
- Thorough incident analysis: Organizations should perform a comprehensive analysis of the data spill incident, examining the timeline, methods of intrusion, and the extent of the breach. This analysis helps in understanding the vulnerabilities that were exploited and areas where the response could be enhanced.
- Identifying lessons learned: The post-incident analysis is an opportunity to identify lessons learned. What worked well during the response, and where were the gaps? Evaluating the effectiveness of implemented measures and identifying areas for improvement contribute to a more resilient security posture.
Building a Resilient Data Spill Response Plan
To effectively manage data spills, organizations must have a well-defined response plan that outlines clear steps for prevention, detection, response, and recovery. This plan serves as a roadmap to minimize the impact of data spills and ensure a swift and coordinated response.
- A resilient data spill response plan should be dynamic, evolving with the organization’s changing infrastructure and threat landscape.
- Regular updates ensure that the plan remains relevant and effective against emerging threats.
- Regular drills and simulations are invaluable in testing the effectiveness of the response plan.
- Conducting mock data spill scenarios helps teams understand their roles, identify potential bottlenecks, and refine their response strategies in a controlled environment.
Wrapping up
Effectively managing data spills is an ongoing commitment that requires a combination of proactive prevention, swift response, and continuous learning. Organizations must recognize that in today’s digital arena, the question is not whether a data spill will occur, but when.
By implementing key components such as prevention strategies, early detection, transparent communication, and a resilient response plan, organizations can navigate data spills with resilience.
In conclusion, the journey to robust data spill management involves a holistic approach, learning from experiences, and embracing a culture of continuous improvement.
By prioritizing data security and leveraging insights from real-world case studies, organizations can strengthen their defenses and safeguard sensitive information in an ever-evolving cybersecurity landscape. Scrut can help you in your journey to data protection. To learn more, get in touch today!
Frequently Asked Questions
1. What is the primary cause of data spills, and how can organizations prevent them?
Data spills often result from cyberattacks, human error, or system vulnerabilities. Prevention involves robust cybersecurity measures, employee training, and regular system audits.
2. In the event of a data spill, what immediate steps should a company take to minimize damage?
Swift response is crucial. Isolate affected systems, notify relevant parties, and implement incident response plans. Cooperation with cybersecurity experts aids in containment and recovery efforts.
3. Are there specific industries more prone to data spills, and if so, why?
Highly regulated industries like healthcare and finance are often targeted due to the value of their data. However, any sector can face risks, emphasizing the need for universal data spill preparedness.
4. How can encryption technologies contribute to data spill prevention and management?
Encryption safeguards sensitive information, rendering it unreadable to unauthorized individuals. Implementing robust encryption protocols adds an extra layer of protection and minimizes the impact of a spill.
5. What legal obligations does a company have in disclosing a data spill to affected parties?
Legal obligations vary, but transparency is crucial. Many jurisdictions mandate prompt and clear communication with affected parties, helping build trust and demonstrating commitment to data protection.


















