Aquasec Alternatives

Aqua is a Cloud Native Application Protection Platform (CNAPP) which safeguards the application lifecycle from development to the cloud. Although it is good, it may not be the best option for everyone. Its limitations include the platform’s user interface having several issues, particularly with the sign-up/sign-in process, alerts, authentication, and results.
Aqua provides complete visibility into your multi-cloud environment, allowing you to identify and correct misconfigurations and other risks that leave you exposed. If you’re looking for Aquasec alternatives, this article will be useful. To help you save time, we’ve compiled a list of the top 8 Aquasec alternatives. Before considering the alternatives, look at Aquasec’s key features and disadvantages.
Key Features
The key features of the platform are listed below:
- The Aqua platform safeguards cloud-native applications by reducing their attack surface and detecting vulnerabilities, embedded secrets, and other security issues during the development cycle.
- The platform prevents security risks from becoming security incidents by detecting and remediating vulnerabilities, malware, exposed secrets, and other risks in your code, build tools, and delivery pipelines.
- It enables seamless team collaboration, eliminates cloud-native blind spots, and prevents successful attacks by utilizing a single source of truth throughout the entire software development lifecycle.
- Aqua automates security testing in your CI/CD pipeline and continuously scans registries and serverless function stores for emerging threats.
- The tool focuses on the most critical vulnerabilities to prioritize those that pose the most significant risk to your environment based on the workloads you run, the availability of exploits in the wild, and the level of exploitability.
Drawbacks
The platform has some drawbacks, such as:
- It may take them some time to explain or resolve issues.
- Aqua’s user interface has several issues, particularly with the sign-up/sign-in process, alerts, authentication, and results.
- The platform lacks prominent alert notification channels, such as Datadog and Webhooks.
- It takes time to integrate it with platforms.
- High traffic loads require restarting gateways.
- DaemonSet Enforcer taking control of the docker sock on compute nodes puts production runtime at risk.
8 Best Aquasec Alternatives
Let’s discuss eight alternatives to Aquasec, starting with our platform, Scrut.
1. Scrut
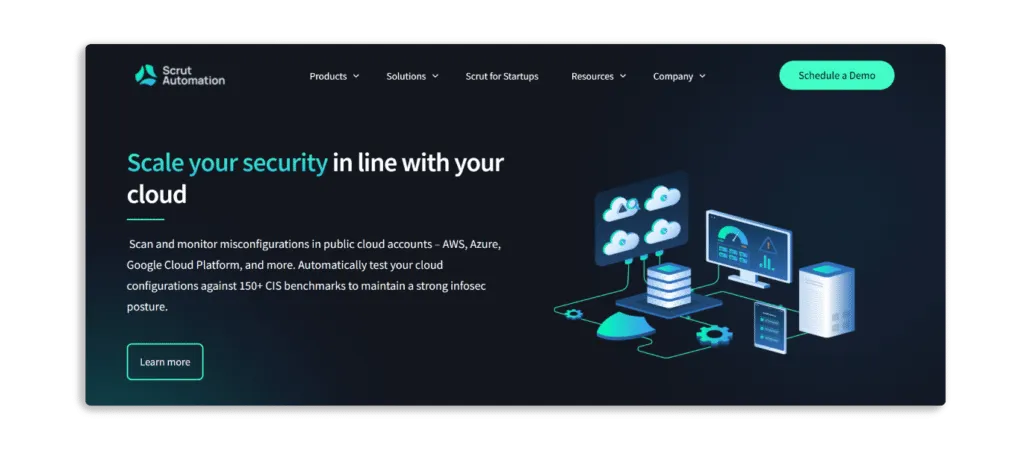
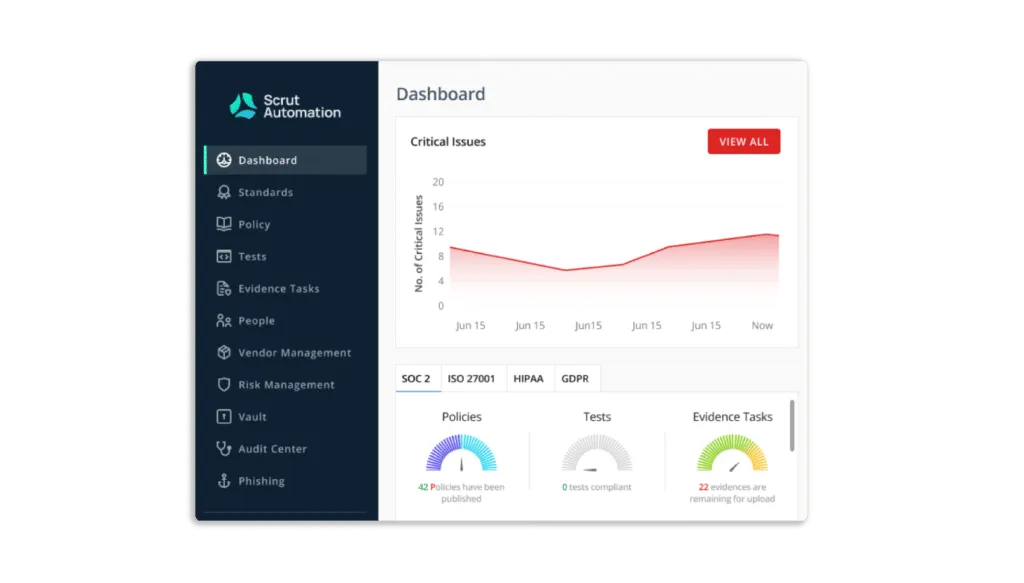
Scrut Cloud Security can be integrated with your cloud accounts – AWS, Azure, GCP, and others – in less than 10 minutes using pre-built integrations.
The platform displays the status of all cloud resources, and if any cloud resource fails to meet your security standards, you will see one of the following statuses:
- Danger – The most critical issues that must be addressed immediately.
- Warning – After dealing with the “danger” issues, you can proceed to these.
- Low – These are low-level risks that can be addressed later.
- Ignored – Everything is fine as long as you are compliant.
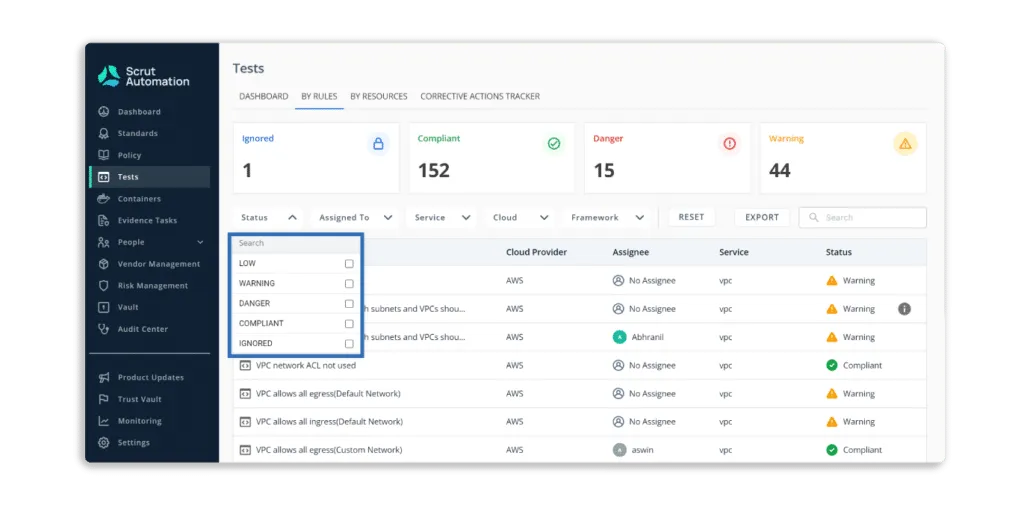
Pros
- Scrut Cloud Security ensures that your public cloud accounts are always secure and compliant. It sends you alerts with actionable recommendations for correcting misconfigurations.
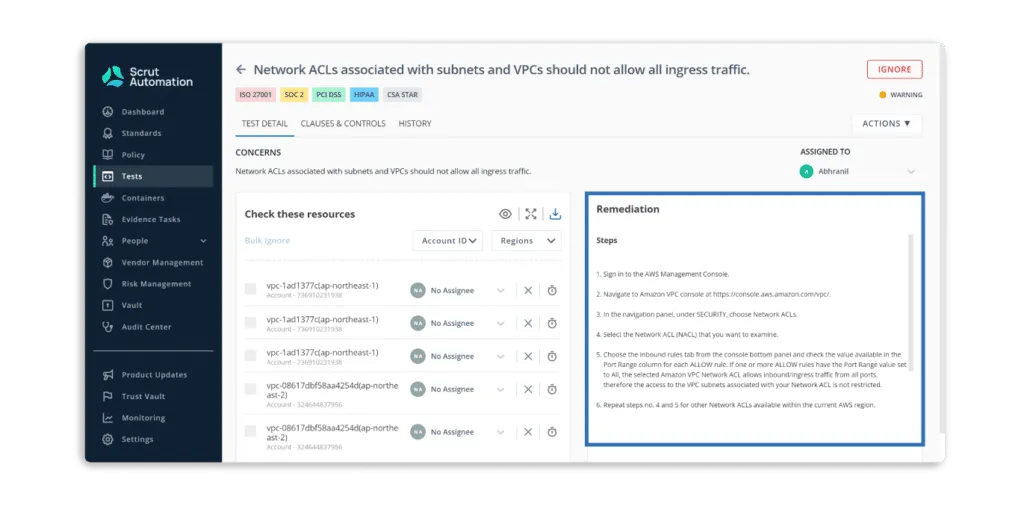
Furthermore, you can assign tasks to team members to fix misconfigurations.
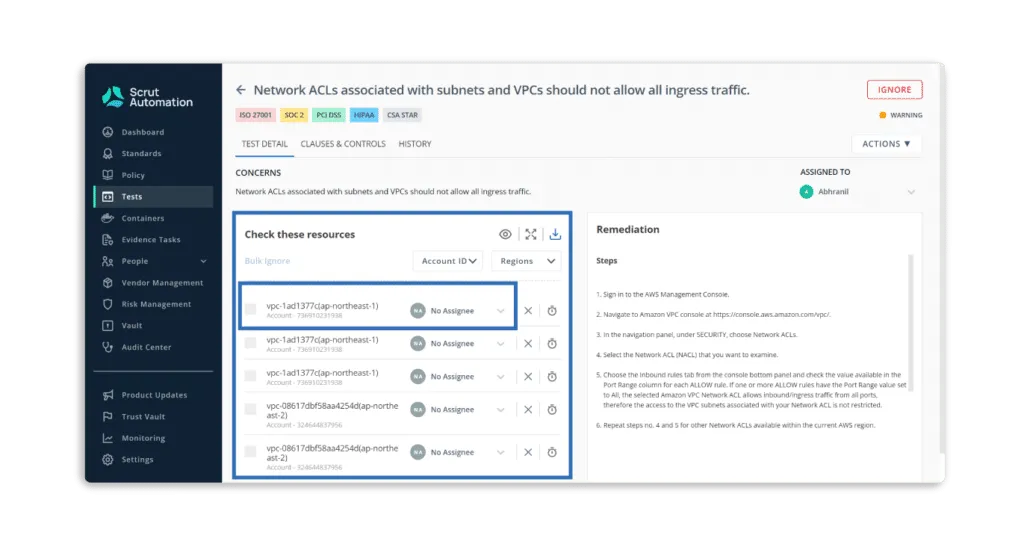
- Scrut Cloud Security enables you to implement best-practice security policies consistently across your hybrid and multi-cloud infrastructure to establish full-stack security for all your cloud-native deployments, including virtual machines (VMs), containers, and serverless.
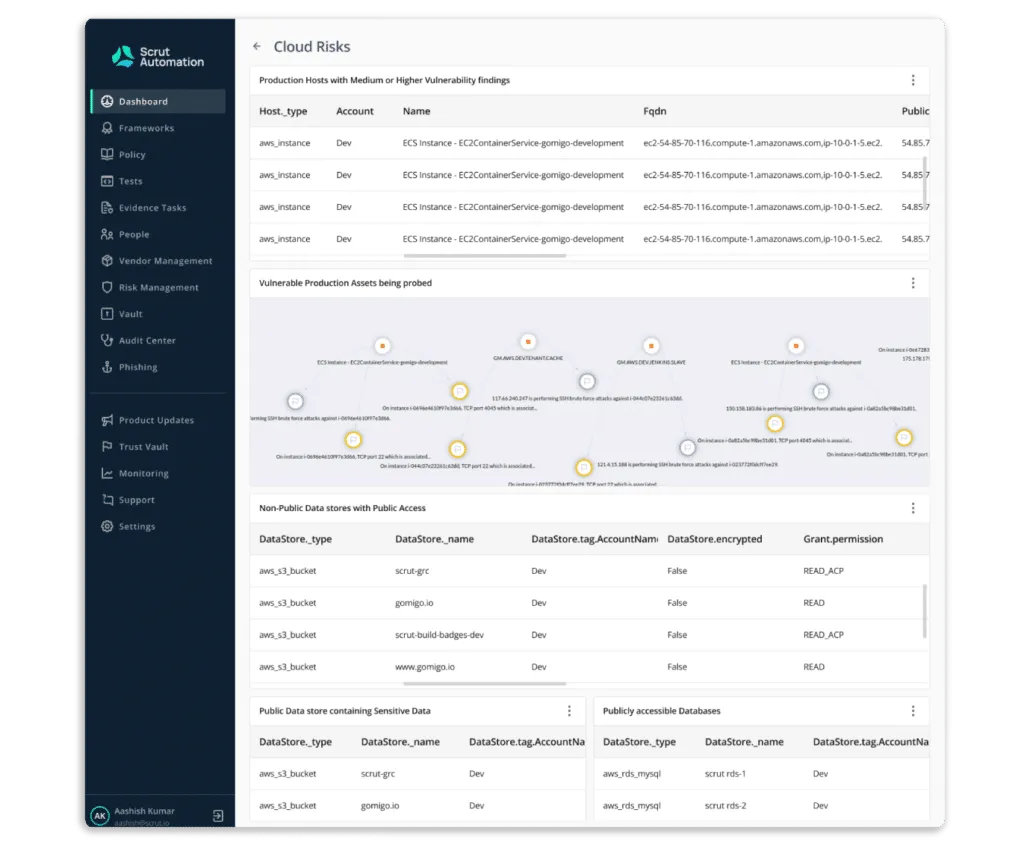
- It provides the visibility required to understand your information security activities’ status, efficacy, and impact on your compliance posture. The tool offers a centralized repository for all information security tasks and artefacts, allowing you to close compliance gaps in real time and stay compliant 24*7.
- The platform automatically compares your cloud configurations to 200+ cloud control across CIS benchmarks to ensure a strong information security posture.
Customer Rating
- G2- 5/5
2. Prisma Cloud
Prisma Cloud is the Cloud Native Application Protection Platform (CNAPP), providing security and compliance coverage for infrastructure, workloads, and applications across the entire cloud-native technology stack and hybrid and multi-cloud environments. It simplifies compliance while reducing the difficulty of safeguarding multi-cloud setups. The platform provides complete control and insight over the security posture of each deployed resource. Furthermore, it automatically corrects common configuration errors before they cause security incidents.
Pros
- Prisma supports multiple cloud environments.
- Prisma cloud secures applications through threat prevention, which can protect against newly generated malware and threats.
Cons
- The platform has a variety of interfaces, policies, and approaches, making it difficult to understand.
- There is a lack of visibility into system resources.
- The platform is not sufficiently automated and requires numerous manual processes.
Customer Rating
- G2- 4.3/5
3. JupiterOne
JupiterOne unifies and standardizes asset data across your complex multi-cloud environments. It collects identity, code, security, endpoint, infrastructure, and ephemeral asset data and maps their relationships to create a complete picture of your digital environment. The tool provides comprehensive protection for all of your cloud entities. It connects the dots between assets, users, endpoints, code repositories, and more to give your teams with a complete picture of their environments. Furthermore, it creates and classifies resource entries automatically to continuously assess, audit, and evaluate the configurations of your cloud resources.
Pros
- It provides continuous instrumentation and monitoring of cloud environments and controls.
- The platform makes it easy for users to integrate evidence for SOC, HIPAA, GDPR, and other compliance assessments.
Cons
- Understanding the tools’ overall potential requires a steep learning curve.
Customer Rating
- G2- 5/5
4. Sysdig Secure
Sysdig Secure is a cloud and container security platform that supports multi-cloud environments and addresses risk across all your cloud accounts and deployments. Teams can use the Sysdig Secure platform to secure builds, detect and respond to runtime threats, and manage real-time cloud configurations, permissions, and compliance.
Pros
- The new risk spotlight feature allows users to focus on real and imminent risks.
- The platform allows for flexible policy configuration.
Cons
- Navigating the UI can be difficult at times.
- Not fully covered report API v2.
Customer Rating
- G2- 4.8/5
5. CloudGuard
CloudGuard Cloud Security Posture Management automates governance across multi-cloud assets and services, detecting configuration errors and enforcing security best practices and compliance standards. It offers cloud security and compliance posture management for cloud-native environments, including Amazon, Azure, Google Cloud, Alibaba Cloud, and Kubernetes. The tool enforces gold standard policies across accounts, projects, regions, and virtual networks while visualizing security posture. It applies runtime CI/CD remediation in place and active security enforcement.
Pros
- The platform lets you see your cloud workloads and services in detail.
- Flexible enough to deploy everything from large centralized data centres to IoT/OT devices to local branches.
Cons
- The cloud guard console makes it difficult to monitor traffic and threats.
- The platform does not offer policy recommendations that help users to delete unused objects.
Customer Rating
- G2- 4.5/5
6. Wiz
Wiz connects to your cloud environment and provides complete visibility and actionable context on your most critical misconfigurations, allowing your teams to improve your cloud security posture proactively and continuously. You can prioritize misconfigurations using the Wiz Security Graph based on operational, business, cloud, and data context. For instance, you can disregard resources that a cloud service or empty VPCs control. Furthermore, it evaluates your compliance posture against over 35 built-in compliance frameworks, including CIS Azure/GCP/AWS/OCI/ESXi, NIST CFS/SP/800-171/800-53, PCI DSS, SOC2, HiTrust, and others.
Pros
- The platform prioritized alerts based on context.
- The platform’s threat centre makes it easy to see which resources require attention.
Cons
- The Wiz platform does not support the custom report templates feature.
- The status of container discoveries is not automatically updated to resolved.
Customer Rating
- G2- 4.7/5
7. Lacework
Lacework discovers, monitors, and inventories all assets in your cloud environment. It records daily inventory to understand changes over time, even if assets are no longer available. The tool evaluates your security posture and compliance with hundreds of pre-built policies for standards such as PCI, HIPAA, NIST, SOC 2, and others. It automatically monitors and detects misconfigurations and suspicious cloud activity.
Pros
- Lacework provides extensive coverage for a wide range of cloud workloads (including containers, Kubernetes, AWS, and Azure), allowing the organization to secure the entire cloud environment with a single platform.
- It easily provides the information required to assess risks and develop a mitigation plan.
Cons
- Due to the underlying approach, detections can take up to an hour.
- Slack notifications occasionally stopped being linked to events.
Customer Rating
- G2- 4.5/5
8. Scribe Security
Scribe collectors work with your software pipelines to generate attestation of the integrity and provenance of built artefacts and a software bill of materials. The data is analyzed and managed in the Scribe platform, where it can be shared with stakeholders. For each build, the platform analyzes gaps and defines security policies across your CI/CD pipelines.


















