
If compliance is just about checklists for you, you’re missing the bigger picture. It’s about security, efficiency, and trust, and Scrut helps us achieve all three. Scrut has become a crucial part of our security stack.
Run your AI-powered, security-first GRC program with Scrut Teammates.

%201.avif)


























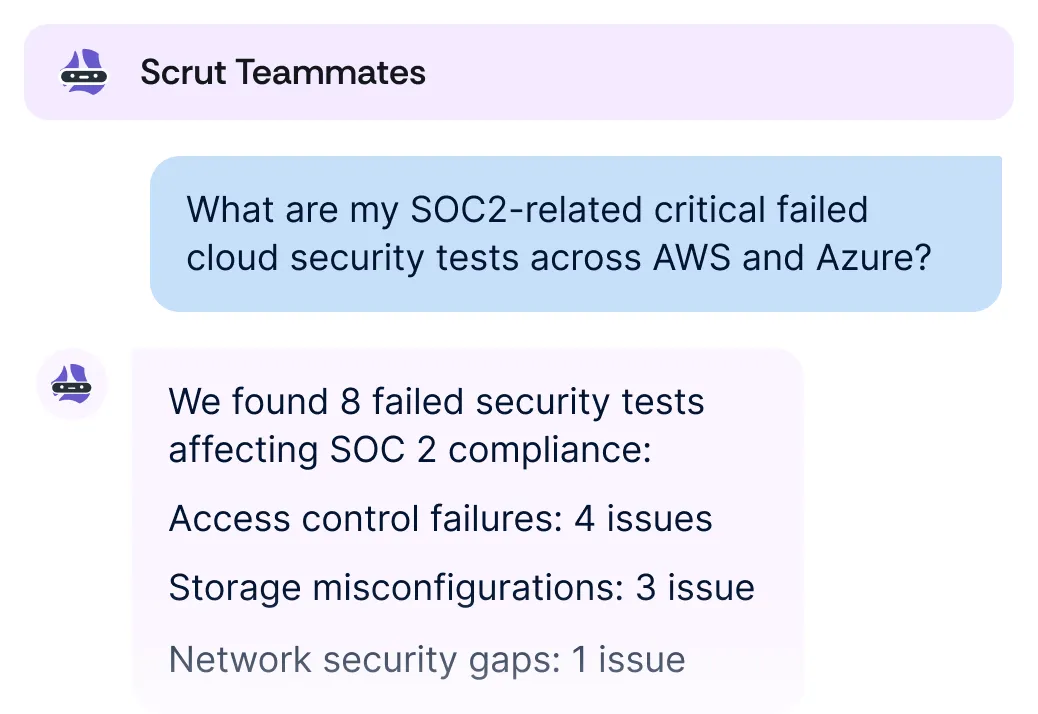





.webp)
Don’t stay limited to surface-level protection that stops at endpoints and IP addresses. Get insights across all cloud infrastructure, applications, people, and third party risks.
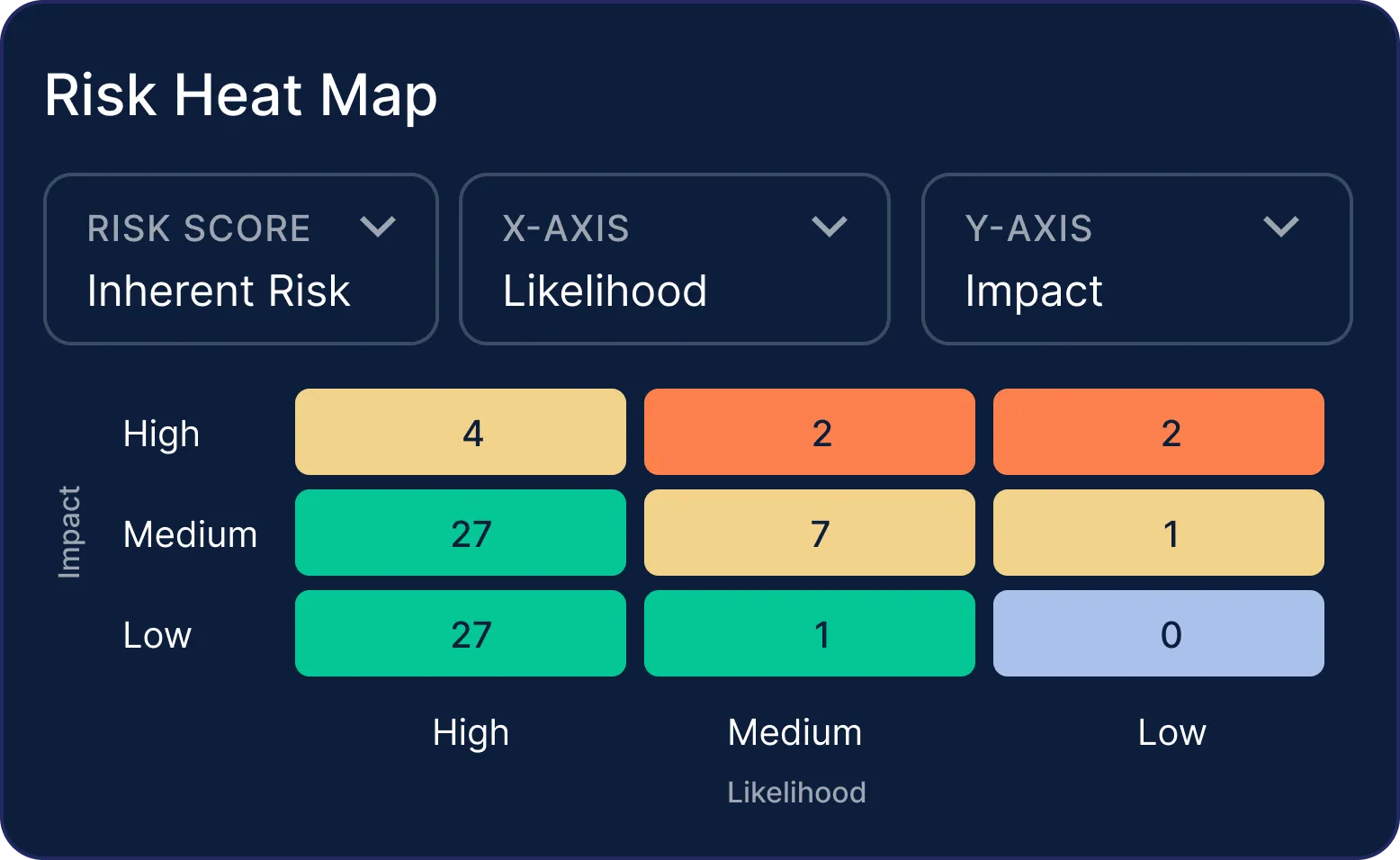
Map controls across all your security initiatives, tie risks to mitigating controls, and cut out redundancy by reusing controls as you scale.

Automate control monitoring, evidence collection, and set up recurring workflows for routine tasks. Connect Scrut to your favourite task management tools and get instant alerts on risk mitigation tasks that need your attention.
.webp)
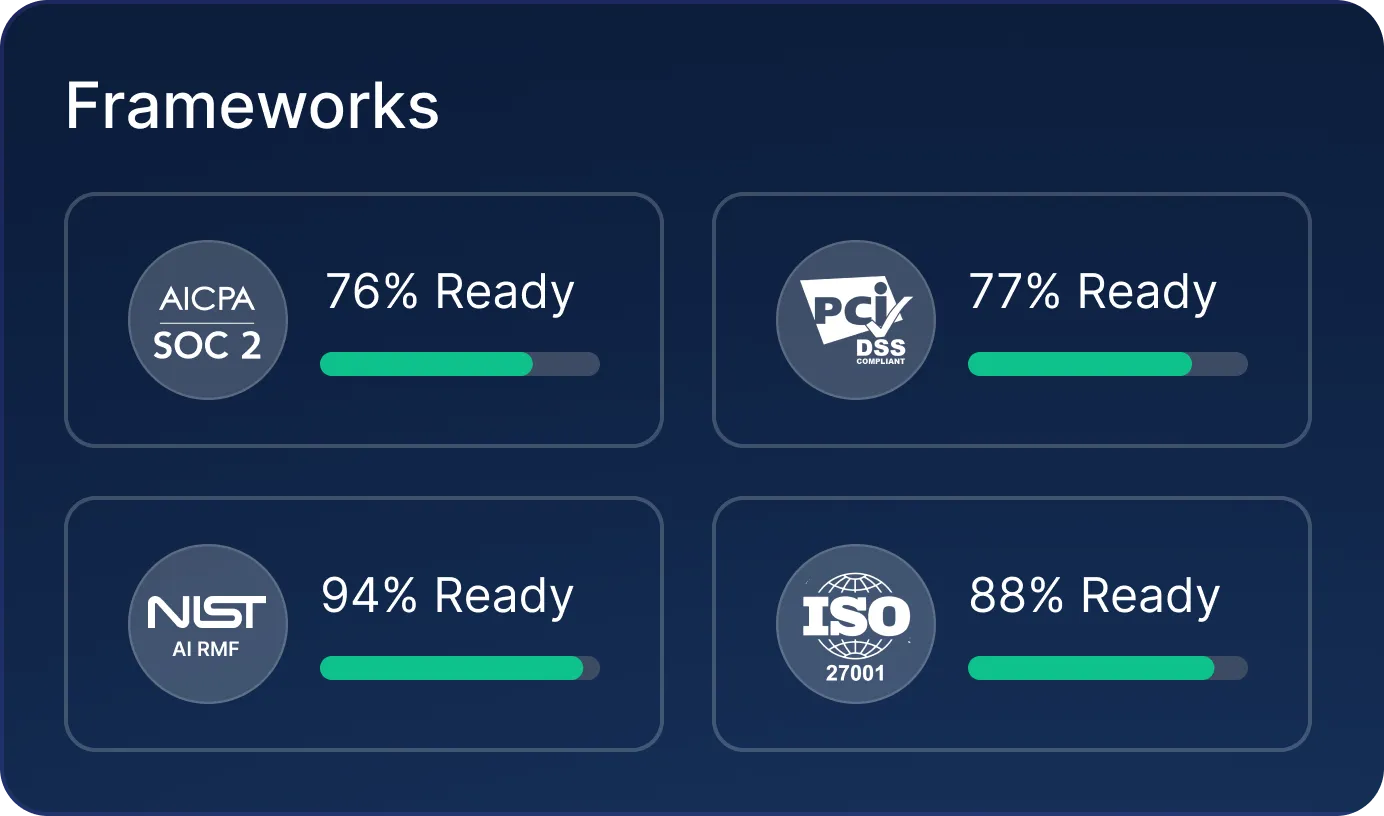
Track your compliance status against every framework under the sun (or build a custom one, it’s your show). When it’s audit time, breeze through both internal and external reviews with confidence. No panic, no surprises.



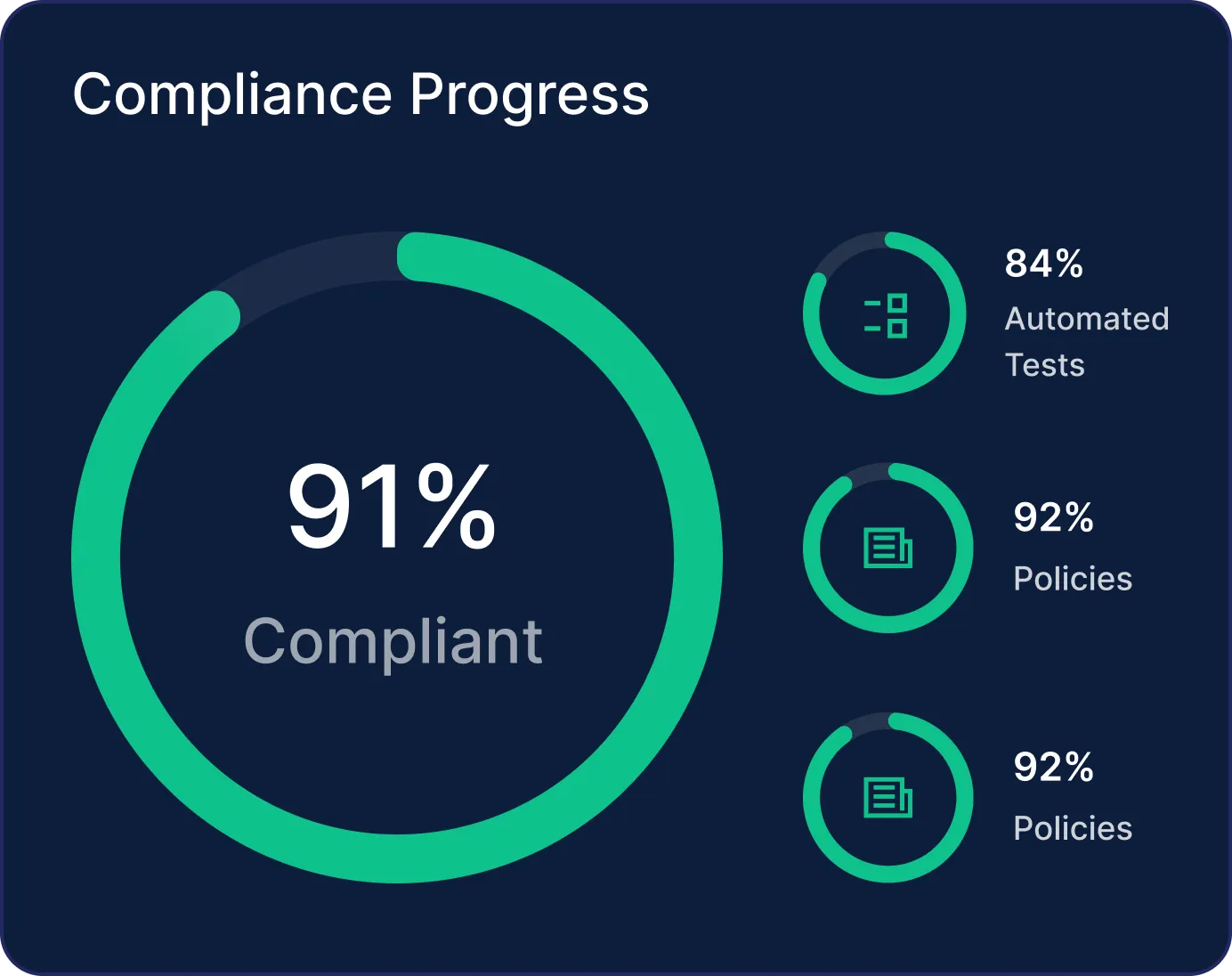
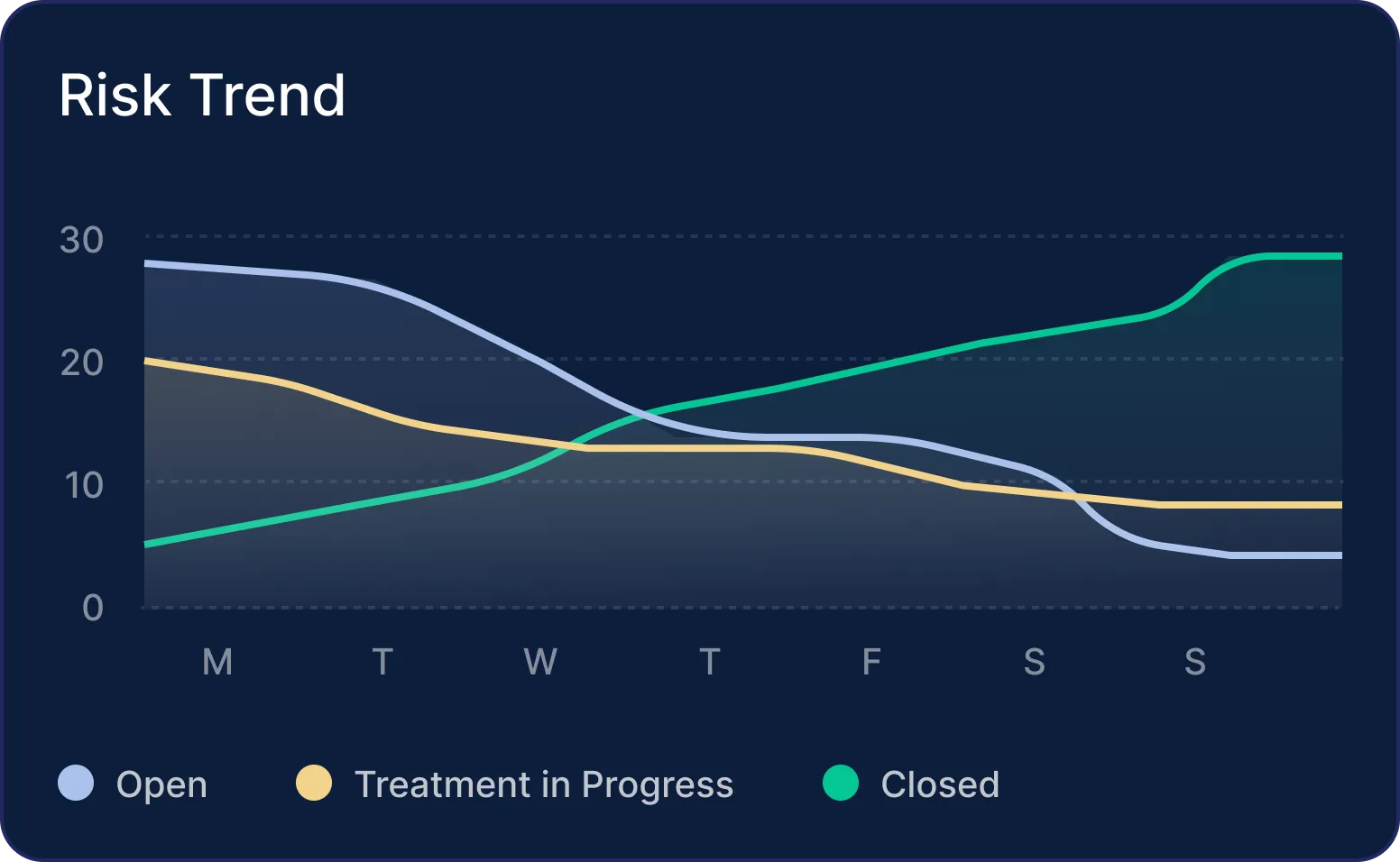
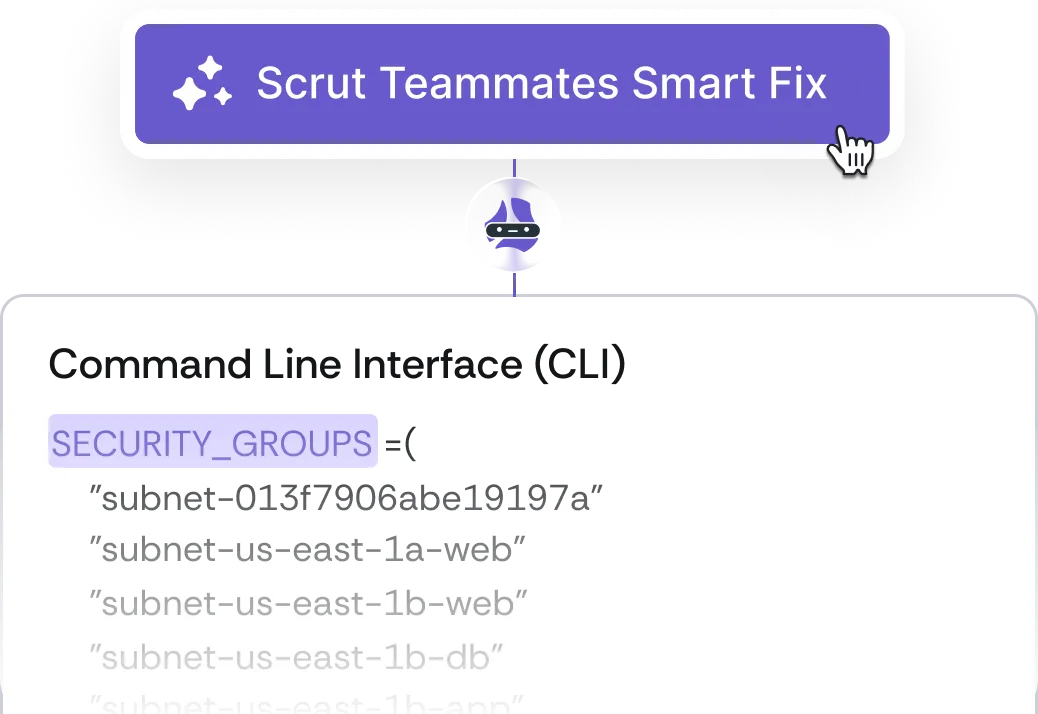
Let Scrut evaluate the effectiveness of your controls 24/7, non-stop. Get notified of gaps and share step-by-step remediation guidelines, right in your task management tools.
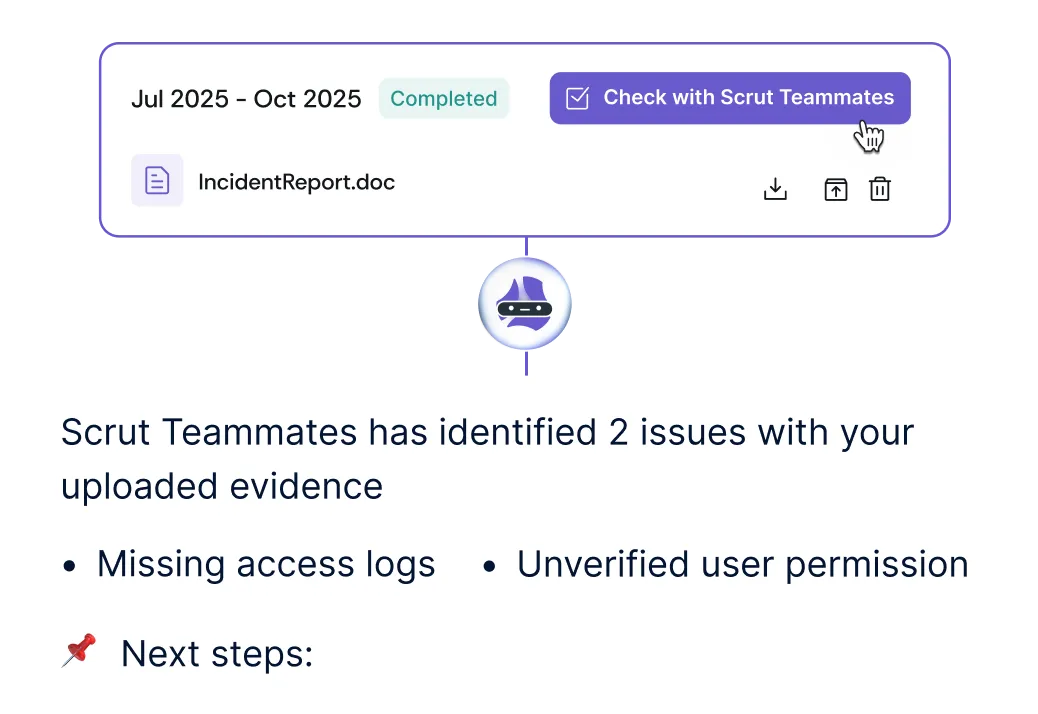
Collect evidence on the way, and so that you never have to hunt down documents for audits


Configure workflows, create custom frameworks and controls, trigger custom tests, and build custom risk formulas for tailored risk assessment.
Build a security program that’s as unique as your business, directly from the interface.


Start with complete coverage: compliance frameworks, policy templates, risk registers, and vendor questionnaires, all pre-mapped to unified controls, so you don’t waste time starting from scratch or duplicating work.


From a Setup Wizard that tracks your progress, to Scrut Teammates that decode control choices in real time, to hands-on support from our InfoSec team; you're never on your own.
Whether it’s onboarding, audit prep, or tightening your risk posture, we get you there faster and smarter.


Let Scrut evaluate the effectiveness of your controls 24/7, non-stop. Get notified of gaps and share step-by-step remediation guidelines, right in your task management tools.
Collect evidence on the way, and so that you never have to hunt down documents for audits

Configure workflows, create custom frameworks and controls, trigger custom tests, and build custom risk formulas for tailored risk assessment.
Build a security program that’s as unique as your business, directly from the interface.

Start with complete coverage: compliance frameworks, policy templates, risk registers, and vendor questionnaires, all pre-mapped to unified controls, so you don’t waste time starting from scratch or duplicating work.

From a Setup Wizard that tracks your progress, to Scrut Teammates that decode control choices in real time, to hands-on support from our InfoSec team; you're never on your own.
Whether it’s onboarding, audit prep, or tightening your risk posture, we get you there faster and smarter.




If compliance is just about checklists for you, you’re missing the bigger picture. It’s about security, efficiency, and trust, and Scrut helps us achieve all three. Scrut has become a crucial part of our security stack.



Working with Scrut to get ISO 27001 and SOC 2 compliant was such a relief. Their platform helped us spot gaps in our security posture, and strengthen our security operations.



With Scrut, we’ve been able to show the right policies, procedures, and evidence, opening doors to more deals.



Thanks to Scrut, we’re saving nearly 100 hours every month across our GRC and solutions teams.


Connect the Scrut Platform to your tools. Automate control monitoring and evidence collection from the word ‘go.’





